I’ve said this many times before … the Internet is full of bad things. Of those bad things, one of the most common threats is Phishing attacks. Wiki defines phishing as “the act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication”. The majority of successful phishing attacks clone popular social networking sources and provide hyperlinks with the hope a target will click the link without questioning the authenticity of the source.
I wrote a post about what to look for regarding fraud email and craiglist sales HERE and 2 example craiglist cons HERE. The concepts are generally the same regarding identifying phishing attackers however in some cases, the attack will be a clone of a real message or website, which makes it very difficult to detect. Best practices is THINK BEFORE YOU CLICK! Here are some examples why this is important.
Example 1:
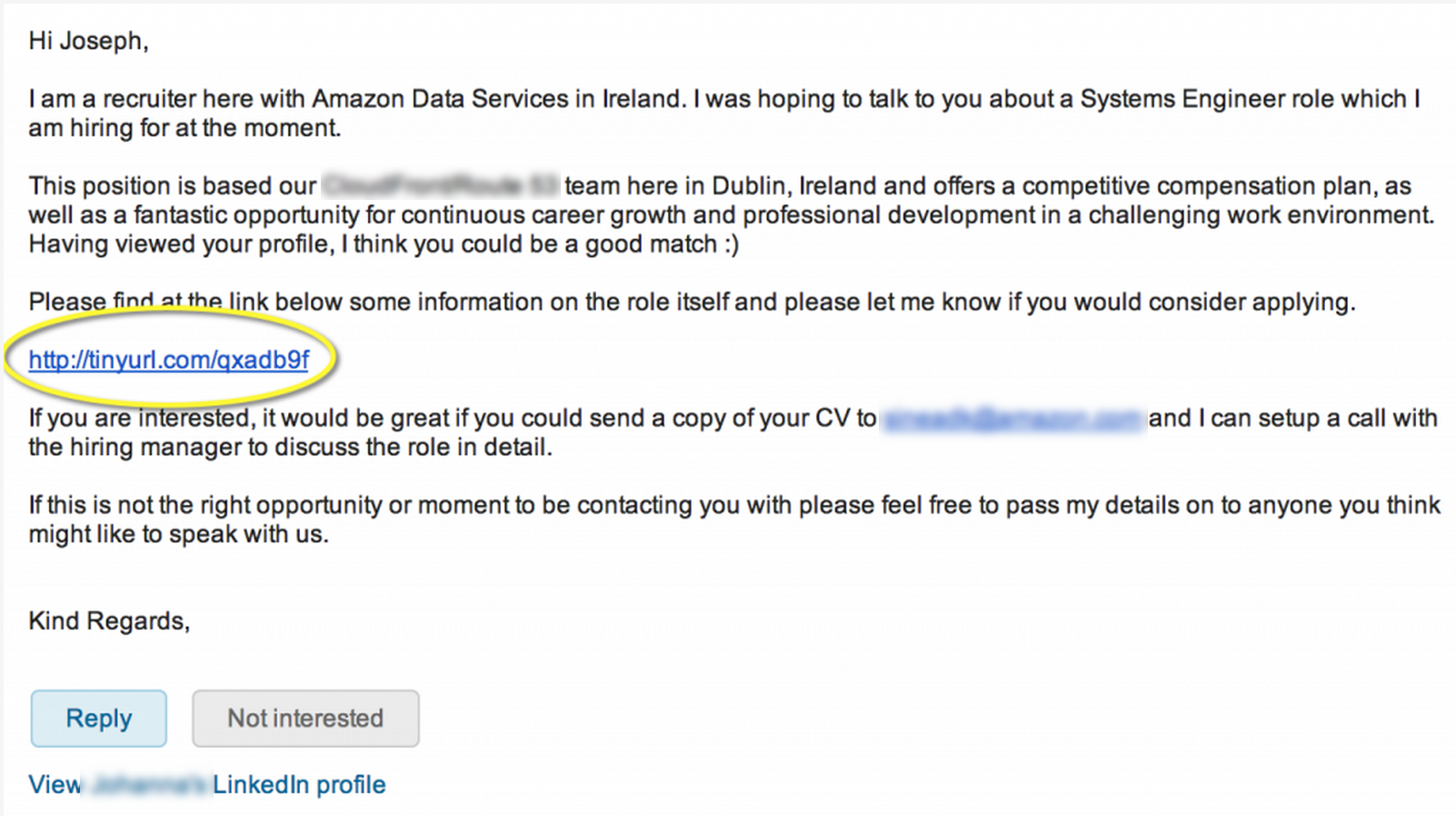
LinkedIn Phishing Example
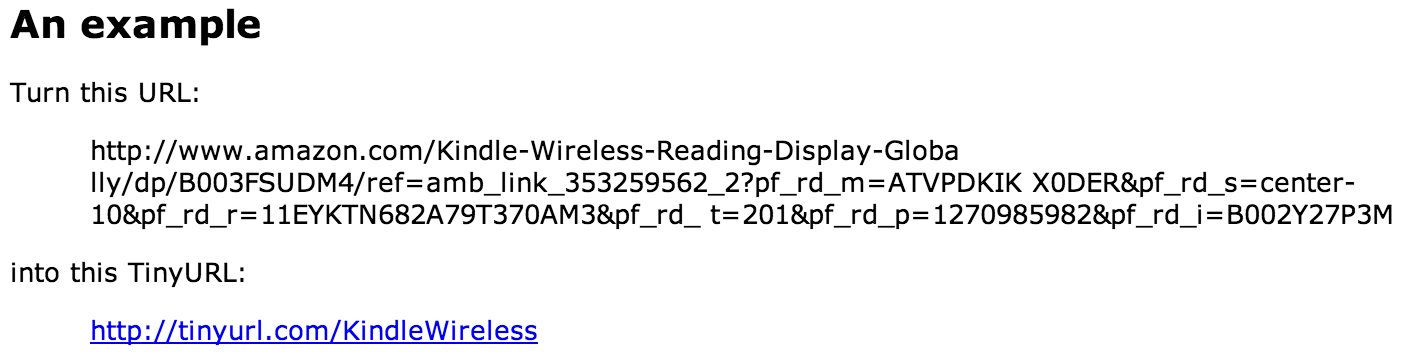
Example of TinyURL making a URL shorter
Here is an example of a request to view a possible job opportunity (see image above). Notice that the hyperlink is using tinyurl.com to hide the actual link. Tinyurl provides a free service to shorten long hyperlinks. The problem is … what is the original link? Is it really link to a job explanation or something malicious? If you don’t know, don’t go.
Example 2:
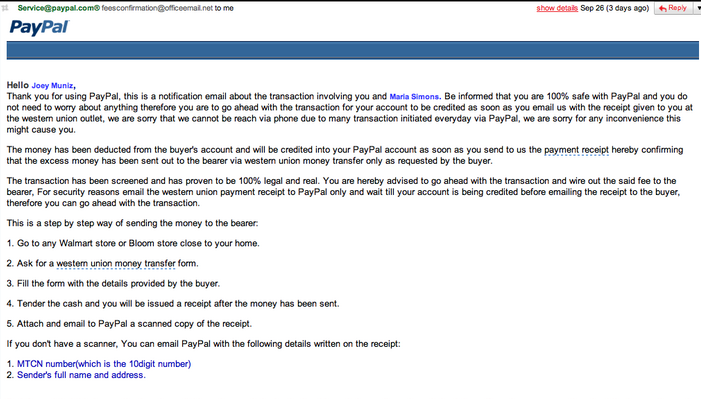
Phishing Email Example
Here is an example of a typical phishing attack with social engineering elements. This email looks like it came from Paypal and states I have funds waiting for me. There are links that suppose to send me to Paypal so I can verify the funds. In reality, those links take me to where the attacker wants me to go. Many of these attacks will have a cloned login screen of Paypal with the hope I login so the attacker can obtain my credentials. Usually, these fake systems will redirect the victim to the real Paypal site once he/she logs into the fake Paypal server with the hope the victim never knows they have logged into a fake system.
This attack was pretty lame however I have heard of more sophisticated attacks that install malware that makes the host system believe it has funds in the bank. It works by acting as a man-in-the-middle updating the screen with wrong data received from the real banking web source. The only way to verify this more advanced version of the attack is actually calling the bank or accessing the web source directly using another browser that the malware isn’t familiar with.
For this example, I sent the email to Paypal’s fraud center knowing they would confirm it as fake. I also opened a browser to access my Paypal account directly rather than using the untrusted hyperlinks. As expected, there were not funds in my account and Paypal confirmed it was bogus.
