My buddy Aamir Lakahni wrote a cool post on how to setup a njRAT (remote access toolkit). The original post can be found at drchaos.com via HERE.
Warning: The ideas, concepts and opinions expressed in this blog are intended to be used for educational purposes only. The misuse of the information from this article can result in criminal charges brought against the persons in question. Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.
One of the most popular malware tools being used today is a RAT (remote access toolkit) named njRAT.
The malware is extremely popular in the Middle East, with the Syrian Electronic Army, and other hacker groups. There are YouTube Videos on how to use it, and the malware C&C (command and control) server can be found relatively easily. Be careful, a quick Google search for njRAT found that most versions contained a backdoor.
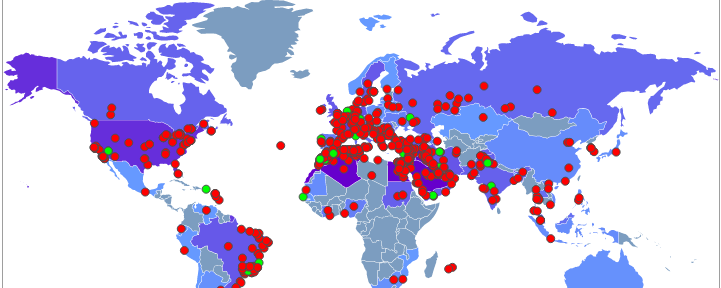
A quick look at the map below shows the active C&C command and control servers detected. Each one of these dots may have hundreds of compromised clients connecting back to them.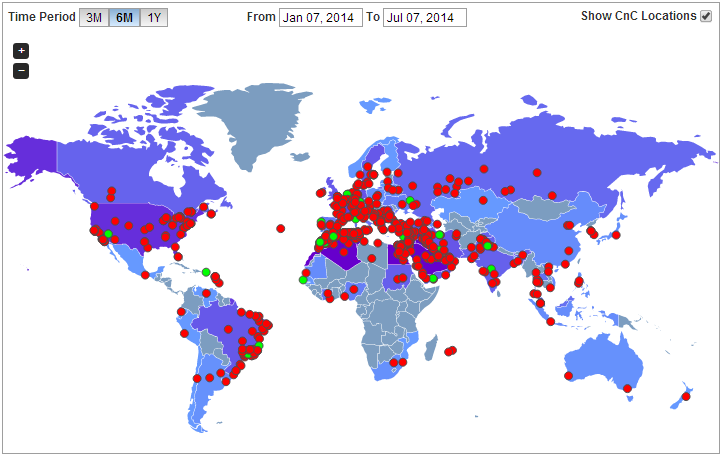
For testing purposes we obtained a copy of njRAT (download at your own risk, it may have backdoors). When you launch the command and control server, you are presented with the main control screen.
This RAT is coded using the Microsoft .Net framework and can remotely access a victim’s machine, operate the webcam, log keystrokes, steal credentials stored in browsers, upload and download files, and update itself. The malware has a GUI-based builder and controller tool that allows its users to create malicious binaries and remotely control all infected machines.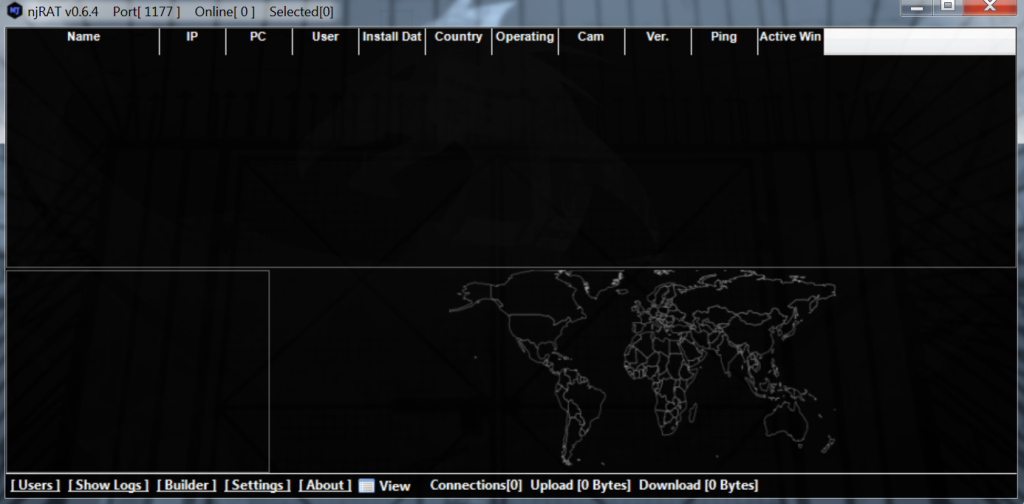
To build the malware from the command and control server, click on the builder menu option.
