Cisco very recently acquired OpenDNS. For those that are not familiar with OpenDNS, they see around 80 billion DNS records a day meaning they can be pretty effective at determining what is a possible threat from a reputation perspective. Customers can point their devices at OpenDNS and enable content filtering along with different threat blocking features. Cisco also just announced that they have integrated other threat intelligence research from ThreatGrid and AMP making the OpenDNS offering much more effective.
I have tried out the free version in the past and now running the Umbrella upgrade. This post will cover my experience with both the free and paid Umbrella offering.
The most popular offerings from OpenDNS is a free service for protecting your home network. All you need to do is go to opendns.com, register as a home user and point your home router to OpenDNS. You will be presented with options to filter content (IE block adult websites, etc) and enable some basic security filtering (IE block malware sites, etc.). There is also a agent you can download that alerts when the system is protected by OpenDNS meaning when I enable VPN, that is not using my home network and therefor not protected until I connect back to my home network via removing the VPN. The entire process to enable OpenDNS takes minutes. Once things are working, you can go to http://welcome.opendns.com (as shown in the next screenshot) and hopefully you will see the following message stating you are now protected verifying things are working properly.
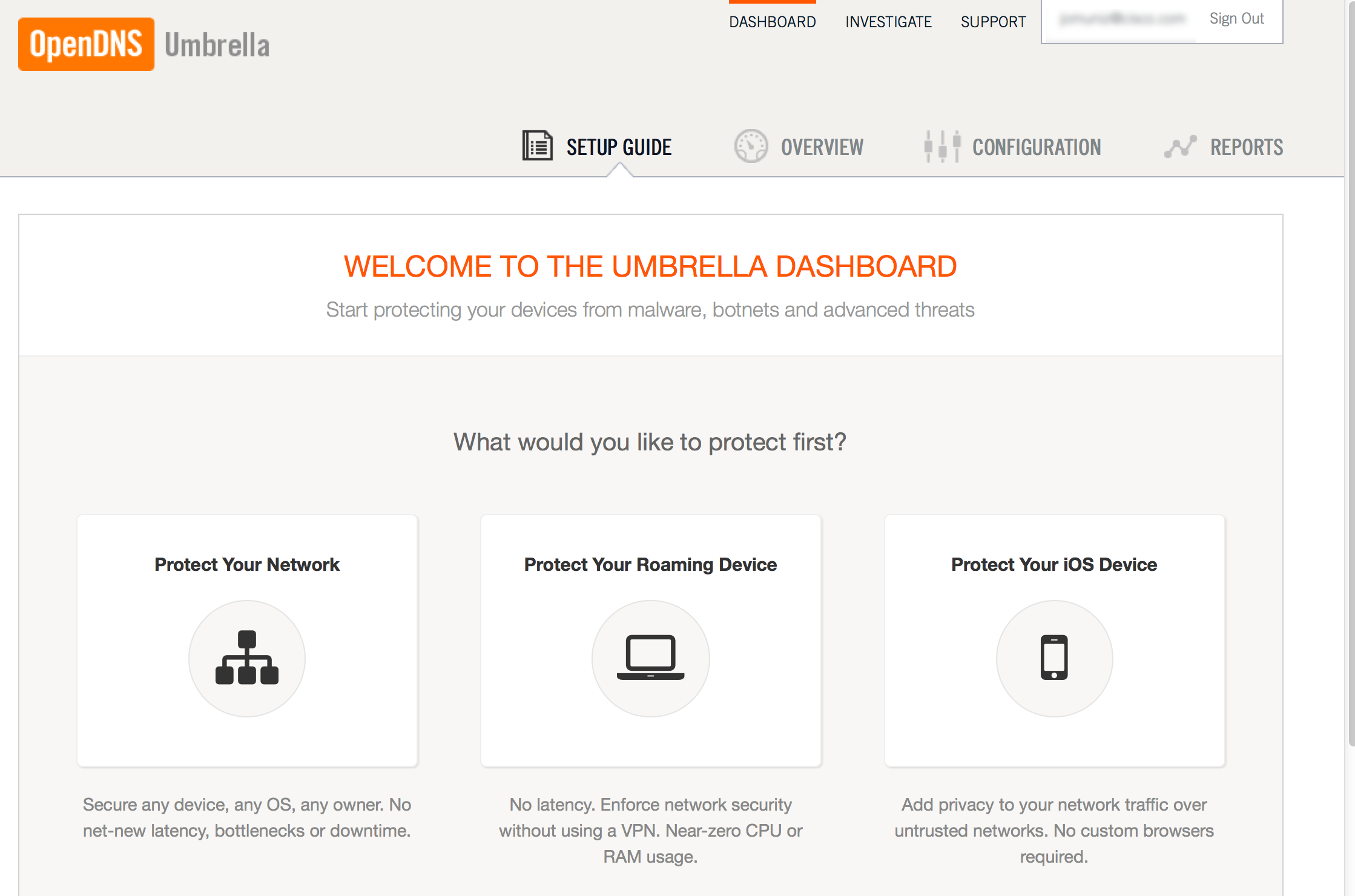
 To protect endpoints such as laptops and iOS mobile devices regardless of what network they are on, you can upgrade to a Umbrella account that has a cost per endpoint. This option provides more features and gives the option to distribute agents to endpoints. This means the agent pushes traffic through OpenDNS so the endpoint is always secured. Mobile devices such as iOS devices can download a VPN configuration so they are always protected via always sending traffic through OpenDNS. The next screenshot shows the welcome dashboard for adding protection to roaming and iOS devices.
To protect endpoints such as laptops and iOS mobile devices regardless of what network they are on, you can upgrade to a Umbrella account that has a cost per endpoint. This option provides more features and gives the option to distribute agents to endpoints. This