The security research team at Cisco known as Talos released a huge discovery of complete hidden whois data attached to more than 282,000 domains registered through the company’s Google Apps for work service. This accounts for around 94% of the addresses Google Apps has registered through a partnership with eNom. The original post can be found HERE. The post was created by Nick Biasini, Alex Chiu, Jaeson Schultz, Craig Williams and William McVey.
Overview
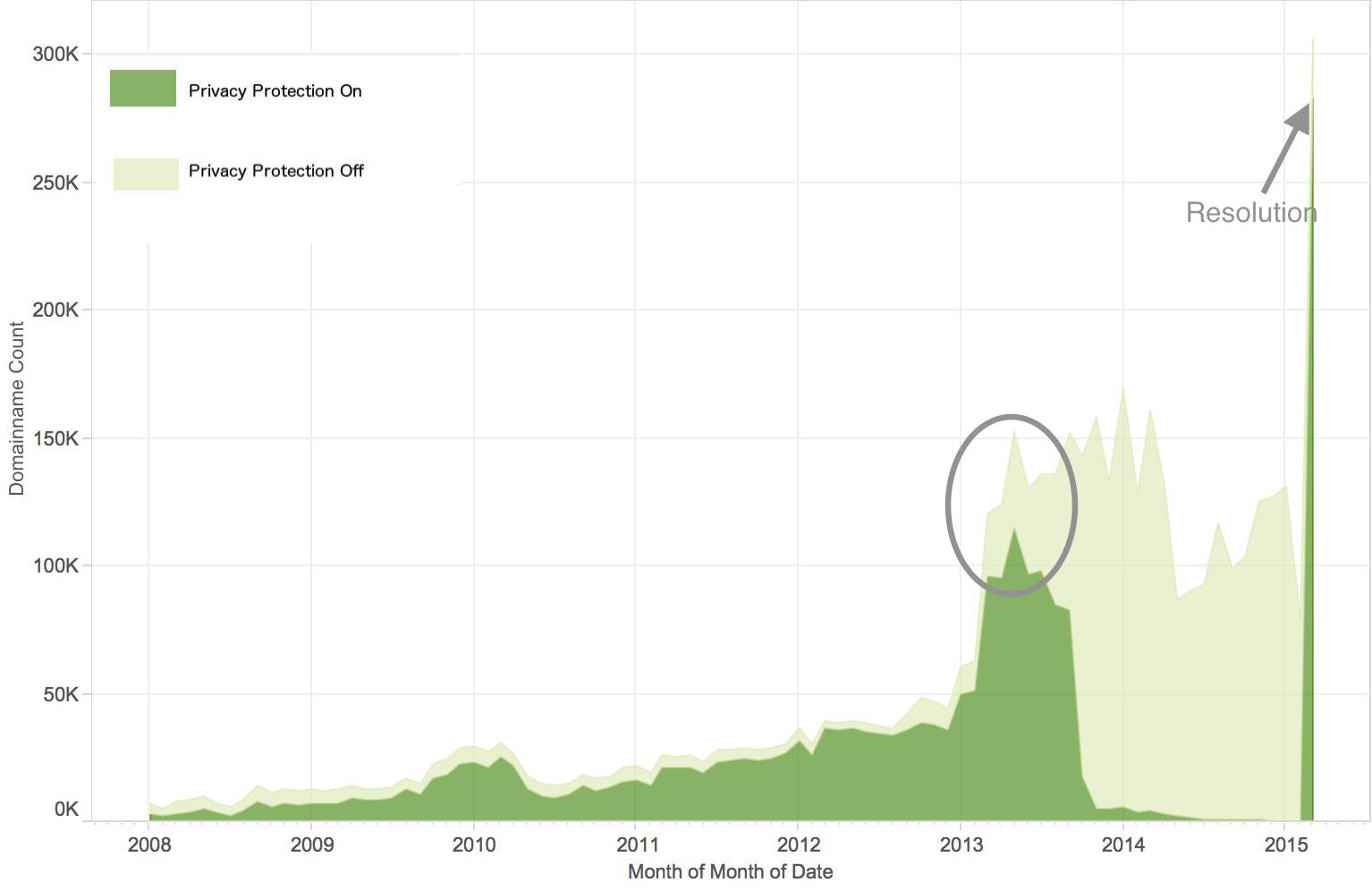
In mid-2013, a problem occurred that slowly began unmasking the hidden registration information for owners’ domains that had opted into WHOIS privacy protection. These domains all appear to be registered via Google App [1], using eNom as a registrar. At the time of writing this blog, there are 305,925 domains registered via Google’s partnership with eNom. 282,867 domains, or roughly 94% appear have been affected [2]. (Google reports that new domains which have not faced a renewal period are not affected and many businesses do not opt into their privacy service.) The information disclosed included full names, addresses, phone numbers, and email addresses for each domain. The information was leaked in the form of WHOIS records.
