 Today’s highlight – WIFI Pineapple Mark III Wireless Penetration Testing Tool.
Today’s highlight – WIFI Pineapple Mark III Wireless Penetration Testing Tool.
There are many cool tools sold at conferences. One tool to check out is the WIFI Pineapple Mark III for around $100 dollars. Basically it’s a wireless honeypot using a man-in-the-middle attack to access data. The way it works is it listens for devices calling out for known wireless networks / SSIDs. The WIFI Pineapple will hear the request and clone the requested SSID so the device believes its connecting to a known trusted network.
 An example is connecting an iPad on an airplane to the online network GOGO SSID. Some time later the user may be at a Starbucks and turn on the iPad that was used on the airplane. The iPad will beacon out “am I still on the airplane and can I re-connect to GOGO?”. The WIFI Pineapple will hear the request and reply back “I’m GOGO … welcome to the internet”. The iPad will auto-connect to the fake GOGO SSID without re-authenticating, which is really the WIFI Pineapple passing traffic through to another network while the hacker sits in the middle. Essentially, the WIFI Pineapple takes advantage of convenience services via auto connecting to known or trusted networks offered by most wireless devices.
An example is connecting an iPad on an airplane to the online network GOGO SSID. Some time later the user may be at a Starbucks and turn on the iPad that was used on the airplane. The iPad will beacon out “am I still on the airplane and can I re-connect to GOGO?”. The WIFI Pineapple will hear the request and reply back “I’m GOGO … welcome to the internet”. The iPad will auto-connect to the fake GOGO SSID without re-authenticating, which is really the WIFI Pineapple passing traffic through to another network while the hacker sits in the middle. Essentially, the WIFI Pineapple takes advantage of convenience services via auto connecting to known or trusted networks offered by most wireless devices.
The WIFI Pineapple is pretty easy to setup. It has two LAN interfaces (pass through and admin access). It provides auto DHCP 172.16.42.X to the administrative interface. To access the main interface, a GUI located at 172.16.42.1. From here, the pen tester can enable many tools as well as see who is connecting to the WIFI Pineapple. Network setup is pretty easy and designed to pass traffic through without systems knowing the difference from the fake SSID or real network.
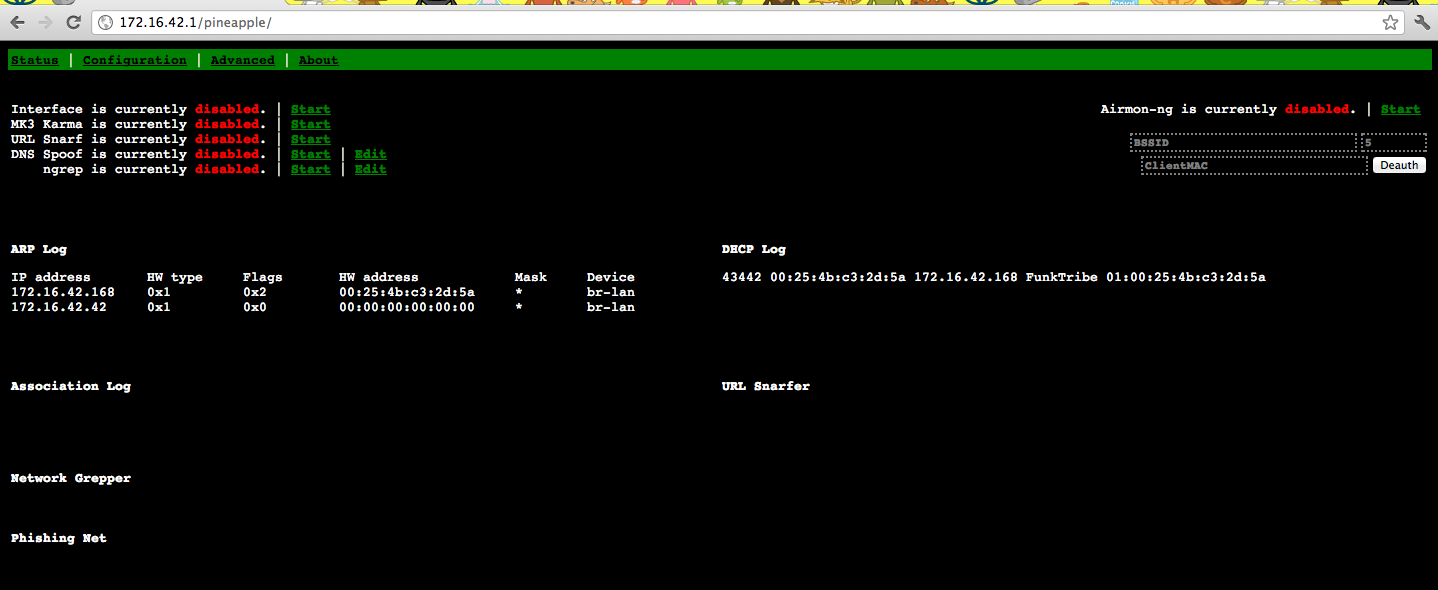 Some built in tool highlights (in the release of software I’m running) are Karma, Snarf and DNS Spoofing. The GUI is pretty easy to get around. I used the WIFI Pineapple to capture cookies and replay in FireFox via the Add N Edit Cookies plugin. An example is capturing a Facebook cookie to accessing the victim’s Facebook account. An example of using cookies to access a gmail account can be found HERE regarding the cookie reply process.
Some built in tool highlights (in the release of software I’m running) are Karma, Snarf and DNS Spoofing. The GUI is pretty easy to get around. I used the WIFI Pineapple to capture cookies and replay in FireFox via the Add N Edit Cookies plugin. An example is capturing a Facebook cookie to accessing the victim’s Facebook account. An example of using cookies to access a gmail account can be found HERE regarding the cookie reply process.
For those wondering how to defend against this tool there are some options. VPN tunnels encrypt traffic from your device to its destination blocking visibility into traffic seen by the WIFE Pineapple (example using Anyconnect by Cisco). Also using data in motion / encryption technology for sensitive data will defend against this attack since the users must be authenticated to access the data contents that are captured by the man-in-the-middle. Disabling auto-connecting to networks may mean extra steps to establish network connectivity however will help in scenarios like this. The bad part about this attack is you may not auto-connect to known risky networks such as Starbucks however the WIFI Pineapple can clone any SSID including your home network.
Check out Hak5 for more details on this and other cool tools.


