Cisco just released its latest version of its access control and identity management software known as Identity Services Engine (ISE) 2.1 (release notes found HERE). To summarize the release, it’s a big deal. There are a ton of changes including a face lift to the GUI. This post will summarize what is new as well as walk through how I upgraded from 2.0 to 2.1.
What is new with ISE 2.1
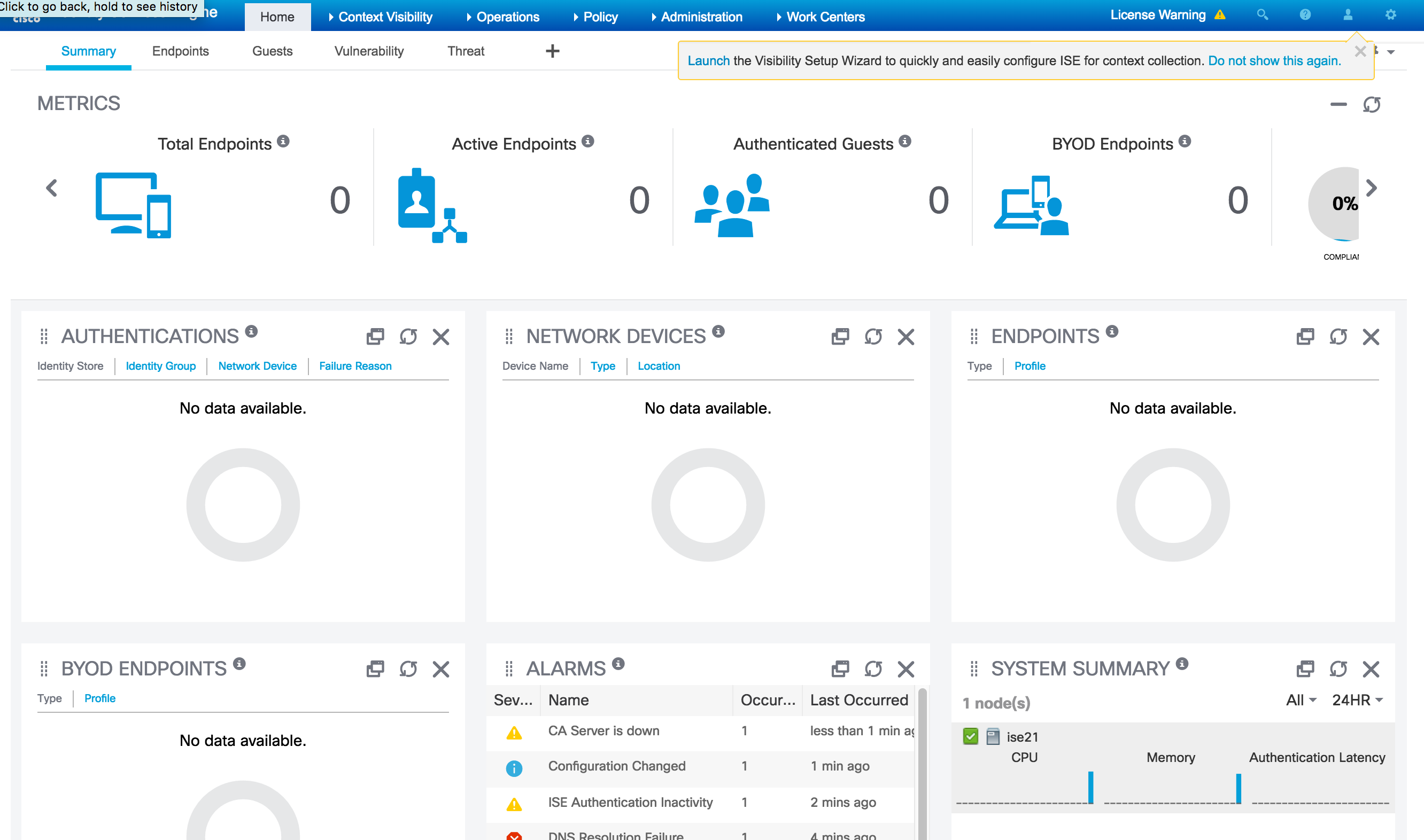
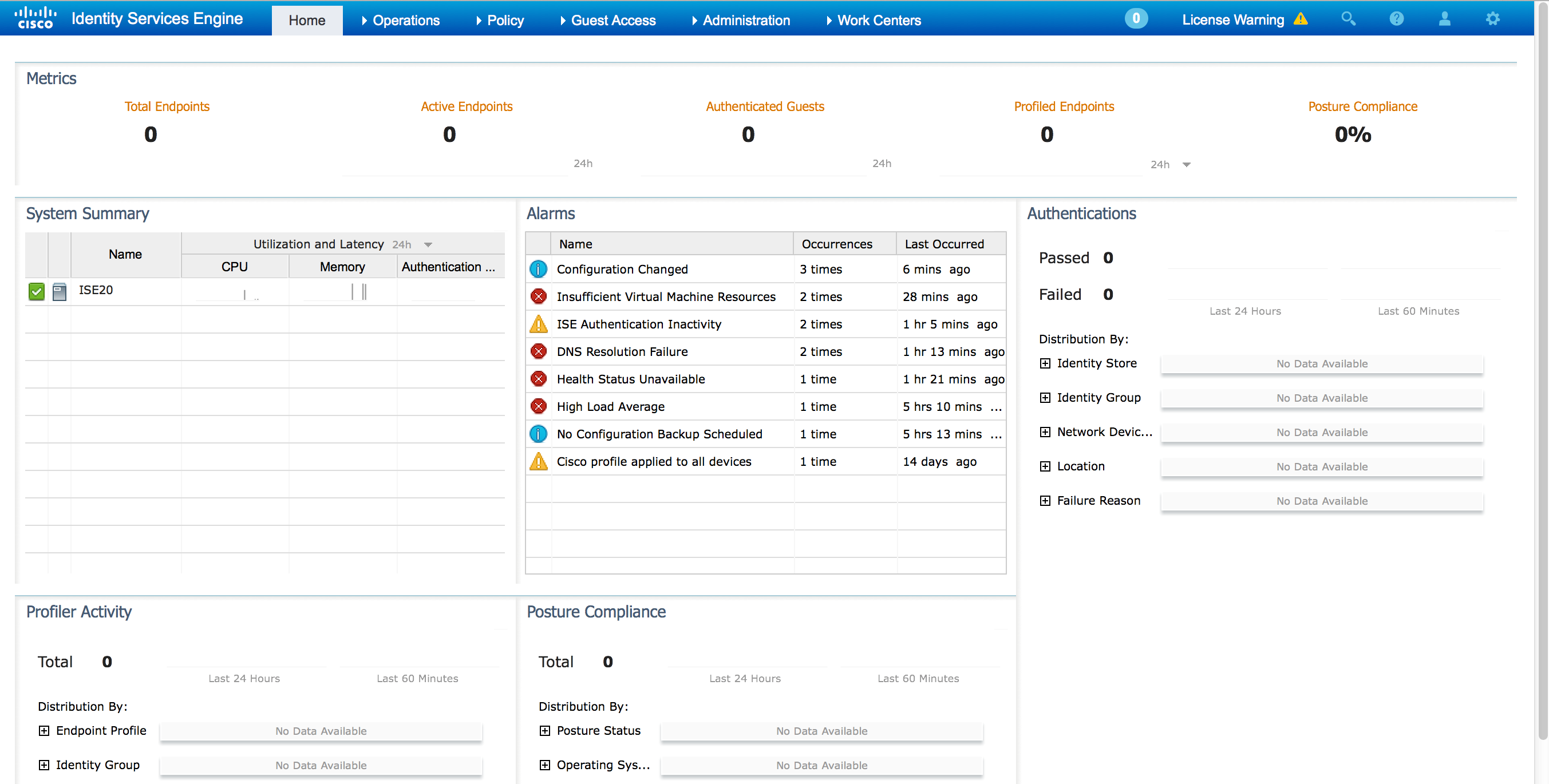
There are a boat ton of new features so I’ll focus on what I feel is cool. The first thing to consider is the new fancy interface. When I first accessed the IP of my manager, I was presented with a new fancy login screen. Upon logging in, I noticed the GUI had a lot more to it as shown comparing the 2.1 GUI to 2.0. This is also customizable.
