Today’s threat landscape is loaded with malicious websites, malware and other risks that attack users every nanosecond of the day. There isn’t a single product available that can guarantee protection from cyber threats. Older solutions leveraging static technologies such as signatures are not good enough. The best approach for dealing with advanced threats is continuously monitoring the entire network through layering security technologies.
Today’s threat landscape is loaded with malicious websites, malware and other risks that attack users every nanosecond of the day. There isn’t a single product available that can guarantee protection from cyber threats. Older solutions leveraging static technologies such as signatures are not good enough. The best approach for dealing with advanced threats is continuously monitoring the entire network through layering security technologies.
Cisco is known for network and collaboration products however Cisco also has a very strong security catalog that extends beyond traditional firewalls and IPS appliances. If I had to summarize Cisco’s core visibility technologies for cyber threats, I would highlight Cisco’s capabilities around Access Control, Web Security and partnership with Lancope for Insider Threats.
Access Control is critical for knowing who and what is accessing your network regardless if it’s the LAN, Wireless or remotely using VPN technology. Cisco Identity Services Engine ISE accomplishes visibility of users accessing the network by leveraging how people authenticate along with profiling what types of devices are being used. The screenshot below shows two users with mobile devices obtaining different levels of wireless access. Cisco ISE can also verify if devices meet specified polies by enforcing posture prior to providing network access meaning ensure Joey’s windows 7 laptop has the latest updates and security applications installed.
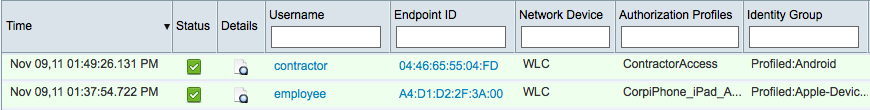 Cisco ISE showing Android with Contractor access and iPhone with Employee mobile access
Cisco ISE showing Android with Contractor access and iPhone with Employee mobile access
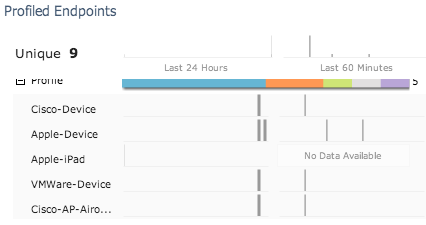 Profiled devices in my home lab. “Apple-Device” is a MACMINI hosting ISE via “VMWare-Device”
Profiled devices in my home lab. “Apple-Device” is a MACMINI hosting ISE via “VMWare-Device”
Some default profiles for Cisco ISE.
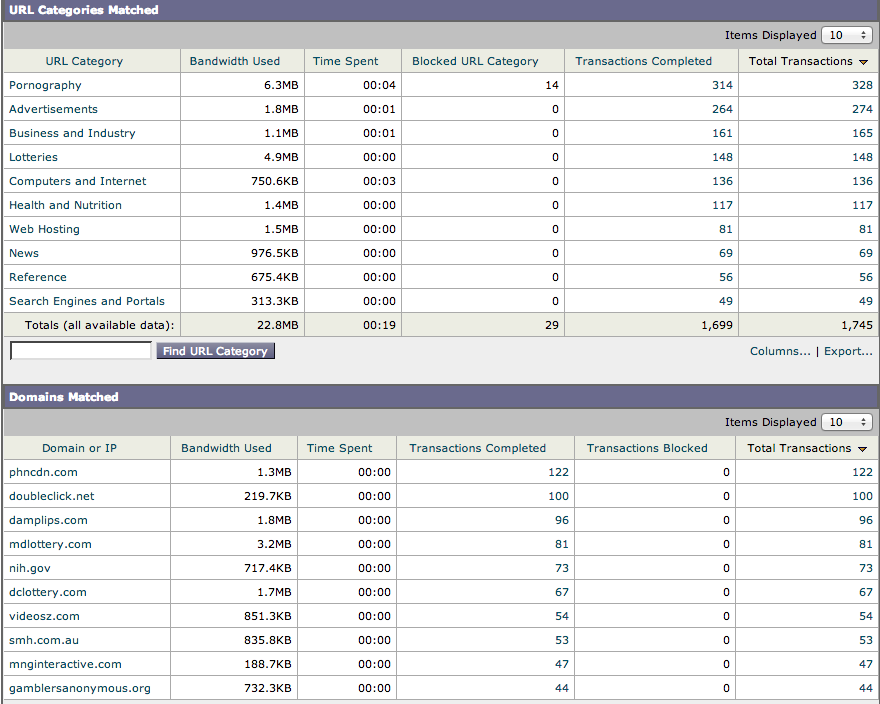
Web Security is crucial for protecting internal users from threats while surfing the public Internet. Cisco Web Security Appliance WSA (previously Ironport) provides visibility of Internet usage as well as security through layered technologies. Network use policies such as denying gambling web content during work hours can easily be enforced through Cisco WSA’s categorized content classes.
