There has been a lot of chatter about a new ransomware being called Locky due to how it renames the files to .locky after encrypting the data. Darkreading posted an article HERE explaining some recent news and Sophos also did a good write up HERE. This post will talk about what Locky is and how to protect your organization from Locky as well as other ransomware.
For those not familiar with Ransomware, HERE is a blog post I wrote that covers the basics. In summary, ransomware is malware that encrypts your computer data and holds it for ransom. It does not destroy the computer or make it unusable. That would not let people be able to go online and pay the ransoms. Ransoms are usually a request in a digital currency known as bitcoins and can range from a few hundred to millions of bit coins. Paying the ransom could get your data back however it also could mean the ransomware has other purposes to continue to take data from the system. Also paying the ransom funds the bad guys so they can get better at it and do it more often. Don’t listen to the FBI … don’t pay the ransom (see THIS post about the FBI’s bad advise).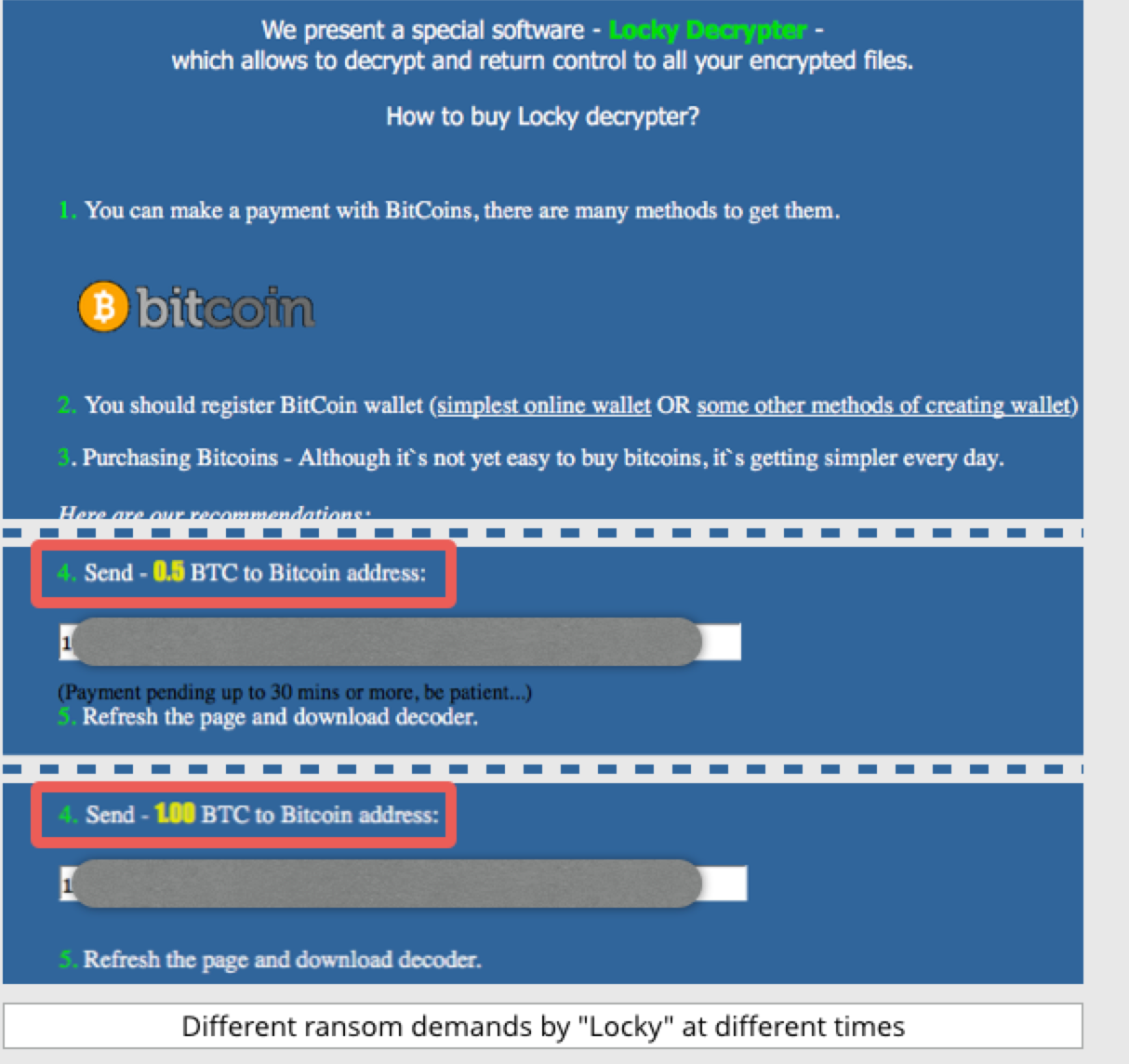
DEFENDING LOCKY
I’ve have had a few customers ask for an IPS SNORT rule to block Locky. IPS typically isn’t designed for this purpose meaning its usually looking for attacks or attempts to exploit a vulnerability rather than the actual malware. Some people think an IPS is a silver bullet and can detect the actual malware. Sorry … this isn’t how the technology works however there are methods using an IPS to detecting the communication to a command and control (C&C) network once you are infected. For example, a SNORT rule to do this is 31299. The problem is this is AFTER you have been owned. Some people who have seen this rule are concerned that it is an older rule. Being older doesn’t mean it isn’t capable at stopping this threat based on detecting the communication. If a rule is not effective, it will end up in the deleted category. If it is relevant, you will see it in the Talos rules. Also note that there are other rules that are more specific however keep in mind the more specific you are, the more likely a different variant of the attack can occur that will not trigger a very specific rule. IPS rules are best when they balance between being generic and specific.
As explained earlier, research shows Locky is typically delivered through email. This means your first defense should be beefing up your email security. Email security should look at various characteristics of the email you receive such as who is sending it (IE reputation of the sender … see THIS blog post for more info), type of files attached, etc.). This does not mean ransomware can’t be delivered another way such as a web link or USB drive however it is less common. Note dedicated email technology is much better at protecting this attack vector than a unified platform that includes email security components.
The best way to target detecting the actual Locky rasomware is using a breach detection client that monitors file behavior. This type of technology looks for the actual Locky malware based on how it acts verses a known signature of Locky, which is what Anti-Virus type technologies use. NOTE this does not mean breach detection technology replaces the value of signature based anti-virus technology. Its best to have both so you look for KNOWN and UNKNOWN threats. If your AV is aware of the variant of Locky, it will block it. If the AV is not aware, the breach detection technology based on behavior will catch it.
An example of how Cisco Talos can help with its breach detection technology is based on how Cisco sees thousands of samples of Locky everyday to help fingerprint behavior patterns. Endpoints and files crossing the network are monitored for these behavior patterns so the infection is caught as soon as it starts acting outside the normal behavior of the file it suppose to be (example a PDF starting to modify system files). Also behavior patterns echo into rules that block domains and IPs associated with reputation feeds (IE this is how C&Cs get blacklisted) as well as help with developing IPS signatures looking for the call backs to prevent the malware from reaching out once the system is infected. Learn more about Cisco AMP HERE.
In summary, Locky is typically a email delivered ransomware. This means the best way to protect against it is having a solid email security solution, reputation security that monitors for external threats sending email, breach detection technology looking for locky being delivered to a endpoint and IPS rules that defend against various attacks that could deliver Locky as well as the phone home C&C communication from Locky once a system is infected.
Hopefully this helps with preparing to defend against this and other threats.




Here are some more SNORT rules (1:37835, 1:37834) for Locky