I have attended the Black hat and DEF CON security conference week for many years and recently spoke for my third time at a Wall of Sheep fire talk for DEF CON 24. This year I gave up a day to volunteer for the Wall of Sheep group with the goal of learning more about everything that goes down at this village within DEF CON. This post will cover that experience.
DEF CON is a unique security conference that follows the Black Hat conference. One way to compare the two conferences is Black hat could be considered a more cooperate sponsor driven event with a ticket cost ranging from one to multiple thousand dollars while DEF CON is a hacker culture (hacker meaning exploring technology verses being evil) focused event with a much more reasonable $240 dollar cash only price tag. Both conferences provide talks on various security topics and probably one of the best places to hear the latest trends. It is important to also note that there is another fantastic security event that happens prior to DEF CON and simultaneously with Black hat known as B-Sides Las Vegas also providing top notch security content. Many people would say a B-Sides / DEF CON schedule is comparable in quality to a Black hat / DEF CON schedule depending on your learning and business objectives.
 Within DEF CON are various groups including the infamous Wall of Sheep village. Many DEF CON attendees wonder into the Wall of Sheep village area and notice a large screen displaying user names and half of their passwords representing somebody that had their login credentials stolen. The purpose of this demonstration is to present what could happen when users let their guard down while using network resources and not securing their systems and commutation meaning lacking encryption and limiting service exposure. When a new username and password is discovered, it is added to the wall sometimes followed by a humorous video clip of a sheep being physically exploited. You can learn more about the concept behind the wall HERE.
Within DEF CON are various groups including the infamous Wall of Sheep village. Many DEF CON attendees wonder into the Wall of Sheep village area and notice a large screen displaying user names and half of their passwords representing somebody that had their login credentials stolen. The purpose of this demonstration is to present what could happen when users let their guard down while using network resources and not securing their systems and commutation meaning lacking encryption and limiting service exposure. When a new username and password is discovered, it is added to the wall sometimes followed by a humorous video clip of a sheep being physically exploited. You can learn more about the concept behind the wall HERE.
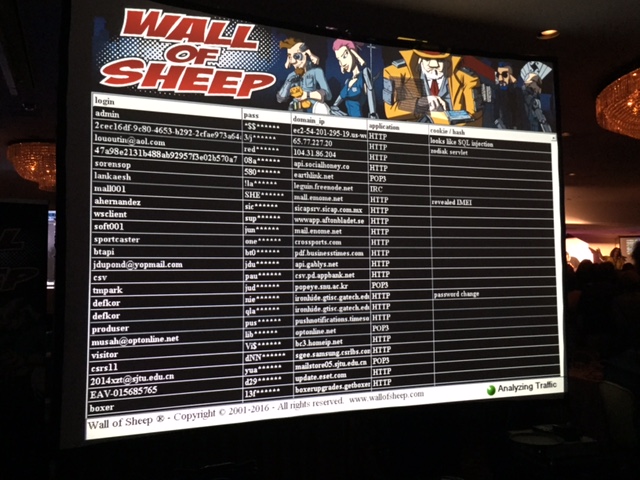 The process to capture credentials found on the Wall of Sheep evolves monitoring the DEF CON network for unencrypted traffic. In the beginning, this was done by members of the Wall of Sheep group however today any attendee is welcome to plug into the network and attempt to eavesdrop on traffic found on the network. This year’s Wall of Sheep village offered seats for anybody interested in participating in sniffing traffic and contributing to data displayed on the Wall of Sheep as shown. Note these are general conference attendees.
The process to capture credentials found on the Wall of Sheep evolves monitoring the DEF CON network for unencrypted traffic. In the beginning, this was done by members of the Wall of Sheep group however today any attendee is welcome to plug into the network and attempt to eavesdrop on traffic found on the network. This year’s Wall of Sheep village offered seats for anybody interested in participating in sniffing traffic and contributing to data displayed on the Wall of Sheep as shown. Note these are general conference attendees.
 There are other events in the Wall of Sheep village beyond the actual wall. One section called the Packet Detective provides various level classes targeting packet detection and analyses. There isn’t a cost to attend any session making it extremely popular and sometimes challenging to find an available seat.
There are other events in the Wall of Sheep village beyond the actual wall. One section called the Packet Detective provides various level classes targeting packet detection and analyses. There isn’t a cost to attend any session making it extremely popular and sometimes challenging to find an available seat.
