Cisco just released the latest version of ISE aka Identity Services Engine version 1.3 on Oct 31st. ISE is Cisco’s flagship access control technology (more on ISE found HERE and how to build a Lab found HERE). In summary, ISE can tell you who and what is on the network, provision the proper access and even remediate devices that are out of expected security posture. You can find the formal release notes for ISE 1.3 HERE.
ISE 1.3’s main new features revolve around providing enhanced guest services such as simplifying the process to on-board new mobile devices. There are other improvements I’ll cover in this post as well. Lets take a look at the new 1.3 version of ISE.
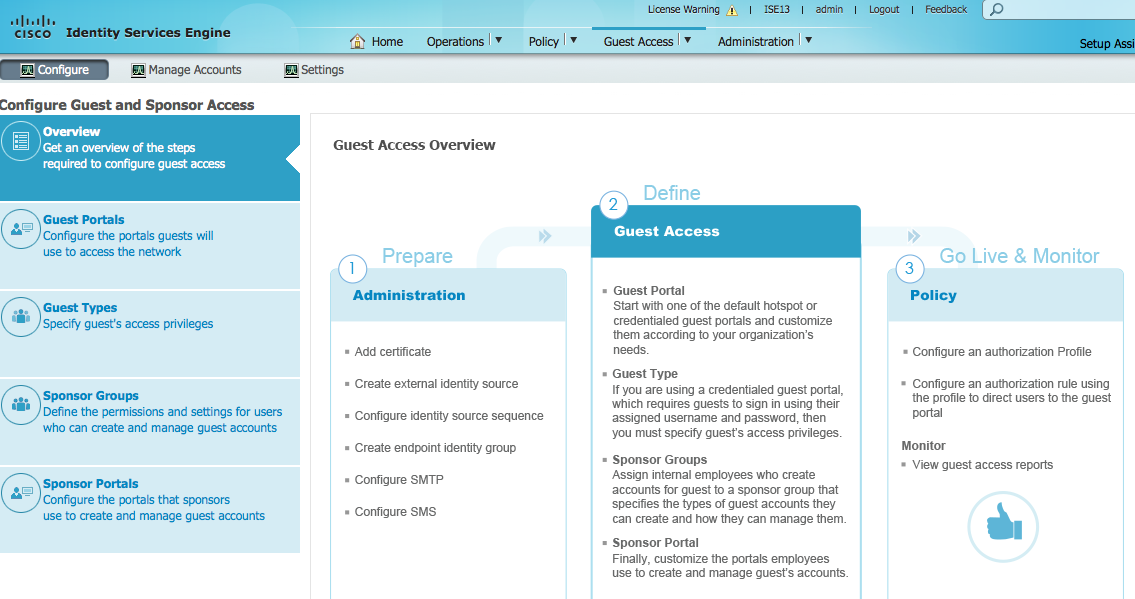
Guest Enhancements: The new way to develop how guests will be handled by ISE has dramatically improved with this release. I can make changes to the page and watch how they will look in realtime. ISE 1.3 also includes a flow chart making it super easy to understand how devices move through the on-boarding process. The next screenshot shows a overview of the process.
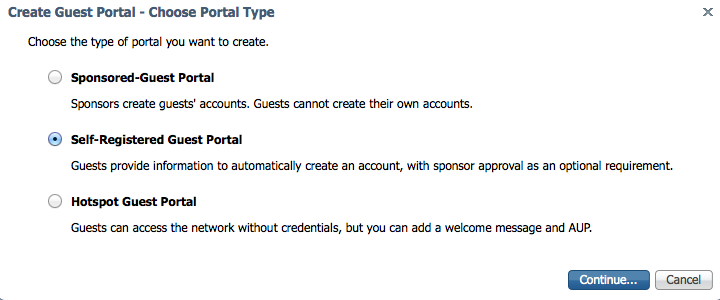
Lets walk through creating a guest portal. First I need to select the type of portal. I’ll go with a self register meaning guests fill out a form prior to getting access.
As you can see from the next image, I can see the expect flow each guest will run through. Once a person registers, the flow shows a Acceptance Use Page (AUP) is displayed. ISE then checks to see if the maximum devices have been reached for that account / guest. Then I select where to send guest after they login, which I’ll setup as www.thesecurityblogger.com.
