Cisco announced the End-of-Sale date for their traditional Intrusion Detection and Prevention product line. You can find a link to the announcement HERE, which includes a list of affected products. Here is the formal announcement as well as suggested replacement technology.
The formal announcement states
“Cisco announces the end-of-sale and end-of life dates for the Cisco Intrusion Prevention System. The last day to order the affected product(s) is April 26, 2015. Customers with active service contracts will continue to receive support from the Cisco Technical Assistance Center (TAC) as shown in Table 1 of the EoL bulletin. Table 1 describes the end-of-life milestones, definitions, and dates for the affected product(s). Table 2 lists the product part numbers affected by this announcement. For customers with active and paid service and support contracts, support will be available under the terms and conditions of customers’ service contract.“
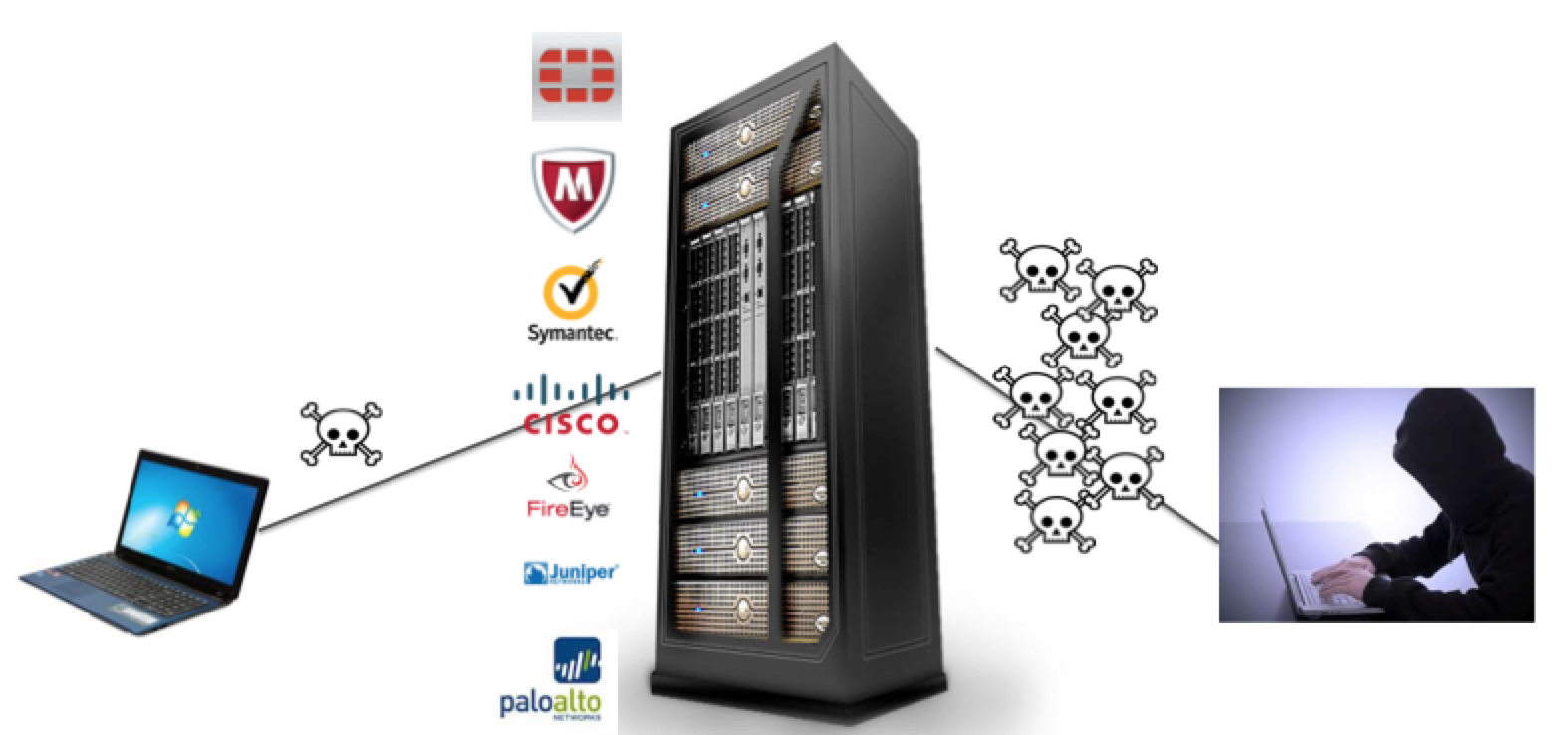
This was probably expected by many people based on the innovations with Sourcefire and other technologies. The focus for Cisco is stopping threats, which must go behind traditional detection capabilities. The reason why is there isn’t a product that can detect all attacks or as many say “there isn’t a silver bullet“. If somebody creates one, it will not last long as the hackers will buy it and build attacks around it as shown in the next image.