This information leakage exposed the affected users to a number of possible threats, some of which are described in eNom’s advertisement for the privacy protection service, which states “In America alone, there are an estimated 9 million cases of identity theft each year and 3 trillion spam emails sent each year. Spammers and thieves can get your information through your domain name’s public record. ID Protect keeps your information safe by privatizing your domain’s entry in public records.”
WHOIS Privacy Protection
WHOIS privacy protection service is a commonly used feature for asserting privacy when it comes to Internet domain name registration. Without it, registration information associated with the domain registration, such as name, physical address, email, and phone number becomes exposed to everyone on the Internet. It’s possible to mine this information and leverage it for malicious purposes, such as spamming, spear phishing or other potential forms of harassment. Judging by our numbers for most domain owners, keeping this information private is important. Typically, WHOIS privacy protection is a feature that customers must request and possibly even pay for, in addition to the cost of the domain registration.
Why Does This Exist
Every domain that’s registered on the Internet must have the registrant’s contact information which could consist of identifiable information on file and publicly available. This information is referred to as WHOIS information. In essence, WHOIS acts as the phone book of the Internet, allowing anyone to query who owns what domain and how to contact them. This is a requirement prescribed by ICANN, who organizes and manages the conventions used in domain names. Domain Name privacy protections are used to mask this information from always being publicly displayed. Just as it’s possible to pay to have your name removed from the phonebook.
The Issue
Below, you can observe the issue first hand. We have blacked out the personal information for the affected individual. You’ll notice on the left the domain has opted into the privacy protection service and on the right you’ll see the more recent record where the protection and provided anonymity was removed. It appears that issue occurred when the domains were re-registered.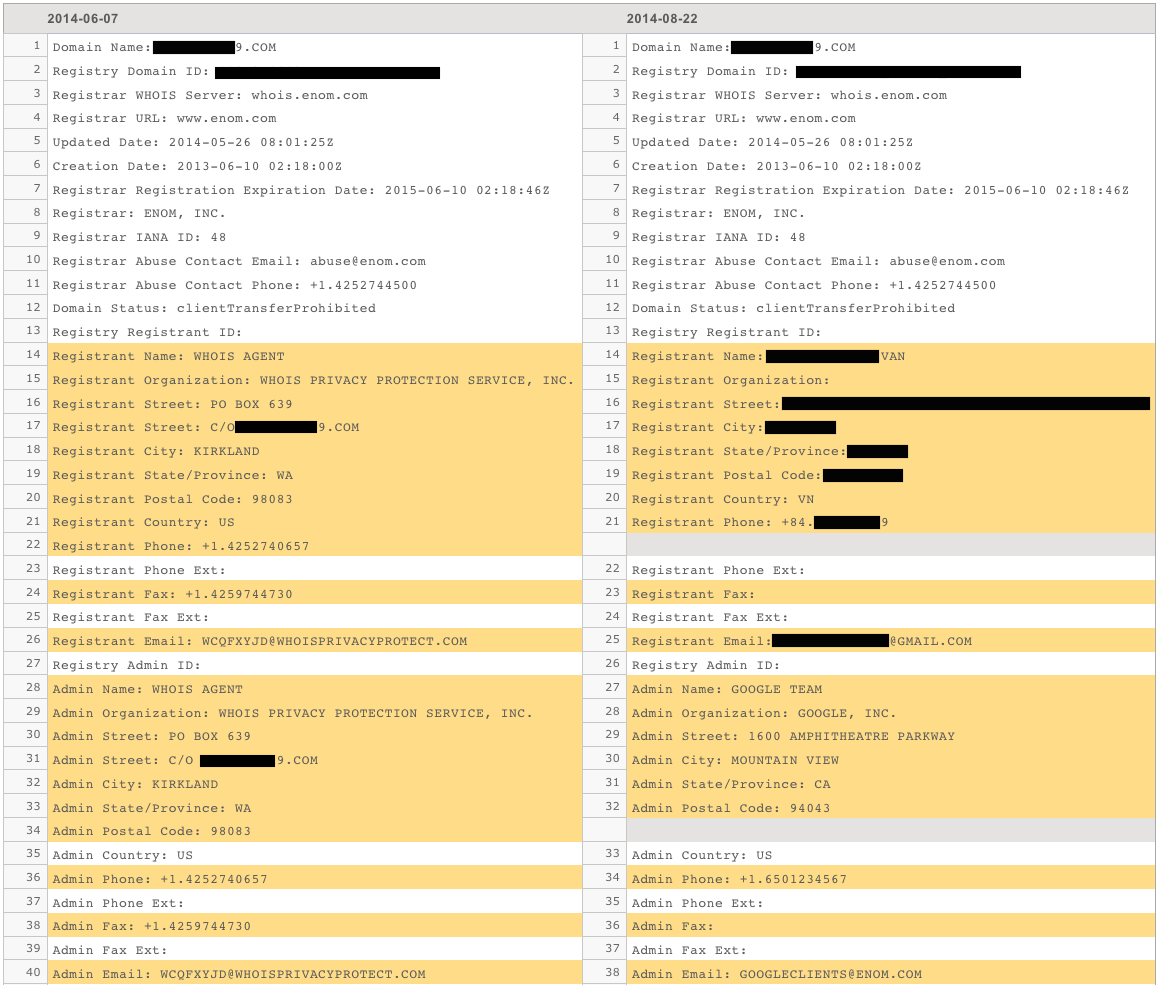
Using DomainTools, a service that tracks hosting, WHOIS, and DNS changes for domains on the Internet, we can see that the domain was privacy protected previously, but was updated later on to the registrants actual name, physical address, email, and phone number.