Next is the experience. There are a bunch of work centers and wizards to simplify using the solution. For example, I use the visibility wizard to quickly capture my network. 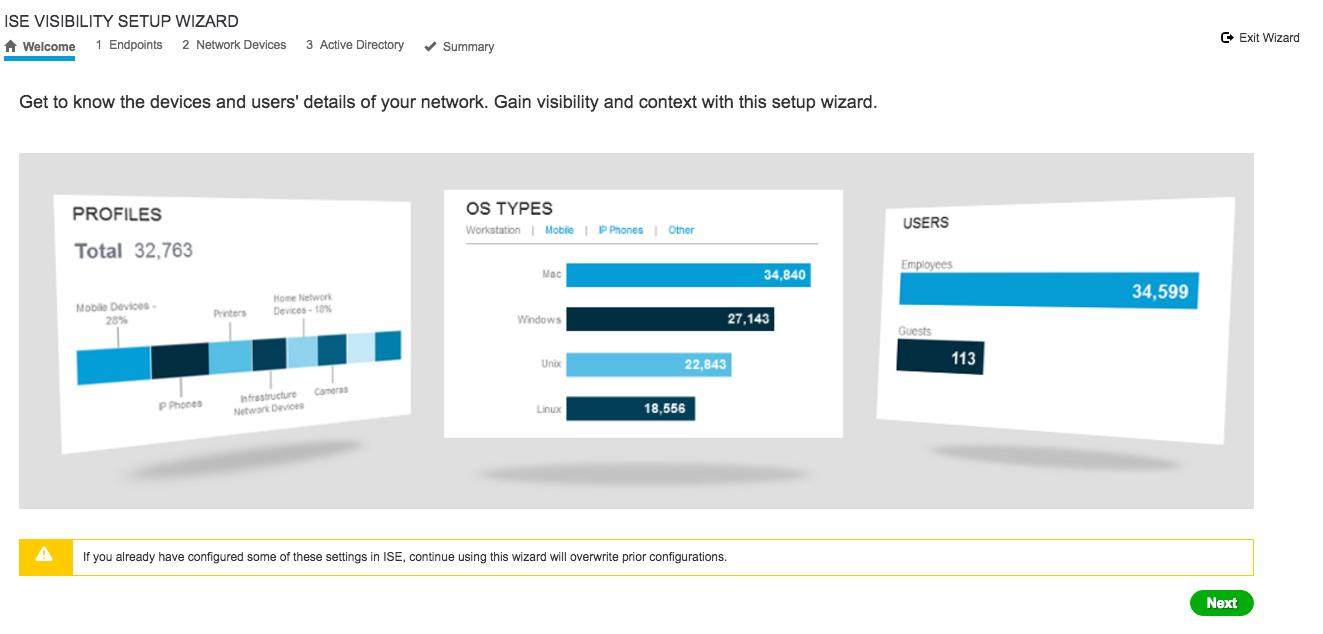 And it found my switch using a SNMP scan. Pretty slick and simple.
