This post will provide a short overview of Microsoft’s answer to the SIEM / SOAR / XDR capabilities that’s needed within any security operation center (SOC). For those not familiar with the terminology, here is a quick summary.
Security Information and Event Management (SIEM) – Centralized place to view security event data from multiple sources (Antivirus, IPS, etc.). Many SIEMs act as a log repository often referred to as a “data lake”, which means other tools send data or “logs” to the SIEM to digest. This is a traditional SIEM that receives logs and allows SOC admins to search the data received for datapoints of interest. Some SIEM like tools do not receive logs but instead, use APIs to continuously reference the data sources for data of interest. For example, a SOC admin wants to know about an endpoint security product’s view of an incident. A data lake SIEM would have the logs to view while an API SIEM would have to query the endpoint security tool’s database to ask what it has seen. SIEMs can read data from many different sources and only as useful as the data it collects as well as how that data is used.
Security Orchestration, Automation and Response (SOAR) – SIEMs lack the ability to take action on events hence require humans to respond to incidents. The SOAR market was created to address this need by adding ways to automate mundane tasks, track responses with workbooks, track time saved and essentially improve how a SOC uses a SIEM.
Extended Detection and Response (XDR) – Endpoint detection and response (EDR) is a endpoint focused SIEM SOAR solution. You have endpoint security tools that protect endpoints and a centralized dashboard that can do both SIEM and SOAR activities. XDR represents moving beyond the endpoint hence creating the outcome of a SIEM and SOAR for all security tools. XDR is not a product, but a outcome most SOCs look to achieve as they invest in SIEM/SOAR capabilities.
There are many SIEM and SOAR options out there from free open-source options to vendor solutions that typically charge based on events managed, but not always. Industry leaders that are popular within modern SOCs include Splunk (SIEM) / Splunk Phantom (SOAR), IBM QRadar (SIEM)/ IBM Resilience (SOAR), Log rhythm and Microsoft Sentinel. What separates industry leaders from other options is the following.
- Ability to support multiple data types / sources
- Ability to support cross vendor technologies
- Ability to automate most tedious tasks
- Ability to improve a SOC’s services such as incident response, threat hunting, case management, etc.
Some solutions are better at specific things such as mining data while others are better at automating tasks. What is key though is support for your business goals. If you have multiple security, network and cloud technologies within your environment, you should expect your XDR solution to easily be able to support those solutions. If the vendor only supports their own technology, then you essentially are reverting backwards since you are not centralizing security management. The next image shows Microsoft Sentinel connection section representing content type from different sources. The Data connector section not shown lists over hundred vendor tools to connect to including Cisco, Crowdstrike, Checkpoint and so on.
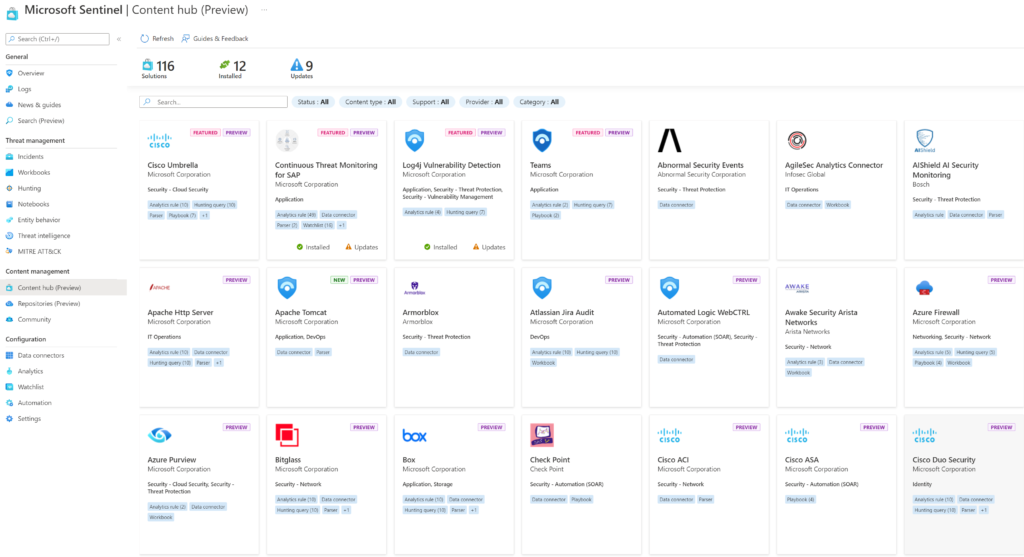
Microsoft Sentinel First Look
Now with all of the introduction concepts out of the way, let’s take a look at Microsoft Sentinel. When you log into a configured system, you first have a dashboard highlighting what is happening with the environment.
