Bleeping Computer posted about a Microsoft vulnerability via NTLM authentication protocol. The original post can be found HERE.
Two security vulnerabilities in Microsoft’s NTLM authentication protocol allow attackers to bypass the MIC (Message Integrity Code) protection and downgrade NTLM security features leading to full domain compromise.
Microsoft patched the two NTLM flaws and issued security advisories as part of the Patch Tuesday security updates issued yesterday after Preempt’s disclosure.
Preempt researchers Yaron Zinar and Marina Simakov discovered that attackers can exploit these flaws as part of NTLM relay attacks that may, in some cases, “cause full domain compromise of a network,” with all Active Directory customers with default configurations being exposed.
The Windows NT (New Technology) LAN Manager (NTLM) authentication protocol is used for client/server authentication purposes to authenticate remote users, as well as to provide session security when requested by app protocols.
NTLM is superseded by Kerberos, now the default auth protocol for domain connected devices for all Windows versions above Windows 2000.
“Despite Kerberos being the more prevalent authentication protocol in most organizations, NTLM is still enabled and thus abused by attackers to exploit the vulnerabilities that we have described above,” adds the Preempt advisory.
Tampering vulnerability impacts all in-support Windows versions
Preempt’s research team was able to find flaws that could be abused by potential attackers to circumvent NTLM relay attack mitigations provided by Microsoft.
While Microsoft added a Message Integrity Code (MIC) field to block attackers from tampering with NTLM messages, Preempt’s researchers found a bypass on NTLM authentication that allows attackers to “modify any field in the NTLM message flow, including the signing requirement.”
“This bypass allows attackers to relay authentication attempts which have successfully negotiated signing to another server, while tricking the server to entirely ignore the signing requirement.”
The NTLM tampering vulnerability that leads to this bypass is tracked as CVE-2019-1166 (dubbed Drop The MIC 2 by Preempt) and was, as mentioned above, patched yesterday by Microsoft as part of October’s Patch Tuesday.
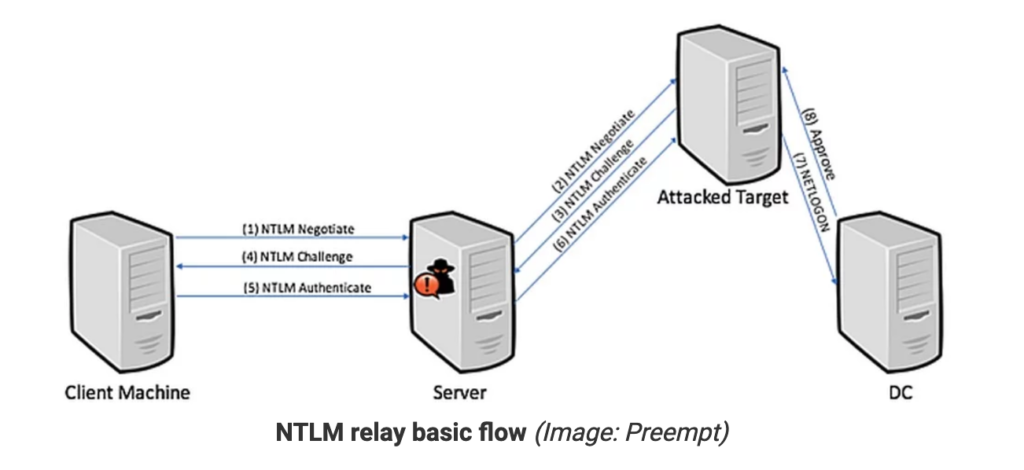
NTLM relay basic flow (Image: Preempt)
CVE-2019-1166 impacts all in-support Windows versions, with all servers that do not enforce signing being vulnerable to
“A tampering vulnerability exists in Microsoft Windows when a man-in-the-middle attacker is able to successfully bypass the NTLM MIC (Message Integrity Check) protection,” says Microsoft’s advisory. “An attacker who successfully exploited this vulnerability could gain the ability to downgrade NTLM security features.”
Second flaw impacts clients sending LMv2 responses
The second flaw discovered by Preempt also circumvents the MIC protection against NTLM relay attacks, as well as other NTLM relay mitigations including but not limited to “Enhanced Protection for Authentication (EPA) and target SPN validation for certain old NTLM clients that are sending LMv2 challenge responses.”
The Windows NTLM security feature bypass vulnerability is tracked as CVE-2019-1338 and, just like the first one, was patched by Microsoft as part of this month Patch Tuesday.
Itaffects Windows 7 SP1, Windows 2008, and Windows 2008 R2 devices, and could be used in attacks that enable threat actors “to use NTLM relay to successfully authenticate to critical servers such as OWA and ADFS and steal valuable user data.”
“A security feature bypass vulnerability exists in Microsoft Windows when a man-in-the-middle attacker is able to successfully bypass the NTLMv2 protection if a client is also sending LMv2 responses,” says Microsoft’s security advisory.
“An attacker who successfully exploited this vulnerability could gain the ability to downgrade NTLM security features.”
AD customers with default configs exposed to attacks
To exploit CVE-2019-1166 potential attackers would need to tamper with the NTLM exchange, while attackers attempting to abusing CVE-2019-1338 as part of their attacks would need to be able to modify NTLM traffic exchange.
“All Active Directory customers with default configurations are vulnerable to such attacks,” added the Preempt researchers.
“Moreover, organizations that do not block LM responses and have clients who still send these default responses are vulnerable to targeted attacks on these clients to bypass additional NTLM protections”
More technical details and background information on the two NTLM flaws are available in Preempt’s analysis.
Previous NTLM flaws and protection
This is not the first time Preempt discovered NTLM vulnerabilities, with two critical ones consisting of three logical flaws and allowing attackers to run remote code and authenticate on machines running any Windows version having been fixed by Microsoft as part of June’s Patch Tuesday security updates.
Previously, Preempt disclosed another flaw impacting all in-support Windows version at the time, fixed by Microsoft during July 2017 Patch Tuesday and enabling attackers to create admin accounts on a local network’s domain controller (DC).
Preempt’s research team provides the following recommendations to protect networks with devices impacted by these vulnerabilities:
•
Enforce NTLM mitigations. In order to be fully protected from NTLM
relay attacks you will need to enable server signing and EPA on all
relevant servers.
• Patch! Make sure your systems are fully protected with the latest security updates.
• Apply advanced NTLM relay detection and prevention techniques similar
to the ones disclosed by Preempt in our Black Hat 2019 talk (a free encore presentation can be found here).
• Some NTLM clients use weak NTLM variations (e.g., don’t send a MIC).
This puts your network at a greater risk of being vulnerable to NTLM
relay. Monitor NTLM traffic in your network and try to restrict insecure
NTLM traffic.
• Get rid of clients sending LM responses and set the GPO Network
security: LAN Manager authentication level to refuse LM responses.
• NTLM is not recommended to use in general as it poses some security
concerns:NTLM relay, brute forcing, and other vulnerabilities. You can
read about general NTLM risks here. As a rule of thumb: try to reduce NTLM usage in your network as much as possible.
“Even though NTLM Relay is an old technique, enterprises cannot completely eliminate the use of the protocol as it will break many applications,” said Preempt’s Chief Technology Officer and Co-Founder Roman Blachman in June.
“Hence it still poses a significant risk to enterprises, especially with new vulnerabilities discovered constantly.”