Cisco WSA Content Dashboard
The real value of Cisco WSA is going beyond average web content filtering by offering layers of security options that protect users accessing approved content. The first layer is verifying if the web source is a known evil location based on reputation. Reputation can be factors such as where it’s located, how long it’s been up or if it has been marked as a source for malicious activity. If the web source has a safe reputation, WSA scans traffic with a combination of Sophos, McAfee and Webroot engines along with other intelligence looking for malicious behavior. There is also a botnet scanner that sits on a spam port designed to capture users that happen to get compromised and have malware phone home activity from their devices. The botnet scanner is a first step towards identifying insider threats but not good enough.
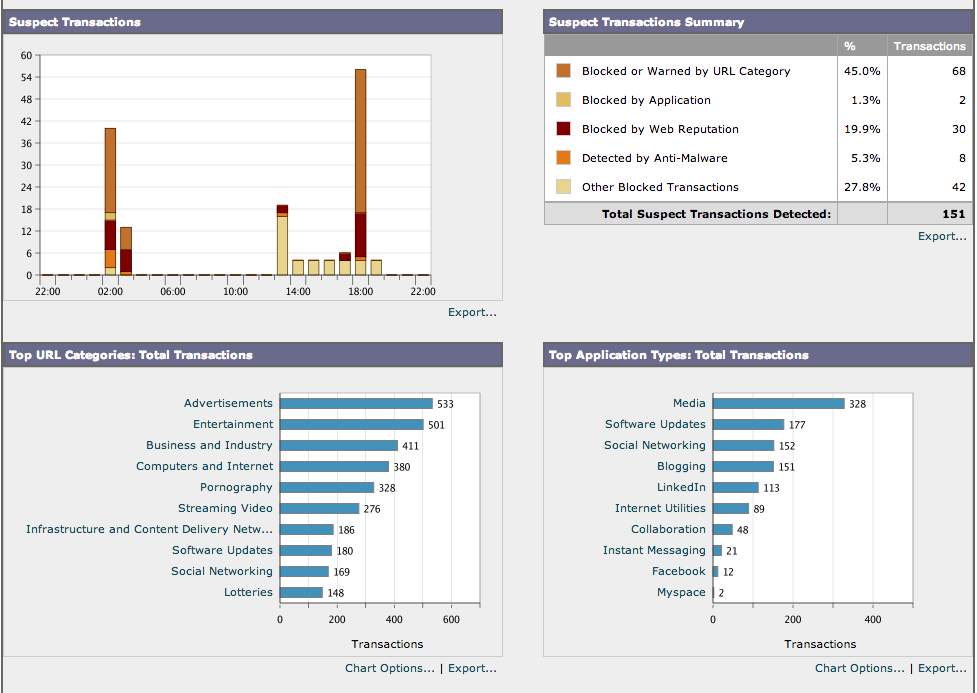
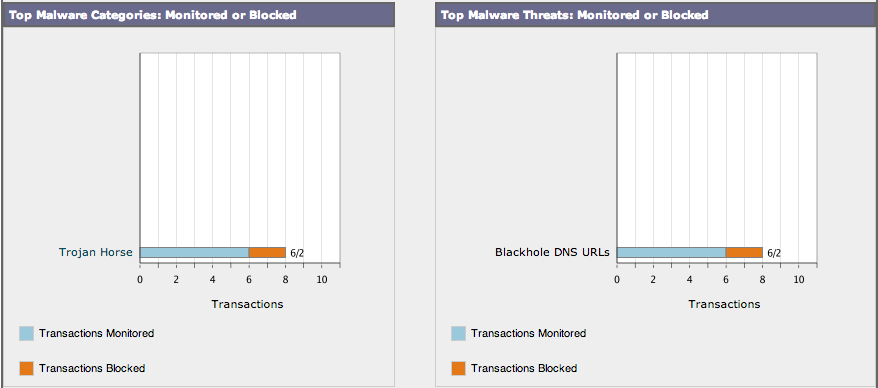
True insider threat visibility can only be accomplished by monitoring all internal traffic for threats that can compromise your network through email, web, infected devices or other means. Cisco has partnered with Lancope to give network wide forensic visibility leveraging capabilities that exist within networking products such as routers, switches and firewalls as well as in the datacenter. Administrators can use Lancope’s Steathwatch to see the top 10 threats that range from Data Loss to Botnet infections.
