My buddy Aamir Lakhani wrote a post on the reaction to Heartbleed. He points out the media attention on Heartbleed is opening new opportunities for phishing attacks. The original post can be found HERE.
Everyone is in frenzy due to the OpenSSL Heartbleed bug. The mainstream media has been reporting on it for a few days. Unfortunately, with this much publicity, there is also opportunity for attackers to take advantage of the hype. In the last 24 hours I am seeing a major rise in phishing emails and other scams.
As people understand and hear about the bug, I expect scams and malicious phishing emails to exponentially increase.
(source: hotforsecurity.com)
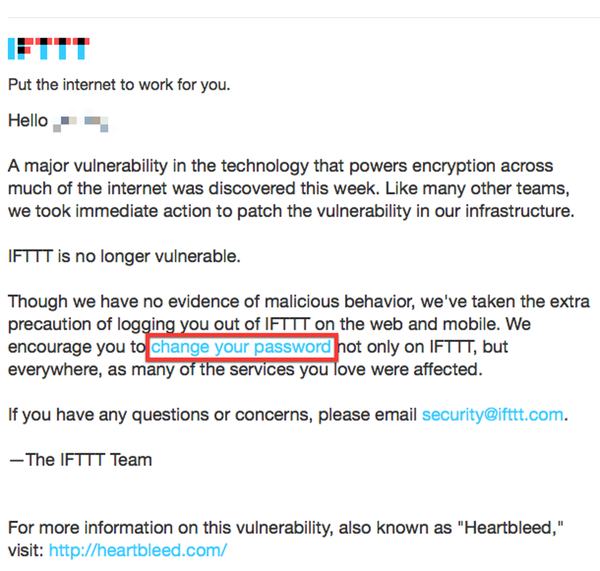
DO NOT CLICK ON LINKS THAT ADVICE OR ENCOURAGE YOU TO CHANGE YOUR PASSWORD
Most security professionals are advising people to change all their passwords. Some people may consider this drastic, but in truth, this for most security professionals is our Salmmer. It will make the security industry question policies and practices.
My advice, yes you should change all your passwords. However, only change them on sites after they have confirmed they have fixed the problem. You can check manually if your website owner has fixed the bug by checking manually at: http://filippo.io/Heartbleed.
If people start blindly changing their passwords, they most likely will choose poor passwords and also use the same password or some variation of it on multiple sites.
I would recommend using a password manager. Password managers can create complex random passwords for every website you visit. Therefore, if one site is compromised, you minimize the risk of being compromised on other sites.

Password managers allow you create one Master Password, eliminating the need to remember another username or password. Password managers makes it easier to have unique login data for each of your online accounts without the hassle of remembering them or recovering them when you forget.
Complex passwords such a B@T^^@n99 maybe very difficult to break, but they are also very difficult to remember. If we picked a passphrase that meant something to us, it might be easier to remember and more difficult to crack. A good example of a passphrase is DrCh@aIsAGre@tSite – My passphrase is Dr. Chaos is a Great Site. I can remember that statement. I can also remember I replaced the letter “a” with the “@” easily.
The great thing about password managers is that I only have to come up with, and remember one really good password. I can have the password manager remember all my complex, difficult, and random passwords that the program itself can generate.
Lastly, since you will be changing most of your passwords, I would recommend turning on 2-factor authentication. Most popular web sites use two-factor authentication. This includes, Google, Dropbox, Facebook, Twitter, and many others.
From <a ” href=”http://www.pcworld.com/article/2141602/the-heartbleed-bug-and-you-a-users-guide.html”>http://www.pcworld.com/article/2141602/the-heartbleed-bug-and-you-a-users-guide.html
“Security flaws like this are also a good time for some reminders about how best to secure your online accounts.
You should really be using two-factor authentication for all your accounts that offer it. Two-factor authentication requires you to enter an extra code before accessing your online accounts. The code is typically generated by a smartphone app or keychain dongle, but you can also receive codes to your phone via SMS.
This extra step requires attackers to know how to generate your two-factor authentication code before they can login to your account….”
“Now’s a good time to start using a password manager especially if you’re going to be changing some user logins over the next few days. A password manager makes it easy to generate randomized passwords using a combination of letters, numbers, and special characters. It also relieves you of having to memorize every one of those overly complex codes…”
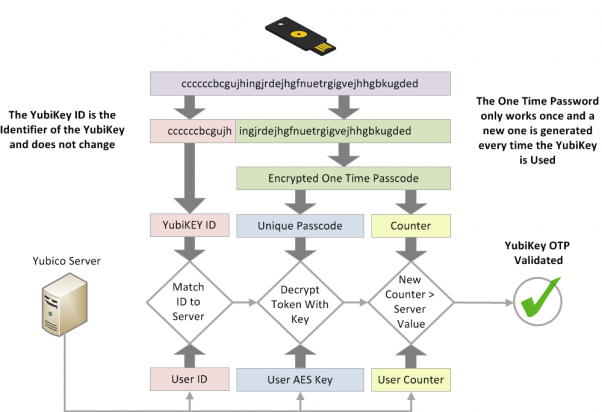
Lastpass is a popular password manager that supports 2-factor authentication with a Yubi Key.
A YubiKey is a key-sized device that you can plug into your computer’s USB slot to provide another layer of security when accessing your LastPass Account. YubiKeys are a secure, easy to use, two-factor authentication device that are immune from replay-attacks, man-in-the-middle attacks, and a host of other threat vectors. You can purchase a Yubi Key and a LastPass subscription on Yubi Key’s website: http://www.yubico.com/products/yubikey-hardware/lastpass-yubikey/
Do not trust any links, and be very suspicious of anyone or any message trying to cause fear. Hover over your links to see where they are really going to. On a Apple or iPhone device hold the link and you will see the real destination address. Stay safe.
Related Article: ” href=”http://www.drchaos.com/openssl-heartbleed-bug/” target=”_blank”>Heartbleed OpenSSL Bug. Learn how enterprise products such as Cisco and F5 are responding, how to write your own IDS signature, and what you can do to protect yourself.



Very nice information you provided about different attacks. Really liked the article. I agree about password managers though. Installing a password manager and then creating a good master password, is all that is required to manage all the passwords together. I personally use Password Depot. It is a very good password management tool. Very safe and easy to use. http://www.password-depot.com/