 How secure is your home or corporate network? Many administrators believe they are protected behind layers of security solutions such as firewalls, IPS/IDS appliances, endpoint security products, content filters, SIEMs, etc. Regardless of your investment in security technology there will always be risk, which dramatically increases as soon as people are included in the equation. One way to verify your risk level is to become the hunter rather than hunted by scanning all traffic on your network for malicious behavior. You may be surprised to find an unpatched server leaking sensitive information through hidden ports or bots hidden on your personal computer phoning home in the middle of the night!
How secure is your home or corporate network? Many administrators believe they are protected behind layers of security solutions such as firewalls, IPS/IDS appliances, endpoint security products, content filters, SIEMs, etc. Regardless of your investment in security technology there will always be risk, which dramatically increases as soon as people are included in the equation. One way to verify your risk level is to become the hunter rather than hunted by scanning all traffic on your network for malicious behavior. You may be surprised to find an unpatched server leaking sensitive information through hidden ports or bots hidden on your personal computer phoning home in the middle of the night!
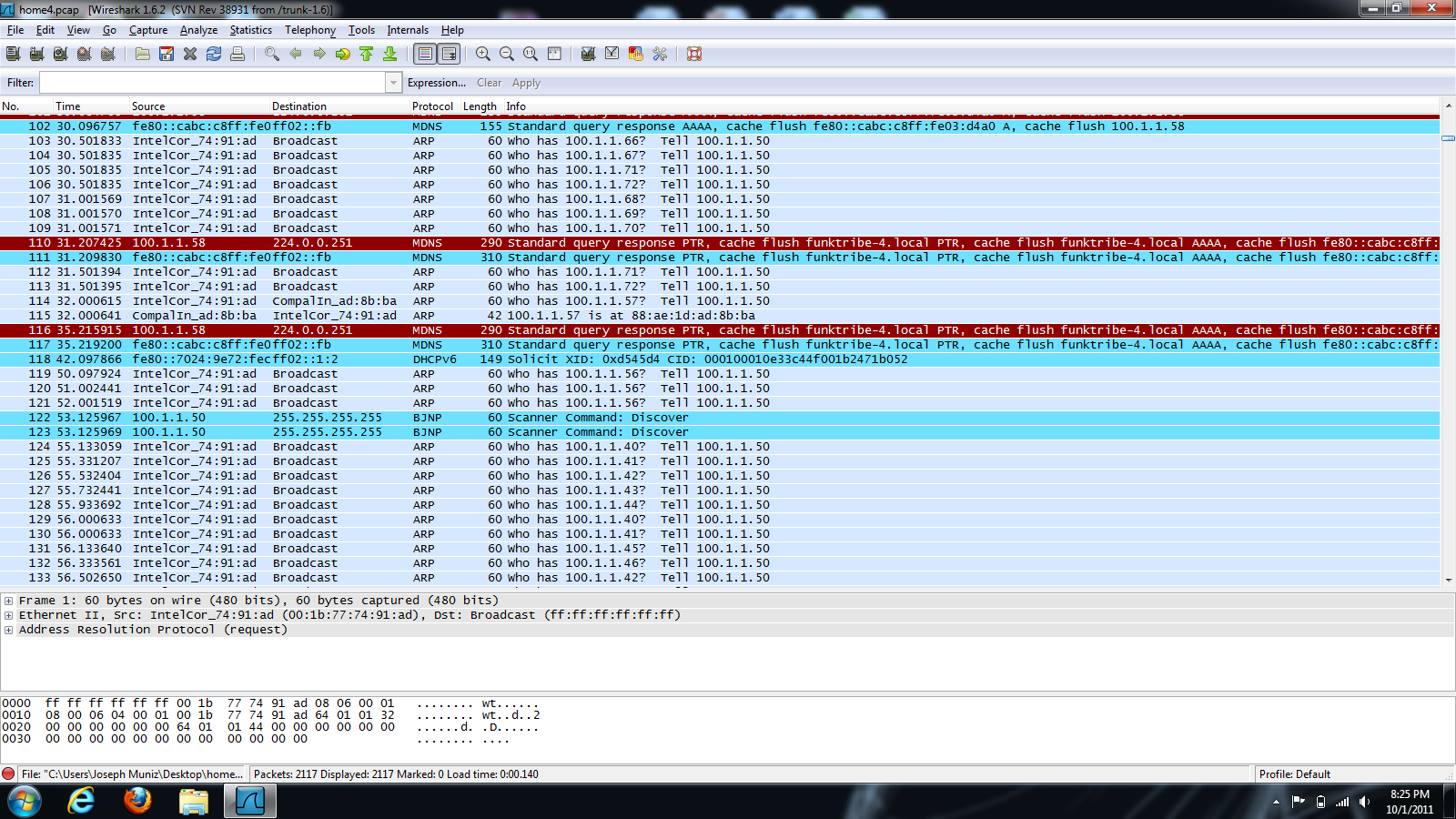
There are vendors and consultants that can offer scanning services, which usually are extremely pricey but worth every penny. Regardless, some of us don’t have the budget or would like to test our home network and can’t justify purchasing enterprise level technology for one or two computers. For those use cases, there are open source tools available for performing packet captures. One of the most widely used open source tools is Wireshark. Wireshark provides detailed information about network traffic down to the packet level. Unfortunately many administrators don’t understand the information being displayed by protocol analyzers such as Wireshark. For some people it’s like staring at the matrix code, which only trained security analyst are capable of seeing the blond, brunette and redheads. NetWitness offers a free threat analysis tool called NetWitness Investigator that quickly translates a large packet capture session into readable data. For example, Investigator may reveal your home network is sending large amounts of data to other countries, which is a pretty good indicator that you have a problem.
