People have asked me to recommend a tool that can be used to analyze files for viruses that does more than standard anti-virus. Usually the need is to prove something being flagged by a security product is actually malicious verses a false positive alert. There are enterprise level sandbox solutions such as Cisco’s ThreatGRID sandbox that offer this (more on this found HERE) however one very popular open source free option is Cuckoo.
Cuckoo is a malware analysis system. You can set it up and run files against it to so Cuckoo can analyze the behavior of the files in a controlled environment. Pretty much any file type is game meaning .exe, dll, scripts, zip files, documents, etc can be ran on a virtualized host to see their behavior. Some results Cuckoo can provide are:
- Traces of win32 API calls performed by all processes spawned by the malware.
- Files being created, deleted and downloaded by the malware during its execution.
- Memory dumps of the malware processes.
- Network traffic trace in PCAP format.
- Screenshots of Windows desktop taken during the execution of the malware.
- Full memory dumps of the machines.
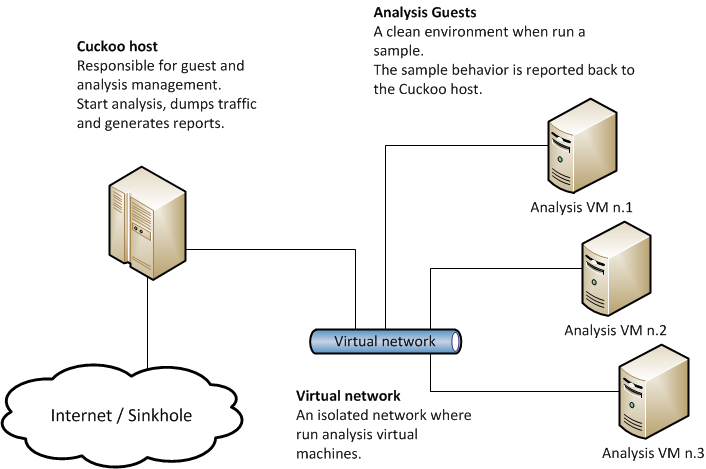
The system architecture is made up of a Cuckoo host (preferably Ubuntu but can be others) and guest systems to analyze malware (typically Windows XP). The next image represents a typical Cuckoo design.
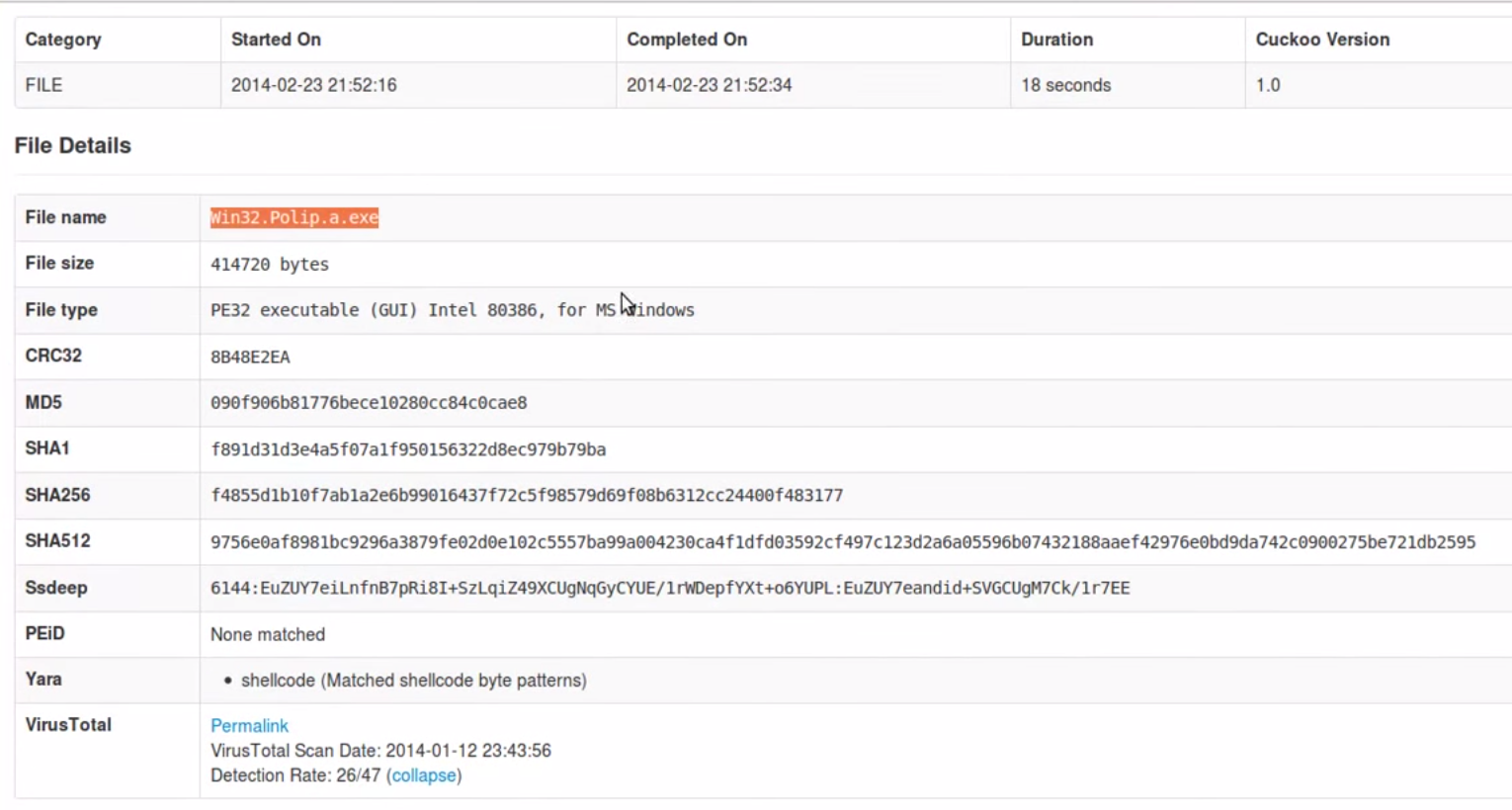
The next screenshot shows a file ran in Cuckoo. This executable got flagged as malicious with some details about the file.