Recently, Google sent out the following notification:
Implications for the Good & Bad Guys
The reality of this WHOIS information leak is that it exposed the registration information of hundreds of thousands of registration records that had opted into privacy protection without their knowledge or consent to the entire Internet. This information will be available permanently as a number of services keep WHOIS information archived.
Cisco Talos has already identified many affected domains that we have linked to malicious activity. For example, looking at some of the unmasked domains possessing very poor web reputation scores, we can see several potential threat actors who might have some ‘splaining to do. For example, the domain “federalbureauinvestigations.com” has an extremely poor web reputation score. Another domain, “hfcbankonline.com”, also possesses a similarly poor web reputation score (we can only speculate as to the reason). Of course, it is well-known that many WHOIS registration details can easily be forged. In the event that the WHOIS record clearly contains false data, that information can still be used for the sake of threat attribution, as was the case of the String of “Paerls” investigation.
On the other end of the spectrum are domains registered using WHOIS privacy protection for quite legitimate reasons. The obvious risk here is that some of these individuals who have been unmasked may now be in some form of danger as a result of their connection with the domain registration. Additionally, threat actors may use domain registration information for malicious purposes. For example, sending targeted spear phish emails containing the victim’s name, address, and phone number to make the phish seem even more authentic. As eNom points out, identify theft is also a possibility. To best protect themselves users are urged to adopt safe browsing habits and make use of layered defenses like antivirus and antispam technology.
Current State & Mitigations
Cisco Talos became aware of this problem and immediately notified the Google security team. Within days the privacy settings were restored to the affected domains.
However, the Internet never forgets. Affected users need to realize that this information has been publicized. These records will continue to be available to anyone with access to a cached database of WHOIS information.