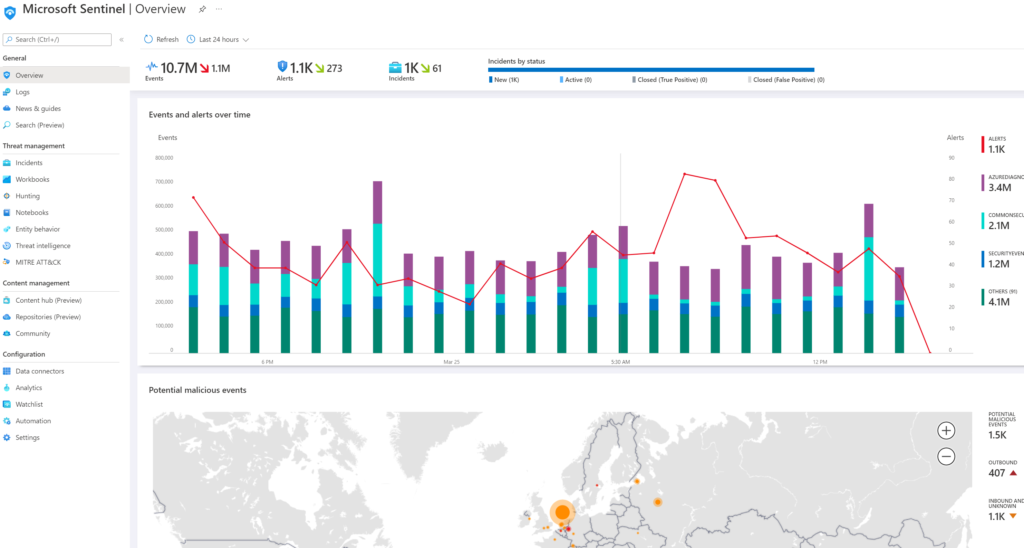
This dashboard gives you an idea of the most recent events that are occurring, where they are occurring and how many cases are open, closed, or InProgress. It is essentially a SIEM/SOAR dashboard giving you an idea of what is being worked on and where to focus your next effort.
Another good place to get a first look at what is going on is the News and Guides area. For example, many administrators are concerned about Log4j vulnerability detection. As new detection is created for recent threats or best practices, guidance is posted here. Recommendations can include new threat hunting techniques and tactics (TTPs) to look for, new vulnerabilities, etc.
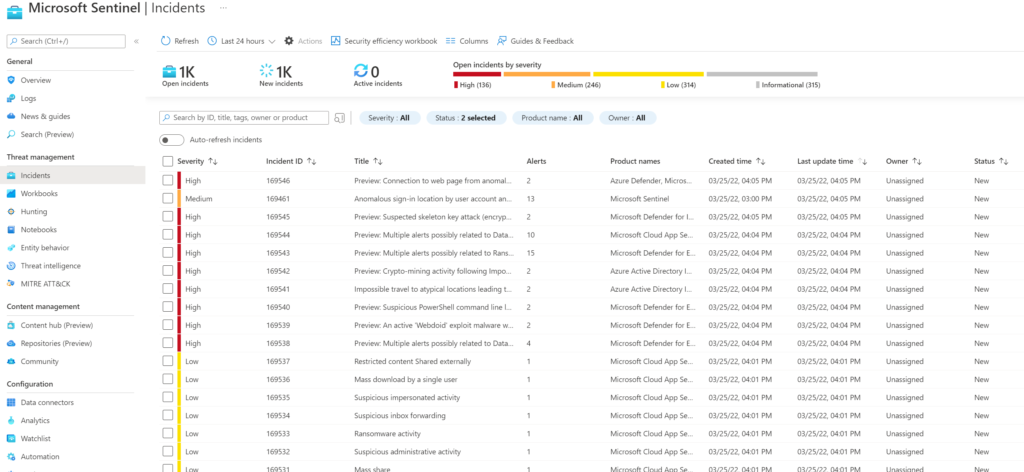
If you are interested in what threats are occurring, the Incidents dashboard summarizes all incidents and groups them into severity categories. You can quickly determine if something needs to be investigated now as well as if it has been assigned to an analyst. Clicking an assignment will pull up what has been done by those assigned to the case.
Workbooks represent possible automated tasks such as responding to incidents or looking into something. Microsoft offers tons of templates, which can be adjusted to fit your situation and saved as your own workbook. Let’s say you want to investigate an Amazon Network environment for activities related to the creation, update and deletion of security groups based on the risk that an attacker has breached that environment. There is a workbook template that scripts out this investigation so you simply run the AWS Network Activities workbook rather than manually spending time clicking through your AWS management dashboard. Workbooks can also be created after responding to a incident to improve speed and expected outcomes when responding to specific incident type.