means the agent pushes traffic through OpenDNS so the endpoint is always secured. Mobile devices such as iOS devices can download a VPN configuration so they are always protected via always sending traffic through OpenDNS. The next screenshot shows the welcome dashboard for adding protection to roaming and iOS devices.
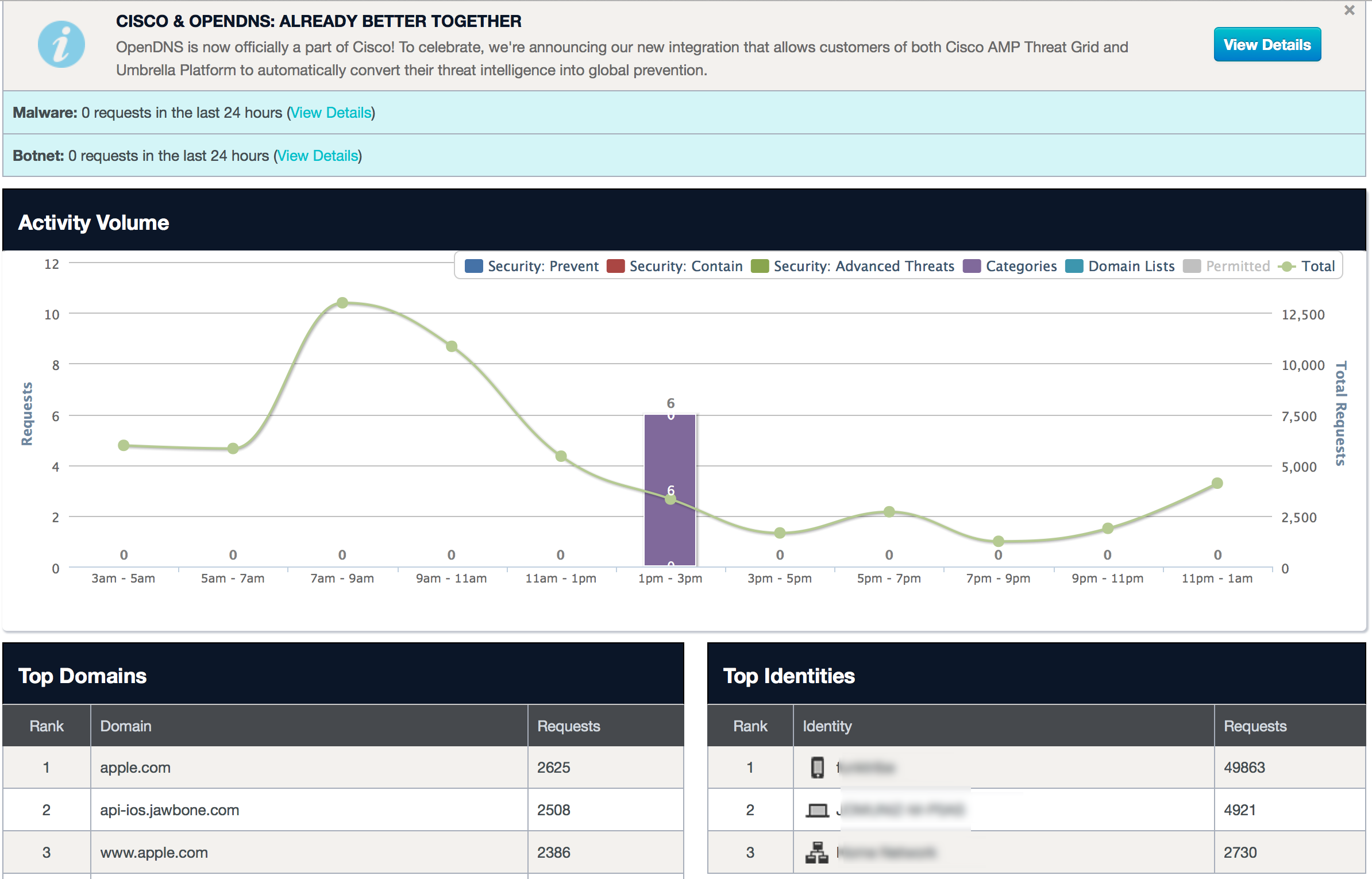
 I already had my home network protected using the free account so I went ahead and added OpenDNS to a laptop and iPhone. After a few minutes, I had a nice dashboard showing web usage as shown next. The dashboard for umbrella seems to have more details than what comes with the free version.
I already had my home network protected using the free account so I went ahead and added OpenDNS to a laptop and iPhone. After a few minutes, I had a nice dashboard showing web usage as shown next. The dashboard for umbrella seems to have more details than what comes with the free version.
Notice that there is a information message stating the Cisco has already combined the OpenDNS research with ThreatGrid malware research.
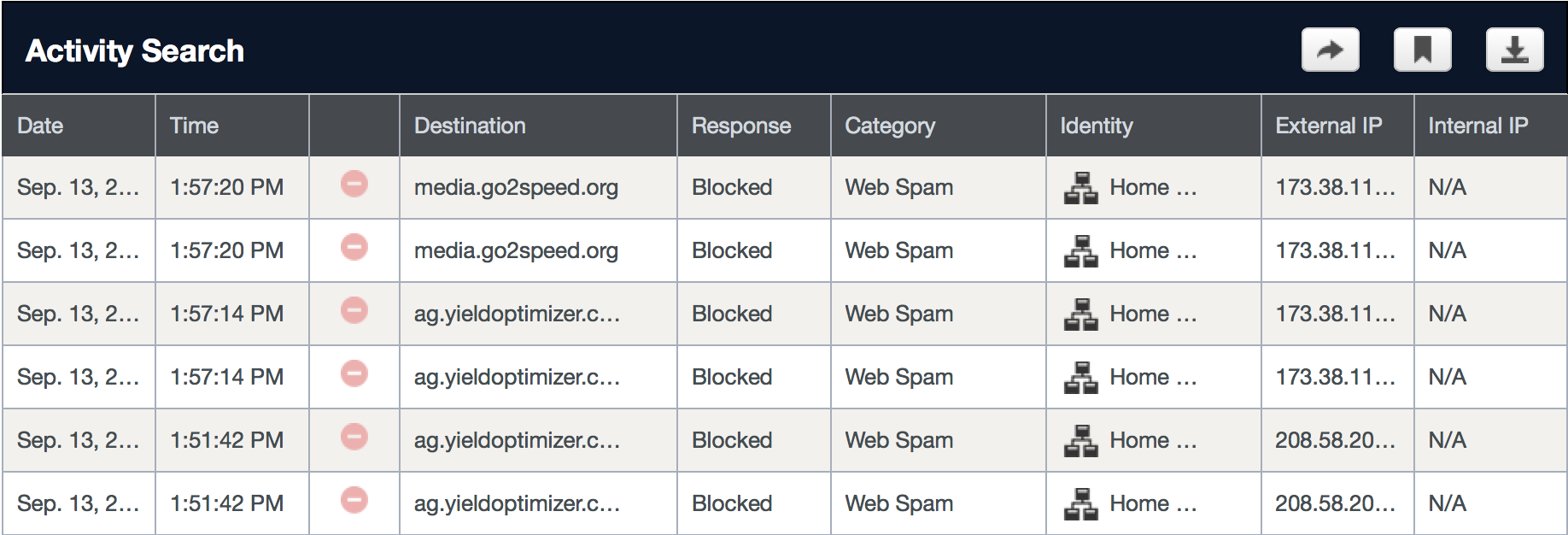
 If I click the block categories, I see a few web spam entries that were blocked as shown.