And it found my switch using a SNMP scan. Pretty slick and simple. 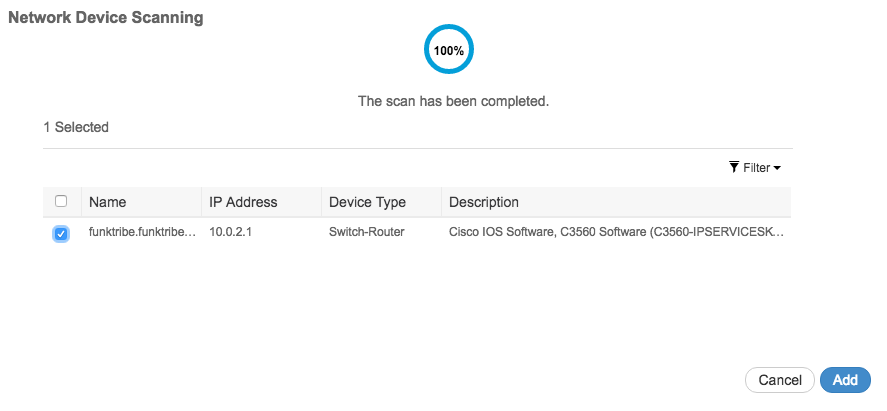 Easy Connect lets you connect users with Windows endpoints to a network securely by authenticating them through AD and not ISE. Basically ISE is collecting user authenticaito information and issues a change of auth to the network device.
Easy Connect lets you connect users with Windows endpoints to a network securely by authenticating them through AD and not ISE. Basically ISE is collecting user authenticaito information and issues a change of auth to the network device.
The guest experience has a handful of updates including a dedicated work center as shown. 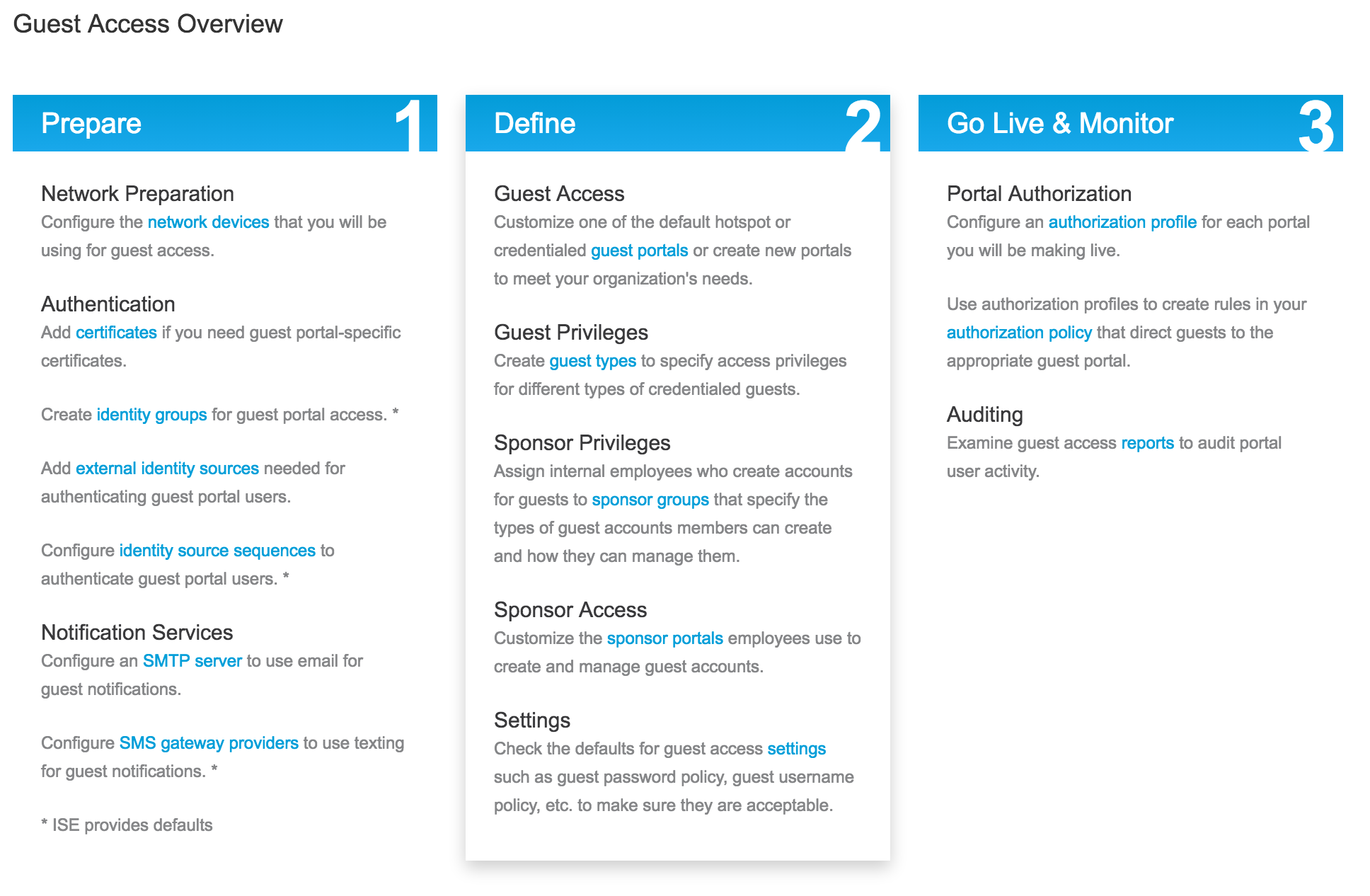 Another cool thing is the Threat-Centric NAC feature. This lets you create authorization policies based on the threat and vulnerability attributes received from the threat and vulnerability adapters. Threat severity levels and vulnerability assessment results can be used to dynamically control access. Today the threat adapters are SourceFire FireAMP and Qualys. I imagine this list will grow.