Responding to incidents is important for an XDR solution however, a modern and effective SOC can’t sit back and wait for attacks to occur aka only be “reactive”. Being proactive sounds great but how do you know what to hunt for? Where do you start your investigation? Do you just randomly search for …. stuff??? What is cool about Sentinel is it has a dedicated section to proactive threat hunting. You can look across a threat model that starts with recon and works through common steps of an attack such as exfiltration behavior. Within each step are threat hunting scripts to see if activity exists within your environment. For example, there is a script to identify when multiple password resets were created by a user. You would hope the native application or other security tools would pick up on this however, it is best to check for this behavior across all tools using automation found within Sentinel. For a general proactive threat hunt, you can select one or more categories and run all of the various checks to see if threats may exist within your environment that have not been detected by your security tools.
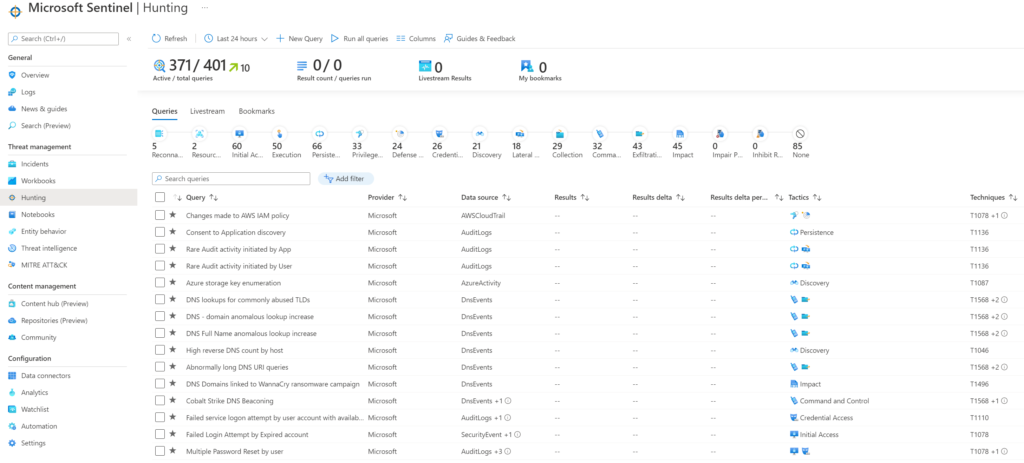
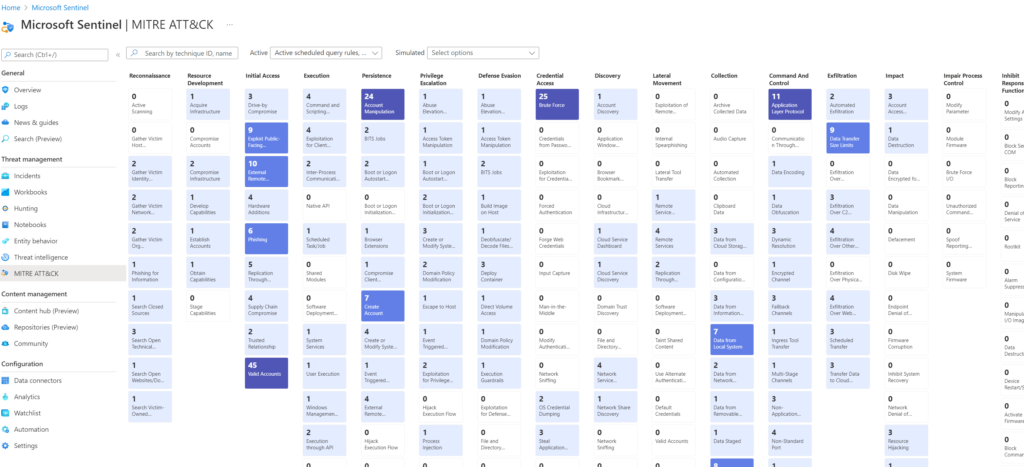
Another industry respected flavor of viewing potential threats is using MITRE ATT&CK. Think of this approach as applying detailed threat modeling against your environment. Sentinel has this work done for you meaning you can literally pull up the MITRE ATT&CK model and compare it against your environment as shown.
