I recently posted about the new release of Cisco’s flagship access control solution Identity Services Engine (ISE) 2.0 HERE. That post lists the highlights of the new features including the highly requested TACACTS+ support. I downloaded the .ova file and performed a fresh install using the virtualized version supporting up to 6,000 devices. This post provides a first look overview of the new features as well as compares ISE 2.0 to the last release 1.4.
After downloading the ISE 2.0 .ova, I deployed it using my ESXI environment. The steps were very straight forward. The next screenshot shows the .ova deployment, which took about 22 minutes. 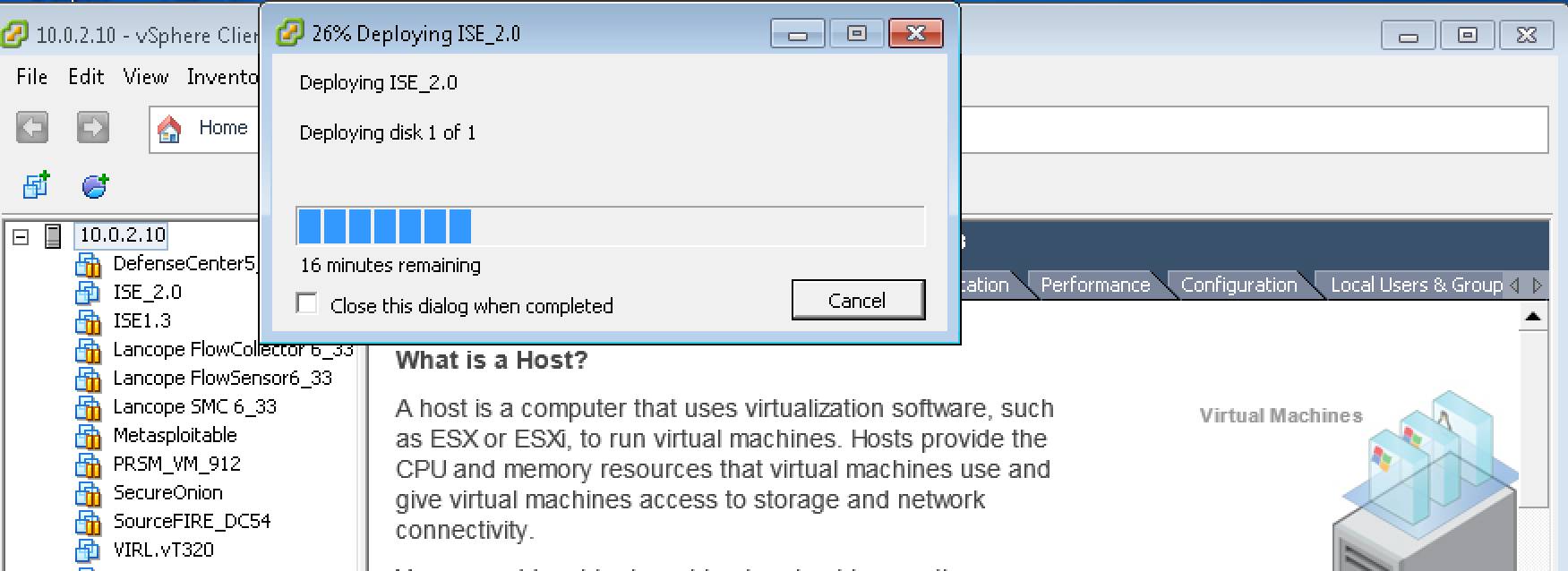 Next I fired up the VM and went through the command line configuration answering basic network info questions. This took around 20 minutes to complete.
Next I fired up the VM and went through the command line configuration answering basic network info questions. This took around 20 minutes to complete.
