Lancope enables visibility for security and network performance. Security capabilities focus on identifying insider threats such as botnets, malware and data loss using non-signature network wide correlation of all traffic. Pretty much anything touching the physical or virtual network leaves a footprint known as NetFlow that is investigated for malicious intent and performance statics.
Lancope offers a virtual and physical appliance option for the StealthWatch technology making it easy to build a lab. This post will explain how to build a simple Lancope lab integrated with Cisco ISE 1.2 beta using an Apple Mac mini server hosting vSphere ESXI 5.1 with ASA 5505 firewall.
It’s important to understand components of Lancope.
- StealthWatch Manager (SMC)– This is the centralized system that manages all other components. Administrators will access this system’s IP for GUI management.
- StealthWatch Collector – This is what collects NetFlow. All devices generating NetFlow will send data to this device for correlation.
- StealthWatch Sensor – This generates NetFlow on behalf of devices unable to send NetFlow. This also can view application layer data providing additional context.
- StealthWatch Identity Box OR Cisco ISE – These identify users and devices based on authentication and profiling. IP addresses are linked to USER information.
- StealthWatch Replicator – This replicates UDP management data such as Flow data, SNMP traps and syslog.
- StealthWatch SLIC – This is a reputation feed that correlates external known threats with possible insider threats.
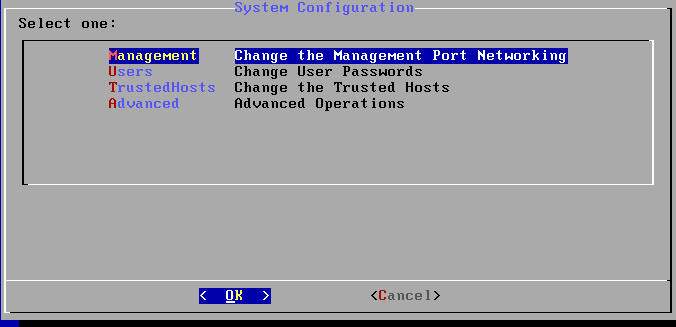
My lab is using virtualized appliances of all Lancope technology components. You can obtain Lancope .OVA files preloaded on Cisco 3850 switches, Lancope’s website or from a solution provider. The first step is loading the Lancope .OVAs into vSphere. All appliances will ask for basic IP, DNS and NTP information upon launching. The default login for everything is either admin or root and lan1cope or lan411cope. I had some problems with default logins and recommend accessing the administration of each Lancope appliance using command line, typing SystemConfig and resetting the passwords prior to logging into the GUI.
SystemConfig found in the appliance command line
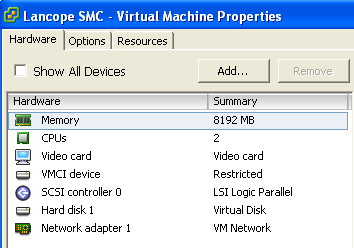
Lancope SMC ESXI Properties
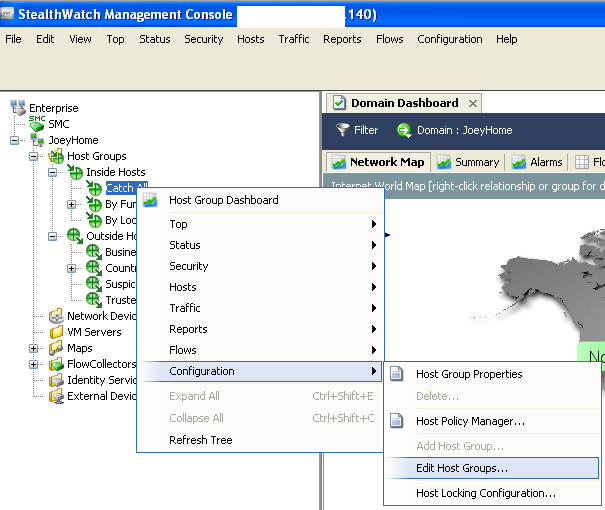
The Lancope SMC requires a minimum of 8 Gigs or memory and 2 CPUs. Step up is basic IP and accessing its GUI via https. Additional system configuration can be done by clicking Administer this server or the User GUI can be opened by clicking Start. One important first step in the GUI is adding the main inside network subnet to the Catch All.
