The hacker news posted about a vulnerability in the VingCard digital lock used by millions of hotel rooms. They didn’t post the actual exploit but it still isn’t fun knowing this is possible. The original post can be found HERE.
If you often leave your valuable and expensive stuff like a laptop and passports in the hotel rooms, then beware. Your room can be unlocked by not only a malicious staff having access to the master key, but also by an outsider.
A critical design vulnerability in a popular and widely used electronic lock system can be exploited to unlock every locked room in a facility, leaving millions of hotel rooms around the world vulnerable to hackers.
The vulnerability has been discovered in Vision by VingCard locking system—made by the world’s largest lock manufacturer, Assa Abloy, and deployed in more than 42,000 facilities in 166 different countries, which equals to millions of doors.
After thousands of hours work, F-Secure researchers Tomi Tuominen and Timo Hirvonen managed to build a master key that could be used to unlock doors and gain entry to any of the hotel rooms using the Vision by VingCard digital lock technology, without leaving a trace on the system.
How Hackers Built a ‘Master Key’
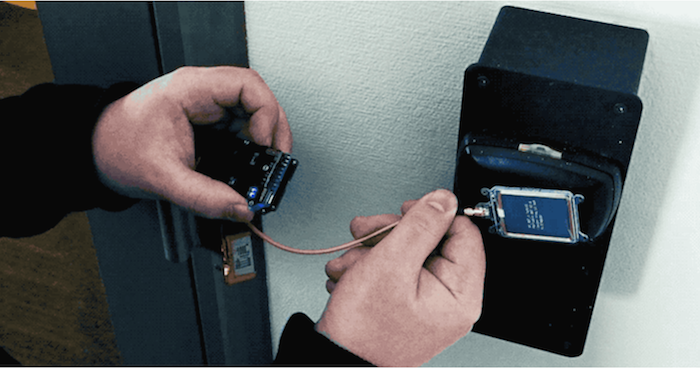
 To create a master key to access a room secured by the Vision system, the first requirement is to get hold of an electronic keycard—any existing, old or expired electronic keycard to any room in the target facility would get the job done.
To create a master key to access a room secured by the Vision system, the first requirement is to get hold of an electronic keycard—any existing, old or expired electronic keycard to any room in the target facility would get the job done.
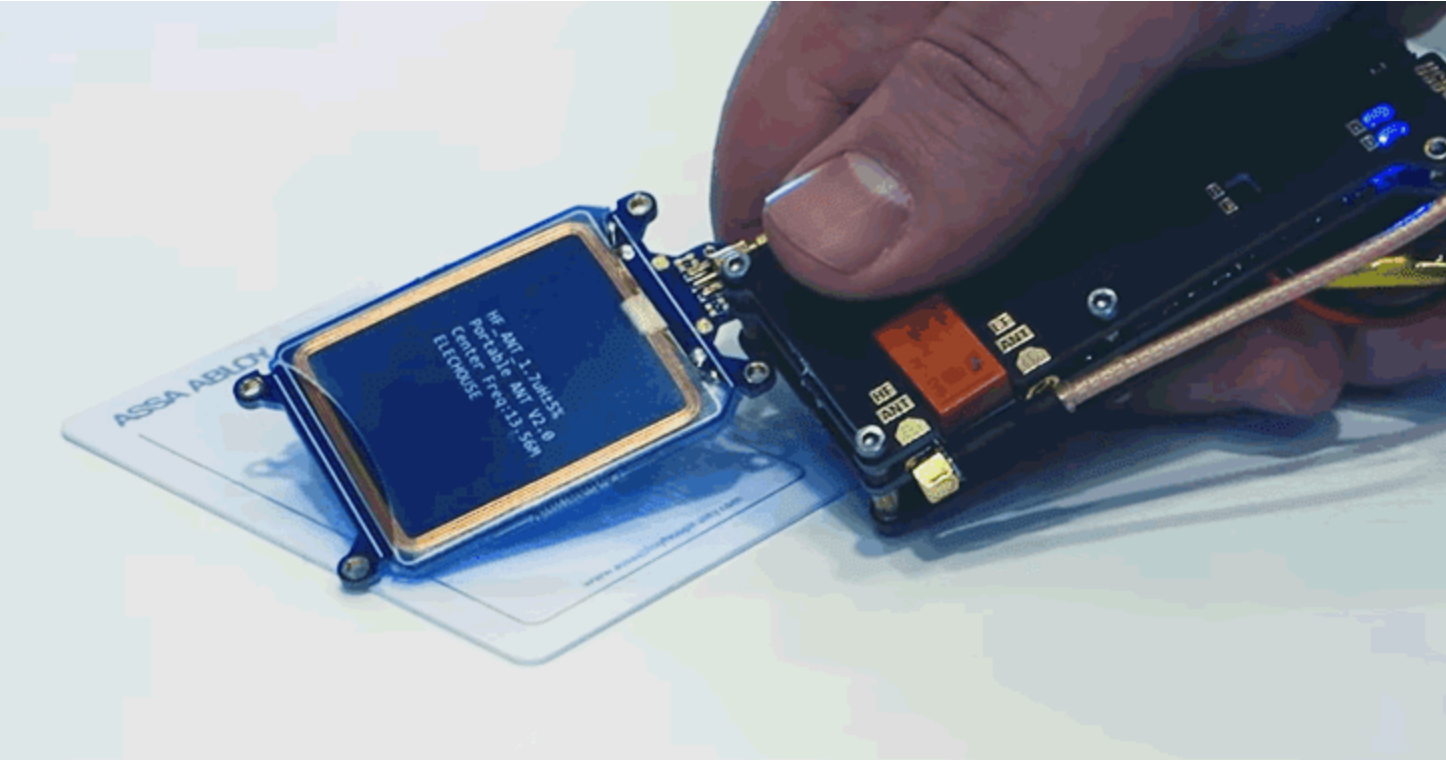
To obtain the electronic key (RFID or magstripe), an attacker could read the data remotely by standing close to a hotel guest or employee having a keycard in his pocket, or simply could book a room and then use that card as the source.
The attacker would then need to buy a portable programmer for a few hundred dollars online to overwrite it, and therefore creating a master key within minutes.
However, F-Secure says it used its custom software which made this particular hack possible, and for obvious reason, the researchers will not be releasing it.
The custom-tailored device (actually an RFID reader/writer) is then held close to the target lock, which tries different keys in less than one minute and locates the master key and unlocks the door.
Now, you can either use this custom-tailored device as the master key to open any door in the facility or write the master key back to your keycard. Once done, you can now access any room in the hotel using the master key.
“You can imagine what a malicious person could do with the power to enter any hotel room, with a master key created basically out of thin air,” said Tuominen in a blog post published Wednesday. “We don’t know of anyone else performing this particular attack in the wild right now.”
Researchers have also provided a video demonstration, which shows the hack in action.
Assa Abloy released software fixes for its systems in February 2018, and the updates have been made available to the affected facilities.
“I would like to personally thank the Assa Abloy R&D team for their excellent cooperation in rectifying these issues,” Tuominen said. “Because of their diligence and willingness to address the problems identified by our research, the hospitality world is now a safer place. We urge any establishment using this software to apply the update as soon as possible.”
F-Secure has not yet released full technical details of the hack. Also, there’s no evidence that the hack has ever been exploited in the wild, but cyber attacks against hotels are not at all surprising.
About a year ago, we saw how hackers forced a luxurious hotel in Austria to pay ransom in Bitcoin, after ransomware hit the hotel’s IT system, locking hundreds of guests out of their rooms.