Cisco’s research team Talos wrote a interesting article on their research on Phishing. The original post can be found HERE. For those that don’t know what Phishing is, its the cyber attack where a malicious party pretends to be a legitimate source with the goal to trick a victim into clicking a email, accessing a website, or just giving up sensitive data. Here is the Talos article.
Attackers are constantly looking for ways to monetize their malicious activity. In many instances this involves targeting user data and accounts. Talos continues to see phishing attacks targeting customers of multiple high profile financial institutions. In the past couple of months, we have observed phishing attacks against various financial customers including credit card companies, banks, credit unions, and insurance companies, as well as online businesses such as Paypal and Amazon. These phishing attacks have gone old-school in that they either attach an HTML document or include HTML data in the actual email to present the user with official looking pages that appear to be from the actual businesses being targeted.
Although many phishing attacks attempt to get the user to open attachments that are designed to load malicious software on the user’s system, we have noticed that some attackers have stuck with the basics. Instead of trying to get a user to download or run malicious attachment, these current attackers are simply attaching an HTML document to their phishing emails or including the HTML instructions in the body of the email itself. The following shows the a sample of the realistic phishing attempts that these attackers can generate to trick users into revealing their sensitive information.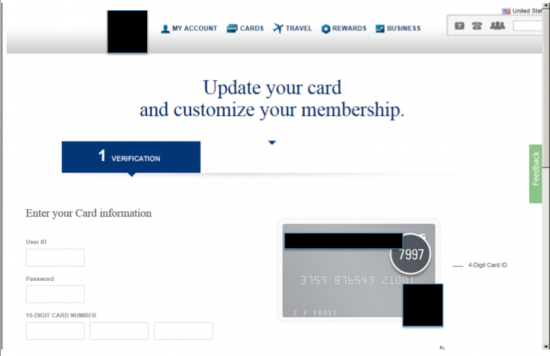
These phishing emails tend to fall into the following two categories:
- Frozen account due to unauthorized access (suspicious charges, unknown ip)
- New security procedures being implemented
Messages targeting the first category include the following: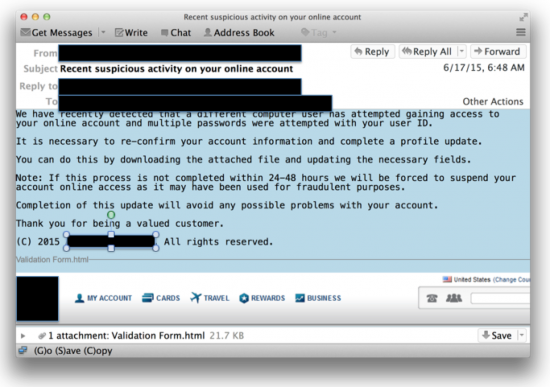
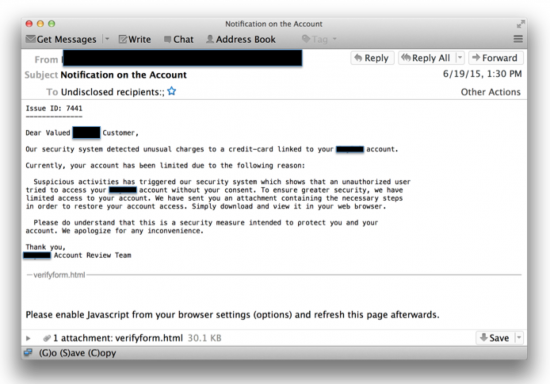 The second category is interesting in that it seems to take advantage of all of the security compromises being reported in the press. These phishing attempts make it appear that the company is upgrading its security to protect its customers better. A sample email targeting this technique is shown below:
The second category is interesting in that it seems to take advantage of all of the security compromises being reported in the press. These phishing attempts make it appear that the company is upgrading its security to protect its customers better. A sample email targeting this technique is shown below: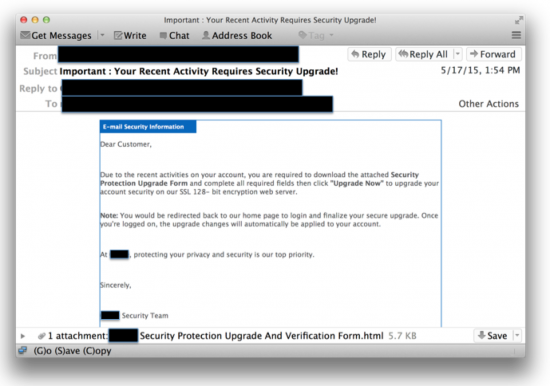
Some of the subject lines observed include the following:
Important Message.
