Many of our customers are investing in multi-factor authentication solutions. The multi-factor industry offers a range of options such as physical cards, certificates and tokens that represent “Something you have” mixed with a pin, password or security phase that is “Something you know”. A upcoming multi-factor technology is biometrics representing “Something you are” however its not as common as having and knowing something. DoD has standardized on Common Access Cards or CAC while civilian agencies tend to use Personal Identification Verification or PIV cards for accessing systems and secured areas. Both card solutions use similar smart card technology however things like the Certificate Authority and what is printed on the cards are different between organizations.
Customers request my team to provide security demonstrations and often ask if the solution being showcased is CAC / PIV / smart card capable. There are a few players in the CAC / PIV / smart card market. One we like is Active Identity (now part of HID Global). Active Identity offers many multi-factor authentication solutions including CAC / PIV and smart card packages that range from the HID reader to the card management system. Active Identity’s flagship card management solution is ActivID CMS, which is a web-based application using Apache Tomcat and IIS. Active Identity does not provide a Certificate Authority (CA) for generating certificates or Hardware Security Module (HSM) for storing master keys however a lab can work without these.
For those who want to build a CAC / PIV / smart card lab, go to Active Identity’s demo download page found HERE and download the latest ActivID CMS. I’m running ActivID CMS in my lab using VMware workstation on a standard windows laptop. There are a lot of steps in the install guide so make sure to download that as well. To summarize the installation steps, you will need to do the following:
1) Create a ActivID CMS Rep Windows Account
2) Allow Rep to enroll smart card logon and smart card user certificates