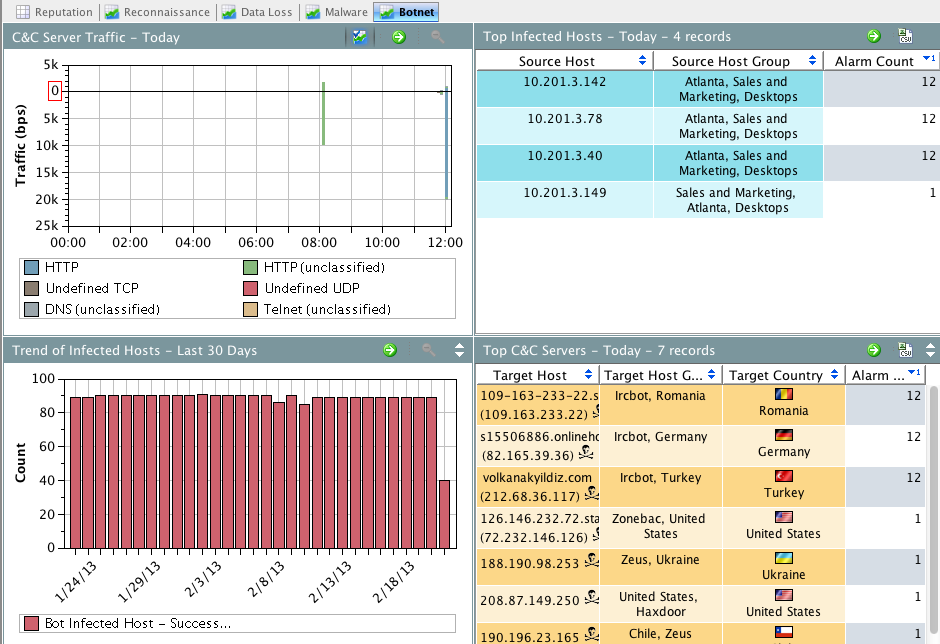 Main Lancope Cyber Security Dashboard
Main Lancope Cyber Security Dashboard
(Top 4 machines infected with botnets)
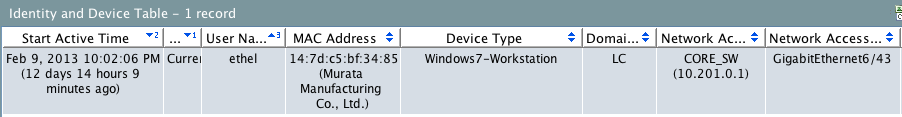 Ethel’s Windows 7 Workstation With Botnet
Ethel’s Windows 7 Workstation With Botnet
 Ethel’s Workstation communicating with malicious source
Ethel’s Workstation communicating with malicious source
Lancope identifies threats using a combination of reputation and behavior regardless if the threat attempts to hide by throttling, encryption or interact through multiple compromised systems. Some examples are flagging a user dumping large amounts of data to dropbox, communication with known malware web sources, host-to-host reconnaissance and use of obscure ports. Lancope can zero in on a threat by stitching together the entire communication chain meaning an administrator will see a map of all infected devices, how the infection started, who the users are (including Cisco ISE integration), where its spreading and how its sending traffic off the network. Lancope also gives visibility into abusing network resources, unauthorized tunneling and problems in network performance.
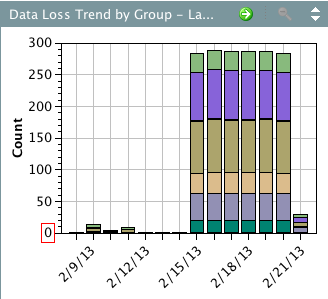 Lancope Dataloss Diagram
Lancope Dataloss Diagram
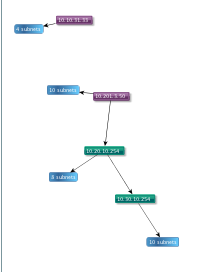 Malware Propagation Diagram
Malware Propagation Diagram
Purple IP has infected green IP which is probing other systems
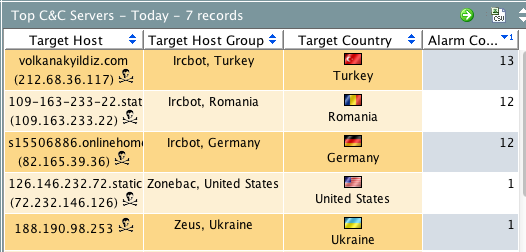 Known Botnet Sources via Reputation
Known Botnet Sources via Reputation
Combing Access Control, Web Security and Insider Threat technology gives administrators complete visibility of what is happening on the network. There is a lot of power having reports showing every user and device on the network, how those devices access the public Internet and near real-time analytics on if any of those devices have been compromised. This information can dramatically improve identification and reaction to cyber threats saving time, money and other problems caused by network breaches.