Another cool thing is the Threat-Centric NAC feature. This lets you create authorization policies based on the threat and vulnerability attributes received from the threat and vulnerability adapters. Threat severity levels and vulnerability assessment results can be used to dynamically control access. Today the threat adapters are SourceFire FireAMP and Qualys. I imagine this list will grow.
There is also new hardware, more 3rd party vendor support and so on. Check out the release notes. I plan to spend some time this week getting use to the new features and will post again on this in a few weeks.
Upgrading from ISE 2.0 to 2.1
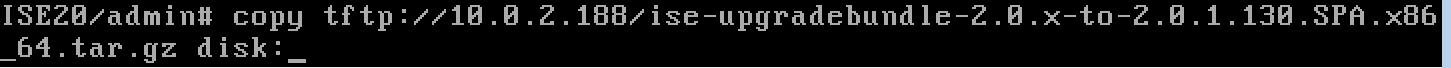
I logged into my lab and found I was on 2.0. This means I was looking at two upgrades meaing going to 2.0.1 then 2.1. I went ahead and downloaded both 2.0.1 and 2.1 upgrades as shown. 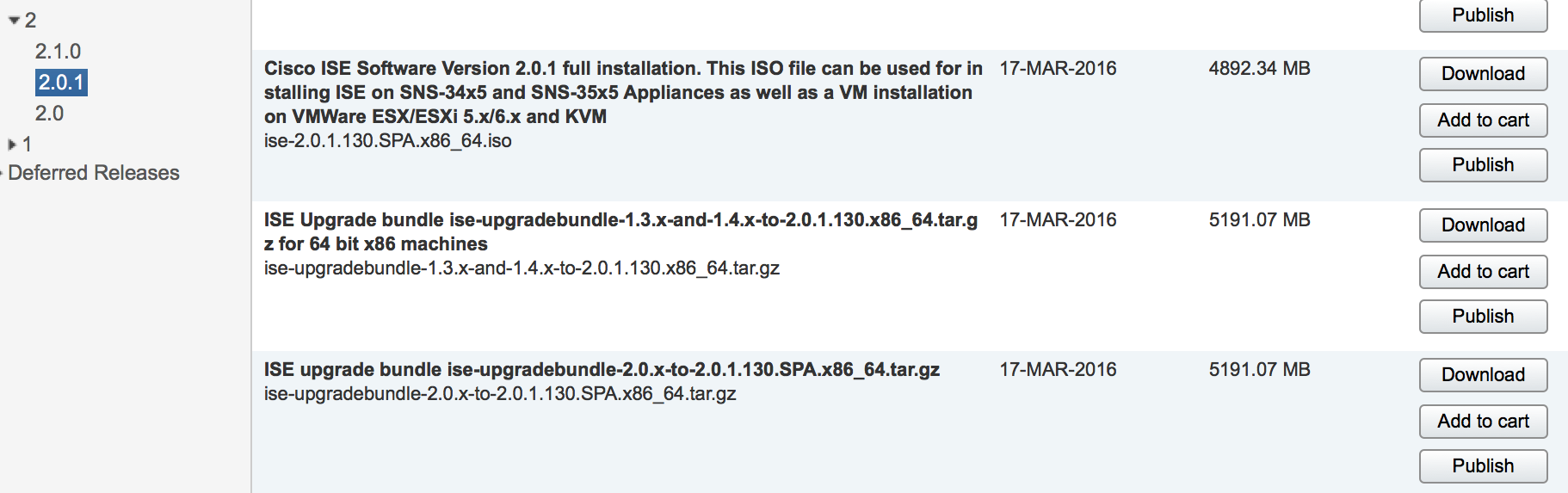 The next step is getting the upgrade file to the ISE server. I used filezilla for this, which took about 15 minutes to copy over each file. The command to copy it over from the ISE server command line is copy [server type] [file to copy][location on ise server]. So for me, it was copy tftp://MYSERVERIP/ISE2.0.1 disk:/ as shown.