You can download WireShark from HERE
- Once downloaded and installed, open WireShark
- Click capture from the top menu.
- You will see the capture options
- Choose the interface you want to capture (Ethernet, wireless, etc.)
- Tune things as you see fit or leave them default and click start
- You should see packets flowing on the screen. If not, you have not selected a live interface.
- One way to see which interfaces are seeing data is clicking capture followed by capture interfaces. You will see which interfaces see packets via the counters.
- Once your done, save your capture and move to NetWitness.
Using NetWitness Investigator: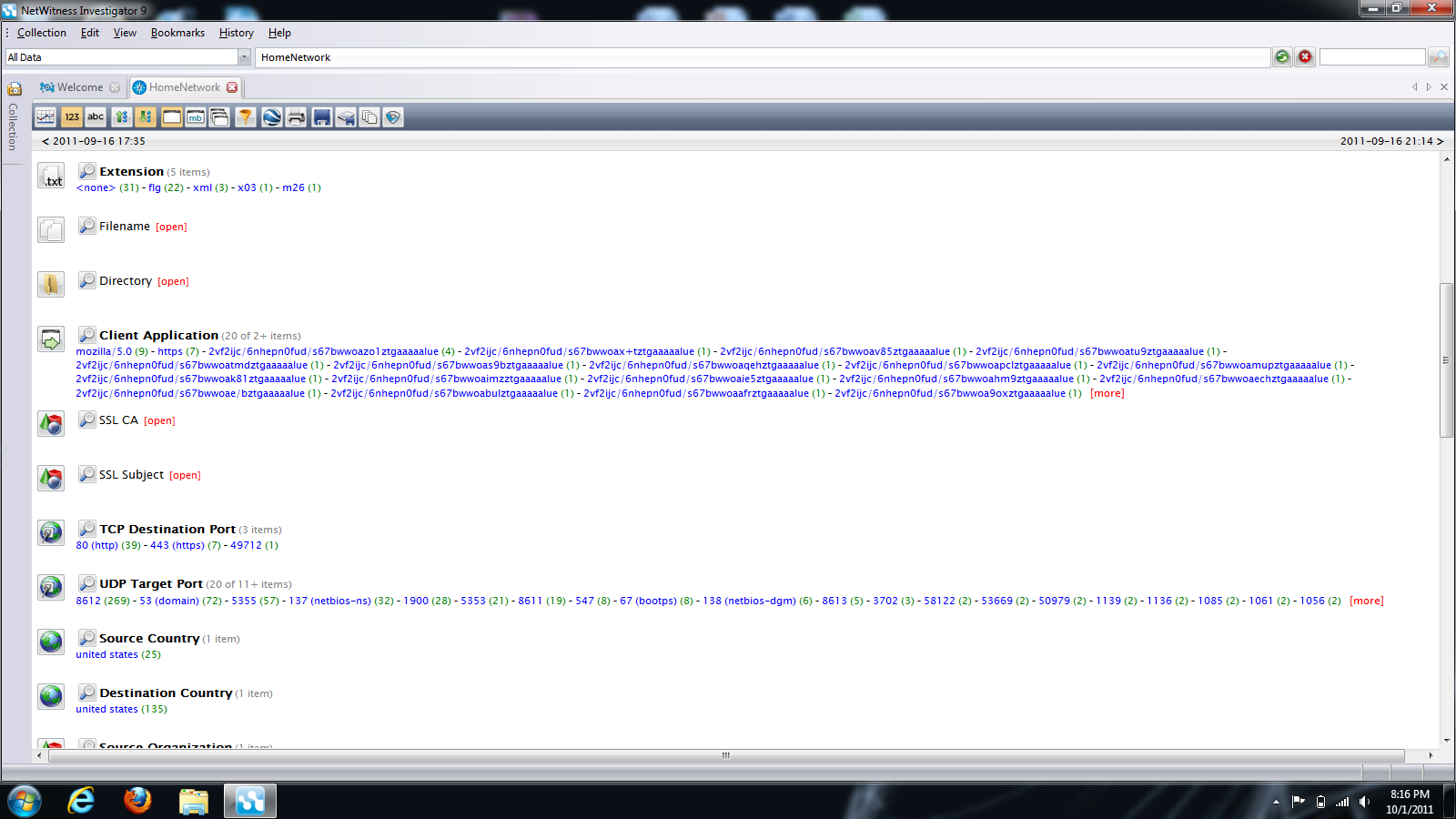
You can download NetWitness Investigator from HERE
- Once downloaded and installed, open NetWitness Investigator
- Right click the left column under Demo Collection and select new local collection
- Give it a name and click OK
- Click your new folder and select import packets
- Select your wireshark capture.
- Double click the folder and your capture will be presented
- Click any selection on the left to dive deeper into your capture.
- Look for odd behavior such as weird ports, destinations, countries, etc.
It’s important to test the security status of your network. Many malicious applications are designed by hackers to be hidden using stealthy techniques that can’t be seen without a packet capture tool. Both Wireshark and NetWitness Investigator are free yet powerful tools you can use to detect communication from hidden malicious applications.




Thank you for this! It clearly explains the differences between the two tools and how to use them together.
Looks pretty damn helpful! 😉