KeRanger is the first Mac based Ransomware. This goes to show that attackers are targeting Apple, which should be expected as Mac gains market share. The interesting aspect is how the Ransomware leveraged a valid Mac app development certificate, which has been revoked by Apple. Here is a post by Techcrunch on this story. The original posting can be found HERE.
Apple has shut down what appears to have been the first, fully-functional ransomware targeting Mac computers. This particular form of cyber threat involves malware that encrypts the data on your personal computer so you can no longer access it. Afterwards, the hackers request that you pay them in a hard-to-trace digital currency – in this case, bitcoin – in order for you to retrieve your files. This ransomware, called KeRanger,” was first reported by researchers at Palo Alto Networks. They also noted that Apple has now revoked the abused certificate that was used in the attack and updated its built-in anti-malware system XProtect with a new signature to protect customers.
Technically, KeRanger was not the first ransomware aimed at Mac users. The security firm said that another malware application known as FileCoder had been previously discovered. However, FileCoder was incomplete at the time it was found, which is why the firm believes that KeRanger is the first functional ransomware to appear on the OS X platform.
The fact that OS X has now been targeted speaks to the popularity of Apple’s operating system – ransomware is a fairly common form of cyber threat these days as victims are often likely to cave into attackers’ demands. This has even been the case in some high-profile attacks, as with the ransomware that shut down servers in an L.A. hospital last month. The hospital eventually paid a ransom equivalent to $17,000 in bitcoins to get its systems back up-and-running.
With KeRanger, the demands were more modest, though it’s unclear for now how many users actually fell victim to the attack and how successful it was at exploiting those victims.
For what it’s worth, Ryan Olson, Director of Threat Intelligence at Palo Alto Networks, tells us his company believes that their quick action combined with Apple’s fast response has “greatly limited the impact of this threat.”
According to Palo Alto Networks, attackers infected two installers of Transmission, an open source BitTorrent client, with the malware which would then encrypt files and then demand a ransom of one bitcoin (around $400) to release the files back to the users’ control.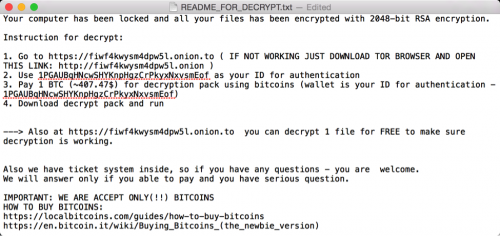
 The KeRanger application itself was signed with a valid Mac app development certificate, which is how it was able to skirt around Apple’s Gatekeeper protection mechanism. After being alerted to the threat on March 4, Apple acted quickly this weekend to revoke this certificate and update its antivirus signature, Palo Alto Networks said.
The KeRanger application itself was signed with a valid Mac app development certificate, which is how it was able to skirt around Apple’s Gatekeeper protection mechanism. After being alerted to the threat on March 4, Apple acted quickly this weekend to revoke this certificate and update its antivirus signature, Palo Alto Networks said.
End users are also reporting seeing protections “KeRanger.A malware” as being rolled out in the latest XProtect update. Other user-to-user advice on Apple’s forums helps to detail the steps those who have already become infected with the malware should take, which require finding and deleting certain hidden files.
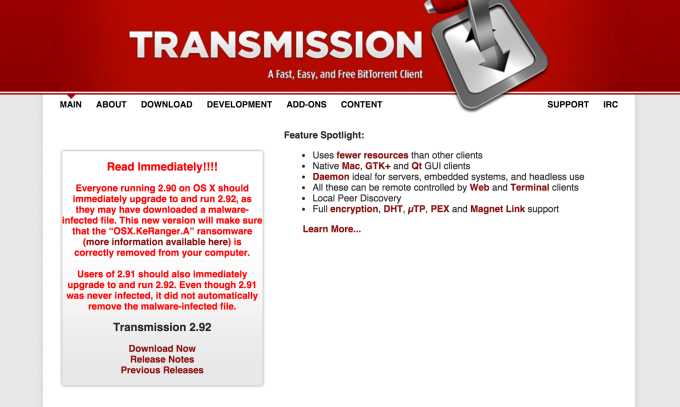
Transmission, which was a victim of the attack in its own way, has also updated its website to advise users who downloaded the infected version 2.90 of the software to upgrade and run version 2.92 instead. This version will remove the malware-infected file from the system. (Transmission was never hosted on the Mac App Store, but its app has an auto-update mechanism which will help those who don’t manually upgrade.)
 In addition, if a user now tries to run the infected version of Transmission, they’ll be shown a warning dialog that informs them to eject the disk image, and that the app will damage your computer and should be moved to the Trash.
In addition, if a user now tries to run the infected version of Transmission, they’ll be shown a warning dialog that informs them to eject the disk image, and that the app will damage your computer and should be moved to the Trash.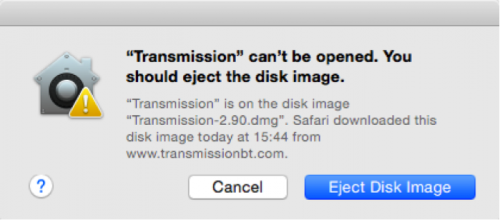 While Apple has addressed the immediate threats posed by KeRanger, there is still some concern given that the security firm believes this malware is still under development. Its analysis suggests that attackers may be trying to develop backdoor functionality that would encrypt users’ Time Machine backups, as well.
While Apple has addressed the immediate threats posed by KeRanger, there is still some concern given that the security firm believes this malware is still under development. Its analysis suggests that attackers may be trying to develop backdoor functionality that would encrypt users’ Time Machine backups, as well.
If that was the case, then victims wouldn’t be able to recover their files using Time Machine – they would be more at the mercy of the hackers’ demands.




