I’m not a big fan of Windows however for those that are, here is your Kali alternative. The original post can be found HERE
FireEye today released Commando VM, which according to the company, is a “first of its kind Windows-based security distribution for penetration testing and red teaming.”
When it comes to the best-operating systems for hackers, Kali Linux
However, Kali is a Linux-based distribution, and using Linux
Moreover, if you are wondering why there is no popular
To help researchers and cyber security enthusiasts, cybersecurity firm FireEye today released an automated installer called Commando VM.
But don’t get confused with its name. Commando VM is not a
pre-configured snapshot of a virtual machine image with many tools
installed on a Windows system. It’s not even a complete distribution.
Instead, Commando VM is an automated installation script that turns your
Windows operating system, running on a virtual machine (VM) or even on
the base system, into a hacking machine.
“It is possible to archive the same result if you run the install script on the base machine. However, we strongly discourage this behavior. Commando VM downloads additional offensive and red team tools on Windows. Many of these tools are flagged by windows defenders as malicious. Therefore, we disable many Windows security features. Running Commando VM on the host will leave it vulnerable, and therefore strongly discouraged,” FireEye researcher confirmed The Hacker News via an email conversation.
But, I have to mention that Commando VM is not the first of its kind.
Available since 2015,
Developed by Indian security researcher Aditya Agrawal, PentestBox
Commando VM release 1.0 includes two different set-ups, one works on Windows 7 Service Pack 1 and another for users running Windows 10 operating system.
Commando VM offers a smooth working environment by
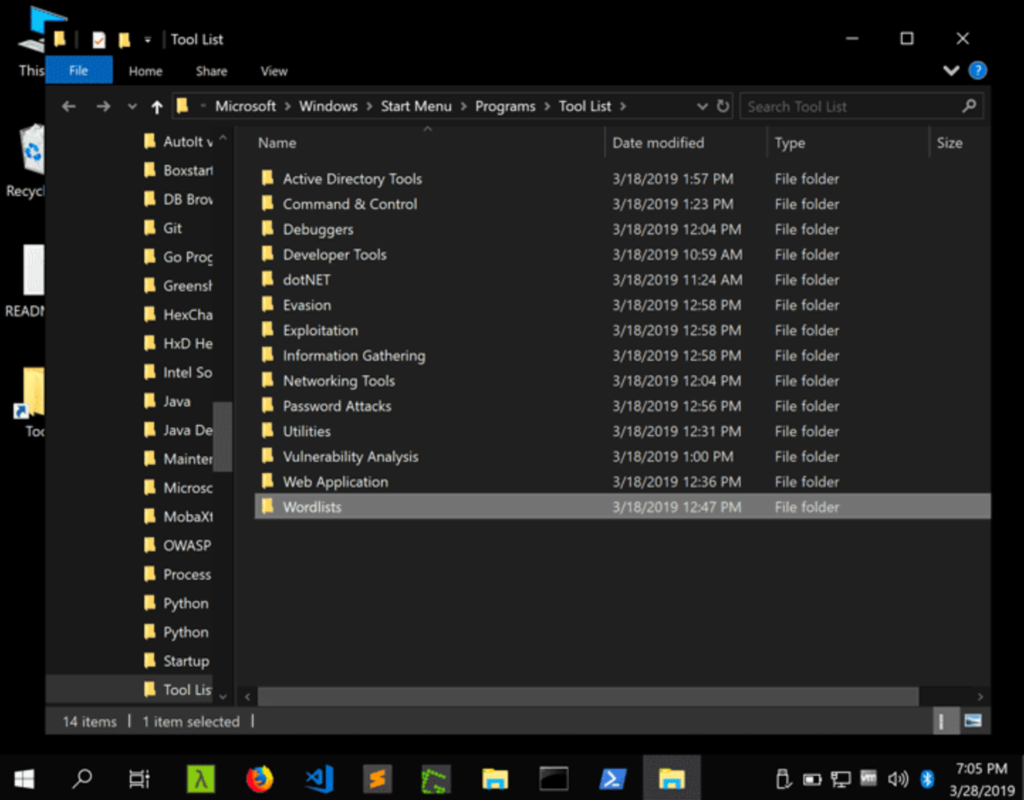
According to one of the authors of Commando VMs, the following are the top three features of the tool that make it more interesting:
- Native Windows protocol support (SMB, PowerShell, RSAT, Sysinternals, etc.)
- Organized toolsets (Tools folder on the desktop with Info Gathering, Exploitation, Password Attacks, etc.)
- Windows-based C2 frameworks like Covenant (dotnet) and PoshC2 (PowerShell)
“With such versatility, Commando VM aims to be the de facto Windows machine for every penetration tester and red teamer,” FireEye says.
“The versatile tool sets included in Commando VM provide blue teams with the tools necessary to audit their networks and improve their detection capabilities. With a library of offensive tools, it makes it easy for blue teams to keep up with offensive tooling and attack trends.”
According to FireEye, Commando VM also uses Boxstarter, Chocolatey, and MyGet packages to install all software packages. Running a
To use this on your Windows computer, you need at least 60 GB of free hard drive space, 2GB of RAM and a freshly installed Windows OS on a virtual machine software, like VMware or Oracle VirtualBox installed on your system.
Installing Commando VM is pretty easy. Just download the Commando VM, decompress it and then execute the PowerShell script available in the package on your VM-based Windows to complete the installation.
The remaining installation process will be done automatically, which may take between 2 to 3 hours to finish depending upon your Internet speed.
“The VM will reboot multiple times due to the numerous software installation requirements,” FireEye says. “Once the installation completes, the PowerShell prompt remains open waiting for you to hit any key before exiting.”
After the completion of the installation process, you’ll be presented with Commando VM, and all you need to do is reboot your machine to ensure the final configuration changes take effect.