Here is a guest post from Pierluigi Paganini. He is a security researcher for InfoSec Institute. InfoSec Institute is an information security training company now offering a mobile computer forensics course.
The IT landscape is dominated by the rise of paradigms such as cloud computing, mobile networking, and social networking, three concepts that have totally revolutionized the daily user’s experience on the web.
Users, in a more or less conscious way, have now become slaves of the concepts of mobility and connectivity, technological change has been rapid and has involved masses of people as never before. There are a billion people, acting as nodes in a global network and exchanging an unimaginable quantity of data, while ignoring the basic concepts of information security.
– Which means are used for the data transfer?
– Are the communications channels secure?
– Where is the user’s information hosted?
– What is the impact on user’s private and what is the impact of technological innovation for business?
All of these questions need careful reflection to avoid serious consequences for our data, for our digital identities, for our business.
Every day we read the world “BYOD” in many articles, but how much we know about it?
BYOD is an acronym for “bring your own device” and it refers to the fact that employees, business partners, and other users bring their own mobile computing devices, such as laptops, tablets, and smartphones, to the workplace for use and connectivity on the corporate network and for access to business data. The repercussions, from the security perspective, are extremely serious, because the absence of proper policies regulating the use of these devices exposes user and company to risk of data leak and cyber attacks.
These policies have to address the ways in which employees could use the devices once out of workplace, the mechanisms of access protection to be adopted, data encryption, data accessible by the mobile platform, and limiting the execution of applications that can be run outside the company (e.g., email client or data mining applications).
Suggestions for a secure BYOD policy
The proper management of mobile devices and their use by employees when outside is a critical aspect for the security of enterprises. Companies today may choose to be compliant to different standards and regulation; the majority of them, such as ISO 27001, already cover many aspects that could improve a BYOD policy.
Because the presence of mobile devices inside companies and government agencies has increased at an impressive rate, ordinary business relationships with other enterprises, such as clients and providers, require the definition and the adoption of a proper BYOD policy. Sophos proposed a document titled “BYOD Risks and Rewards” that reports that one in four devices used today for work are either smartphones or tablets.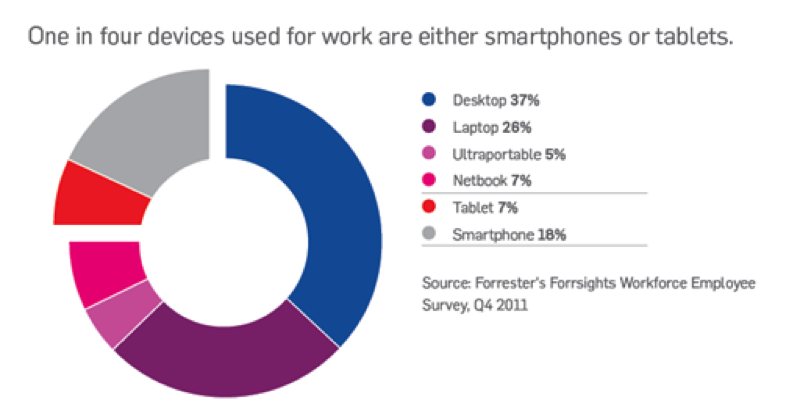
Figure 1 – Sophos BYOD Survey
The SANS (SysAdmin, Audit, Networking, and Security) Institute in March 2012 published the whitepaper “SANS Mobility/BYOD – Security Survey.” The survey found that “only 9 percent of respondents felt completely aware of all mobile devices accessing their enterprise infrastructure and applications. At the same time, nearly 40 % felt they were fully aware of their devices, while nearly half did not have the level of awareness that they should.”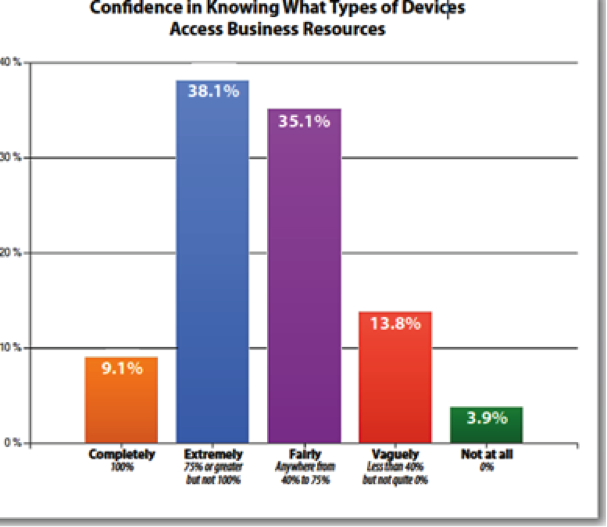
Figure 2 – SANS Institute -State of Mobile Devices Awareness
IT departments of many companies have a new challenge, keeping corporate resources safe, ensuring data integrity, protecting internal data from unauthorized access, preserving confidentiality, and making sure that BYOD regulation is accepted and implemented by the staff.