The builder will give attackers different options on how persistent they would like to create the malware. It has a few other options as well:
1: IP Address – This is the IP address that the victim machine will connect back to the C&C server. By default the C&C server listens on TCP port 1177, so an attacker will need to have that port open.
The IP address will be the address the victim connects to, so in many cases this will be the NAT address. The default port can be changed.
2: Victim name: You can have a unique name for each executable. In reality, most attackers will mass spread their executable (unless it is a targeted attack) and do not bother with individual names.
3: Name: – This will be the name of the executable dropper on the victim’s machine
4: Additional options: Where do you want to store it, and how persistent you want to make it. If you look at the options in the screen shot below, you will notice we are only storing a single executable in the tmp directory. This will make it easier to remove the malware after our research.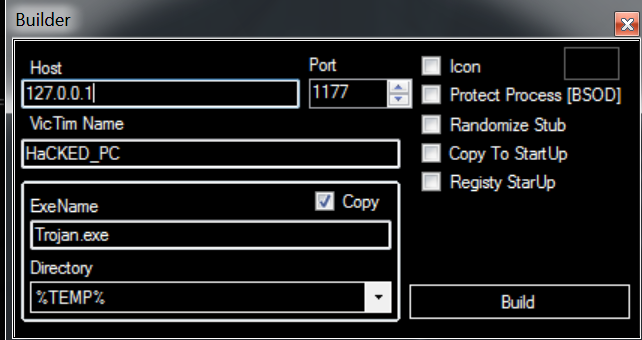
Once the builder app is complete, it will create an executable file. The goal for most attackers is to get the executable file onto the victim’s machine. In this case njRAT is an extremely well documented for it’s malicious activities so basic anti-virus should stop the file from running on the victim’s machine.
We can see when we take the executable that njRAT made, it is being detected by a large number of AV manufactures. You can see from the screen shot below 43 out of 56 AV manufactures detected this as malicious code.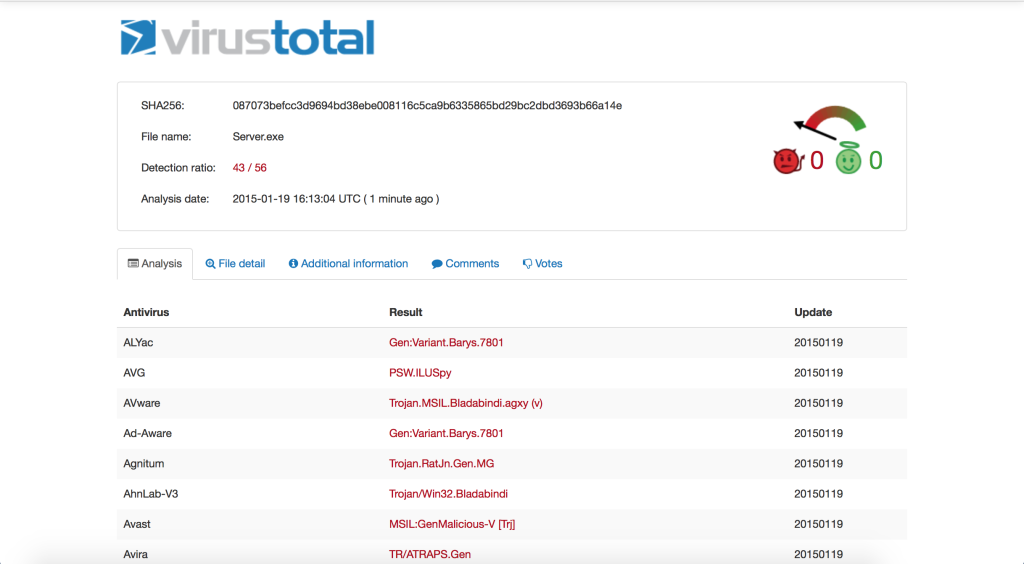
Many attackers will attempt to obfuscate their malware by using encryptors. When we ran the executable njRAT created thru an encryptor tool called exeStealth you can see the file significantly changed. Below is the original md5 checksum of what njRAT created and the modified checksum after running it thru exeStealth.
