I recently purchased the latest tool from Hak5 and thought to provide a quick first look. The tool came within a few days of ordering and contained some stickers, a small card suggesting to go to packetsquirrel.com/set to learn how to use it and the actual hardware. I was surprised how small it is, which you can see from the pictures. Hak5 doesn’t include a micro USB cable so you need to dig one up to power this badboy on.
 The setup is similar with the bashbunny. There is switch on the slide that you can move into four different places. Three are used for delivering payload scripts and one is for configuring the device payloads. Moving it all the way to the left puts it in arming mode, which lets you connect over SSH and access folders you place payloads in for the other switch settings. The other three switch modes trigger the code within the payload folder. The other side of the device has a USB connection as shown for storing things such as PCAP files.
The setup is similar with the bashbunny. There is switch on the slide that you can move into four different places. Three are used for delivering payload scripts and one is for configuring the device payloads. Moving it all the way to the left puts it in arming mode, which lets you connect over SSH and access folders you place payloads in for the other switch settings. The other three switch modes trigger the code within the payload folder. The other side of the device has a USB connection as shown for storing things such as PCAP files.
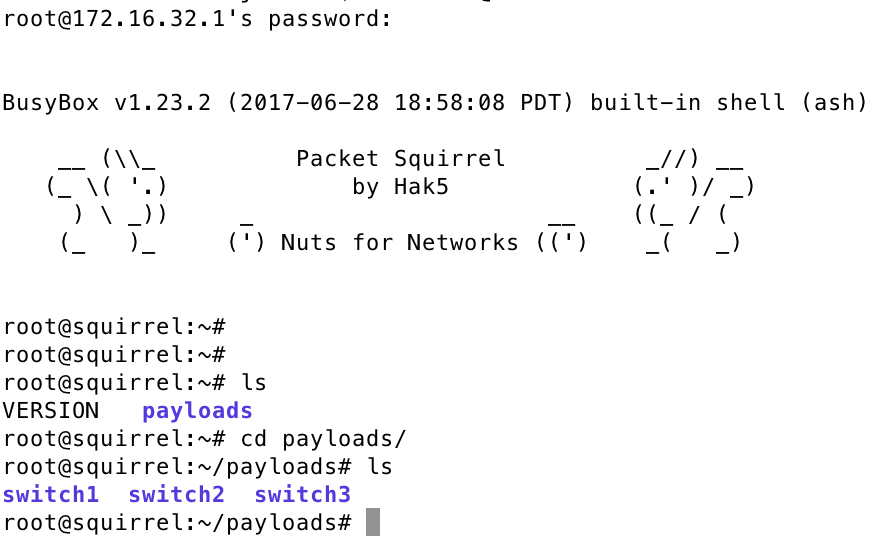
 To load a payload, I plugged in the micro USB to my computer to power it up and attached my computer to the ethernet port on the same side as the microUSB connection. Within a minute, I recieved a 172.16.32.x IP. I opened a terminal and SSHed using root and password hak5squirrel. Once logged in, I found a folder called payloads containing three folders for each switch. The next image shows these folders.
To load a payload, I plugged in the micro USB to my computer to power it up and attached my computer to the ethernet port on the same side as the microUSB connection. Within a minute, I recieved a 172.16.32.x IP. I opened a terminal and SSHed using root and password hak5squirrel. Once logged in, I found a folder called payloads containing three folders for each switch. The next image shows these folders.
 By default, the three payloads broken up between each switch folder are one for performing TCPdump on traffic seen by the squirrel, a DNS Spoofing tool and VPN tool. I tested the TCP dump and it was pretty straight forward. All you do is plug in a USB drive formatted for NTFS or EXT4 to the standard USB slot on the squirrel, connect the squirrel between two devices and it will start capturing. There is a LED that shows its working. You can stop the capture by pressing the small button on the top of the squirrel. This creates a loot folder on the USB that contains PCAP files you can read with tools like WireShark. Pretty nifty for quick packet capturing and potential network troubleshooting.
By default, the three payloads broken up between each switch folder are one for performing TCPdump on traffic seen by the squirrel, a DNS Spoofing tool and VPN tool. I tested the TCP dump and it was pretty straight forward. All you do is plug in a USB drive formatted for NTFS or EXT4 to the standard USB slot on the squirrel, connect the squirrel between two devices and it will start capturing. There is a LED that shows its working. You can stop the capture by pressing the small button on the top of the squirrel. This creates a loot folder on the USB that contains PCAP files you can read with tools like WireShark. Pretty nifty for quick packet capturing and potential network troubleshooting.
The Spoof tool has lots of potential. I can see one usecase could be spoofing a trusted site so one or more internal users are sent to attack source. For example, spoof a company intranet page, Facebook, etc and send people to a cloned version hosted by BeEF or SET. This removes the need to use phishing to get targets to access the landing page, which is pretty slick. The usecase would require getting a squirrel between a specific system or network point and there are some limitations i’m finding as I do more research. For example, the throughput isn’t the greatest, but that should be expected from a small inexpensive tool like this. I plan to test this concept soon to see how effective it is. Hopefully it won’t slow things down so much that people notice.
The VPN payload reminds me of the LANturtle. I like the LANturtle for its reverse SSH backdoor capabilities and assume this could be configured similarly. Either one (turtle or squirrel) seem to be good for this purpose.
I’m sure there will be many more payloads to come out as this tool gets more popular. I see myself using this for quick network PCAP captures when testing traffic between the message of hardware I have in my lab and the DNS spoofing attack if it works as it claims. So far, the Hak5 tools have been solid so I’m sure people will find some very interesting exploits using this in the near future.