Wow just this week I posted about the largest DDoS take down using IoT devices. Now there is a even larger one covered by hothardware.com HERE. This one is seeing close to 1Tbps of data! Pretty much any website online would go down if this was aimed at them. Please be nice to my blog … I’m just a guy with a website … now to the article.
If you thought that the massive DDoS attack earlier this month on Brian Krebs’ security blog was record-breaking, take a look at what just happened to France-based hosting provider OVH. OVH was the victim of a wide-scale DDoS attack that was carried via network of over 152,000 IoT devices.
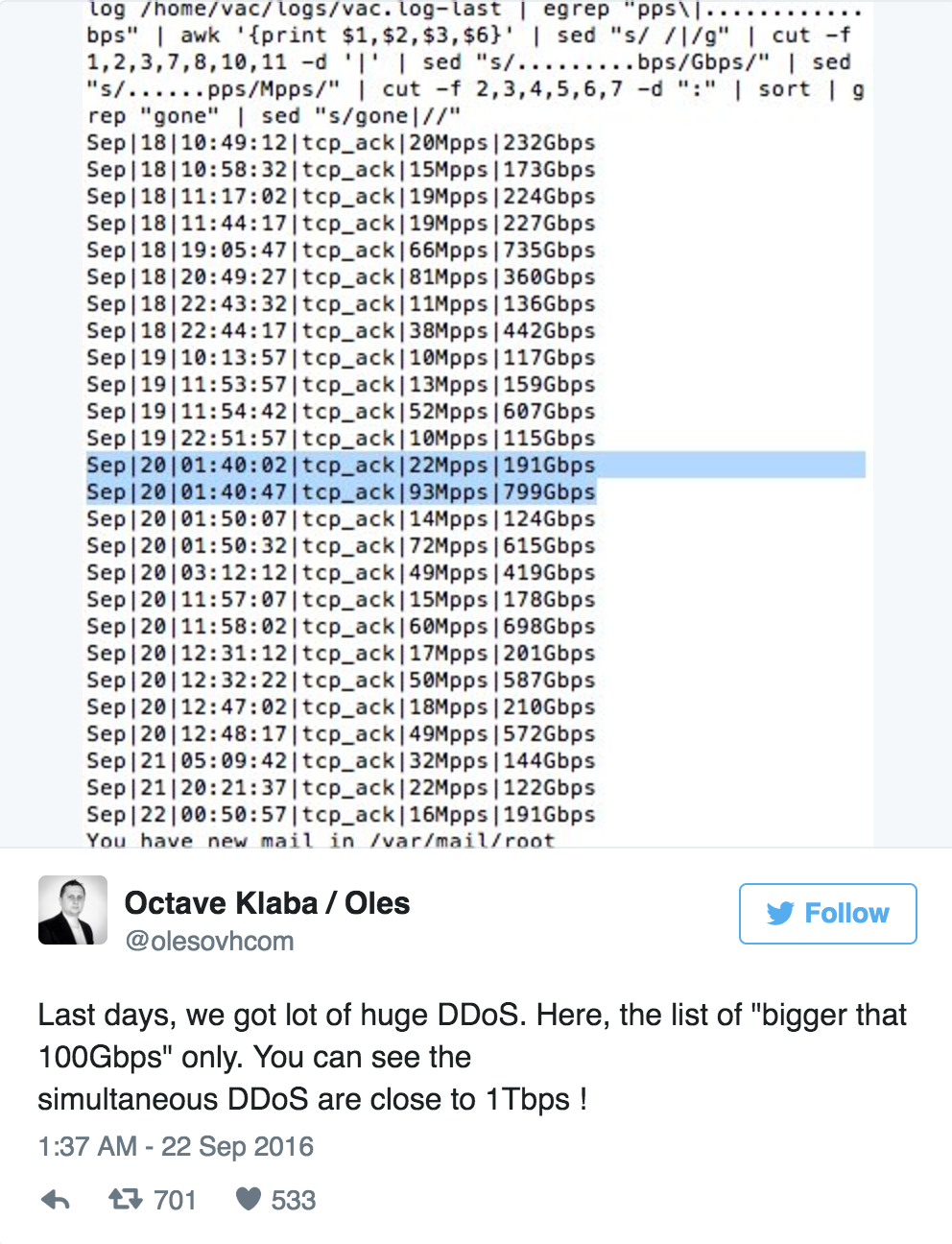
According to OVH founder and CTO Octave Klaba, the DDoS attack reached nearly 1 Tbps at its peak. Of those IoT devices participating in the DDoS attack, they were primarily comprised of CCTV cameras and DVRs. Many of these types devices’ network settings are improperly configured, which leaves them ripe for the picking for hackers that would love to use them to carry our destructive attacks.
