Cisco once again recently released it cybersecurity midyear report. You can find the report HERE. For those that are not aware of this report, it focuses on trends in security and attacks seen over the past year by 300 companies from vairous business types. Focus includes Attacker Behavior, Vulnerbilities, and Secuirty Challenges / Defense oppurtunities. I find value in seeing how these trends shift based on threat actors and impact to organzation types. Here are my perosnal top take aways from the latest report.
1. I’ve personally have been beating the IoT risk drum for years and this report is doing the same. Many organizations lack visibility and security around IoT since many of these devices can’t have “security” installed on them. This report highlights IoT botnets as a growing issue. The Common characteristics of IoT botnets was particularly interesting
• Setup is fast and easy; in fact, it can be completed within an hour.• Distribution is rapid. The infection recurrence mechanism leads to exponential growth in the botnet’s size. In fact, perpetrators can have a botnet of more than 100,000 infected devices in 24 hours.• The malware has a low detection rate. It is very difficult to retrieve samples because the malicious code lives in the device’s memory and is wiped out once the device is restarted
2. The report points out a shift from remote exploitation meaning less exploit kit useage and more email based attacks. The report points out this started when major exploitkit players such as Angler were taken down however, this could just be a dry point before they come back again …. like disco. 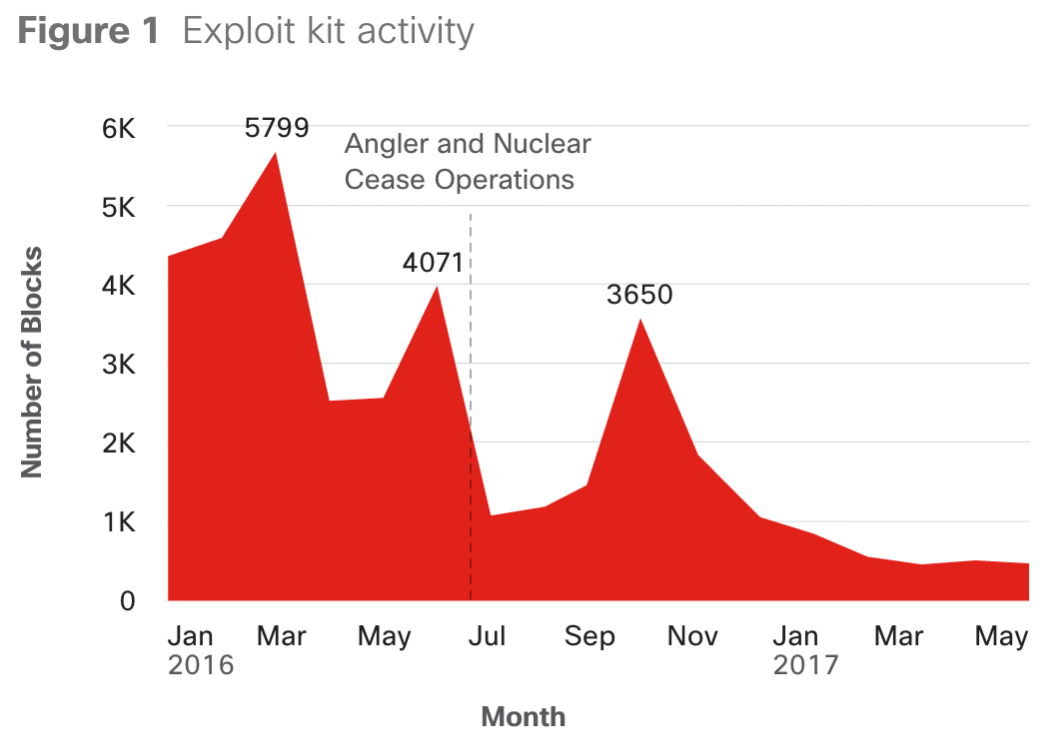 3. This report highlights how bad Spyware really is. The term spyware seems like a early 2000 problem however, its a major issue today. Lots of your coworkers, friends and family likely have some form of spyware installed on thier devices. I’ve personally run across this in organizations that have filtering in place for streaming video and music. People will download crap with the goal to bypass security or get something that is paid for free. (IE Hola or DNSChanger type programs). As our mother’s always told us … nothing is free. The following numbers were surprising to me.