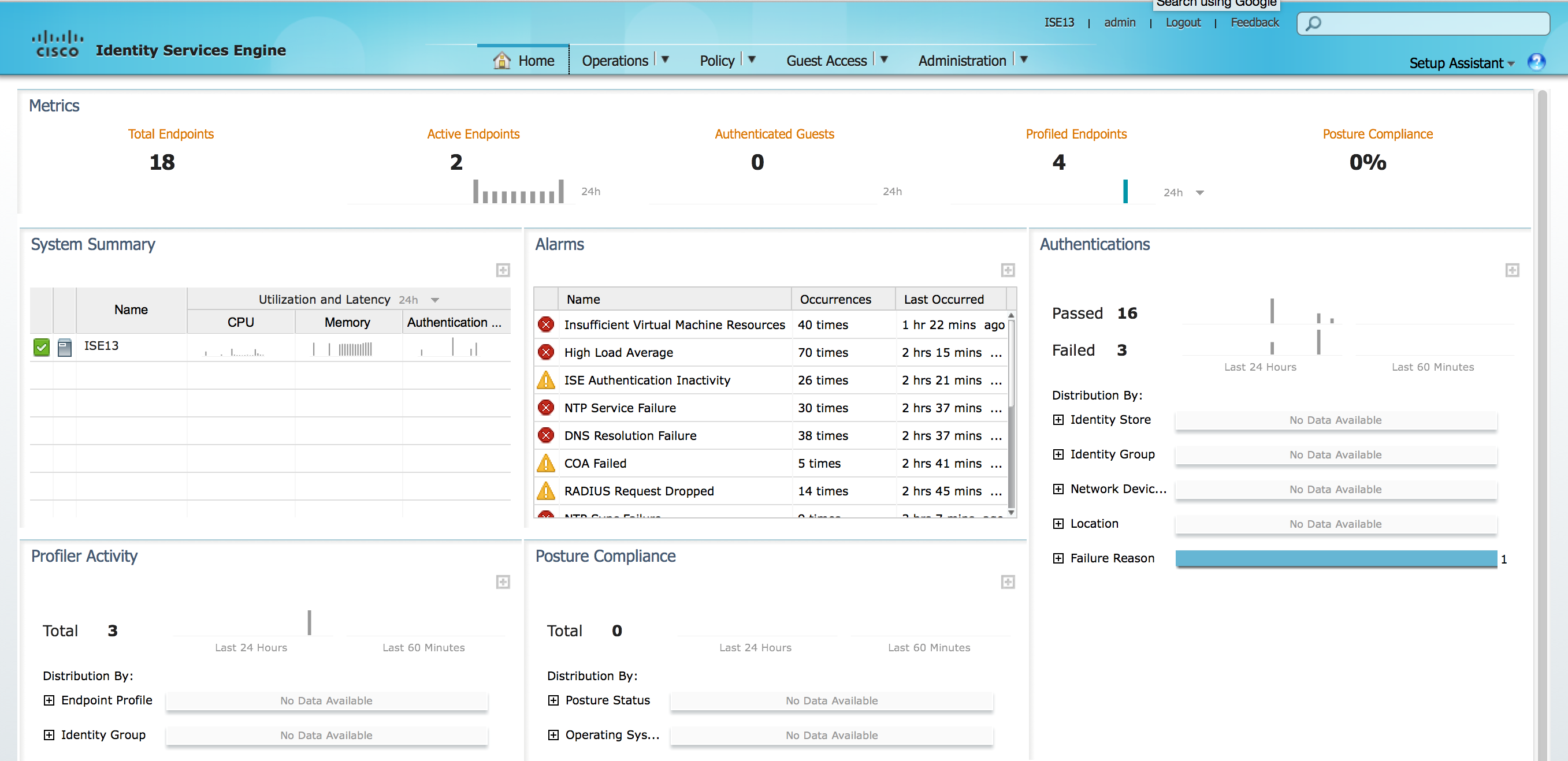
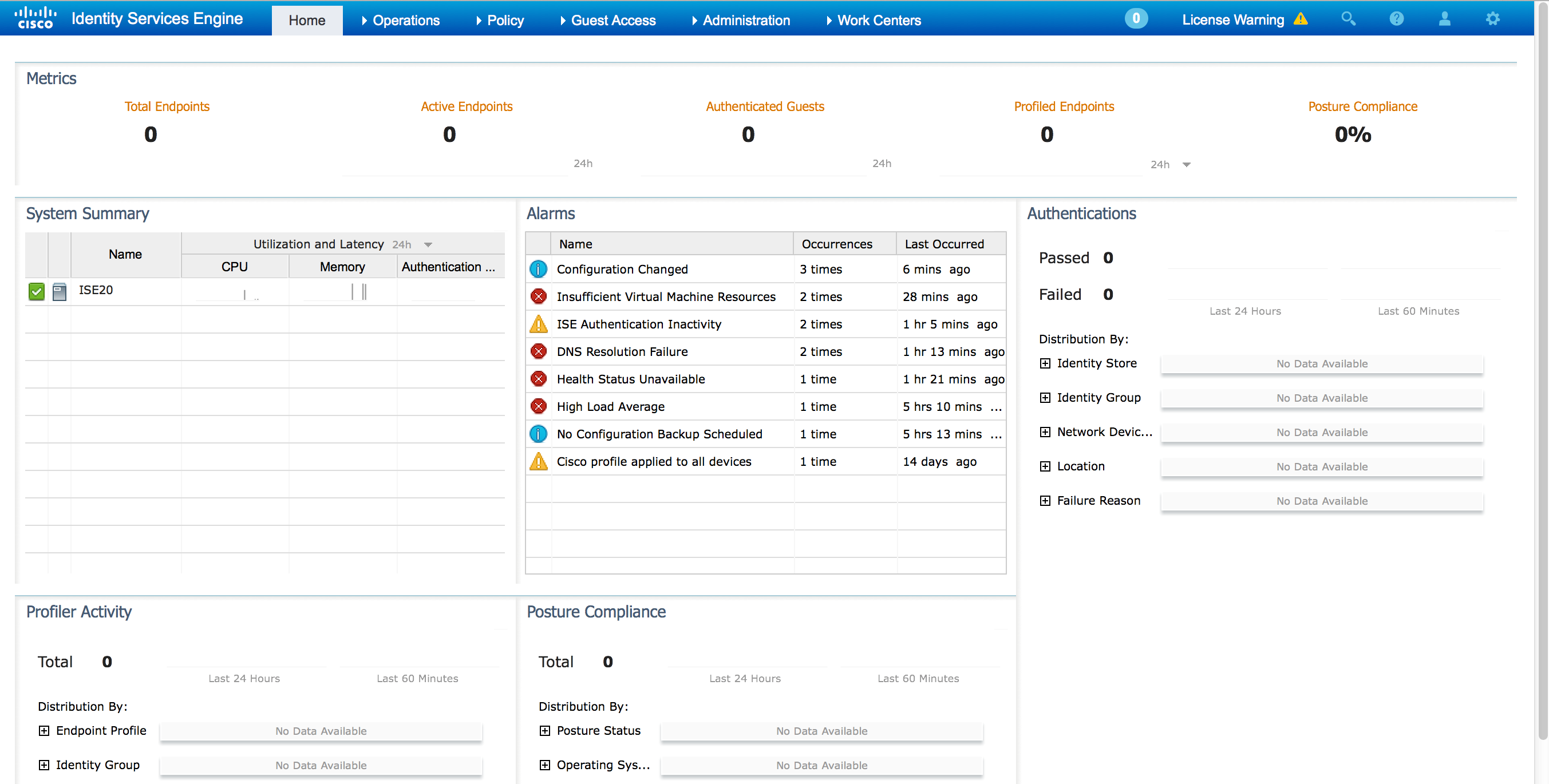
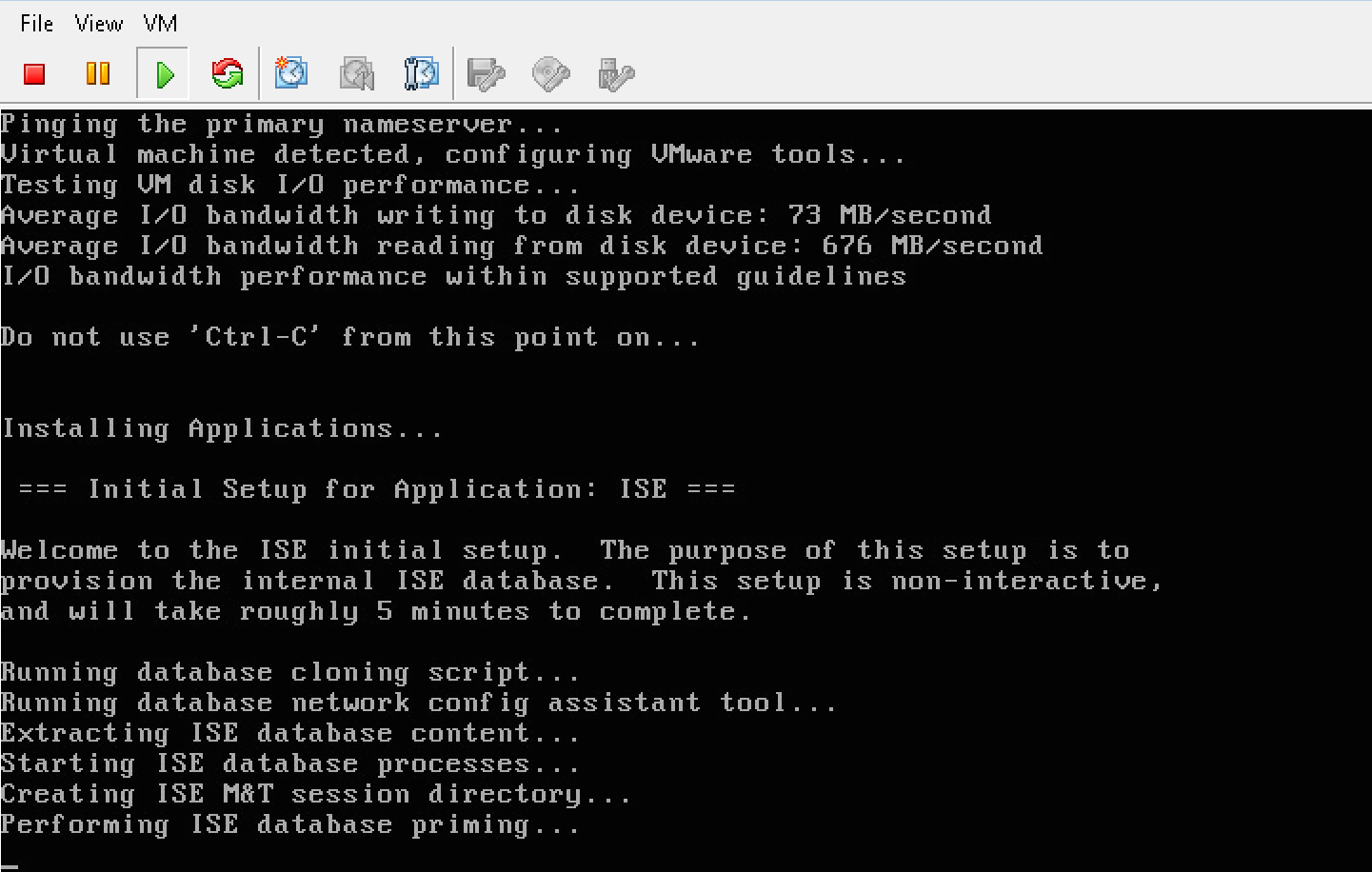 ISE rebooted and I was able to log into the GUI. The first thing I noticed is the GUI is different from ISE 1.4. The next two screenshots compare ISE 2.0 and ISE 1.4 main dashboard.
ISE rebooted and I was able to log into the GUI. The first thing I noticed is the GUI is different from ISE 1.4. The next two screenshots compare ISE 2.0 and ISE 1.4 main dashboard.