 Klaba originally stated that 145,607 devices made up the botnet, but recently confirmed that another 6,857 cameras joined in on the attack. The DDoS peaked at 990 Gbps on September 20th thanks to two concurrent attacks, and according to Klaba, the original botnet was capable of a 1.5 Tbps DDoS attack if each IP topped out at 30 Mbps.
Klaba originally stated that 145,607 devices made up the botnet, but recently confirmed that another 6,857 cameras joined in on the attack. The DDoS peaked at 990 Gbps on September 20th thanks to two concurrent attacks, and according to Klaba, the original botnet was capable of a 1.5 Tbps DDoS attack if each IP topped out at 30 Mbps.
 And to think this massive DDoS campaign was directed at Minecraft servers that OHV was hosting.
And to think this massive DDoS campaign was directed at Minecraft servers that OHV was hosting.
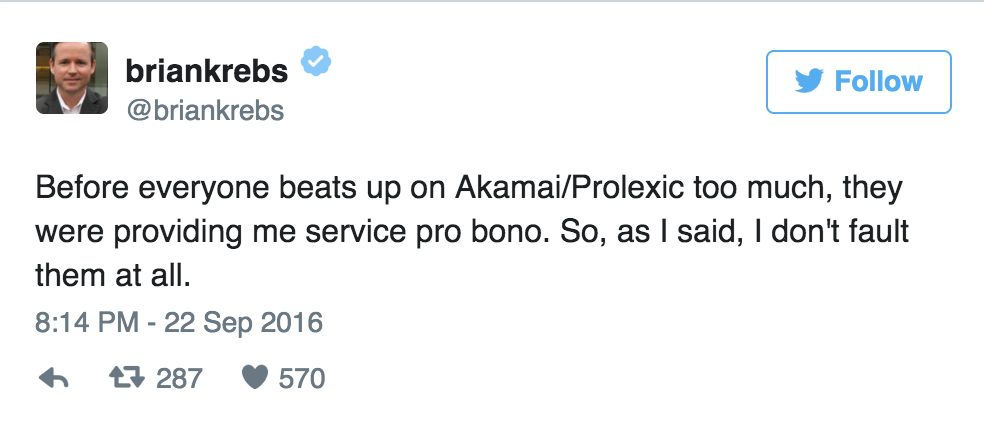
The DDoS attack witnessed by KrebsOnSecurity peaked at 620 Gbps, and was destructive enough to cause Brian Krebs’ hosting company, Akamai, to drop him with only two hours’ notice. Krebs is thought to have been attacked due to his part in taking down the Israeli firm vDOS, which profits from initiating DDoS attacks on websites.
As for Akamai’s decision to give KrebsOnSecurity its walking papers, Krebs himself harnessed no ill will towards the company:
 With that being said, there’s a reason why many IoT devices become mindless zombies in global DDoS campaigns. “Most IoT malware targets non-PC embedded devices. Many are Internet-accessible but, because of their operating system and processing power limitations, they may not include any advanced security features,” wrote Symantec in a blog posting.
With that being said, there’s a reason why many IoT devices become mindless zombies in global DDoS campaigns. “Most IoT malware targets non-PC embedded devices. Many are Internet-accessible but, because of their operating system and processing power limitations, they may not include any advanced security features,” wrote Symantec in a blog posting.
Symantec went on to provide a number of steps that you can take to protect your IoT device from being compromised by nefarious parties. These include using strong passwords for your devices and your home Wi-Fi network, avoiding default usernames (which makes it easier compromise a device), disabling services like Telnet and SSH, and making sure that your device has the latest firmware updates installed (among other things).
For a comprehensive look at what you can do to safeguard your devices, check out our article here.