The next step is getting the upgrade file to the ISE server. I used filezilla for this, which took about 15 minutes to copy over each file. The command to copy it over from the ISE server command line is copy [server type] [file to copy][location on ise server]. So for me, it was copy tftp://MYSERVERIP/ISE2.0.1 disk:/ as shown.
 I went ahead and copied both over since I would be running both of these. There are recommend steps to follow before proceeding with a upgrade as stated in the upgrade guide HERE. Since this is my lab, I just created a snap shot and went forward with it.
I went ahead and copied both over since I would be running both of these. There are recommend steps to follow before proceeding with a upgrade as stated in the upgrade guide HERE. Since this is my lab, I just created a snap shot and went forward with it.
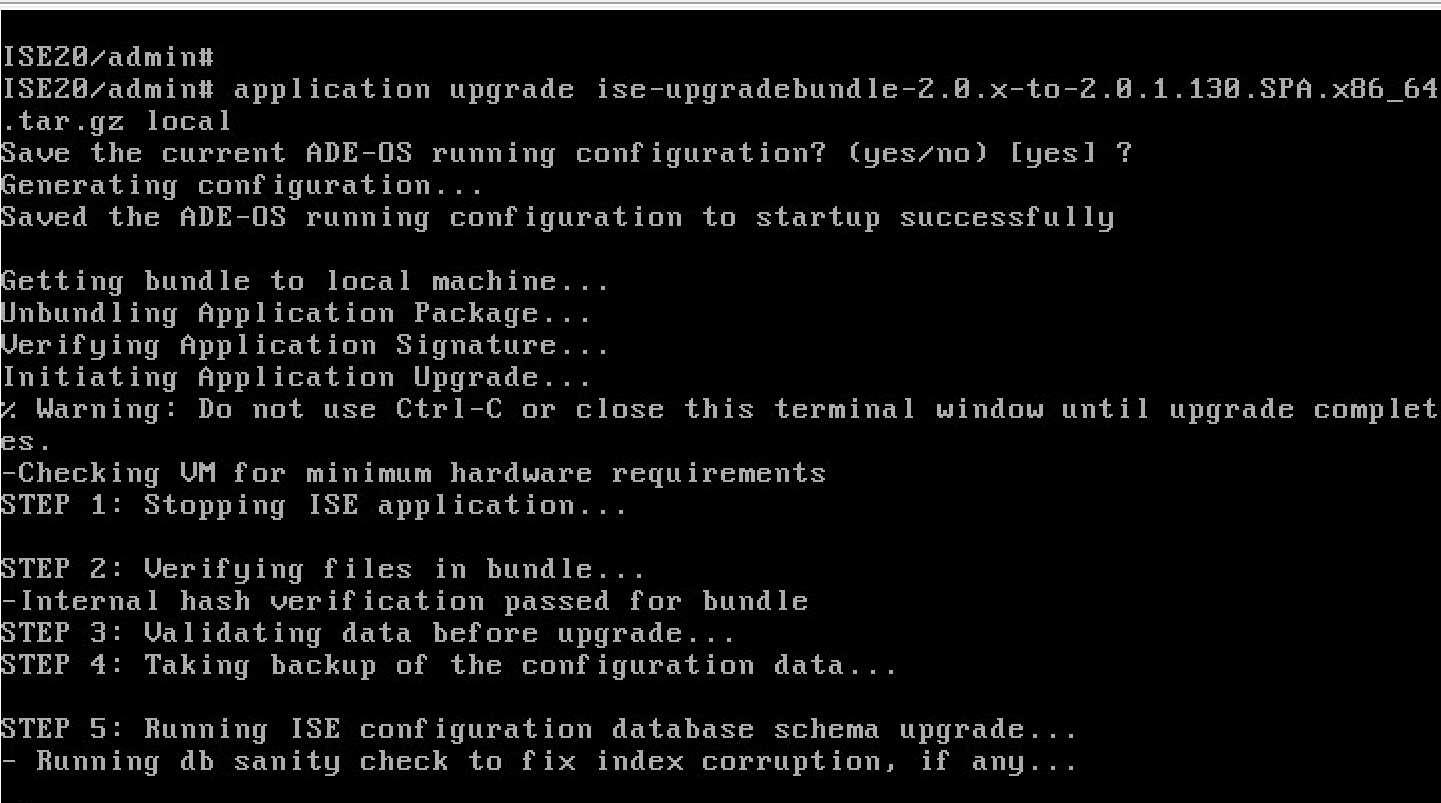