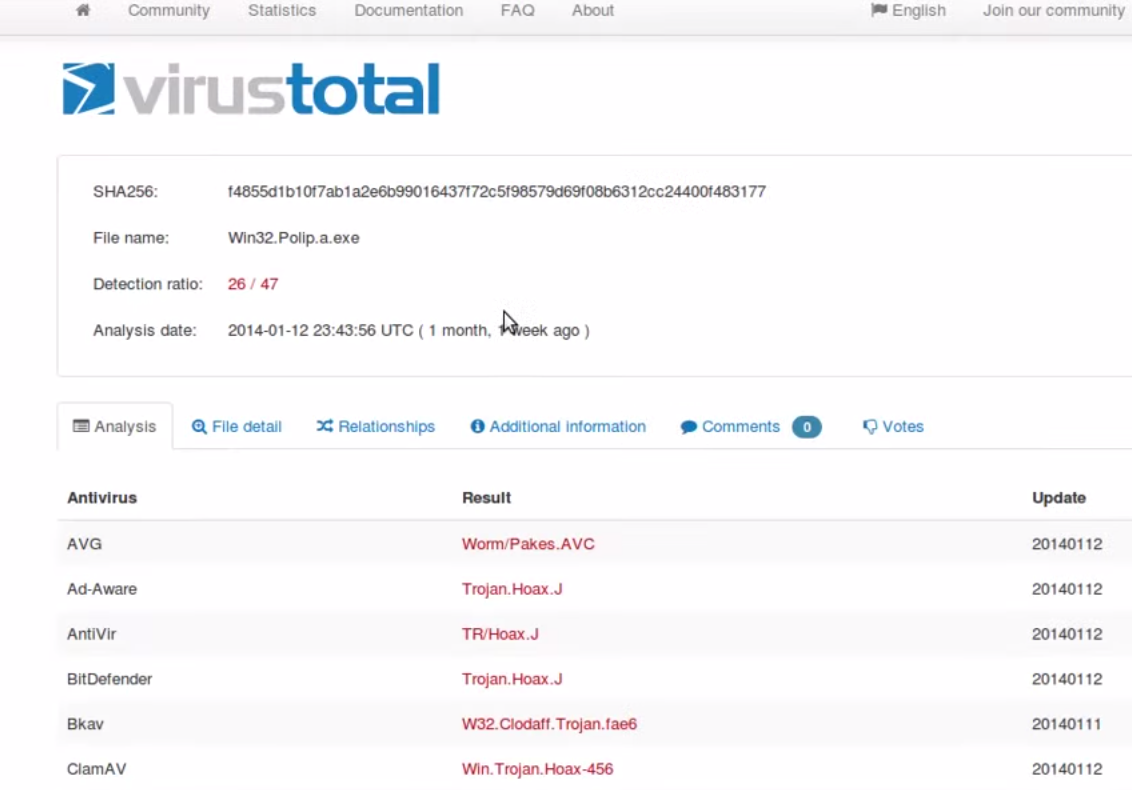
You can click the virus total link to see that it has been identified by a handful of security solutions as malicious under different names. The screenshot doesn’t show it, but if you you scroll down, you will find security solutions that currently don’t catch this threat.
Cuckoo can be challenging to setup. This video provides a good resource that walks through the process found HERE. You can also check out the Cuckoo communities from their main page found HERE. If you are looking for a free tool to test malware, Cuckoo is a pretty good option.