Hackday posted an interesting post about the credit card skimmers. The original post can be found HERE.
Credit cards are loaded with security features, but the game of cat and mouse goes on. Nefarious syndicates continue to develop technology to steal data in new and innovate ways. After SparkFun did a teardown on some illicit hardware, they were visited by local law enforcement, who requested their help once more.
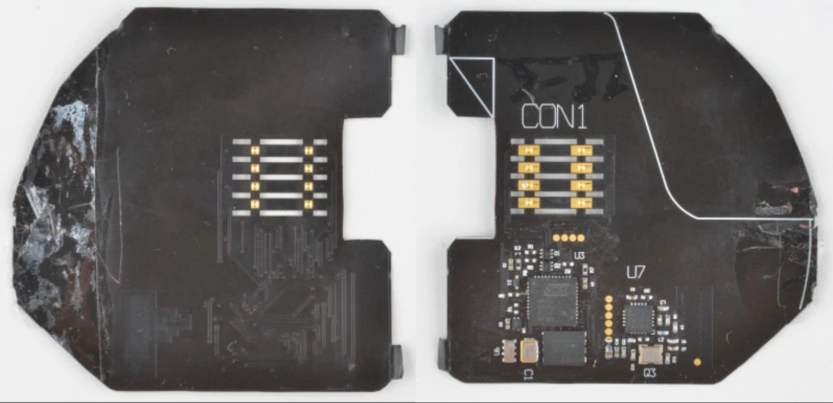
[Nick] from SparkFun refers to the device in question as a “shimmer”. It’s intended to be installed inside the chip reader of a credit card terminal, in between the terminal and the user’s credit card. Fabricated on a flexible film PCB, it’s thin enough to glue inside without being obvious even during maintenance.
The investigation begins with identification of the major components on board, followed by attempts to communicate with the device. Unfortunately, the hardware was largely unresponsive, even when connected to a card reader. In an effort to learn more, a schematic was produced. [Nick]’s analysis raised more questions than answers, and the suspicion is that the hardware may have been damaged at some point. However, the basic capabilities of the device are obvious, given the ability of the hardware to interact with a card via its contacts and offload the data through the onboard nRF24L01 radio module.
Thanks to people like [Nick], and earlier work from SparkFun, we all now have a better understanding of the risks when using payment terminals out in the wild. Unfortunately, unless your local gas station is willing to let you spend 20 minutes disassembling their card reader before paying, there’s not a whole lot the individual can do about it. Stay vigilant, and if you’ve got the skinny on a skimmer, drop us a line.