Verizon security researchers along with calibration from more than 50 other organizations have released the Verizon 2014 Data Breach Report (download HERE). My colleague Aamir Lakhani (www.DrChaos.com) and I would like to share our opinion of the trends we saw after analyzing the findings. We encourage you to download the report, along with other sources we reference in this post.
In 2012, the Verizon Data Breach report along with Mandiant (now FireEye) APT1 report (download HERE) found that geopolitical and foreign nation attacks were on the rise. These reports demonstrated a real threat to businesses and organization causing financial loss, intellectual property compromise, and destabilization in business and brand worthiness.
In the current report, Verizon dubbing 2013 as the year of the retailer breach. Attackers were relentlessly attacking retailers. It seemed every week there was an occurrence where personal and private information was being compromised. The Target breach (source: HERE) was one of the most publicized breaches of 2013. However, others made the breach list such as Michaels, Schnucks, Living Social, Evernote, and Adobe.
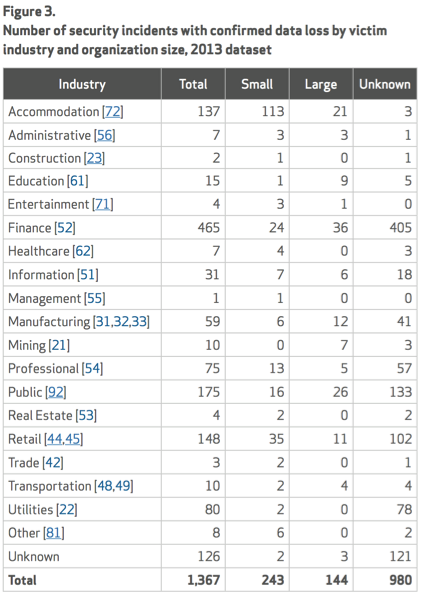
The data shows there are specific industries that appear to be more of a target for cyber attacks than others. It states, “certain sectors will always skew higher in the victim count given their attractiveness to financially motivated actors”. This would explain why a large amount of cyber attacks is around financial scams. We also saw a general increase in other financially motivated crimes such as “smash and grab”, credit card skimmers, and attacks against point of sale systems.
The famous criminal Willie Sutton was once asked why he robbed banks, and his response was simple, eloquent, and humorous: Because that’s where the money is .. Now ask yourself why the majority of malware is released on windows platforms and infection method is web based? We believe its because of the critical mass and popularity of the systems combined with the rate of return. Basically it comes down to this simple fact: Attackers will target where victims are spending the most time. This contradicts the old thought “I won’t be at risk if I don’t spend time on malware infested sources such as free software or pornography websites”. As shown in this report and particularly where the largest amounts of attackers were seen, hackers are targeting online retail because that’s where the growth was in 2013 for shopping. Accenture pointed this out in a report last year claiming more people will shop online for Christmas gifts than in stores (resource). More online spending means more online targets. The next diagram shows Finance and Retail being the top targets of 2013.
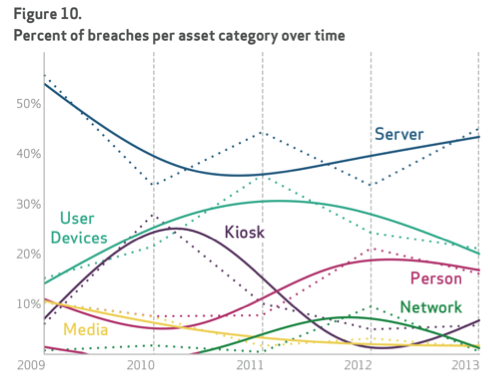
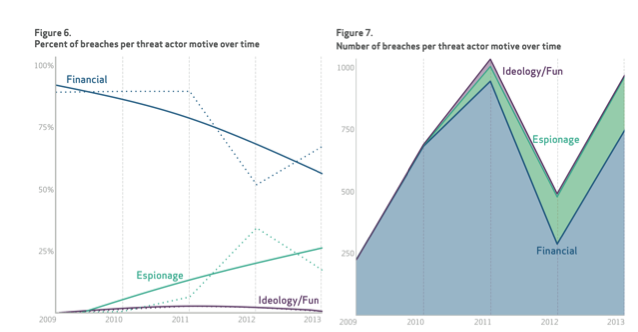
The industry breakdown demonstrates all business sectors saw some form of threat and next image shows how breach types continues to change every year without consistent patterns in any area. Why does this report show fluctuation between attack types each year? Our guess is attackers are changing according to where security defenses are investing research. If network based appliances become a hot consumer item, attackers will focus on servers. When the “next generation” technologies harden servers, endpoints will rise as the target. It’s a constant changing cat and mouse game between attackers and defenses developed by leading security companies.