So what should you consider to replace an existing EoS security appliance? Cisco’s latest offerings focus on stoping attacks using a layer of security defenses. Those layers are Pre-attack, Application Visibility and Controls, IPS/IDS and Detecting Day Zero. Pre-attack means blocking known bad sources, which can carve off around 80% of common attacks (more on this concept HERE). The simple concept is people won’t hack you from their home network based on not wanting to be identified. They will use random sources that are built for the purpose to attack you. We can identify these sources based on how long they have been online, the type of content, where they are based out of, etc and block them before they have a chance to attack you.
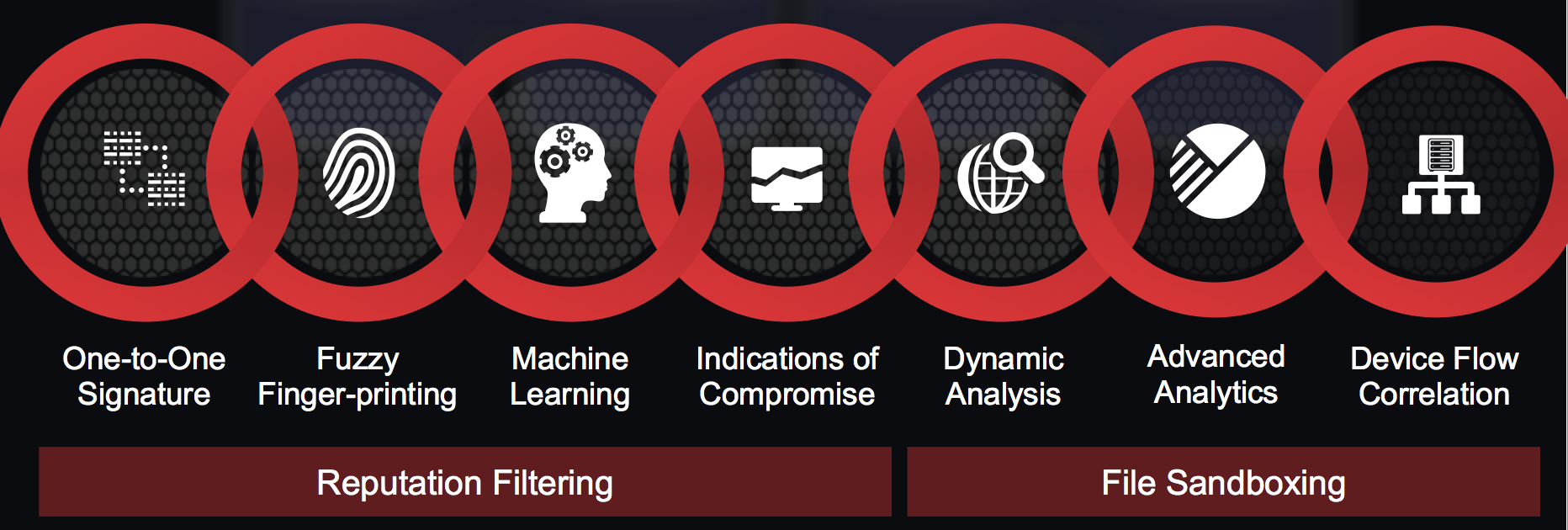
Application Visibility and Controls allows you to block anything from non-appropriate work content (gambling, adult websites, etc) to applications such as Farmsville on Facebook or Dropbox apps on iPads. IPS/IDS blocks attacks but must know what to look for. Cisco’s latest IPS capabilities that replaces the EoS hardware can not only do this, but also self tune based on traffic it sees on your network. This means if Cisco sees you have a Microsoft Server or users running Firefox, it will auto enable signatures to protect those assets. The same concept goes for removing signatures that are enabled however never used.
The last layer is detecting and preventing Day Zero threats on your network with Advanced Malware Protection. This is a combination of Sourcefire and Threat Grid technology providing visibility of every single file that comes on your network. Cisco can analyze files locally as well as using various cloud based detection methods to detect threats. Once a threat is identified, Cisco can go back in time and tell you every device that has that file, any variations of the threat and who was the first person to bring it on to your network. You can find more on this technology HERE.
These security features offered by Cisco come in many flavors. You can connect a network device to the cloud using Cloud Web Services, leverage the cloud but have onsite hardware using Meraki appliances, purchase the latest ASA firewalls and enable Firepower services or invest in dedicated Firepower appliances. All of these offerings can consolidate the features from the recently announced EoS cisco IPS appliances along with other technologies such as Content Filters, Firewalls, VPN Concentrators and Day Zero detection platforms.
Check out www.cisco.com/go/security to learn more about these and other offerings.