The definition of a proper BYOD policy has to be contextualized for the specific sector. Every company in fact has its own needs for mobile connectivity, depending on the employment sector; different sectors in fact are characterized by the enormous differences in term of data and processes.
Every day employees access company repositories from outside, use corporate applications to connect to internal repositories and access the company’s information, and they can do it using different technological solutions such as VPNs or dedicated communication channels.
The mobile devices are assigned to the employee with the intention of offering a mobile office, a functional workspace that provides an equal opportunity for access when it is in place.
But how do employees manage their mobile devices?
Let’s consider a simple example: an employee accesses the internal network using a custom application installed on his mobile. When he is at home, his son uses the same mobile to install games, download music, and chat with his friends, all operations that expose the father’s company to security risks. Believe me, that is normal! Compromised applications could expose corporate sensible data to data breach risks and could allow cyber criminals to steal credentials and access corporate networks with disastrous consequences.
Again, what could happen if a mobile device is stolen or lost and the data stored on hard disk are not enciphered? The thief could easily use the device to acquire corporate sensitive data such as a secret project or the quotations for a product to present for a tender.
The most important reasons for adopting mobile devices are the simplicity of use and the possibility of quick access to data and internal resources. Dedicated security mechanisms are developed to allow it, but these are perceived by the employee as useless overload.
Following is a short list of suggestions that could improve a BYOD policy to preserve corporate security when mobile assets are used by employees from outside the company.
- Set expectations for the introduction of a BYOD policy. Company management must define a set of targets that they intend to achieve with the introduction of the policy, as usual calibrating the effort needed with the expected results.
- Review any security policy related to mobile devices. A useful exercise for the company is to identify the best practices suggested by other standards and regulations with which the company is compliant.
- Take a census of all mobile devices among the staff, determining which ones will meet the security requirements of the company. The company could decide, for example, to permit only specific use of mobile by personnel.
- Write clear policies governing the use of mobile devices by employees. Terms of use must be defined for each category of mobile devices, including data and applications referenced by employee. Any employees participating in BYOD must accept the terms of use defined.
- Verify the integrity of each mobile device, confirming that they haven’t been jailbroken or rooted by employee.
- Define and make mandatory a set of security mechanisms for mobile devices (e.g., authentication processes, data encryption).
- Review security policies for web services, remote access through mobile devices, and VPN use.
- Determine which applications can be installed and used by employees.
- Define which data can be accessed from outside.
- As mobile devices become conduits for information to flow, look for apps that include auditability, reporting, and centralized management. Many current apps don’t meet these requirements.
- Periodically review policies and audit mobile devices and installed applications.
- Provide training to employees on the proper use of mobile devices and the way they access internal network and data.
- Improve risk management process and instruct employees on possible threat and related risks for mobile.
Responsibilities
The definition of a BYOD policy has a direct impact on company employees, precise and well-defined responsibilities are assigned to each individual. Following is an example of how these responsibilities could be divided between the different departments of any business.
- Corporate IT Security Management is responsible for defining and maintaining the company BYOD policy, taking charge of the various problems arising from its introduction. Management must evaluate the corporate capabilities offered to the employees and the related benefits. Management has a crucial role; its commitment is fundamental for BYOD governance, assigning roles and responsibilities to each actor in the company. Security management is also responsible for the identification of the security, financial, and competitive risks involved in pursuing the BYOD strategy.
- Human Resources is responsible for running educational programs to raise awareness and understanding of the obligations established in the BYOD policy.
- IT Department is responsible for managing the security of corporate data and infrastructure.
- IT Help/Service Desk is responsible for providing limited support for BYOD to the employees.
- All employees are responsible for complying with corporate policies proposed by management.
- Quality and Internal Audit Department is responsible for assessment activities to verify level of compliance with this and other corporate policies.
BYOD and business … Mobile Device Management Strategy
Today enterprise IT and the consumer world are converging. An increasing number of devices and applications could be used for both purposes, therefore it is fundamental to define a set of policies that regulate the phenomenon in corporate environment.