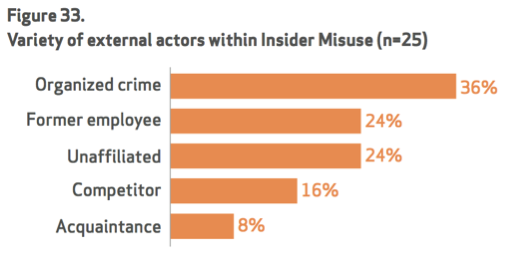
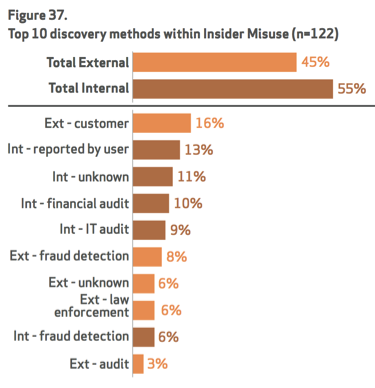
The lesson learned from this type of report is anybody can be a target. Many organizations we work with will take the most minimalistic approach to cyber defense because they feel they are not targets or do not have enough revenue to attract the attention of organized crime. Reports like this show they are wrong. Especially with last year’s focus on small to medium business as being heavily targeted as shown in the report. Even if you think your organization is at low risk for external attacks, there remains the possibility of insider misuse and errors that harm systems and expose data. The next few diagrams show the top insider threats are executed by organized crime rather than formal employees and typically discovered by external parties rather than internal security defenses. We find many of our customers forget to include post compromise technology in their security defense strategy, which makes sense why the data shows this way.
Another common misconception is financial institutes protect people if they are compromised. That is only true if fraudulent credit card charges appear on your credit card account. There is very little recourse if money is transferred or wired from your account. Every year, thousands of people have their bank accounts wiped out because their credentials got lost of stolen through malware. Again, we see in the Verizon Data Breach example below that financial cyber attacks are common and could happen outside of what users are able to track. An easy example of this is how anybody shopping at Target prior to the breach doesn’t know for certain if or what data was stolen during the infamous breach. They are just advised to change passwords and look for unknown charges.
These attacks are going to continue. As a consumer, we recommend that you take advantage of some free consumer services by signing up with the Do Not Call registry and the Opt-out Program. We also recommend using a identity protection service that provides full recovery services. Victims of identity theft reporting fraudulent charges are generally easy to take care of. However, what about everything else? Tickets and criminal cases against you, bank accounts opened in your name, lawsuits are just some of the headaches victims of identity theft have to deal with . Most identity service agencies do not provide protection to victims against these types fraudulent acts. Those that do, offer very limited services and will charge for their time.
As a network administrator, its best practice to look at all areas of your network from a BEFORE, DURING and AFTER attack perspective. Consider how hackers can access your network and limit threats to only trusted sources. Have detection and prevention in place in the event a trust source does launch an attack. Lastly have a means to detect if a attack gets through because as shown in this report, it will eventually happen. We look at being compromised like getting the flu … its happens every once in a while but we remediate it with medicine before it kills us. If you can’t tell if you are sick or stop somebody that has breached your defenses, they will kill your business through exposing your internal secrets and cause negative finical impact. This includes all areas of your network from datacenter to remote user.