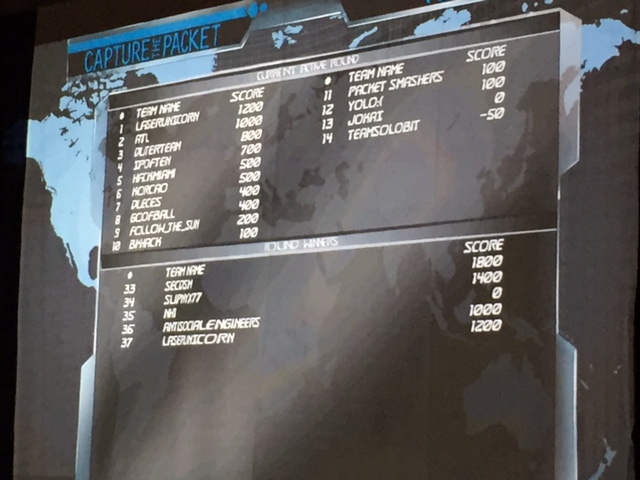
 If you have the black belt skills then another popular event that happens within the Wall of Sheep is the capture the packet tournament IE the CTP. Individuals or teams of two compete by answering various challenges involving examining traffic off a network port. The top teams are invited to take on other top teams in a semi-final and later final round for prizes and fame. I spent time this year volunteering time supporting this event with tasks ranging from assigning teams their work space to ensuring only authorized people were in the gaming area. The next images show the gaming environment and the scoreboard as the competition was taking place. We saw a lot of talent this year.
If you have the black belt skills then another popular event that happens within the Wall of Sheep is the capture the packet tournament IE the CTP. Individuals or teams of two compete by answering various challenges involving examining traffic off a network port. The top teams are invited to take on other top teams in a semi-final and later final round for prizes and fame. I spent time this year volunteering time supporting this event with tasks ranging from assigning teams their work space to ensuring only authorized people were in the gaming area. The next images show the gaming environment and the scoreboard as the competition was taking place. We saw a lot of talent this year.

 One popular feature of The Wall of Sheep area are the security talks beyond what is listed for DEF CON that happen during the entire DEF CON event. For example, this year my talk “Now you see me, no you don’t” happened at 1:10pm on Saturday. Talks are extremely popular and this year overcrowded the designated area. To accommodate more space and due to heat from crowd, the Wall of Sheep team had to move the entire speaking area before my talk, which they accomplished in a astonishing 25 minutes (very impressive). You can see an example of this past year’s talks HERE.
One popular feature of The Wall of Sheep area are the security talks beyond what is listed for DEF CON that happen during the entire DEF CON event. For example, this year my talk “Now you see me, no you don’t” happened at 1:10pm on Saturday. Talks are extremely popular and this year overcrowded the designated area. To accommodate more space and due to heat from crowd, the Wall of Sheep team had to move the entire speaking area before my talk, which they accomplished in a astonishing 25 minutes (very impressive). You can see an example of this past year’s talks HERE. Here is the crown right after we moved things outside of the village before my talk.
Here is the crown right after we moved things outside of the village before my talk.

 Other challenges are offered within the Wall of Sheep that let attendees attack various types of devices as well as hunt for wireless enabled devices. The following images show some of the devices that were available to penetration test. Those sections are called WIFI SHEEP HUNT (searching for wireless devices) and SHEEP CITY (attacking various devices).
Other challenges are offered within the Wall of Sheep that let attendees attack various types of devices as well as hunt for wireless enabled devices. The following images show some of the devices that were available to penetration test. Those sections are called WIFI SHEEP HUNT (searching for wireless devices) and SHEEP CITY (attacking various devices).
 One last aspect of the Wall of Sheep is the overall vibe of the area. There are volunteer DJs playing live music, which I played old-school hip-hop vinyl set at a few years back. Everybody is super cool and willing to contribute to this learning environment no matter what level of skills or awareness you have. The Wall of Sheep village is really a conference within the DEF CON conference and fantastic community of people donating time for the pure cause of throwing a great security event.
One last aspect of the Wall of Sheep is the overall vibe of the area. There are volunteer DJs playing live music, which I played old-school hip-hop vinyl set at a few years back. Everybody is super cool and willing to contribute to this learning environment no matter what level of skills or awareness you have. The Wall of Sheep village is really a conference within the DEF CON conference and fantastic community of people donating time for the pure cause of throwing a great security event.
Make sure to spend time attending the Wall of Sheep village at next year’s DEF CON and don’t be afraid to signup for some of the classes and challenges. Many good people will be there to welcome you to the community. Oh and check out https://www.wallofsheep.com for various penetration testing products. I ended up spending less money for similar tools in the Wall of Sheep vending area verses the general DEF CON market place. The good news the Wall of Sheep online market is always open!