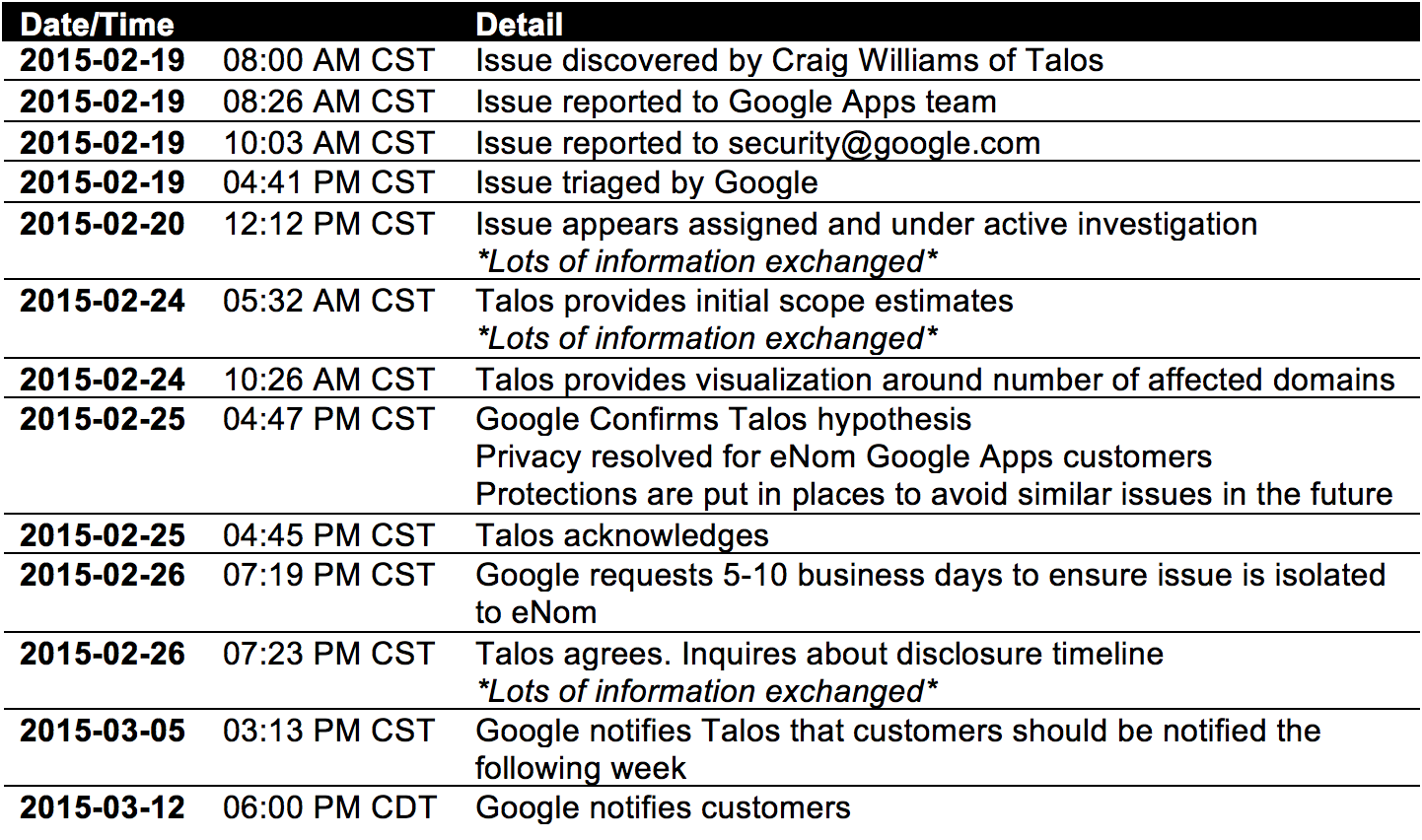
Disclosure Timeline
Conclusion
Privacy remains a key issue of concern for individuals and organizations of all sizes. In the case of WHOIS data and privacy protection, it’s clear that there is value in protecting domain registration information from being published given the 94% opt-in rate. Organizations that handle any sensitive information must ensure that the appropriate systems are safeguarded and that the processes handle failure gracefully. In this instance, a simple check on domains changing state from being privacy protected to not being privacy protected could have identified the problem as it started to occur.
Footnotes
- Google partners with third-party registrars to allow customers who do not already own a domain to purchase one through them to use with Google Apps. This is separate from Google Domains, which launched as a beta in Summer 2014. The numbers quoted above were derived viaDomainTools WHOIS database.
- We arrived at the number domains affected by this information leak by taking the total number of domains which were public when the issue was discovered and subtracting the number that were public after the issue was resolved.