Please note: encryptors by themselves are not necessarily malicious and having them does not mean you are planning on using or distributing malware. There are legitimate uses for encryptors. Additionally, sometimes encryptors are used by attackers to obfuscate their malware.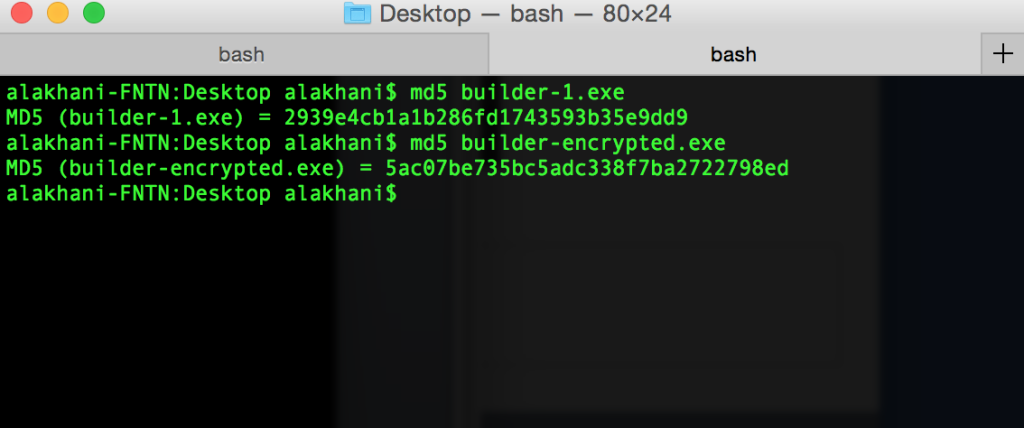 When we run the encrypted file thru Virus Total, you can see there are now quite a few more AV engines that do not detect the encrypted file. 22 out of 57 AV vendors have detected the file as malicious when it is encrypted (versus 46 before it was encrypted).
When we run the encrypted file thru Virus Total, you can see there are now quite a few more AV engines that do not detect the encrypted file. 22 out of 57 AV vendors have detected the file as malicious when it is encrypted (versus 46 before it was encrypted).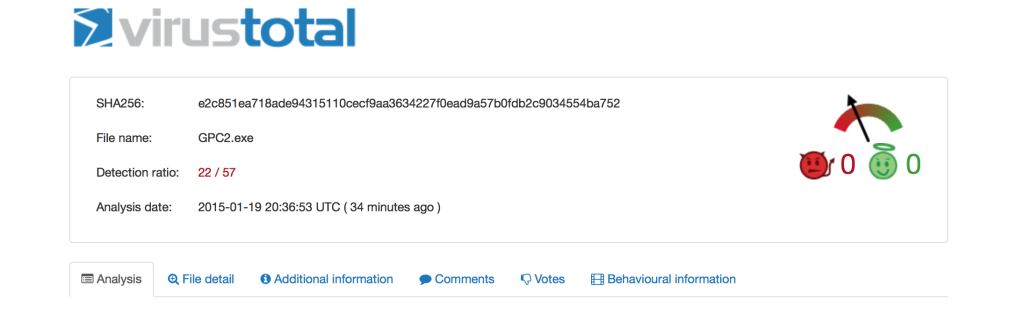 If a victim successfully runs the executable created by njRAT, the attacker will see a connection back on his C&C server.