You probably first want to use the command terminal session-timeout 0 to avoid the session timing out during the upgrade process. Next use the command show repository local to validate that your files copied over. In my example, I see I have both of my upgrade files. 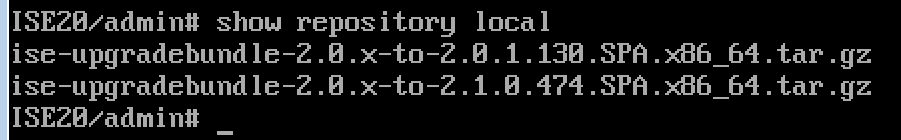 When you are ready to launch the upgrade, use the command application upgrade [FILE] [location on ISE Server]. So for me thats application upgrade ise-upgradebundleBLALBABLA.gz LM-LOCAL as shown. You will be asked to save the current ADE-OS and it will go. It took me a few hours to complete the process so plan for a long wait.
When you are ready to launch the upgrade, use the command application upgrade [FILE] [location on ISE Server]. So for me thats application upgrade ise-upgradebundleBLALBABLA.gz LM-LOCAL as shown. You will be asked to save the current ADE-OS and it will go. It took me a few hours to complete the process so plan for a long wait.
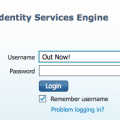
 The first time I ran it I found I needed to add more RAM to my ISE server. The next image shows the error I received after around 10 mins.