When walking through the configuration details, I can select the login page to be something guest create or require a access code. I can specify what fields they need to fill in (name, company, phone number, etc), require a SMS text message or email to verify the information is correct as well as various others options. The AUP can be a one time thing, required each day or at each login. I can lock down the amount of devices each guest can register such as one mobile device per account so they don’t blow up my network.
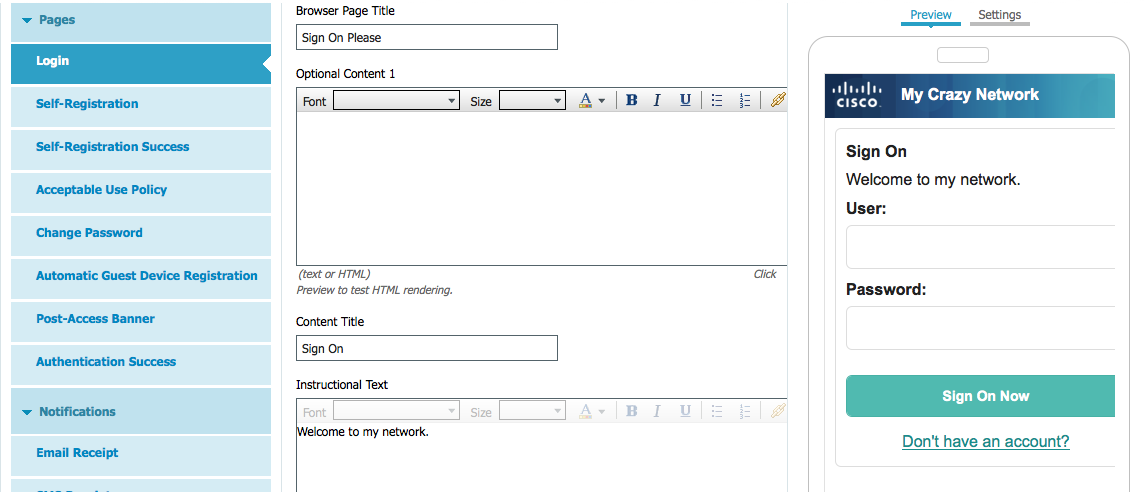
 Customizing the Guest Page look is much better with this release. I can see changes in real time as I adjust things. The next screenshot shows my login page on the right and different areas I can edit on the left.
Customizing the Guest Page look is much better with this release. I can see changes in real time as I adjust things. The next screenshot shows my login page on the right and different areas I can edit on the left.
Overall the process to build a professional looking guest experience takes 10-15 minutes minus time for creating custom banners / graphics that can be imported. Kudos to the ISE team for making this process so much easier.
Internal Certificate Authority: This compliments the Guest improvements by providing a local certificate authority for BYOD and MDM deployments. To be crystal clear, the purpose of this is not to replace a general certificate authority. The goal is targeting only on-boarding mobile devices. ISE also provides an OCSP responder to check for the validity of the certificates.
Support for OVA Installation on Virtual Machines: Nothing too special here. Just makes ISE for virtual environments easier to deploy. See my guide to build a home lab HERE and skip ahead to when you get command line inside ISE.
PX Grid: This is huge for ISE. PXGrid permits sharing ISE information with other technologies as well as leveraging ISE as a security enforcement tool. For example, another SIEM can add context to identified devices (aka turn a IP address into user Joey Muniz using device iPhone 6) as well as its location (aka port 12 of switchXYZ or Access Point XYZ). PXGrid also enables other Cisco products to be able to leverage ISE such as Firesight and the ASA series. This is the foundation to leverage ISE as the network bouncer for all other security solutions.
Anyconnect Unified Agent: Another big ask has been to consolidate endpoint agents. Now ISE posture can be performed with the dedicated NAC agent or using the Anyconnect VPN agent. So if you have Cisco VPN, deploying ISE remediation is dramatically simplified.
Multi-Forest Active Directory: For those with multiple Active Directory forests, this feature is for you. I personally dealt with this problem with a deployment a few years back so its great to see that ISE can finally handle up to 50 domains.
