I have been involved with a ton of conversations regarding requirements for CMMC. Questions typically involve the following
- What part of my organization will need to meet CMMC?
- Do I need to go level 1 for FCI data, level 3 for CUI data or even higher?
- Can I compartmentalize anything requiring CMMC?
- What is the cost and needed steps to becoming certified?
- What happens if I don’t meet CMMC?
My general answer for many of these questions is first, the requirements for CMMC are based on best practices from NIST, which all organizations should be doing anyway. CMMC is different based on how its forcing organizations to follow best practices rather than suggesting things to be done. Can you compartmentalize CMMC requirements … maybe. Do you need to go higher than level 1 … maybe. What is the cost to become CMMC certified … it depends. Sorry, but the answer to many of these questions are very specific to your organization and how you do business. It is best to start looking into this now however, rather than waiting until you find you are no longer able to access certain contracts as meeting CMMC will take you time and something you can’t quickly buy your way into.
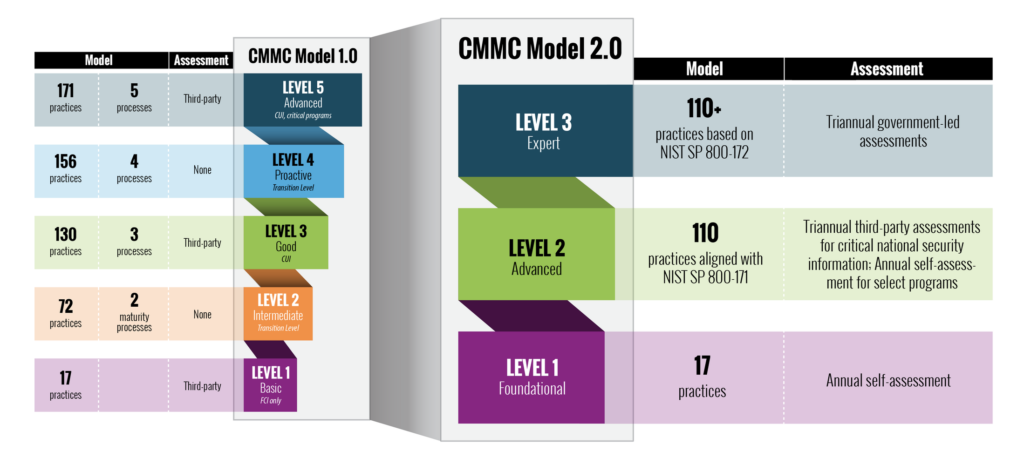
This month (nov 2021), the CMMC board released version 2.0 for CMMC. There are some significant changes that were made. The details of those changes can be found below (taken from THIS page). A short summary of the changes are the following:
- 5 Levels have been reduced to 3
- Level 2 is called Advanced, contains 110 practices (vs the previous level 3 cover 130 practices) and very aligned to NIST SP 800-171. Level 2 is likely what you need for CUI
- Level 3 is called Expert and based on 130+ practices. Level 3 is the highest and likely what you need for very sensitive data such as contracts dealing with chemical warfare items.
- Level 1 requires a annual self-assessment vs in the passed required a third party assessment. This one is HUGE news.
My take on these changes is the CMMC board heard feedback about how hard it would be for many organizations to meet level 1 and softened the requirements. See the diagram below for details as well as a more detailed article on CMMC v2.0. Here is that article ….
Cybersecurity is a top priority for the Department of Defense.
The Defense Industrial Base (DIB) is the target of increasingly frequent and complex cyberattacks. To protect American ingenuity and national security information, the DoD developed CMMC 2.0 to dynamically enhance DIB cybersecurity to meet evolving threats and safeguard the information that supports and enables our warfighters.
Overview of the CMMC Program
The Cybersecurity Maturity Model Certification (CMMC) program enhances cyber protection standards for companies in the DIB. It is designed to protect sensitive unclassified information that is shared by the Department with its contractors and subcontractors. The program incorporates a set of cybersecurity requirements into acquisition programs and provides the Department increased assurance that contractors and subcontractors are meeting these requirements.
The framework has three key features:
- Tiered Model:CMMC requires that companies entrusted with national security information implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for information flow down to subcontractors.
- Assessment Requirement:CMMC assessments allow the Department to verify the implementation of clear cybersecurity standards.
- Implementation through Contracts:Once CMMC is fully implemented, certain DoD contractors that handle sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
The Evolution to CMMC 2.0
In September 2020, the DoD published an interim rule to the DFARS in the Federal Register (DFARS Case 2019-D041), which implemented the DoD’s initial vision for the CMMC program (“CMMC 1.0”) and outlined the basic features of the framework (tiered model, required assessments, and implementation through contracts). The interim rule became effective on November 30, 2020, establishing a five-year phase-in period.
In March 2021, the Department initiated an internal review of CMMC’s implementation, informed by more than 850 public comments in response to the interim DFARS rule. This comprehensive, programmatic assessment engaged cybersecurity and acquisition leaders within DoD to refine policy and program implementation.
In November 2021, the Department announced “CMMC 2.0,” an updated program structure and requirements designed to achieve the primary goals of the internal review:
- Safeguard sensitive information to enable and protect the warfighter
- Dynamically enhance DIB cybersecurity to meet evolving threats
- Ensure accountability while minimizing barriers to compliance with DoD requirements
- Contribute towards instilling a collaborative culture of cybersecurity and cyber resilience
- Maintain public trust through high professional and ethical standards
Key Features of CMMC 2.0
With the implementation of CMMC 2.0, the Department is introducing several key changes that build on and refine the original program requirements. These are:

Streamlined Model
- Focused on the most critical requirements:Streamlines the model from 5 to 3 compliance levels
- Aligned with widely accepted standards:Uses National Institute of Standards and Technology (NIST) cybersecurity standards

Reliable Assessments
- Reduced assessment costs:Allows all companies at Level 1 (Foundational), and a subset of companies at Level 2 (Advanced) to demonstrate compliance through self-assessments
- Higher accountability:Increases oversight of professional and ethical standards of third-party assessors

Flexible Implementation
- Spirit of collaboration:Allows companies, under certain limited circumstances, to make Plans of Action & Milestones (POA&Ms) to achieve certification
- Added flexibility and speed:Allows waivers to CMMC requirements under certain limited circumstances
Rulemaking and Timeline for CMMC 2.0
The changes reflected in CMMC 2.0 will be implemented through the rulemaking process. Companies will be required to comply once the forthcoming rules go into effect. The Department intends to pursue rulemaking both in Part 32 of the Code of Federal Regulations (C.F.R.) as well as in the Defense Federal Acquisition Regulation Supplement (DFARS) in Part 48 of the C.F.R. Both rules will have a public comment period. Stakeholder input is critical to meeting the objectives of the CMMC program, and the Department will actively seek opportunities to engage stakeholders as it drives towards full implementation.
While these rulemaking efforts are ongoing, the Department intends to suspend the current CMMC Piloting efforts and will not approve inclusion of a CMMC requirement in any DoD solicitation.
The Department encourages contractors to continue to enhance their cybersecurity posture during the interim period while the rulemaking is underway. The Department has developed Project Spectrum to help DIB companies assess their cyber readiness and begin adopting sound cybersecurity practices.
The DoD is exploring opportunities to provide incentives for contractors who voluntarily obtain a CMMC certification in the interim period. Additional information will be provided as it becomes available.