The first time I ran it I found I needed to add more RAM to my ISE server. The next image shows the error I received after around 10 mins. 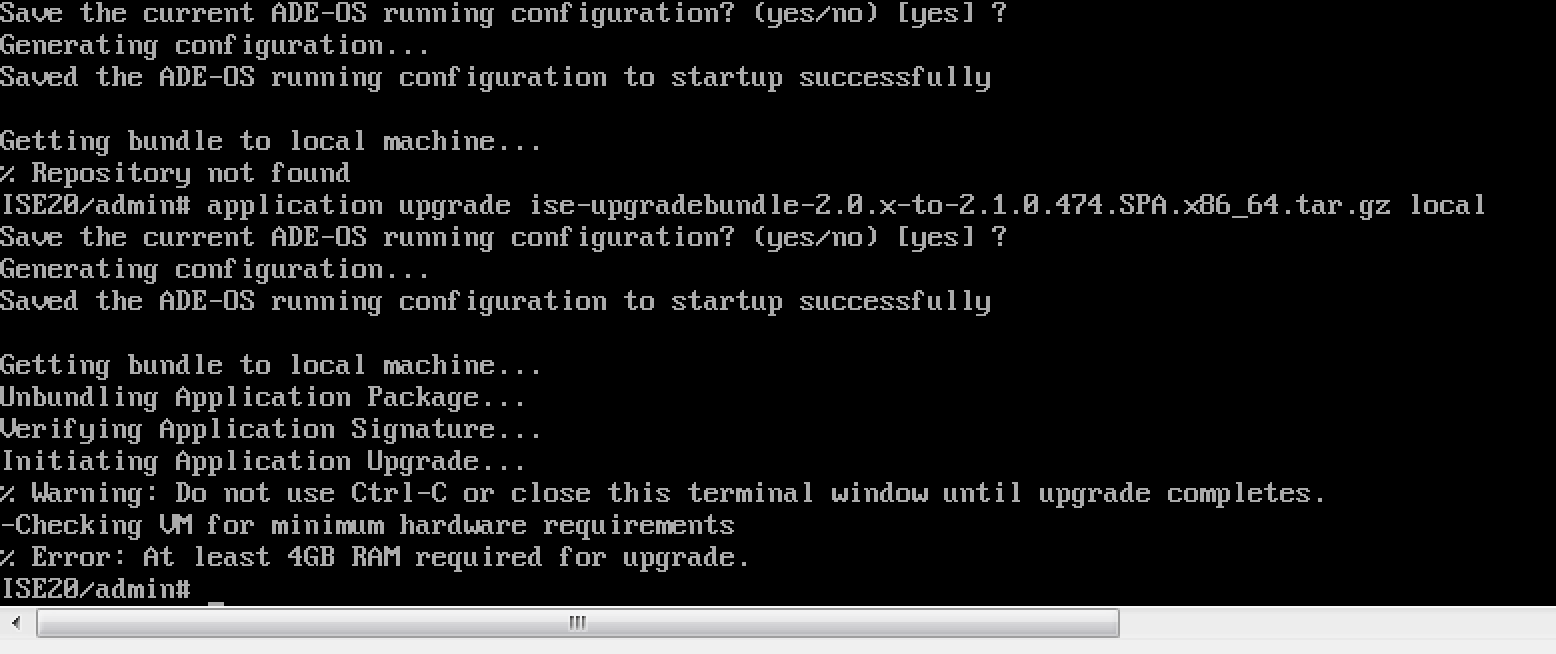 Second time a charm after I added RAM to my VM. Nothing too stressful however it does take a while to complete. I later built a new one using the 100 device .OVA file, which took about the same time to complete the installation.
Second time a charm after I added RAM to my VM. Nothing too stressful however it does take a while to complete. I later built a new one using the 100 device .OVA file, which took about the same time to complete the installation.



Are you facing any issues after the upgrade? is it advisable to upgrade? what are the precautions one should take before upgrading?