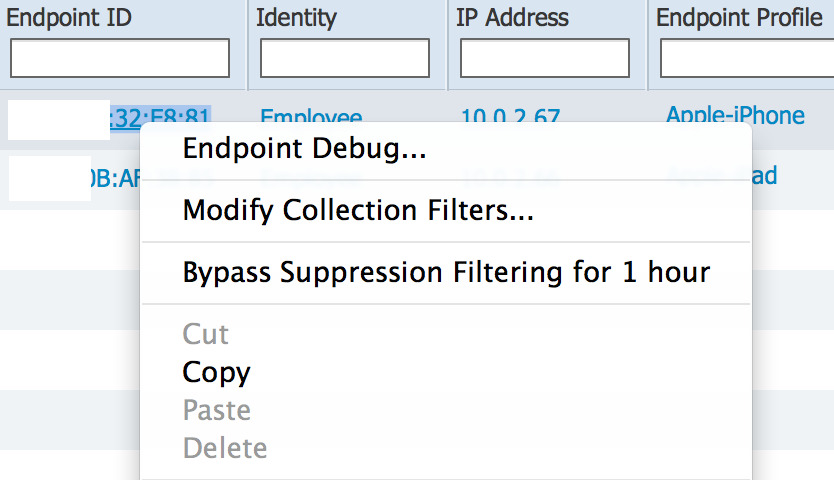
Right Click Options in Live Authentications and Live Sessions: There are now options available when you right click live devices. The next screenshot shows right clicking a iPad and selecting to either debug it, modify how its being profiled or bypass its log info. This makes finding or acting upon information a few less steps.
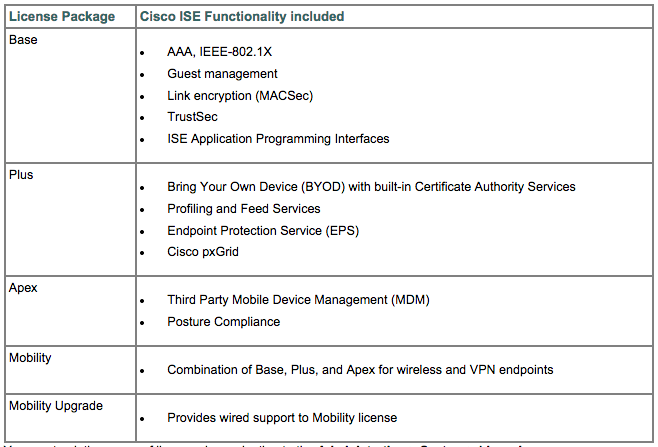
License Changes: Cisco introduced new License options with this release. Previous releases offered two licenses, which were BASE and ADVANCED for full blown ISE while wireless only offered both BASE and ADVANCED. The biggest change is there is a middle ground between BASE and ADVANCED known as PLUS, which offers everything but MDM integration and posture. From a dollar viewpoint, if BASE is 1 dollar, PLUS would be around 4 dollars and Advanced would be around 10 dollars per device This makes obtaining desired features from Advanced more affordable since some people may wait to deploy remediation but need everything else.
(NOTE: Thats not the cost but just a way to think of comparing the increase in cost per license Also NOTE: Base is purchased and owned while PLUS and Advanced are subscription based).
Authorization Enhancements: You can now chain 802.1x with Centralized Web Authentication (CWA) and validate the device using standard 802.1x. The user is prompted to authenticate using the captive portal. You can authorize based on both attributes from 802.1x session and windows AD/LDAP groups from CWA session.
Serviceability Enhancements: ISE 1.3 added improvements for deployment and troubleshooting.
Log File, Report, Upgrades made easier, FIPS support and Alarm Enhancements: Various improvements as the section states
This is a general overview of ISE1.3. Check out www.cisco.com/go/ise for more information and links to download the software.



Hi,
on licensing, did they change the APEX to only offer MDM Integration and Posture and moved all other “advanced” features into Plus so if a customer would like to use AAA, profiling/ BYOD and Posture Assessment to have BASE, PLUS & APEX or is APEX still the all-in-one advanced features license. That is not as clear as in former summaries.