ISE 2.0 has more drop down options and has a smaller banner space. The widgets seem to be the same. I went ahead and added a wireless access point, switch, made the basic configuration and tested connecting a iPad to my network. The steps to build the configuration were pretty much the same as in ISE 1.4. I posted about setting up a ISE lab HERE.
So whats new? Lets check out it out and compare it to ISE 1.4.
First off, there is a dedicated section to TACACTS+. Here is a screenshot of the setup process to enable TACACTS+ on ISE 2.0
 Once setup, there is a separate dashboard used to monitor AAA logins as shown.
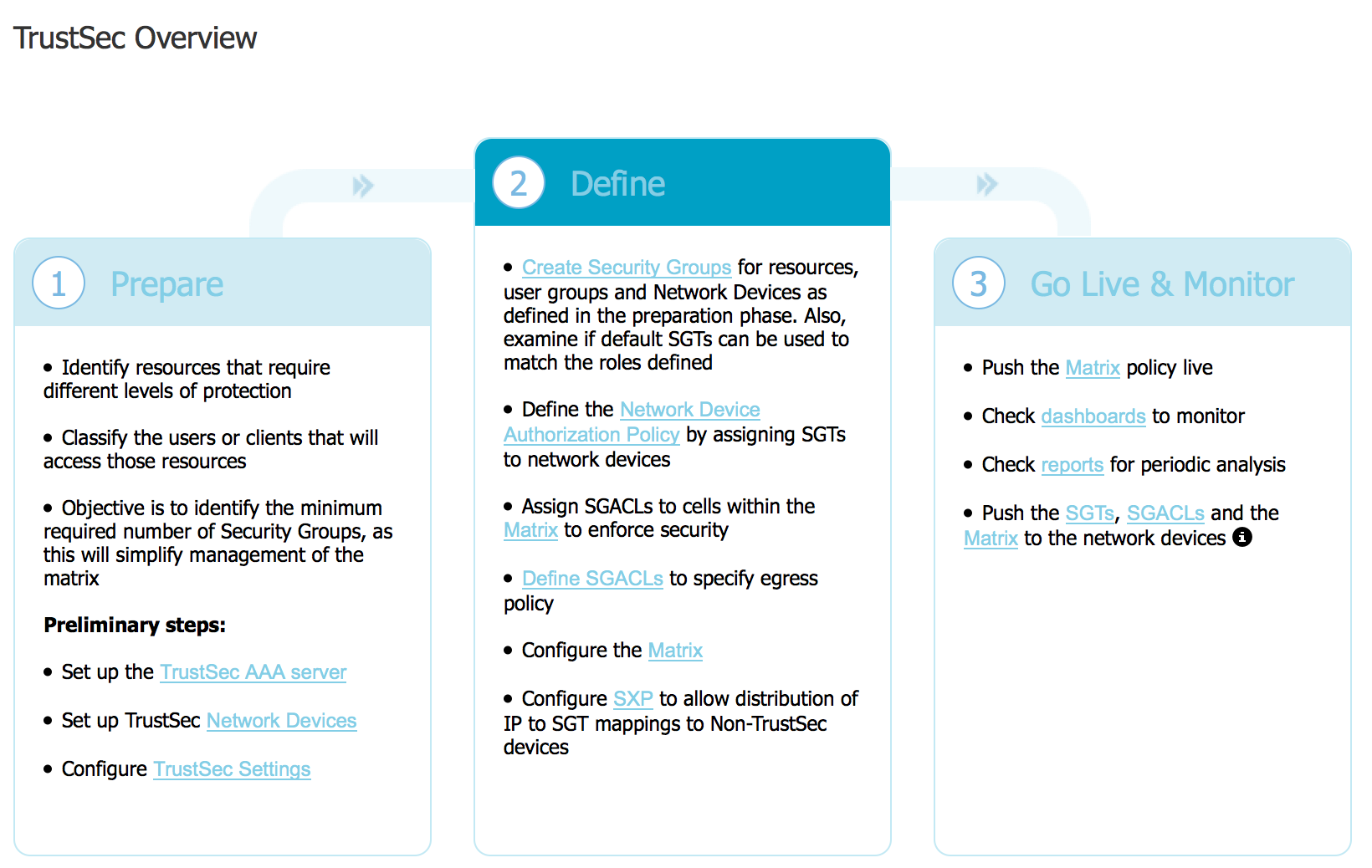
Once setup, there is a separate dashboard used to monitor AAA logins as shown.  Speaking of new dashboards, there is also a new Trustsec dedicated work center. The next screenshot shows the main Trustsec page showcasing how to enable Trustsec.