If I click the block categories, I see a few web spam entries that were blocked as shown.
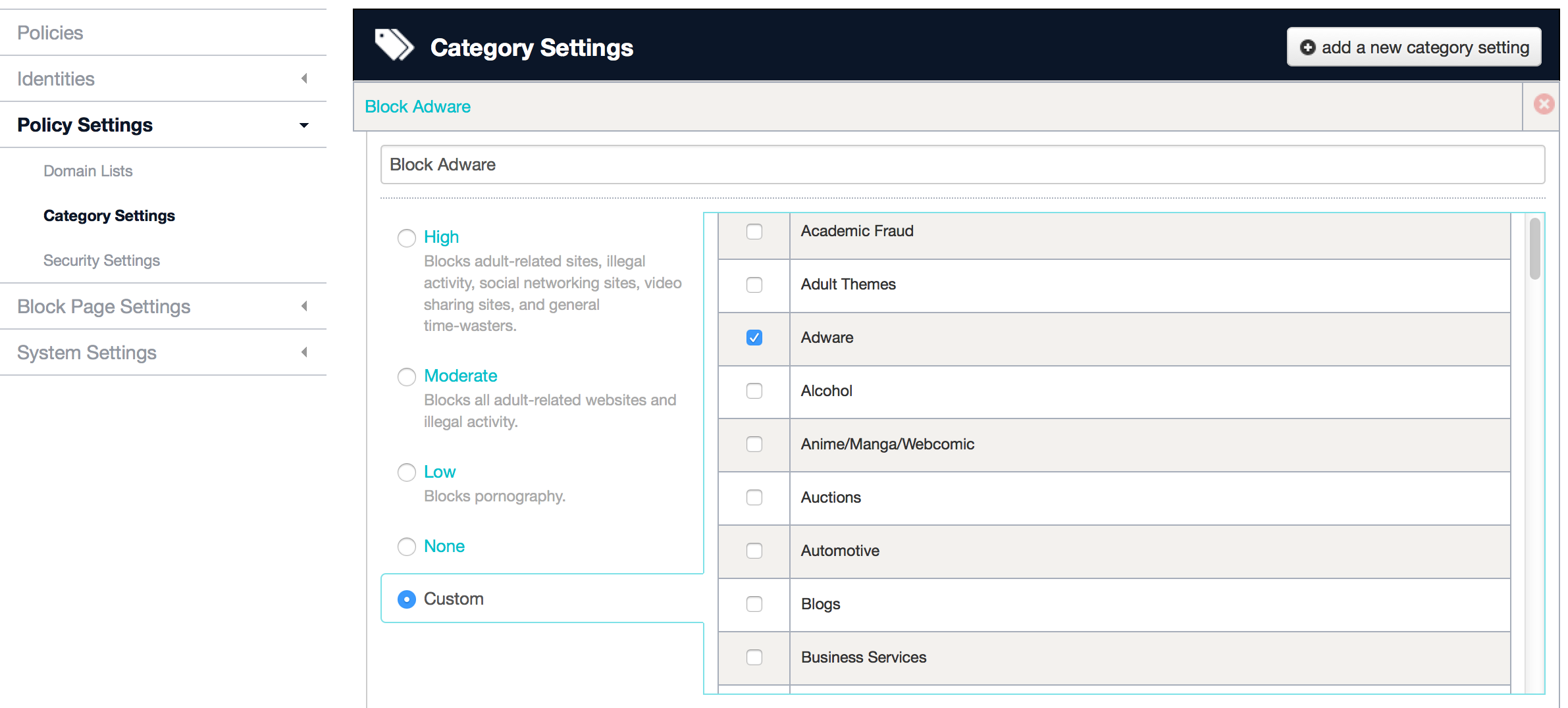
 This was created when I selected to block adware and web spam. The next screenshot shows creating a content filtering policy and choosing Adware. There are the usual filtering categories such as hate, gambling, adult, etc available.