If a victim successfully runs the executable created by njRAT, the attacker will see a connection back on his C&C server.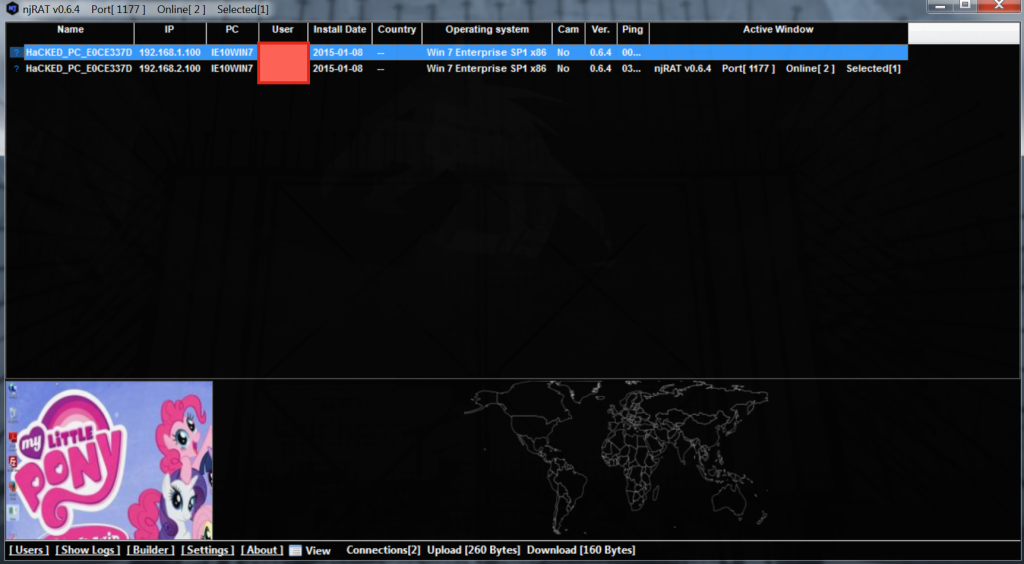 The attacker can see the victim’s desktop (The victim has a nice cartoon as his desktop wallpaper). Furthermore, the attacker has the ability to remote control the victim’s machine, establish access to the PC, transfer files, start a remote chat, and even upgrade the njRAT malware if needed.
The attacker can see the victim’s desktop (The victim has a nice cartoon as his desktop wallpaper). Furthermore, the attacker has the ability to remote control the victim’s machine, establish access to the PC, transfer files, start a remote chat, and even upgrade the njRAT malware if needed.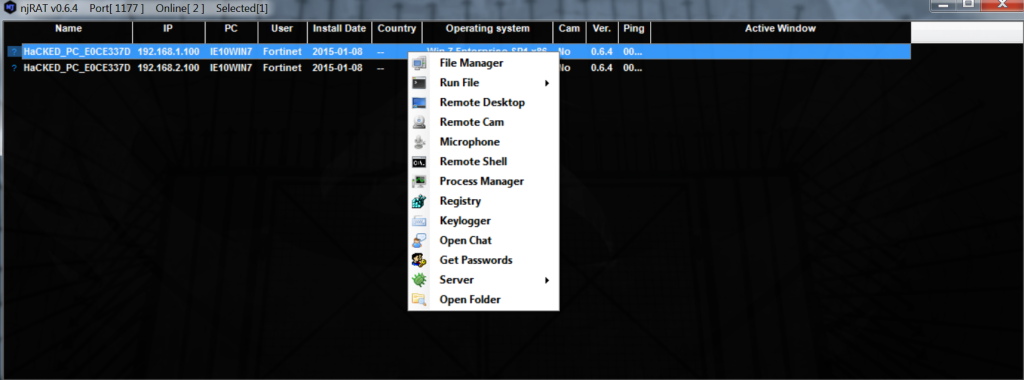 Most attacks, are not this straightforward. Instead of a simple executable, these malware programs are being embedded and packed into legitimate applications, being embedded into documents or PDF-like files, being downloaded thru compromised websites, or users are being tricked into opening them thru social engineering. Furthermore, obfuscation techniques can be much more advanced and complex as well.
Most attacks, are not this straightforward. Instead of a simple executable, these malware programs are being embedded and packed into legitimate applications, being embedded into documents or PDF-like files, being downloaded thru compromised websites, or users are being tricked into opening them thru social engineering. Furthermore, obfuscation techniques can be much more advanced and complex as well.