Treatpost.com posted a interesting article on a recent DDoS attack using reflection via portmapper. The original post can be found HERE.
A number web hosting providers and businesses in the gaming industry were last month guinea pigs for a new type of amplified DDoS attack.
Attackers have figured out how to use Portmapper, or RPC Portmapper, in reflection attacks where victims are sent copious amounts of responses from Portmapper servers, saturating bandwidth and keeping websites and web-based services unreachable.
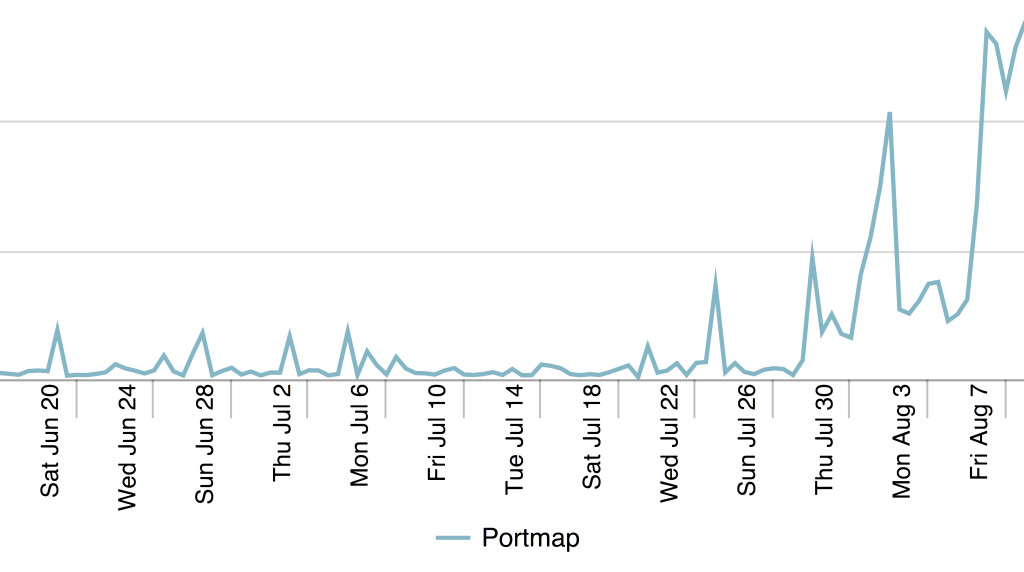
Telecommunications and Internet service provider Level 3 Communications of Colorado spotted anomalous traffic on its backbone starting in mid-June almost as beta runs of attacks that were carried out Aug. 10-12 against a handful of targets, Level 3 chief security officer Dale Drew said.
“The first few days, it looked like they were doing software development and figuring out how to hone and automate the attack,” Drew said. “Then they launched test attacks against specific people on the Internet where traffic ramped up 20- to 30-fold from when we first watched them. We realized we were watching an emerging DDoS that rived the NTP DDoS attacks of two years ago.”
NTP is short for Network Time Protocol, a core Internet service that is used to synchronize computer clocks. Hackers abused vulnerabilities in NTP to launch substantial denial-of-service attacks in late 2013 and early 2014 before the issues were patched.
Level 3’s Drew said his company has notified hosting providers of the emerging attacks, sending them a list of the 1.1 million Portmapper servers accessible on the Internet. Portmapper is a service that runs on all UNIX servers and a growing number of Windows boxes that need to integrate with UNIX. Portmapper runs on network nodes providing Remote Procedure Call services, and always runs on TCP or UDP port 111.
Level 3 said queries used in these attacks have been of a consistent size, making them relatively simple to filter out from networks; the company provided hosting companies and others with the static query to facilitate the creation of firewall rules countering the threat.
Drew said the attacks involve sending a UDP packet to a Portmapper server with a forged originating IP address that belongs to the victim. The Portmapper server sends back a list of networking services to map to, and that list so far has ranged from 7x and 28x the originating request, Drew said, adding that unlike NTP, there are no vulnerabilities with patch with Portmapper.
“It’s just the way Portmapper works unfortunately; it’s doing what it’s supposed to do,” Drew said. “Depending on what you have, it could provide a long list of UNIX or Windows networking services running on the box. It’s a really small query, and you can get back a very long response. All bad guy has to do is send a single query to 1 million Portmapper servers and send 1 million responses back to the victim.”
Level 3 recommends as a mitigation to disable Portmapper and RPC services on the open Internet if they’re unnecessary. Where those services are necessary, the company said organizations should firewall specific IP addresses that can reach those services and then switch to TCP-only.
“It does appear to absolutely be effective,” Drew said of Portmapper DDoS attacks. “These are bandwidth saturation attacks. There’s no finesse to this at all.”