The social engineering side of this attack is the hope I provide sensitive information or wire funds to the attacker. There are a lot of things that give away this attacker such as the poor grammar in the introduction. See this post regarding indicators for web cons HERE. If somebody asks you to wire money in a untraceable format such as western union, most likely they are full of it.
Example 3:
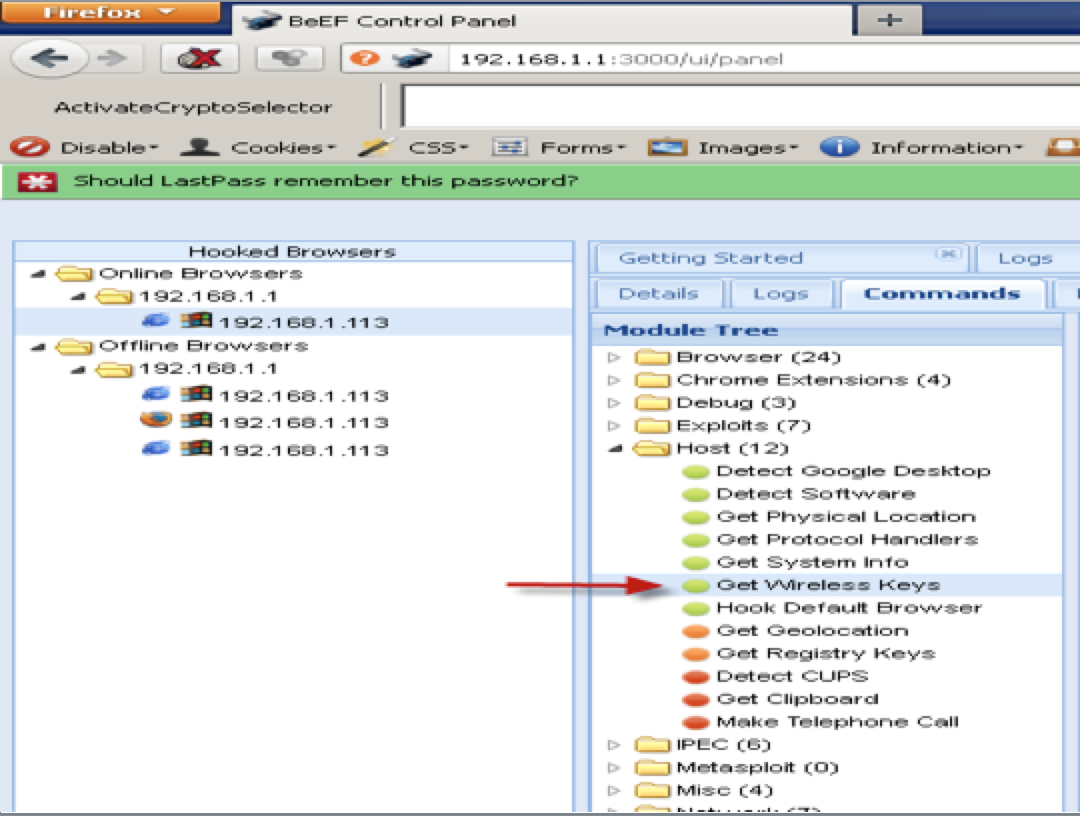
An more sophisticated example of abusing hyperlinks to expected sources is using a attack tool like BeEF (more on BeEF found HERE) and exploiting targets that click a distraction. For example, Aamir Lakhani and I posted xmas cards on Facebook (more on the emily project can be found HERE). When a victim would click the xmas card, they would see the card play (aka the distraction) while we attacked their systems. The victim expected a xmas card however they didn’t know we were hosting the xmas card as a decoy while we scanned their system. Another very popular example of this is streaming illegal movies with the goal of providing that service in exchange for time to hack your computer.
BeEF exploiting a system that has clicked a fake hyperlink
Example Of Free Movie Streaming Site
Example 4:
One suggestion I live by is NEVER trust a QR code. I’m not a robot and can’t read where it sends me so how do I know if the source is trustworthy? It is very easy for a hacker to post a attack server and phish with QR codes that appear to be something else such as coupons or access to freeware.
using www.qrstuff.com to create a QR code
To summarize, you really need to question anything that could expose your system to malicious sources such as hyperlinks and QR Codes. Best practice is accessing sources directly rather than using quick links if possible. Also, use the advice most mothers give … “If it seems too good to be true, it probably is” … aka if you see free software, movies, money, etc, most likely there is a reason why it is available.