The advent of personal devices must be managed within the enterprise. IT management policies need to be drawn up with the active participation of all business functions; this process is called “mobile device management strategy” and one of the hinges is the separation of personal data into the business and related management flows.
Employees like BYOD because they perceive it as the business being open to them. According a study of principal Italian companies, 28% of businesses do not allow any personal devices to access internal data and resources, 44% allow it only in particular cases of top management, and only 28% always allow it.
The worldwide situation is quite similar, according to data from SANS Institute and shown in the following graph: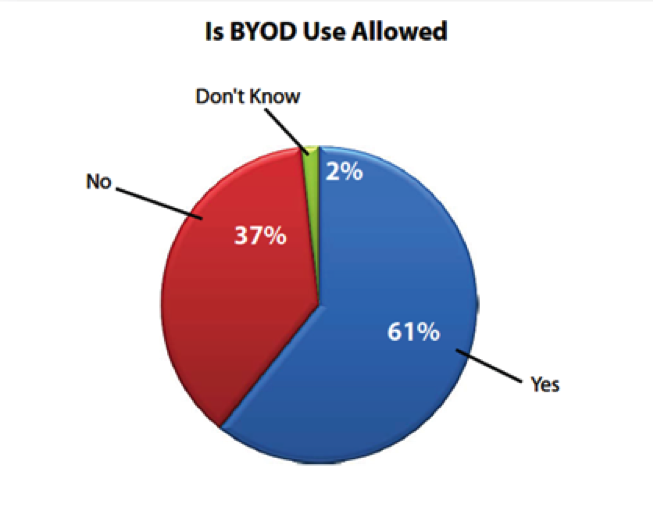
Figure 3 – Organizations allow BYOD devices (SANS Institute)
The data demonstrate that despite the fact that there is an impressive penetration level of mobile, many companies are still not prepared to open their infrastructures to mobile devices from outside; in both cases, the devices are personal and corporate. Having a proper BYOD policy means that a company must invest in infrastructure and security, an overhead not always sustainable, at least until now.
Essentially an enterprise mobile policy is focused on the following aspects:
– Enabling new business processes
– Reducing risks
– Managing direct and indirect costs
The policy has to identify exactly the types of devices that can be used and the employees who are allowed to use them. The operating systems allowed and the applications that can be executed must also be specified.
A crucial factor related to the introduction of mobile devices into the company is the impact on overall security of company.
Security component of BYOD
One of the main impacts of BYOD is that the IT security of the company that must take into account the fact that employees have their own devices and that it is useless to prohibit their use in the workspace. The right approach to the problem is to identify the threat related to mobile environments and the risks for the company.
It is fundamental is to understand that both employees and the company manage the user’s mobile device. Both have to collaborate to secure corporate resources from unauthorized accesses by defining who can bring mobile devices into the company, selecting the data that can be accessed, implementing the authentication methods, and determining which applications can be executed on the devices.
In May 2012, IBM prohibited its employees from using two popular consumer applications, Dropbox and Apple Siri for iPhone, for security reasons; both applications, in fact, if used improperly, could allow data breach.
As suggested by Sophos, the “the first and best defense in securing BYODs begins with the same requirements you apply to devices that are already on your network.” This sentence expresses the need to adopt for mobile devices inside a company the same measures already implemented for any other devices.
When we think of security for any appliance inside a network we immediately think of authentication methods and defense systems. So if we use passwords or many other authentication components on our desktops, why do we not adopt them also for mobile devices? We can have the same discussion about antivirus applications: almost all smartphone users don’t install any antivirus protection and it must be noted that mobile platforms, Android first, are becoming privileged targets of cyber criminals and hackers. An impressive amount of malware is explicitly designed for mobile devices and the risk of introducing them into a company is very high.
Another critical aspect is data protection. What might happen in case of loss or theft of company mobile devices? Corporate sensitive information could be exposed. It’s happened many times; just think of the problem faced by NASA when employees’ laptops were lost. Best practice suggests the adoption of full-disk encryption for disk for any mobile and removable storage. That is the only way to protect data from undesirable accesses and data leaks.
It is also strongly suggested that mobile device management (MDM) be adopted to wipe confidential data when devices are lost or stolen.
Last, but not the least important, applications running on mobile devices must be controlled. Some applications are potentially dangerous to the corporate business; for example, applications that share content in a non-protected mode on cloud storage exposes data to serious risks. The same applies to each application that automatically acquires information on the state of use of devices, such as its movements.
It’s very common to read about the use of non-company software made by employees. A specific term has been coined for this: BYOS (bring your own software).
