If you are internet facing, you are vulnerable to Distributed Denial of Services or DDoS attacks. Attacking network services is on the rise as the price for computing power decreases and people become more dependent on technology. Studies from leading service providers show DDoS attacks have grown from 9 to 500 Gbps in the last five years. Botnets are becoming an underground commodity that can be rented for as low as 10 dollars an hour to launch strategic DDoS attacks. Governments are investing in military strategies based on the ability to interrupt enemy computer services through targeted DDoS attacks. These attacks are indeed a weapon of mass disruption.
If you are internet facing, you are vulnerable to Distributed Denial of Services or DDoS attacks. Attacking network services is on the rise as the price for computing power decreases and people become more dependent on technology. Studies from leading service providers show DDoS attacks have grown from 9 to 500 Gbps in the last five years. Botnets are becoming an underground commodity that can be rented for as low as 10 dollars an hour to launch strategic DDoS attacks. Governments are investing in military strategies based on the ability to interrupt enemy computer services through targeted DDoS attacks. These attacks are indeed a weapon of mass disruption.
Most customers who survive a DDoS attack will experience serious downtime and lost revenue. Older DDoS attacks primary involved saturating bandwidth and network services with bogus traffic. The latest trend of DDoS attacks are targeting applications, which are harder to detect and require less computing power to execute. Some DDoS attacks focus on security tools (example overloading TCP state tables) so the security defenses become bottlenecks and eventually the source of network failure. Other DDoS attacks target key infrastructure such as DNS or other critical services. The area of risk for DDoS is pretty much your entire network.
Companies tend to point blame at their service provider for external DDoS attacks. Service providers offer limited protection due to regulations and unable to deal with data once it leaves their control. There are companies such as Neustar, Prolexic and VeriSign that provide 24/7 DDoS monitoring services and help leading service providers battle DDoS attacks. While monitoring services is a good option, the best approach is to invest in your own DDoS defenses against insider threats, external flooding and targeted application attacks.
