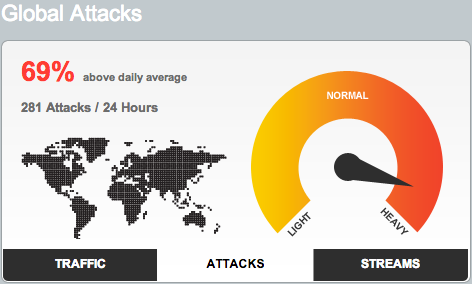
Press around the DDoS attack Operation Ababil has caught the attention of many of our customers. This sophisticated cyber strike used a combination of three separate rootkits targeting webservers, which produced a very high upstream attack method on multiple companies simultaneously. The scary part about Operation Ababil was it was designed to bypass standard DDoS defense methods. This clearly demonstrates there isn’t a silver bullet for addressing advanced DDoS attacks. Distributed Denial of Service DDoS, web application and DNS infrastructure attacks represent some of the most critical threats to enterprises today. Here is some suggestions for a reference architecture to defend against these an other advanced threats.
 The best approach for defending against advanced DDoS as well as other cyber attacks is having multiple security solutions using different methods to detect malicious activity for both internal and external threats. For internal threats, it’s critical to have a well-designed and mature security infrastructure that includes components such as firewalls, IPS/IDS, email and content / application security solutions. Similar security standards need to be applied to endpoints as well as in the datacenter such as proper patch management, anti-virus and anti-malware. It’s important to enable DDoS defense features for these tools. For example, some best practices are leveraging ACLs for ingress and egress filtering, rate limiting ICMP and SYN packets as well as verifying if the source IP of packets have a route from where they arrived.
The best approach for defending against advanced DDoS as well as other cyber attacks is having multiple security solutions using different methods to detect malicious activity for both internal and external threats. For internal threats, it’s critical to have a well-designed and mature security infrastructure that includes components such as firewalls, IPS/IDS, email and content / application security solutions. Similar security standards need to be applied to endpoints as well as in the datacenter such as proper patch management, anti-virus and anti-malware. It’s important to enable DDoS defense features for these tools. For example, some best practices are leveraging ACLs for ingress and egress filtering, rate limiting ICMP and SYN packets as well as verifying if the source IP of packets have a route from where they arrived.
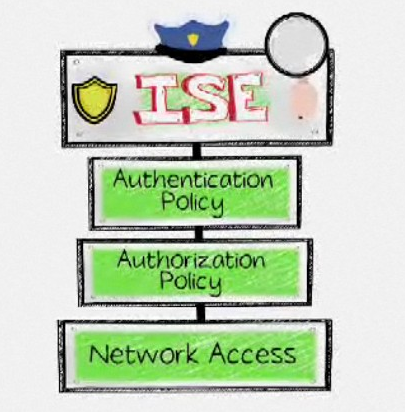
 Standard internal security solutions are important however will not completely protect you from advanced DDoS and other cyber threats. Security administrators need full network visibility to quickly identify anomalies regardless of their location or form of communication. Best practice to identify malicious activity inside your network is monitoring the wire using a NetFlow or Packet capture approach (more can be found HERE and HERE). It’s also important to match identity to devices found. An example is how Cisco offers integration with its flagship access control solution, Identity Services Engine ISE, to network forensic tools such as Lancope, NetWitness and most major SIEMs. Having a tuned monitoring solution will dramatically improve reaction time to internal cyber threats.
Standard internal security solutions are important however will not completely protect you from advanced DDoS and other cyber threats. Security administrators need full network visibility to quickly identify anomalies regardless of their location or form of communication. Best practice to identify malicious activity inside your network is monitoring the wire using a NetFlow or Packet capture approach (more can be found HERE and HERE). It’s also important to match identity to devices found. An example is how Cisco offers integration with its flagship access control solution, Identity Services Engine ISE, to network forensic tools such as Lancope, NetWitness and most major SIEMs. Having a tuned monitoring solution will dramatically improve reaction time to internal cyber threats.
Most administrators associate DDoS as an outsider attack. We hear customers claim their service provider is responsible for providing DDoS defense however a service providers mission of delivering service will always outweigh concerns for security. For this reason, it’s critical to invest in an external DDoS defense solution as well as verify what security tools are included with your service provider contract. The two large players for external DDoS defense are Akamai and Arbor networks. Akamai’s Kona Site Defender provides DDoS mitigation and Application Layer Protection for most service providers. If your service provider uses Akamai, verify if they invested in the additional Kona suite. The leader for enterprise DDoS defense is Arbor (more can be found HERE). Arbor’s Peakflow, Prevail and cloud subscription services are the defacto standard for DDoS defense at the vast majority of our Tier-1 and Tier 2 ISPs as well as enterprise customers. Online DDoS monitoring services are also an option offered by companies such as Prolexic which are an alternative to purchasing equipment.
To summarize the DDoS defense architecture, an enterprise should focus on both internal and external defense. The internal network should have a solid security foundation, monitor the wire for devices that access the network and match identity to those devices to distinguish what is permitted from rouge devices. Investments should be made in external defenses that offer the ability deflect DDoS traffic such as SYN Floods or UDP Floods as well as authenticating valid traffic at the network edge. Best practice is using DDoS solutions that leverage a large customer base via cloud services to improve reaction time as a community. Its also wise to question your service provider for what security solutions are included with your service package. Having this blend of internal and external security solutions will dramatically improve your chances against todays advanced persistent threats such as Operation Ababil.