Employees could use free applications to share documents, such as public cloud storage or VOIP chat services, but these documents might contain confidential data, which would fall into the scope of internal policies, so it is important to census all those applications that could violate internal regulation.
Data encryption could help to secure company documents, but this security process also has to be regulated to avoid risky behavior, such as the use of weak encryption password or the sharing of the same password among different customers or departments of the company.
In a business context, any agreements with third parties that govern the use of mobile systems must also be analyzed.
From personal experience, the most important factor for the success of any BYOD policy is the institution of an efficient training campaign for the employees. Human factor is the weakest link in the security chain; for this reason it is important that any employee knows the advantages connected to the use of mobile devices inside workspace and at same time must be informed about the best practices to follow and the risks resulting from their non-adoption.
Resuming, a BYOD security policy has to address the following aspects:
– Application assessment and control
– Policy compliance and audit reports
– Authentication mechanisms
– Data and devices encryption
– Remote device management
– Email accounts management
– Protection from cyber threats (e.g., malware)
– Revoking access to any corporate data and resource when employee leaves the company
– Evaluation of cloud storage security
– Procedure for disposal of mobiles (e.g., wiping)
Pro & Cons of BYOD
In January 2012, research commissioned by Trend Micro was conducted in the U.S. and Europe involving 200 organizations. It revealed that a restricted number of companies measure the financial impact of BYOD.
The principal factors that drive the majority of the firms to define BYOD programs are:
– Increasing employee productivity (70%)
– Need to provide remote access to corporate data and resources outside the office (63%)
– Costs cutting (40%)
According to the respondents, the main benefits of BYOD are increases in worker productivity (66%) and a flexible work environment (66%), but they have reported the increase of costs for mobile device management cost, helpdesk support calls, and helpdesk costs.
Following are the pros and cons that emerged from the analysis:
– 12% increase in worker productivity
– 15% decrease in device replacement costs
– 8% decrease in reimbursement for employee data expense
– 5% decrease in training and education costs
– 3% increase in bottom line revenues
– 8% increase in the number of help desk calls
– 7% increase in mobile device management costs
– 3% increase in corporate liable data costs
– 3% increase in server costs
– 2% increase in regulatory compliance expenses
BYOD is an opportunity for companies, but it must be considered that the lack of a strategic approach exposes organizations to security risks and further financial exposure. Only by defining an efficient set of policies and actively involving any level of the businesses can the enterprises really benefit from introduction of mobile devices.
Conclusions
A Cisco Systems research report, the IBSG Horizon Study, revealed that IT professionals are rapidly aligning their activities to BYOD policies, Seventy-eight percent of U.S. white-collar employees use a mobile device for work purposes, demonstrating that mobility is a pervasive phenomenon that has to be properly regulated.
Every employee uses mobile devices inside the workspace and brings them outside company, often after accessing internal data and resources. Corporate management is conscious of the trend and allows it, convinced that it represents a benefit in terms of productivity and satisfaction. The downside is the impact of these habits on corporate security. The Cisco study reported that 95% of respondents believe that businesses allow the use of employees’ devices in the workplace and 76% think positively about BYOD regulation.
Cisco experts believe that with the increasing number of mobile devices in the workplace, enterprises and small businesses have to adopt a global mobile strategy to obtain the maximum advantages from the introduction of networking that allow employees to work from everywhere.
The evolution of the mobile landscape requires us to consider BYOD as a top priority. Employees want to be able to work from outside with corporate devices and at the same time they want to use their favorite devices from anywhere also in the workplace. A study revealed that the average number of connected devices per employee will increase from actual 2.8 to 3.3 within 2014.
The principal threat to corporate security is represented by the use of unapproved applications in workplace. According Cisco, 69% of respondents said they make large use of social networks, cloud-based email, and instant messaging.
Mobiles, willy-nilly, are invading the market and becoming the main instrument of work within companies. At the same time, each employee daily uses more devices that might be brought to the workplace, the definition of a BYOD policy is a must … IT management must not ignore it.
References
http://www.ictbusiness.it/cont/articolo/le-aziende-italiane-hanno-sposato-il-byod-e-come/29138/1.html
http://www.sophos.com/en-us/security-news-trends/security-trends/byod-risks-rewards/what-byod-means-for-security.aspx
http://www.sans.org/reading_room/analysts_program/mobility-sec-survey.pdf
http://consumerization.trendmicro.com/the-financial-impact-of-consumerization-is-your-byod-program-in-the-money/