Speaking of new dashboards, there is also a new Trustsec dedicated work center. The next screenshot shows the main Trustsec page showcasing how to enable Trustsec. 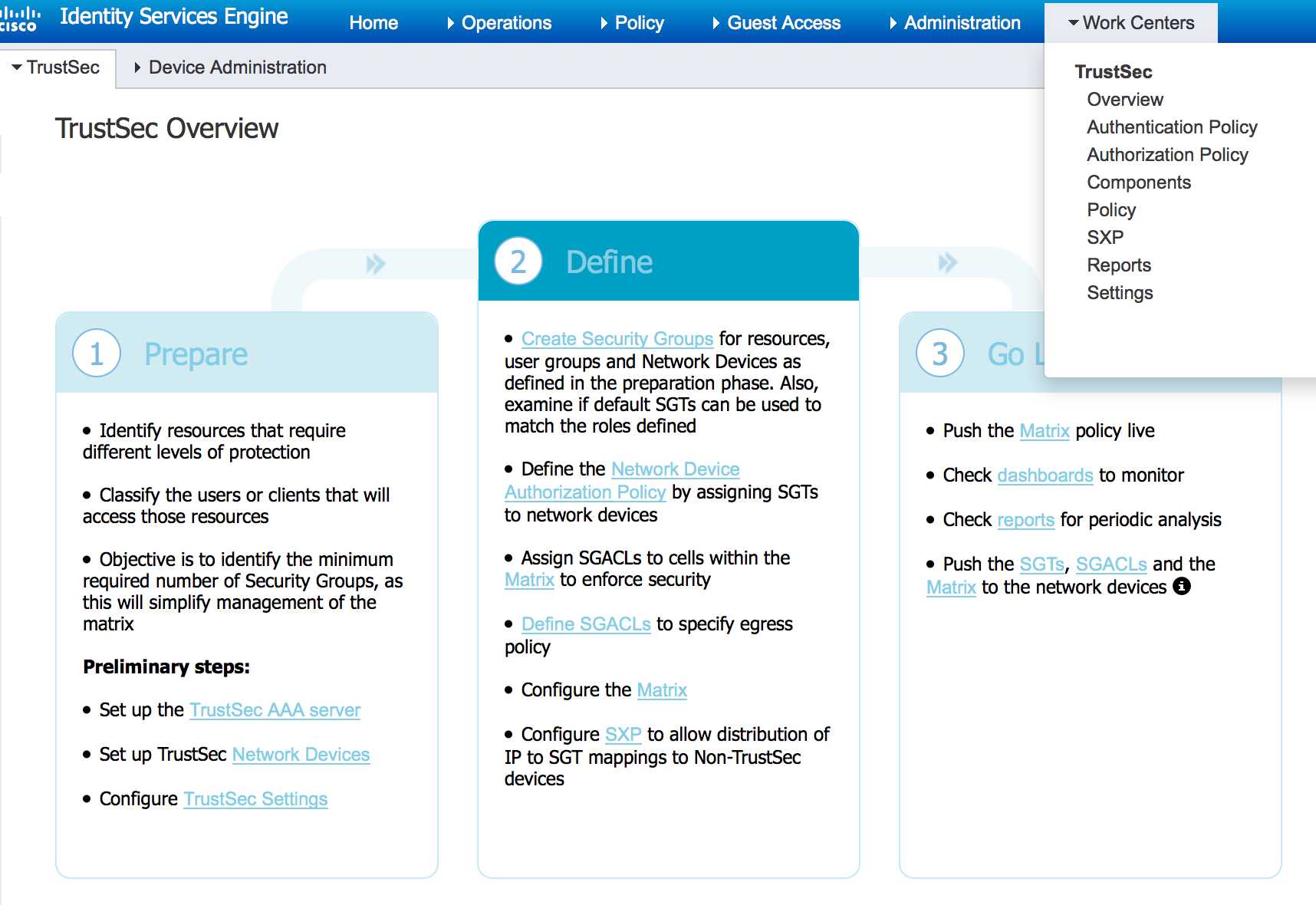 This is huge for simplifying your Trustsec deployment. They also did a bunch of matrix improvements to help administrators understand how access will be controlled using tagging technology.