 Advanced insider threats are difficult to identify. Standard security solutions leverage signature and behavior based technologies however most attackers have knowledge of these defenses. To bypass these solutions, attackers develop day zero targeted threats that throttle their activity to stay under the radar. One way to catch this behavior is leveraging NetFlow using tools like Lancope (more found HERE). Another way is monitoring packets on the wire using tools like NetWitness (more found HERE). Security Information and Event Management (SIEM) tools are a popular way to view events from multiple security solutions so administrators can quickly identify an attack (more found HERE). Best practice is monitoring the wire along with leveraging a management system aggregating events from all internal security devices.
Advanced insider threats are difficult to identify. Standard security solutions leverage signature and behavior based technologies however most attackers have knowledge of these defenses. To bypass these solutions, attackers develop day zero targeted threats that throttle their activity to stay under the radar. One way to catch this behavior is leveraging NetFlow using tools like Lancope (more found HERE). Another way is monitoring packets on the wire using tools like NetWitness (more found HERE). Security Information and Event Management (SIEM) tools are a popular way to view events from multiple security solutions so administrators can quickly identify an attack (more found HERE). Best practice is monitoring the wire along with leveraging a management system aggregating events from all internal security devices.
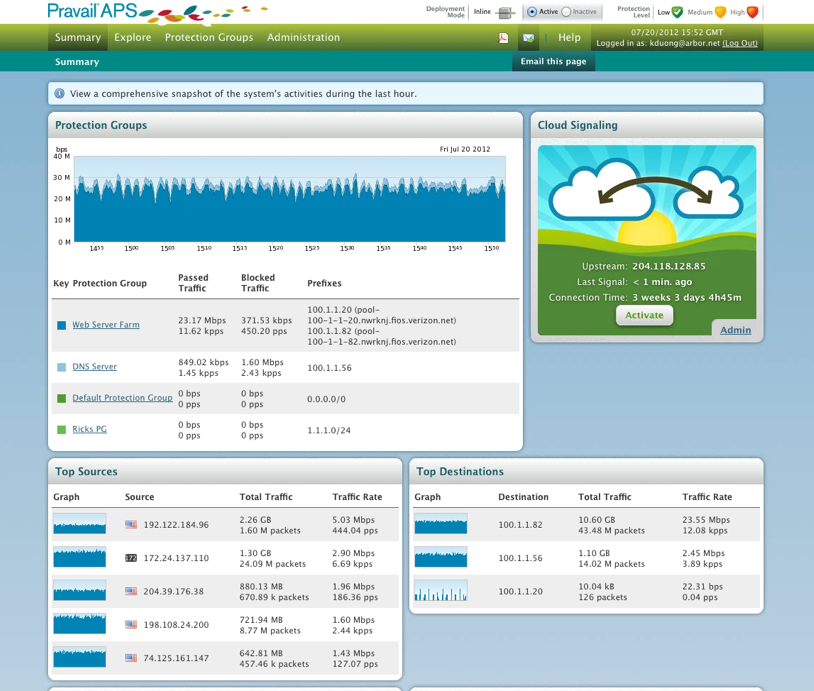
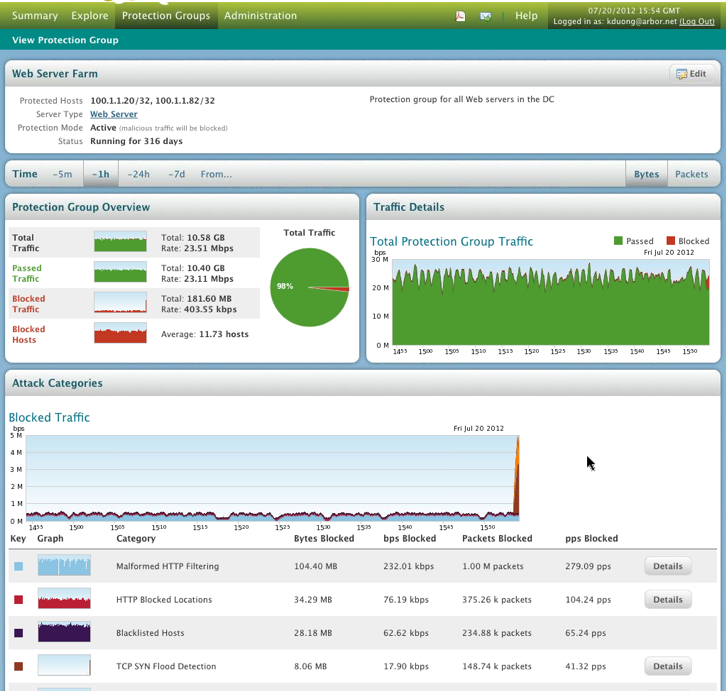
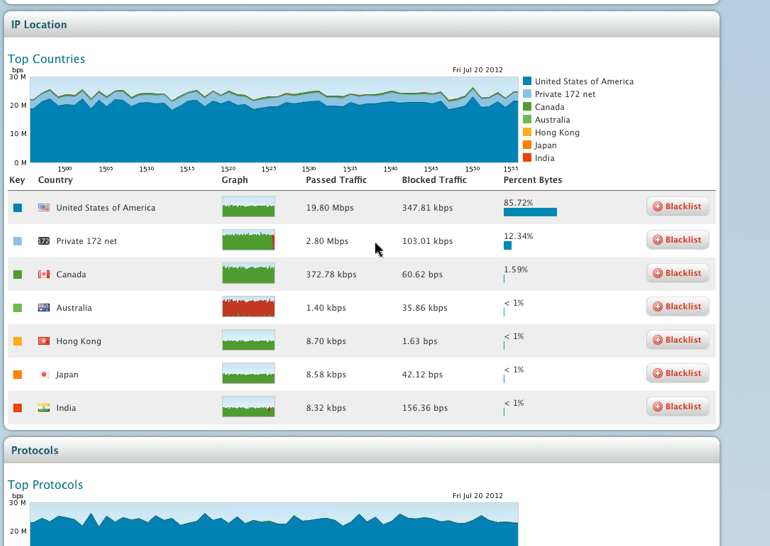
External threats such as targeted DDoS attacks are tougher to deal with. Large vendors like Junipor and Cisco have partnered with the leader for this space, Arbor Networks to address the DDoS landscape (Example Cisco and Arbor released “Clean Pipes” explained HERE.) Arbor offers perimeter and cloud based solutions that address flooding and application attacks. They also offer correlation between their products, cloud updates from their security center and reputation scoring from their large client base. Their flagship solution is Prevail (see screenshots). Prevail makes it easy to understand traffic patterns, identify threats and react to attacks by switching from low to high interrogation of traffic for specific protection groups. Check out their website for more information on their solutions.
MAIN DASHBOARD
Viewing Protection Groups
Viewing Top Talkers
 DDoS is a serious threat vector since standard security solutions focus on Integrity and Confidentiality but not Availability. My expectation is there will be a lot more DDoS attacks in the news. Hopefully it’s not your organization on the front page.
DDoS is a serious threat vector since standard security solutions focus on Integrity and Confidentiality but not Availability. My expectation is there will be a lot more DDoS attacks in the news. Hopefully it’s not your organization on the front page.