This was created when I selected to block adware and web spam. The next screenshot shows creating a content filtering policy and choosing Adware. There are the usual filtering categories such as hate, gambling, adult, etc available.
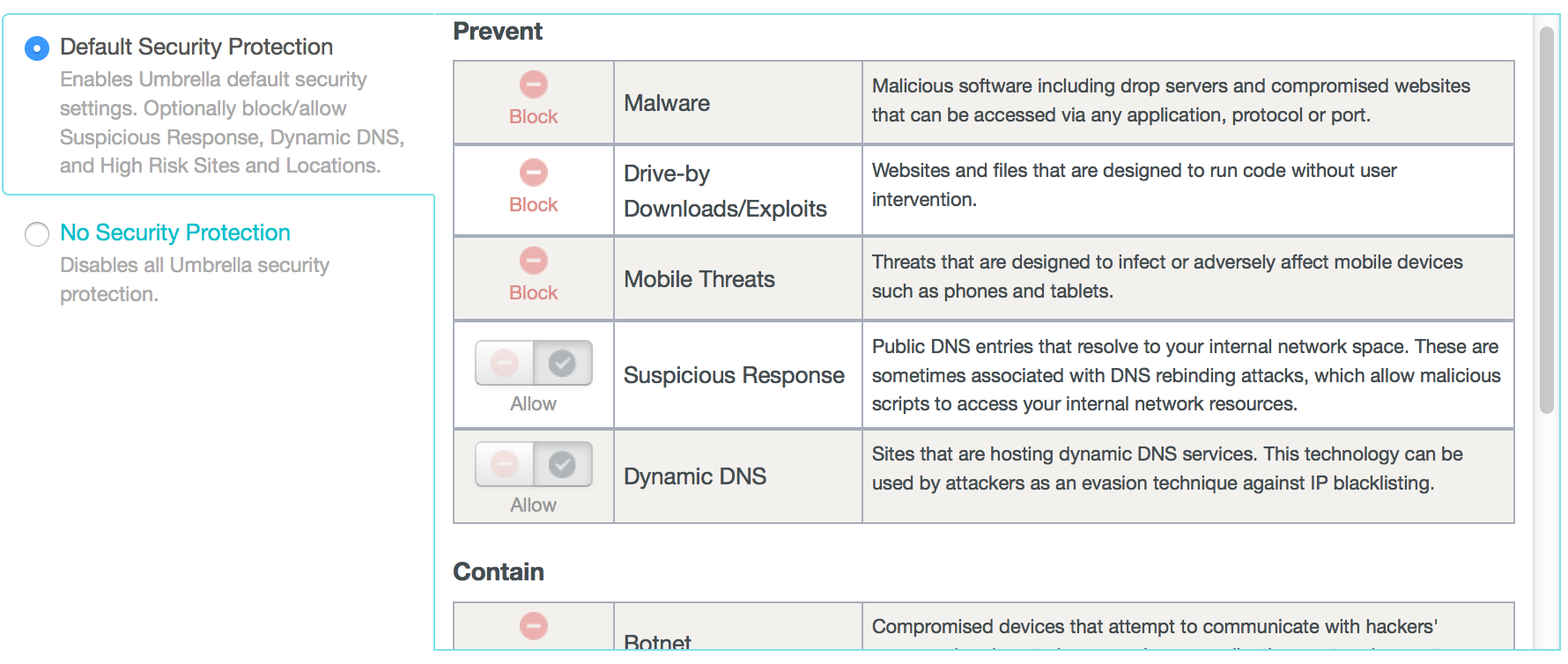
 The next tab is for enabling security defenses. There are a bunch of options that range from malware to botnets. The next screenshot shows the top part from a list of different options.