Adding Inside Network To Lancope Catch All
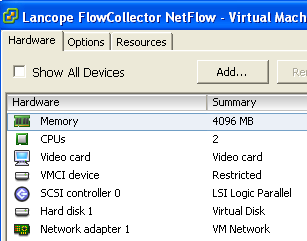
Lancope Collector ESXI Properties
The Lancope Collector lists an 8 Gig memory requirement with 2 CPUs however ESXI 5.1 gave a resource error message upon launching. I reduced the Memory to 4 Gigs per CPU, which fixed that issue. Once the Lancope Collector is up, access its GUI via https. You must point it at the SMC under the configuration tab.
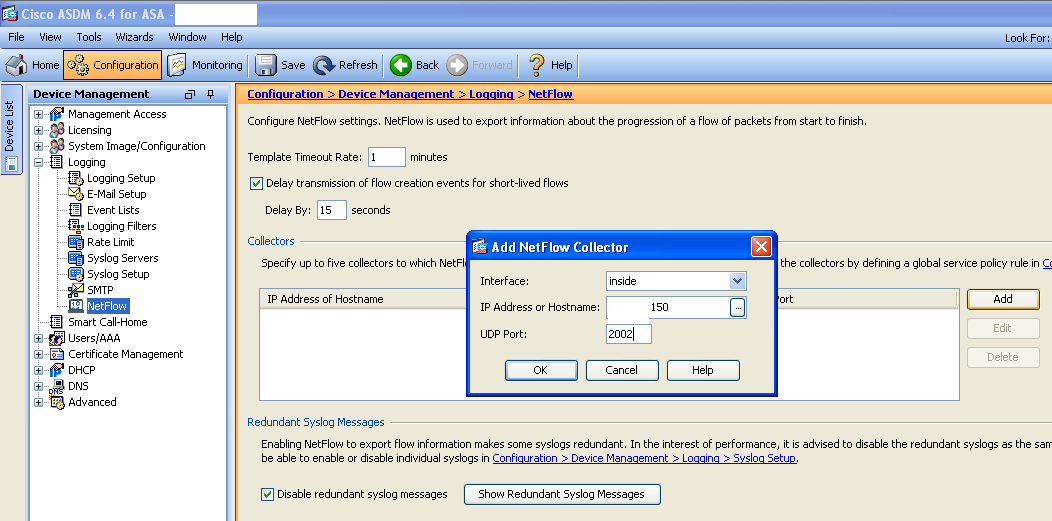
I enabled NetFlow on an ASA5505 firewall (running 8.2(2) or greater) and pointed it at the Lancope Collector for network visibility. My ASA 5505 is also powering my 1121 Access Point for wireless. To enable NetFlow in ASDM, click Configuration under Device Management, click NetFlow under Logging, changed template timeout to 1 min, delay of 15 seconds and checked Disable Redundant Syslog”. Select Inside, enter the collector’s IP and UDP port of 2055.
Creating Netflow Collector in ASA
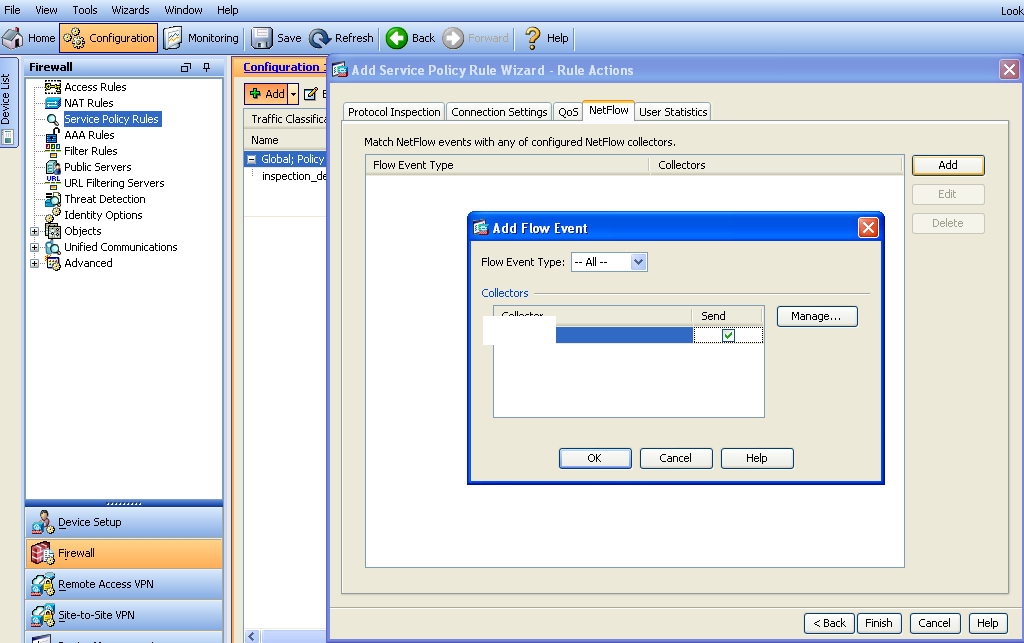
Next create a firewall policy under Firewall and Server Policy Rules. Click Global, give it a name, select All Traffic, click the tab for NetFlow and select the IP you built under device management. NOTE: If you update device management, you must first delete its reference under the firewall policy to avoid errors.
