Many people don’t understand how HTTPS technically operates however get that it means more secure than HTTP. These people log into a bank or other trusted website, see the lock image / https setting and breath out a relaxing sigh that things are now secure. In the real world we all live in, this is not always the case. I’ve posted about various attacks that abuse how HTTPS is enforced such as using a WiFi Pineapple and running the SSL strip attack while being a man-in-the-middle to any WiFi device within my attack device’s range (see more HERE).
This last part of this post comes from the Cisco blog talking about phishing attacks that abuse HTTPS. Before we go there, one interesting concept on phishing attacks is the question “Why do Nigerian Scammers Say They are From Nigeria“. Microsoft answered this question HERE, which came down to a core concept.
The attackers for that particular scam want smart people to delete the email hence make the story very far fetch so only the most gullible people respond, hence getting them the best audience and removing the unwanted people. Basically, people like your grandparents that don’t know any better …
My personal suggestion is to response to those emails with your own fake email and have fun. I talk about this concept HERE. Its really fun. Do it.
Well those fake emails may target the most gullible however these more recent phishing attacks are targeting everybody including tech savvy users. Lets look at this in more details. The original Cisco blog post can be found HERE.
John Smith had a lot of friends and liked to travel. One day he got an email that read: “Money has been sent to your PayPal account”. The sender appeared to be a person he met from recent trip to Cape Town. John Smith was curious and followed the link to PayPal (hxxps://paypal.com-receipt-gifts.online/) which looked a little bit suspicious. Luckily, John had recently taken a phishing awareness training and remembered that HTTPS meant the website is safe. He saw a green padlock next to the URL, decided that everything was fine, typed his PayPal username and password and pressed enter. This is the end of our story but just the beginning of John’s problems.
For quite a while now the security community has been educating users about the importance of secured communication [1]. Users have been taught that important connections will be secured with HTTPS. How can you tell if your connection is secured with HTTPS? Simply check whether there is a little green lock next to the URL in the address bar of the browser[2].
Figure 1: Browser address bar of a legitimate Google website.
Making users aware of communication security is a very important effort. Unfortunately, it has created a strange side-effect of many users trusting anything secured with HTTPS. Green lock means secure which means safe to use. The attackers have been quick to adapt and found a way to use the trust of HTTPS to their own advantage. One of the attack vectors where HTTPS is abused is phishing.
Watch out! Phishing domains
A very common and effective technique used by the attackers is impersonating well-known domain names that users already know and trust, such as the ones illustrated by the green text in Figure 2. The red text is to highlight the counterfeit portion of the domain name.
Figure 2: Examples of phishing domains.
All these domains look very suspicious to a security professional but may appear perfectly legitimate to an untrained eye. These domains often have a very short time-to-live and are dropped after a few days of use. This renders blacklists ineffective against them because they need to be constantly updated with fresh domains.
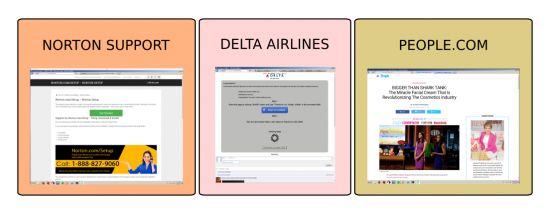
During our analysis, we have observed these domains being used for phishing, as well as by scammers offering fake technical support and by advertisers promoting products of questionable quality.
Figure 3: Examples of web pages with the host name and design similar to the legitimate companies: Norton, Delta airlines and online news outlet people.com. Used by attackers for online scams or advertisement.
HTTPS – using a good thing for a bad cause
Attackers have started to abuse users inherent trust in HTTPS. They do it by signing phishing domains with a certificate. These are usually obtained from certificate authorities like Let’s Encrypt which provides certificates for free [3]. This means that the users who visit the domain and look at the URL will see the little green lock. Rarely will anyone check the actual certificate.
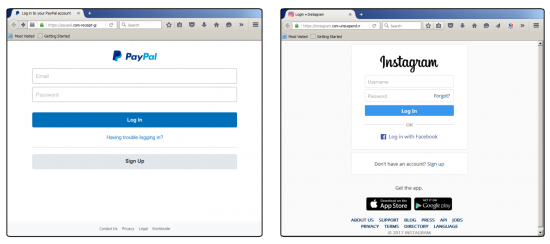
Figure 4: Screenshots of phishing, mimicking legitimate PayPal and Instagram websites. In the address bar we can clearly see the green padlock indicating HTTPS connection.
Above are examples of two phishing campaigns both using HTTPS. As you can see, the locks are green. The websites look legitimate, especially if you make the window narrow enough to cover most of the URL. But if you enter your credentials they will probably steal your money and selfie photos.
Prevention best practices
User education is a very important step in phishing prevention. However, there will always be people who will be tricked, despite the training. Network monitoring tools help to fill the gap and detect successful phishing attempts. Cognitive Threat Analytics (CTA) and Cisco Umbrella are examples of solutions that discover hundreds of phishing domains every week, including sophisticated ones which use HTTPS. Learn more via www.cisco.com/go/security






To me some of the blame can be put on registrars. I have seen this about a dozen times at my organization. IMO there is no way you should be able to register a domain like amazonlogin.com without some vetting process. Get a free month of O365 (pass SPF and DKIM) with the domain purchase and a cert from Let’s Encrypt and you are in like Flynn.
See Let’s Encrypt discuss this: https://letsencrypt.org/2015/10/29/phishing-and-malware.html