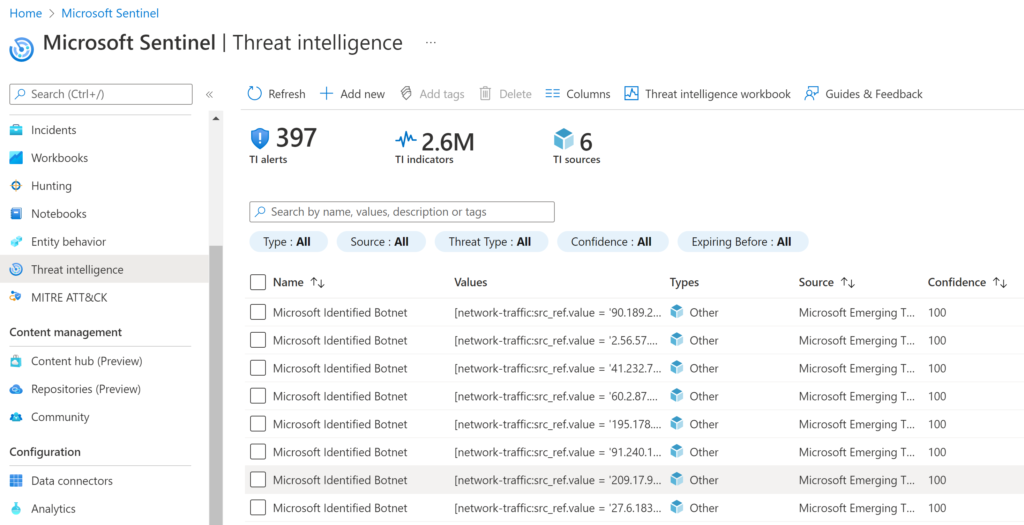
Another common area of interest for XDR is leveraging threat intelligence. It’s good to baseline your environment and look for threats however, it’s better to learn from outside your organization. This requires a way to receive threat intelligence and apply it against what you know about your environment. Sentinel allows you to add external threat intelligence via files, IPs, URLs, etc. and filter out what doesn’t apply to your environment. It is not recommended to dump unfiltered threat intelligence into any XDR solution as that could actually provide more noise than value.
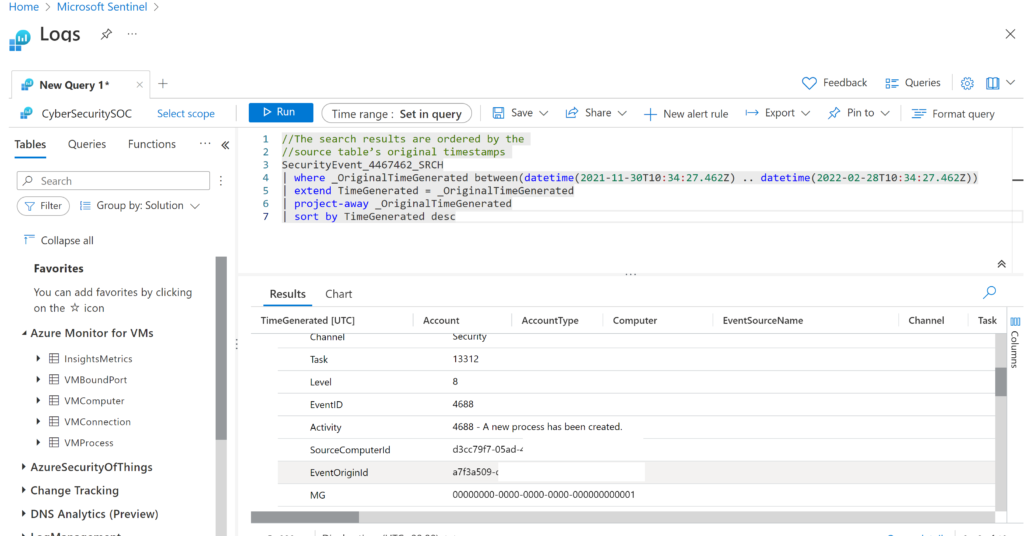
Lastly, an important and expected feature of an XDR is the ability to quickly search for data of interest. Microsoft Sentinel has different ways to do this. My favorite is starting with a basic search filtering on what I know about what I’m looking for. If it is a threat type, I can simply search for terms like dataloss or exfiltration. I can include the IP address of an endpoint tool if my interest in searching only endpoints for those key terms hence searching is using typical AND OR NOT logic. The end results allows you to pull up details found within logs such as MAC addresses, timestamps, reasoning for alerts and so on.
That is a super quick overview of Microsoft Sentinel. Most organizations should have an investment in XDR but if you are one that doesn’t, go to Azure Sentinel – Cloud-native SIEM Solution | Microsoft Azure and turn on Sentinel now. You get 30 days free to light it up and feed it data. You literally can have a SIEM within a few hours and do some threat hunting to see if threat actors have possibly compromised your environment (assuming you have security tools to feed Sentinel. If not, consider turning on Microsoft Sentinel and Microsoft Defender for 30 days). For those with existing XDR solutions, consider how much value you are getting from it verse what Microsoft could do for you. Within a few hours, you could have a side-by-side comparison between your existing XDR solution and Sentinel to see which provides your SOC more value.
The next lab 101 I’ll write up this week will be a first look at a IoT / OT security solution known as Defender for IoT.