Add Firewall Policy in ASA
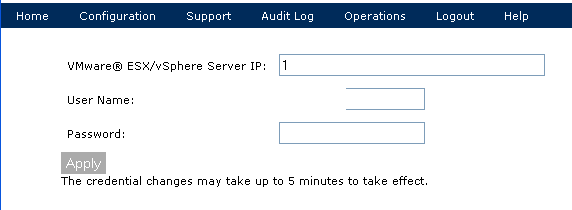
To add visibility into my ESXI environment, I have loaded a Lancope virtual Sensor. The Lancope Sensor requires 1 Gig of memory and 1 CPU. Once the Sensor is up, you must point it at the Lancope Collector and add the ESXI server. Prior to doing that, you must create a read-only user account in ESXI. NOTE: ESXI has discontinued GROUPs. Click Local Users & Groups and create a new user by right clicking and ADD. Give the user a name and password. Next click Permissions right click your New User and Edit. Add a permission of Read-Only. Once the account is ready, login to the https of the Lancope Sensor. Click the Configuration tab and add the Lancope Collector. Next, go under Configuration and add your ESXI server. If the steps are performed correctly, the SMC should automatically detect the new Lancope Sensor and virtual environment.
Adding VMware to Lancope SMC
I have ISE 1.2 providing admission control for my LAN and wireless networks. ISE data can be imported into the Lancope SMC. This is done from the GUI by right clicking Identity Services in the Lancope SMC tree and clicking ADD. Fill out the ISE information using the admin login for ISE.
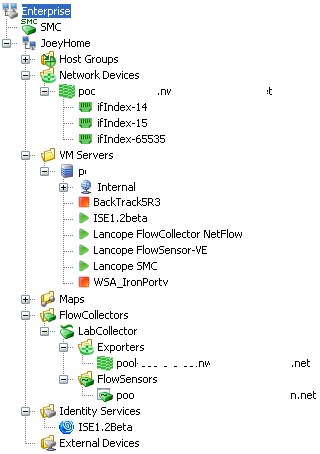
At this point, the Lancope SMC has NetFlow from an ASA firewall seeing LAN and wireless traffic, ISE authentication and NetFlow from inside a virtualized environment. I plan to add SLIC feed for reputation once I obtain a license. I now have full visibility of my home network.
Lancope SMC Device Tree




Interesting!
I am wondering what kind of reports you can get with this set of toys, so we know whether it is worth the ado, and the potential cost in enterprise environment.
BTW, after seeing your last post, I am getting a Mac Mini to build a portable ESXi platform as well.
Hi Ning,
The mac mini is awesome. A buddy of mine advised me to get a second SSD to improve performance. He did it for his older 2011 one which was running sluggish while hosting ISE. I’ll post about it once I go through the process.
Yes Lancope is good stuff. I haven’t had much time to run it since i just finished this project over the weekend however so far its pretty cool. I have plans to test attacks using low orbit ion canon, angry IP and a few others. Most likely I’ll follow up this post with report examples of different attacks and how this setup reacted. There are solutions such as Netwitness Spectrum that inform if a threat could bypass known security products (IE would this breach my Symantec Anti-Virus, McAfee firewall, etc.) however I want to test it myself starting with the firewall and ending with common endpoint security solutions. More to come.
Is there anyone who was able to see an intrusion of ransomware?