3) Install ActivID CMS
4) Configure the ActivID CMS web server and apply ActivID CMS hotfixes
There are many types of card readers that work with ActivID CMS. I’m using a HID Omnikey however I have a few others that also work great (see picture) as well as a blank HID smart card. The concept is I’m going enhance authentication into the ActivID CMS administration portal using a two-factor smart card solution. You can purchase any of readers in the picture and a smart card on amazon for 20-30 dollars.
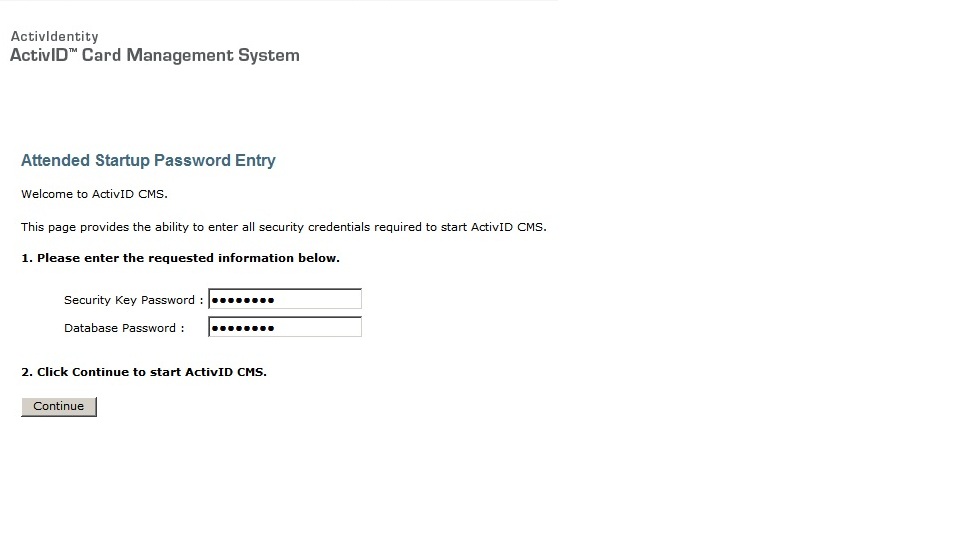
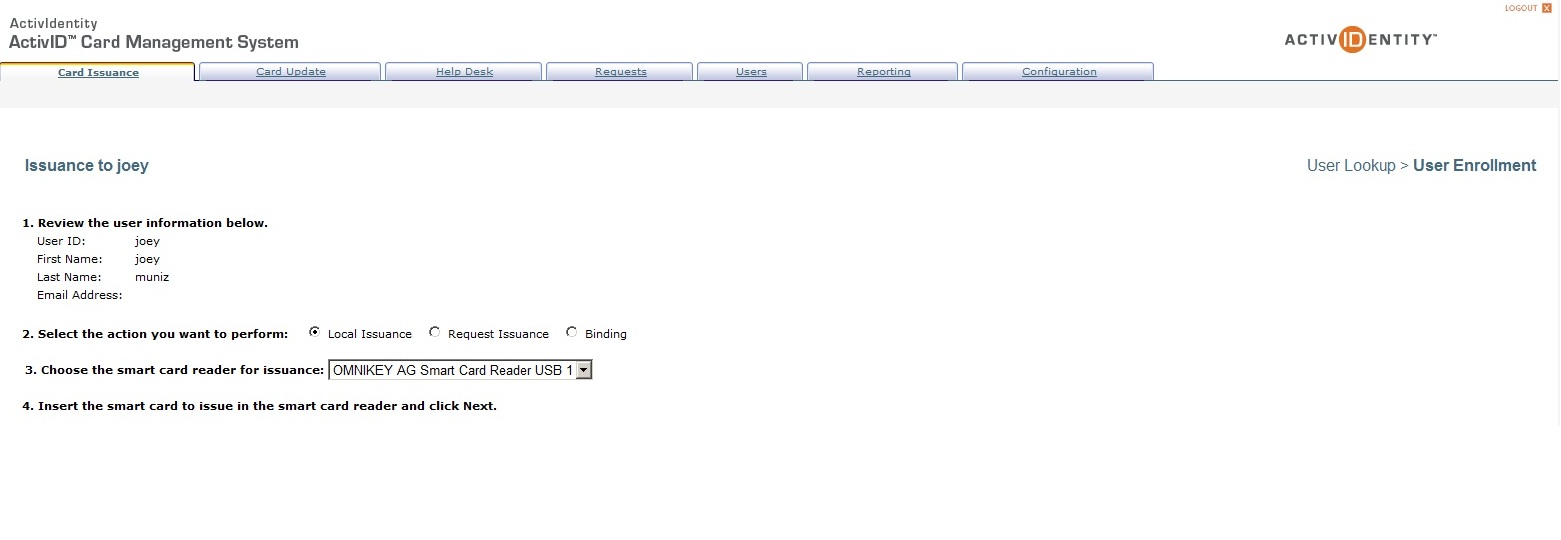
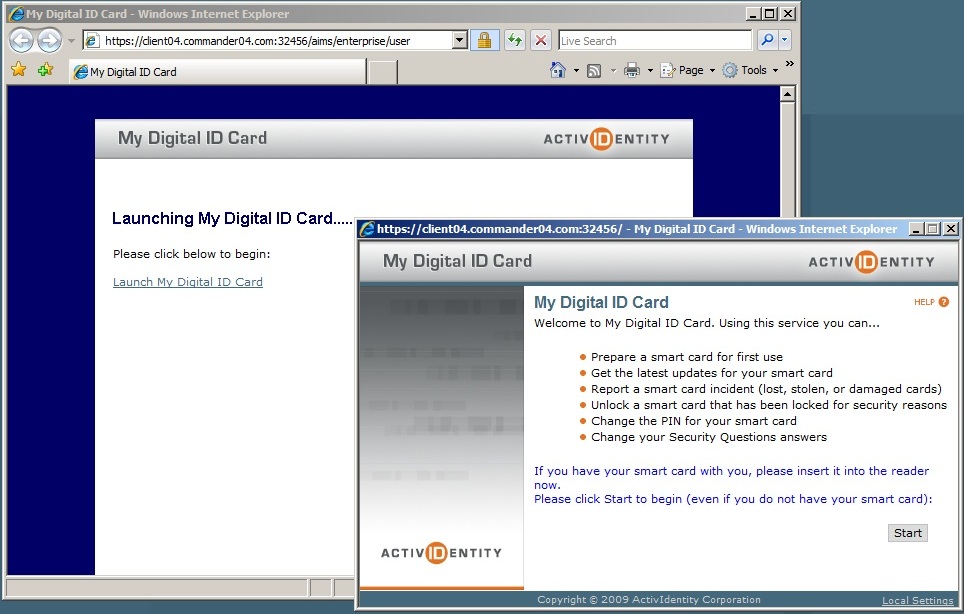
ActivID CMS offers an administration and user web portal. When I first log into the admin page, ActivID CMS will ask for the security and database passwords to start all the services. Once the portal is started, the admin and user portals can be accessed (see picture above). The Admin dashboard lets you provision cards to specific users and control what access they should have. You can setup PIN policies, develop different methods to bind cards to users, terminate cards and other CAC / PIV / smart card management tasks. End users can access their own card information using the User portal to initiate, update and report lost cards. Below is a picture of the main Administration dashboard and pre login of the end user portal showing its features.
My lab is configured to have user Joey use a smartcard and PIN to access the ActivID CMS administration page. The main dashboard picture shows accessing a local existing user Joey and assigning a smartcard through the OMNIKEY reader. The policies configured for my smart card are holding two certificates and policy for a lost card. Its pretty straightforward technology and my future plan is to smart card enable different technologies in other labs. More to come on that work. Feel free to check out ActivID CMS on Active Identity’s website as well as other multi-factor authentication solutions.