The next tab is for enabling security defenses. There are a bunch of options that range from malware to botnets. The next screenshot shows the top part from a list of different options.
 I can click the cloud activity tab to see the types of websites I’ve been visiting. The details are pretty good once I click into one to see more.
I can click the cloud activity tab to see the types of websites I’ve been visiting. The details are pretty good once I click into one to see more. 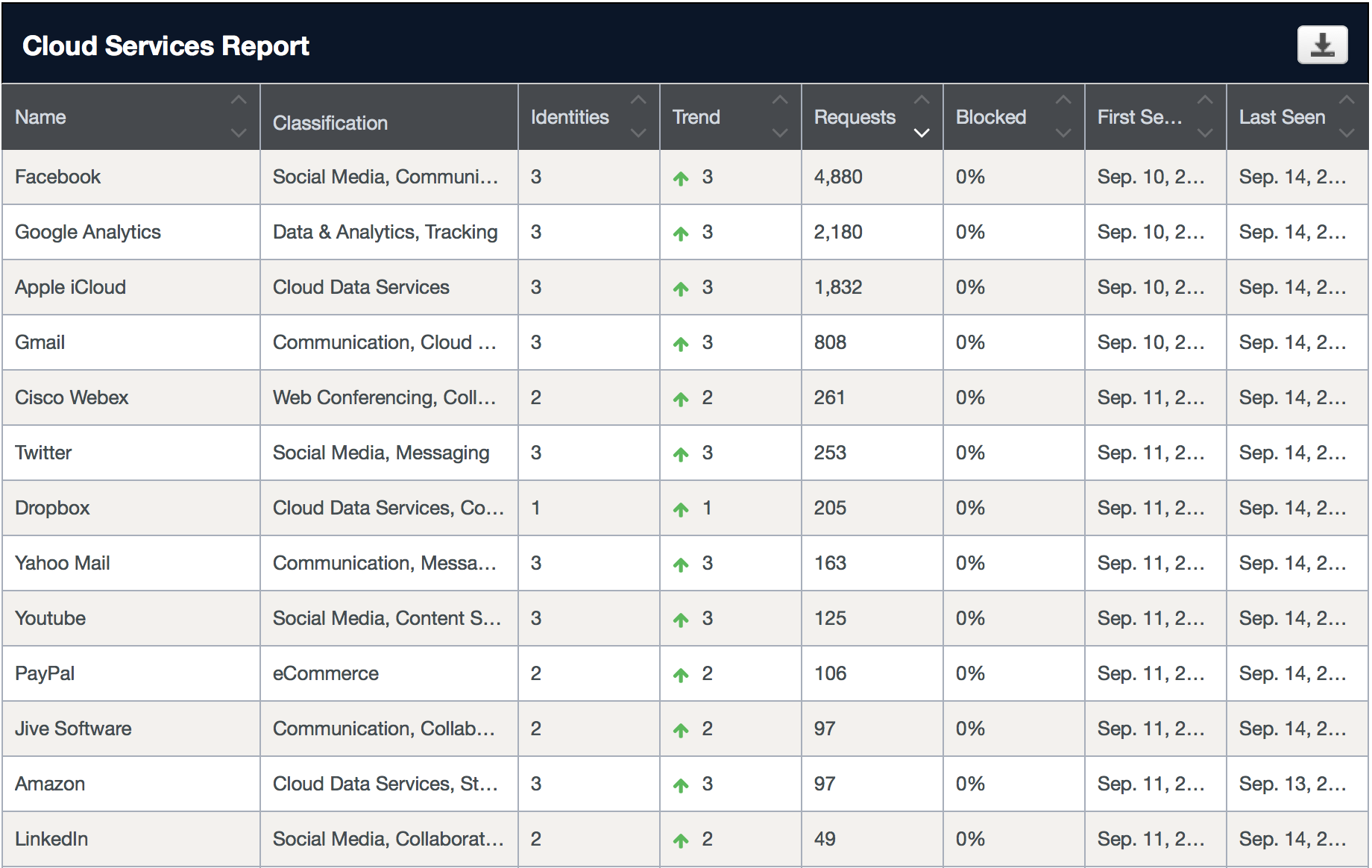 I can investigate websites under the Investigate tab. Here is the traffic seen from thesecurityblogger.com. Details on the search include whois data, DGA detection, a score if its consider a risk, etc. This is helpful for understanding why OpenDNS would block or permit a website.