3. This report highlights how bad Spyware really is. The term spyware seems like a early 2000 problem however, its a major issue today. Lots of your coworkers, friends and family likely have some form of spyware installed on thier devices. I’ve personally run across this in organizations that have filtering in place for streaming video and music. People will download crap with the goal to bypass security or get something that is paid for free. (IE Hola or DNSChanger type programs). As our mother’s always told us … nothing is free. The following numbers were surprising to me. 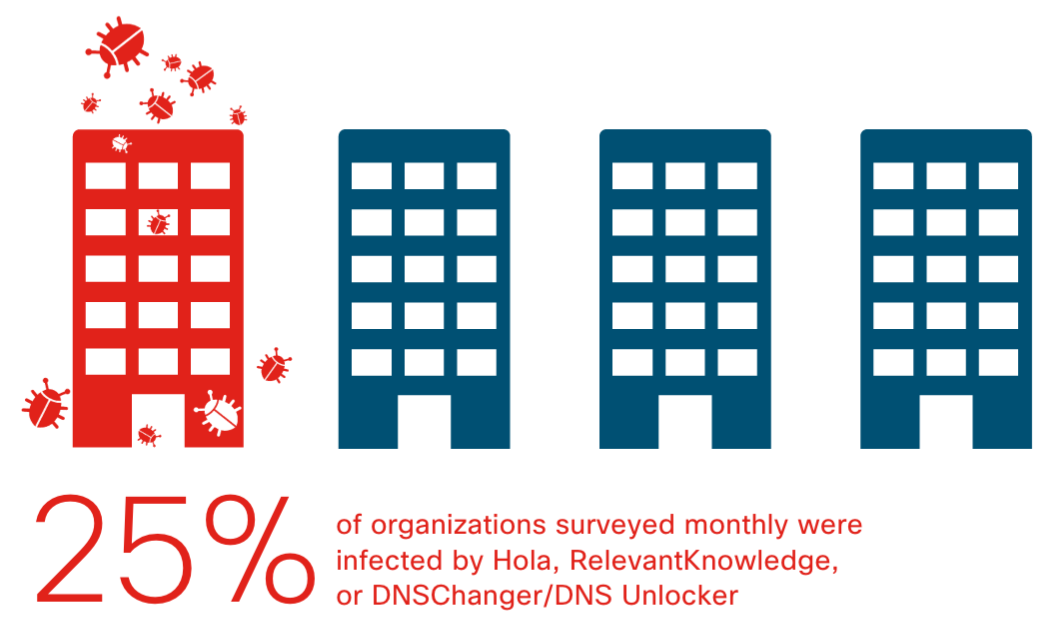
4. There is a highlight to consider buisness email compromise (BEC) as threating as Ransomware. Both target quick money however BEC is rarely in the news. In short, the attackers trick the company to wire money for whatever fake reason (bills, services overdue, etc) so people willingly pay the threat actor. I found it surprising that the Cybersecurity report listed a 5.3 Billion dollar reported loss between October 2013 and December 2016. Thats a huge number!