This is huge for simplifying your Trustsec deployment. They also did a bunch of matrix improvements to help administrators understand how access will be controlled using tagging technology.
There has been some improvements for Mobile Device Management support including now adding Meraki. The next screenshot shows a MDM portal designed to simply the integration.
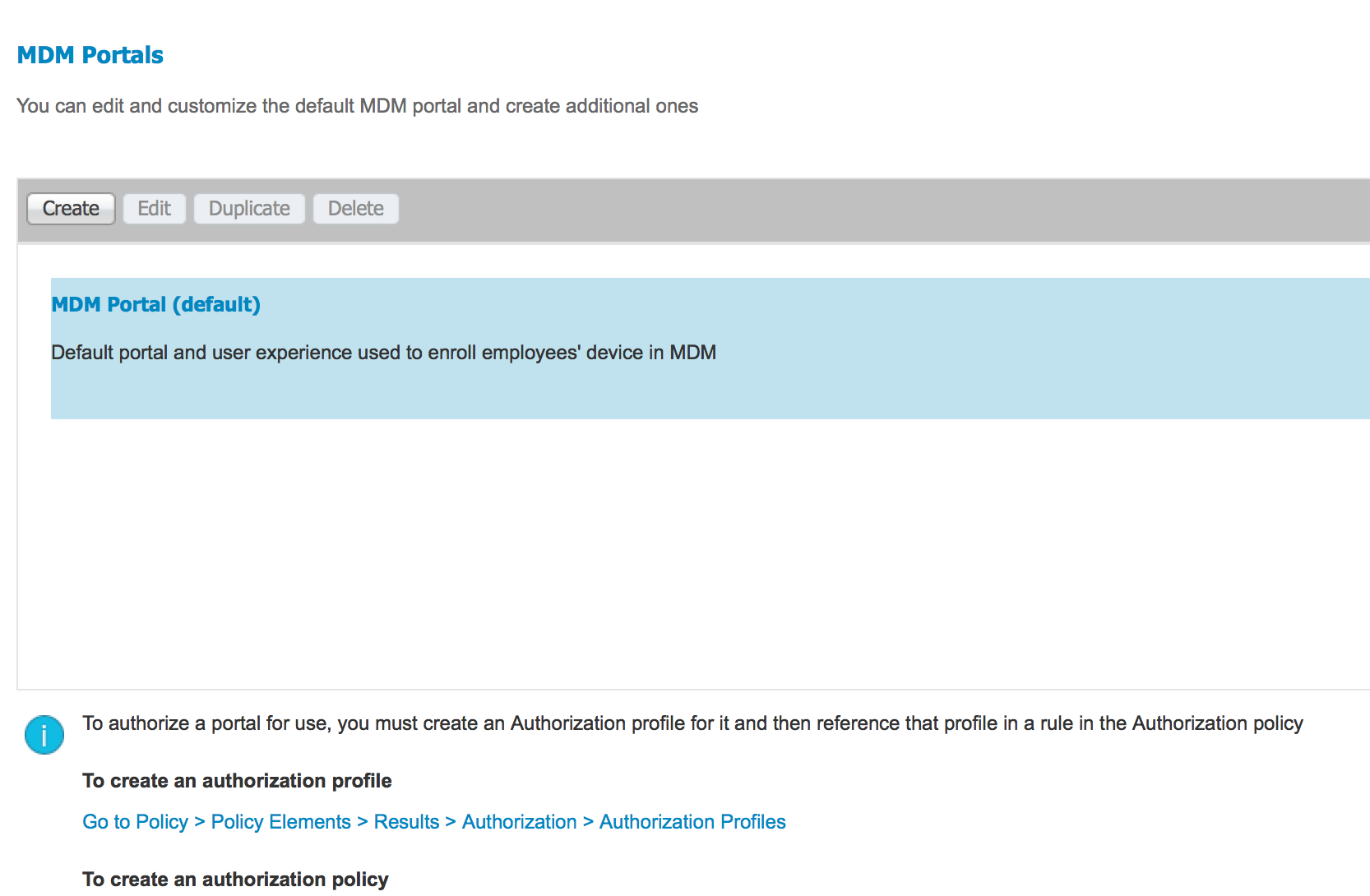 One new feature is how active devices enrolled with a MDM server outside of ISE can connect to a ISE protected network without needing to re-enroll with the MDM server.