I can investigate websites under the Investigate tab. Here is the traffic seen from thesecurityblogger.com. Details on the search include whois data, DGA detection, a score if its consider a risk, etc. This is helpful for understanding why OpenDNS would block or permit a website. 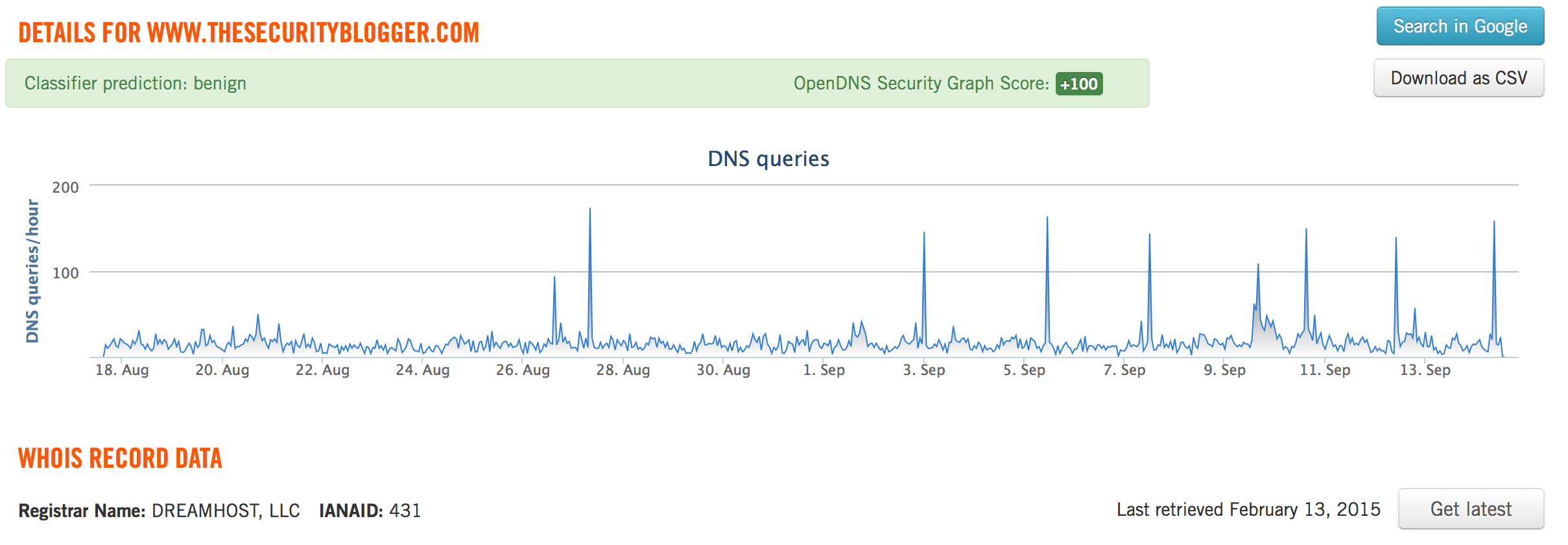 This is a general overview as I’m new at using Umbrella. OpenDNS also offers a more advanced Investigation license as well as threat feed for those looking for more enhanced security options. My opinion is there may be more feature rich cloud security options out there however this is by far the easiest to enable and get immediate value. Plus the free offering should be a no brainer for anybody looking to improve their home network defenses or need to filter content such as making the home network “kid friendly”.
This is a general overview as I’m new at using Umbrella. OpenDNS also offers a more advanced Investigation license as well as threat feed for those looking for more enhanced security options. My opinion is there may be more feature rich cloud security options out there however this is by far the easiest to enable and get immediate value. Plus the free offering should be a no brainer for anybody looking to improve their home network defenses or need to filter content such as making the home network “kid friendly”.
I’m excited to see how this technology is blended into the Cisco security catalog similar to how they spread ThreatGRID and AMP features into other products along with combining research efforts.




