Verizon recently released their annual Data Breach Report (download HERE). This report is based on statics from 19 organizations and showcases 621 security breaches and 47,000 security incidents with the goal of educating the public of the current risks from cyber threats. All results are built from first-hand evidence collected during paid external forensic investigations and related intelligence operations conducted by Verizon from 2004 through 2012.
Verizon recently released their annual Data Breach Report (download HERE). This report is based on statics from 19 organizations and showcases 621 security breaches and 47,000 security incidents with the goal of educating the public of the current risks from cyber threats. All results are built from first-hand evidence collected during paid external forensic investigations and related intelligence operations conducted by Verizon from 2004 through 2012.
There are a lot of interesting findings that range from most common attacks to popular targets. According to the report, everybody is a target. The report states, “from pubs to public agencies, mom-and-ops to multi-nations, nobody was immune”. Some attacks had as high as 95% success rates such as phishing meaning “most attackers would be able to slap a “guaranteed” sticker on getting a click”. They even call out that most agencies should mentally be thinking they are already compromised.
To break things down, here are some highlights:
- Who are the targets? – Everybody
- Who is perpetrating breaches? The majority of attacks are outsiders (92%) however insider is on the rise (14%).
- How do breaches occur? 76% was based on weak or stolen credentials followed by hacking (52%) and Malware (40%).
- How sophisticated are the attacks? From a range of High to Very Low, the majority of first breaches were done leveraging Low level attacks. I like how they put it by saying “Would you fire a guided missile at an unlocked screen door”.
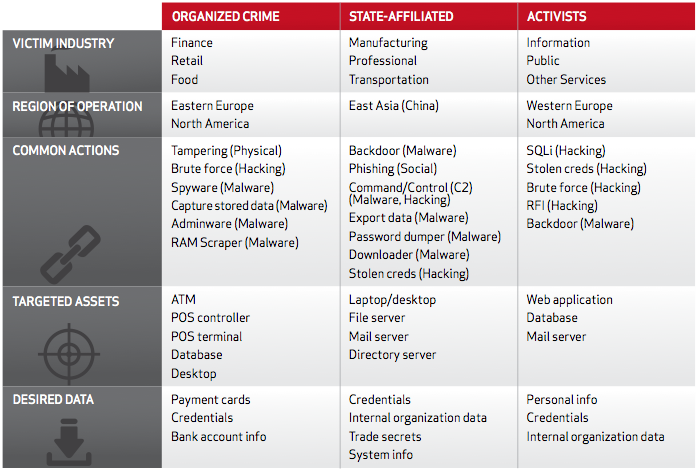
- Who are the Criminals? Organized Crime made up the majority of external attacks (over 50%) while others fell around 20% or less.
- The leader for espionage was China while Romania followed by the USA lead for financial crimes. Spyware (including keyloggers) is the common method for financial crimes while multiple forms of malware are typical for espionage.
- Social Engineering took a dip the last two years but is now up according to 2012 (29%)
- Installing Malware to compromised systems is still the most common vector to be breached.
- ATM hacking was top of the list for physical crimes. I wonder if this was triggered by Barnaby Jack’s Blackhat.
- 2/3 of data compromised was data at rest meaning on an asset like a database or file server. 1/3 of the data was compromised when the data was being processed such as Ramp scrapers, skimmers and key loggers. No data was compromised while in transit (IE compromising a backbone router).
The Verizon report is another confirmation that cyber threats are very real and probably active insider your network. The reports calls out that the most common attacks are easy to execute and have very high success rates (such as phishing campaigns). Standard security products that leverage signatures will not catch many threats called out in this report. The best way to identify these threats is monitoring behavior inside the network and utilize a layered approach to building your security strategy.