One new feature is how active devices enrolled with a MDM server outside of ISE can connect to a ISE protected network without needing to re-enroll with the MDM server.
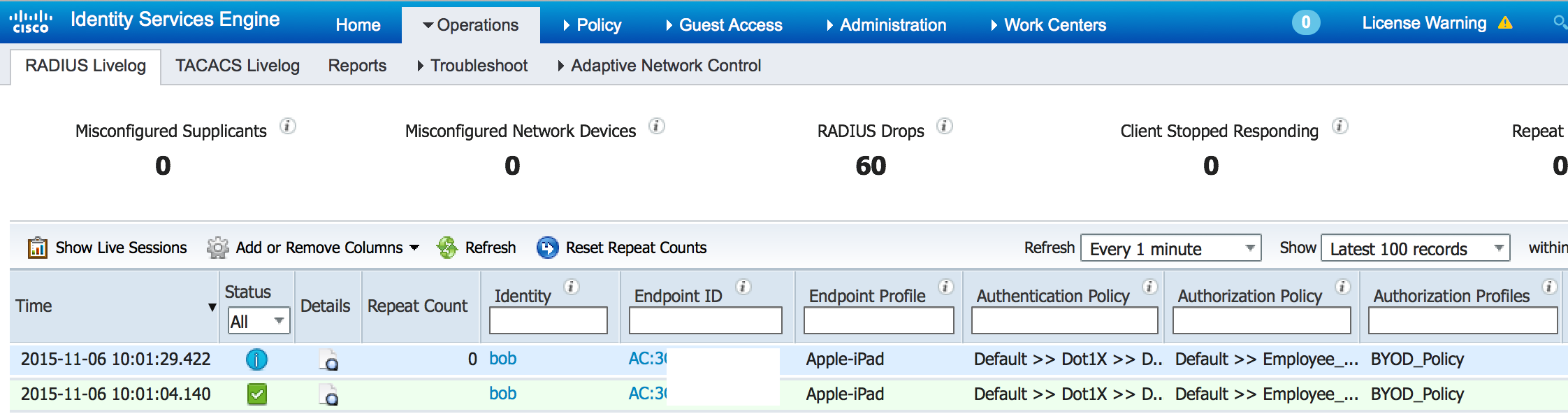
So that’s a quick overview of some new things I found in the 2.0 GUI. There are a lot of new back end items listed in the formal release notes found HERE. The next screenshot shows my new ISE 2.0 lab authenticating my iPad Mini as a BYOD device providing limited wireless guess access. This part of the GUI should be familiar to anybody using previous versions of ISE. So far I like what I see and REALLY happy that future updates can be upgraded using the new GUI upgrade option.




When I try to download ISE from cisco.com, I get message that I don’t have valid contract to download ISE. How do I resolve this?
You need to create a CCW account (its free) before you can download it.