Here is a visual answer for you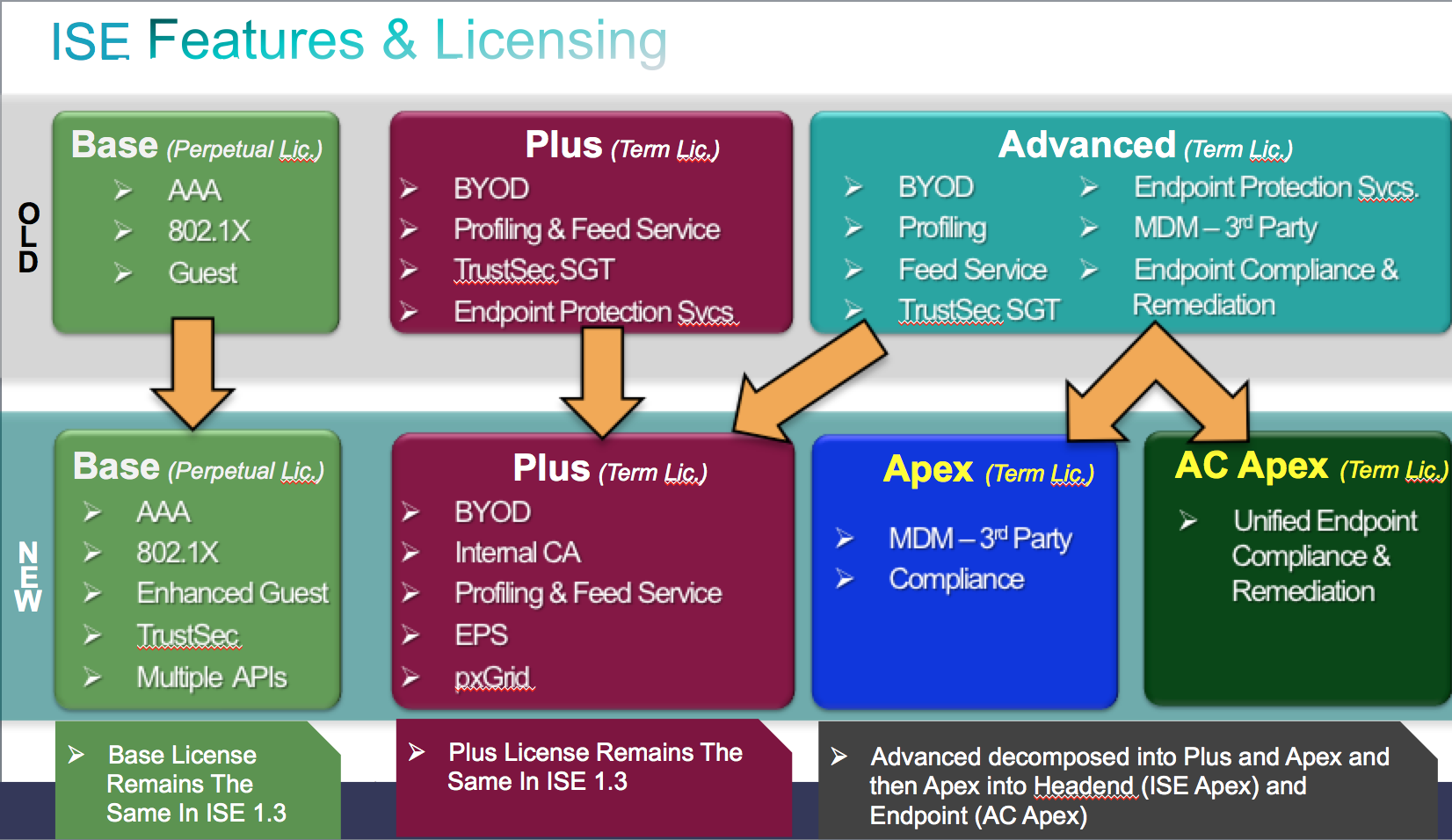
Hi. So if I have ISE 1.2 with Base + Advanced (subscription license) and I want to upgrade to ISE 1.3… Licenses will be upgraded automatically or I need to regenerate new licenses via Cisco website?
I’d like to know this too. I’m building a new pair of 1.3 nodes at the moment.
No you don’t have to regenerate licenses when upgrading ISE. You just upgrade the software. The only time you have to regenerate licenses is when you migrate from older NAC appliance technology to ISE. Hope this helps