5. The callout that Wannacry underscores the risk of hoarding knowledge about vulnerbilities. There has always been two camps of thought …. do you hide vulnerbility data with fear attackers will get it or do you expose it as a means to get the vender and customers to patch thier systems. I personally believe in exposing verses hoarding due to what was pointed out in this report about the Wannacry wakeup call.
6. OAuth awareness continues to be important. This in summary is the concept of connecting a APP that is auto permitted to access other parts of your device. For example, you install some dumb game that is granted access to your email. This is a problem and something you need to be assessing your organization for. This diagram should explain why. 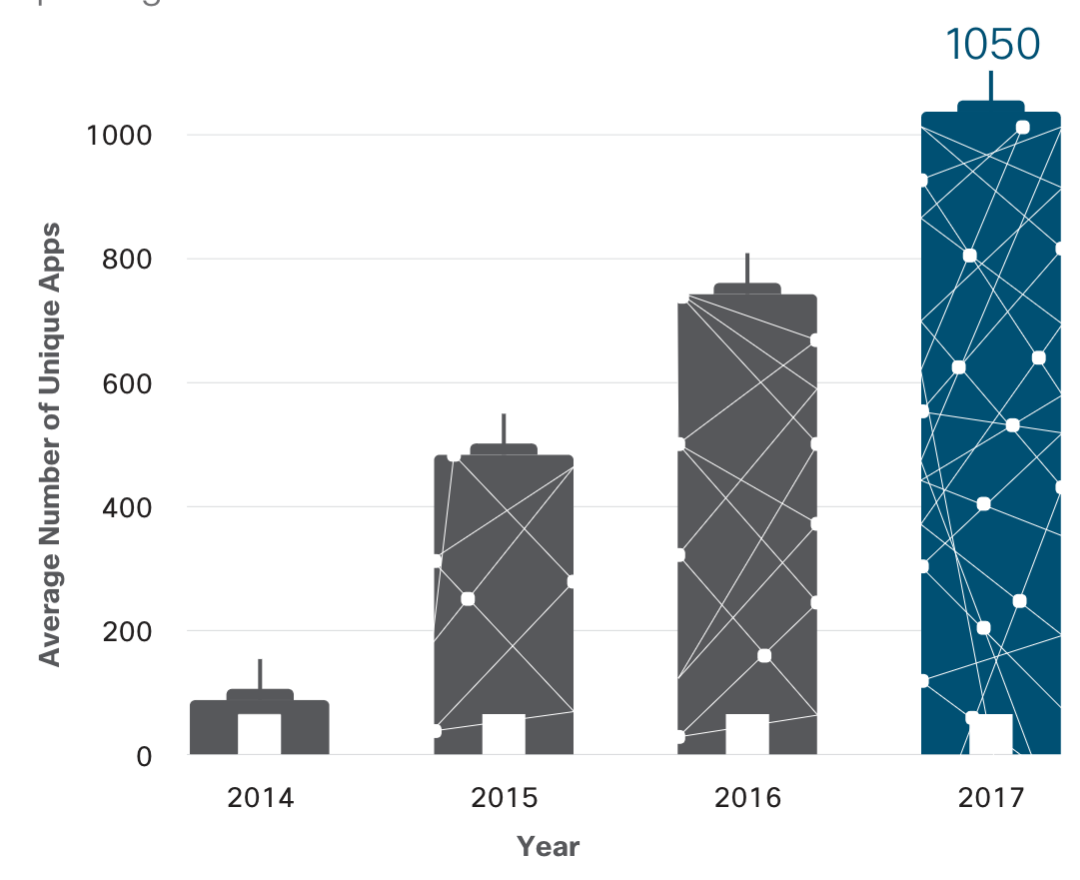 Think about how many of these applications are vulnerable to things like session hijacking. This diagram shows how many people are leaving sessions open … forever
Think about how many of these applications are vulnerable to things like session hijacking. This diagram shows how many people are leaving sessions open … forever 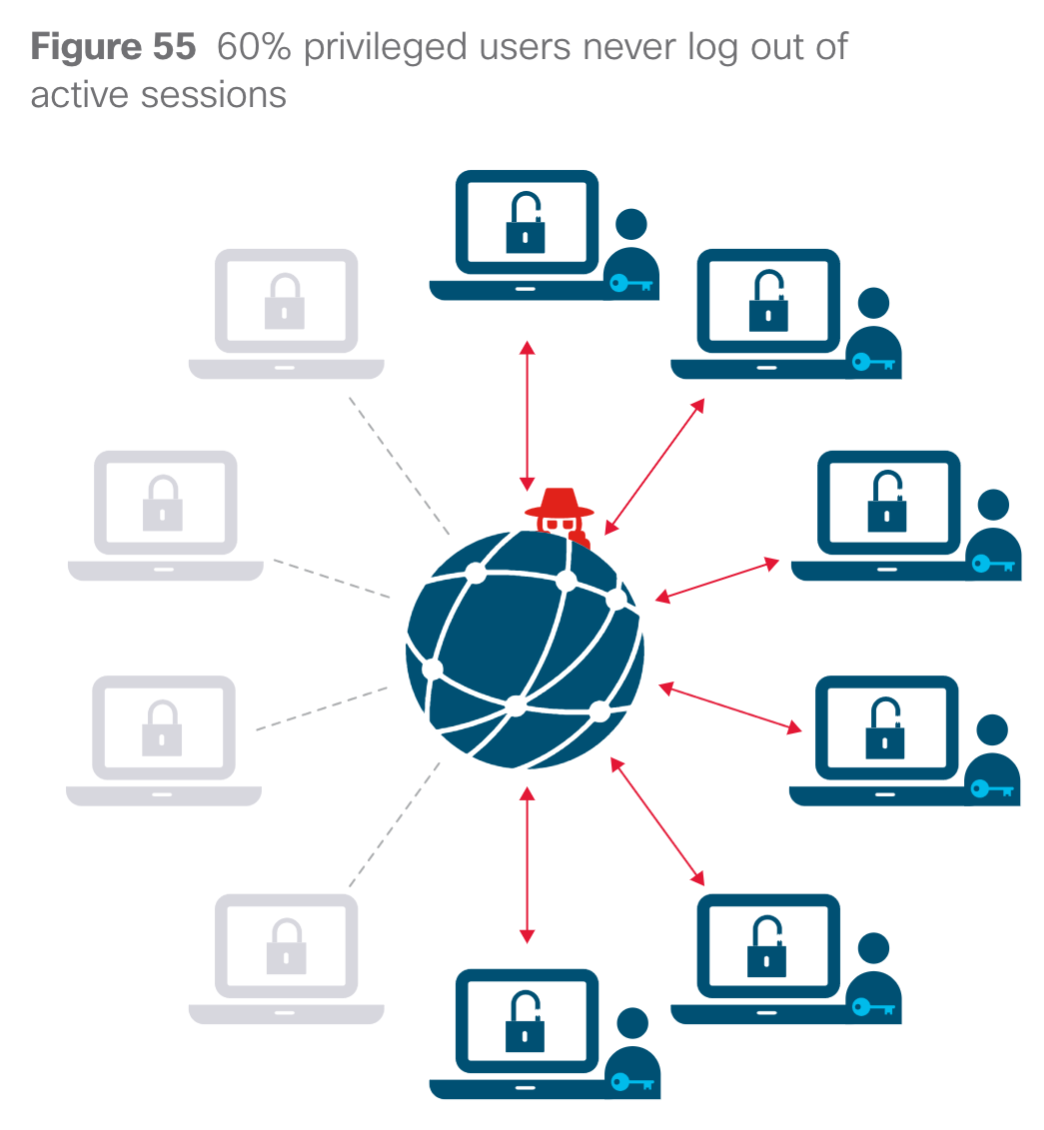 Go check out the report to get details on these as well as other interesting threat data.
Go check out the report to get details on these as well as other interesting threat data.