Important Message
Recent Security Update
Unauthorized Access case [Random String]
Suspicious Account Activity Reference [Random String]
Confirm Your Identity
Recent suspicious activity on your online account
Final Notice: Unauthorized Activity on your online account
Your online access has been temporarily suspended
Fraud Protection Alert
Account Review
Account limited
Account Validation
Temporary Limitation
Activity Alert: Important For your Account .
Online-BOFA-Notification
Online-Notification
Monthly Account Online Security Update
Important : Your Recent Activities Requires Security Upgrade
Although these attackers are using a fairly simple approach to fool users, they are not shy about the massive amount of personal information they try to collect from their victims. Each phishing attempt is customized to the fields that each specific financial business uses and the customers are familiar with. To give you an idea of the breadth of information being phished, here is a some of the data that these phishing attacks are trying to get users to divulge:
Userid
Password
ATM PIN
Name
SSN
Mother’s Maiden name
Phone Number
Address
Date of Birth
Place Of Birth
Verbal Phone Password
Email Address
Email Address Password
Security Questions and Answers
Credit Card #
Card Expiration Date
CVV2
Bank Account Number
Bank Routing Number
The attachments are named with either something related to the business name or something more generic. Some of the attachment file names included the following:
Confirm your identity.html
<Company Name>_Procedure_Index.html
BOFA-ONLINE-UPDATE#1024886.html
<Company Name>_Security_Alert_Form.html
VerificationRequired.html
Verify_Account.html
verifyform.html
Validation Form.html
Verification Form.html
Online_Security_Update.html
pp_verification.html
<Company Name>.html
<Company Name>_OnlineBanking.html
Validation form.html
<Company Name> – Security Protection Upgrade Form.html
<Company Name> Security Protection Upgrade And Verification Form.html
These HTML forms are even written to make sure that the user enters the correctly formatted information into fields such as the email address and makes sure that important fields like password or PIN are not left blank. Below shows the error checking that one phish did on the email address:
var email =3D document.getElementById(’email’);
var emailRegEx =3D /^[A-Z0-9._%+-]+@[A-Z0-9.-]+\.[A-Z]{2,4}$/i;
if(email.value.search(emailRegEx) =3D=3D -1){alert(‘Must enter your =
email address’); email.focus();return false; }
for=3D”defaultaddress1″>EmailAddress:<br>
id=3D”email” name=3D”email” size=3D”20″ value=3D””><br>
In fact, in at least one of the phishing emails, the PIN needed to be entered twice to verify that both entries match (similar to password verification).
The realism in these phishing attempts comes from using the links to the images from the actual website for the business being impersonated. Once the user enters his information and clicks submit, then his information is transferred to the attackers through POST requests to sites on various malicious domains.
IOCs:
Domains:
www.HostMls.com
olubunmi.AlterVista.org
townsmiler.altervista.org
wilsontechgroup.com
api.sg
fekfoekfofucku.com
www.linksec.su
sanoricker.com
scincrewsurvey.com
IPs:
209.140.22.151
69.46.65.136
Conclusion:
Attackers are constantly targeting user data and attempting to trick users into leaking sensitive information through phishing campaigns. These phishing attempts are targeting normal users who represent the customers of the various businesses being targeted. If the emails come through a work email, the user can take advantage of a layered approach to security that will usually indicate these attacks as spam or even malicious. Most home users, however, do not have a the same layered security configuration on their home networks. Many of these phishing also attempt to try to place time pressure on the user to get them to act quickly and without taking the time to think about what they are doing. Therefore, it is important for users to be constantly vigilant, and to remain calm when they receive that cleverly crafted phishing email. Users should always take time to think before revealing any sensitive information, whether it is on the phone, via email, or through the web.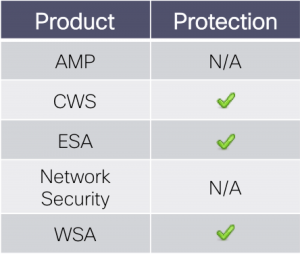
CWS or WSA web scanning prevents access to malicious websites used in these attacks.
ESA can block malicious emails including phishing and malicious attachments sent by threat actors as part of their campaign
Tags: phishing, spam, Talos, threat intelligence




