Nakedsecurity aka Sophos posted about a version of Locky ransomware found within documents. The original post can be found HERE. It is always interesting to see how ransomware attacks evolve…..
SophosLabs has discovered a new spam campaign where ransomware is downloaded and run by a macro hidden inside a Word document that is in turn nested within a PDF, like a Russian matryoshka doll. The ransomware in this case appears to be a variant of Locky.
Most antivirus filters know how to recognize suspicious macros in documents, but hiding those document inside a PDF could be a successful way to sidestep it, according to SophosLabs researchers.
What the latest tactic looks like
Following the typical pattern, this latest ransomware push comes as emailed spam with a PDF attachment: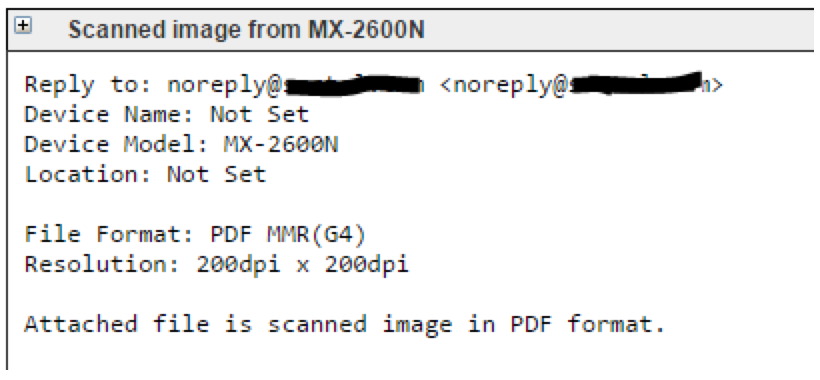
The PDF has an attached document inside, which is trying to get opened by the Acrobat Reader: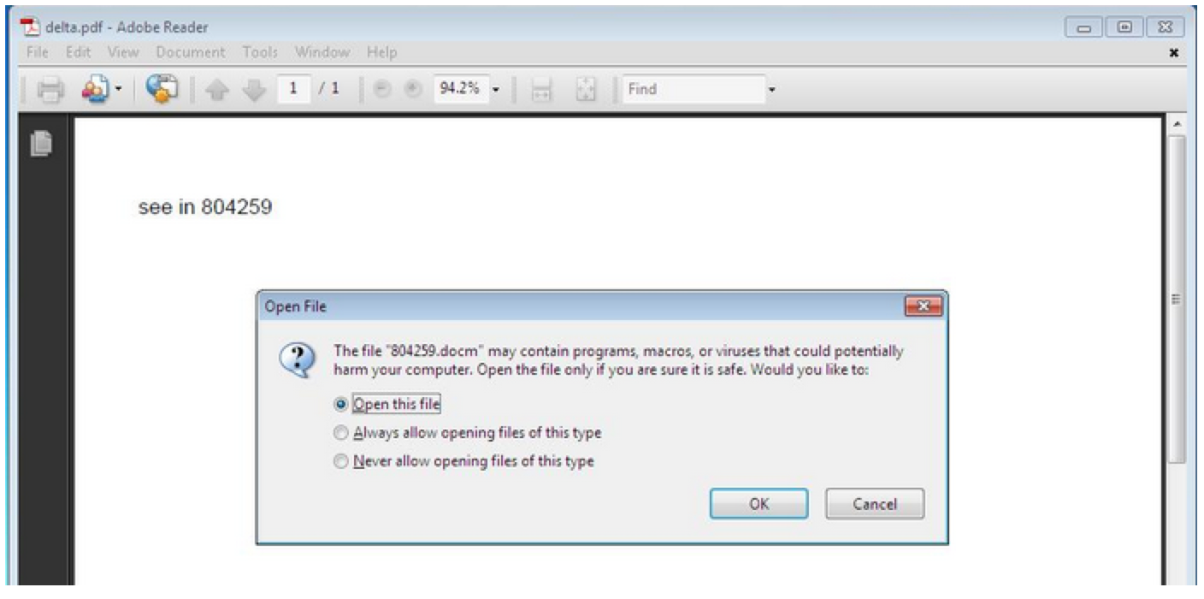 Once the doc is opened in MS Word, it asks you to enable editing through a social engineering attack:
Once the doc is opened in MS Word, it asks you to enable editing through a social engineering attack: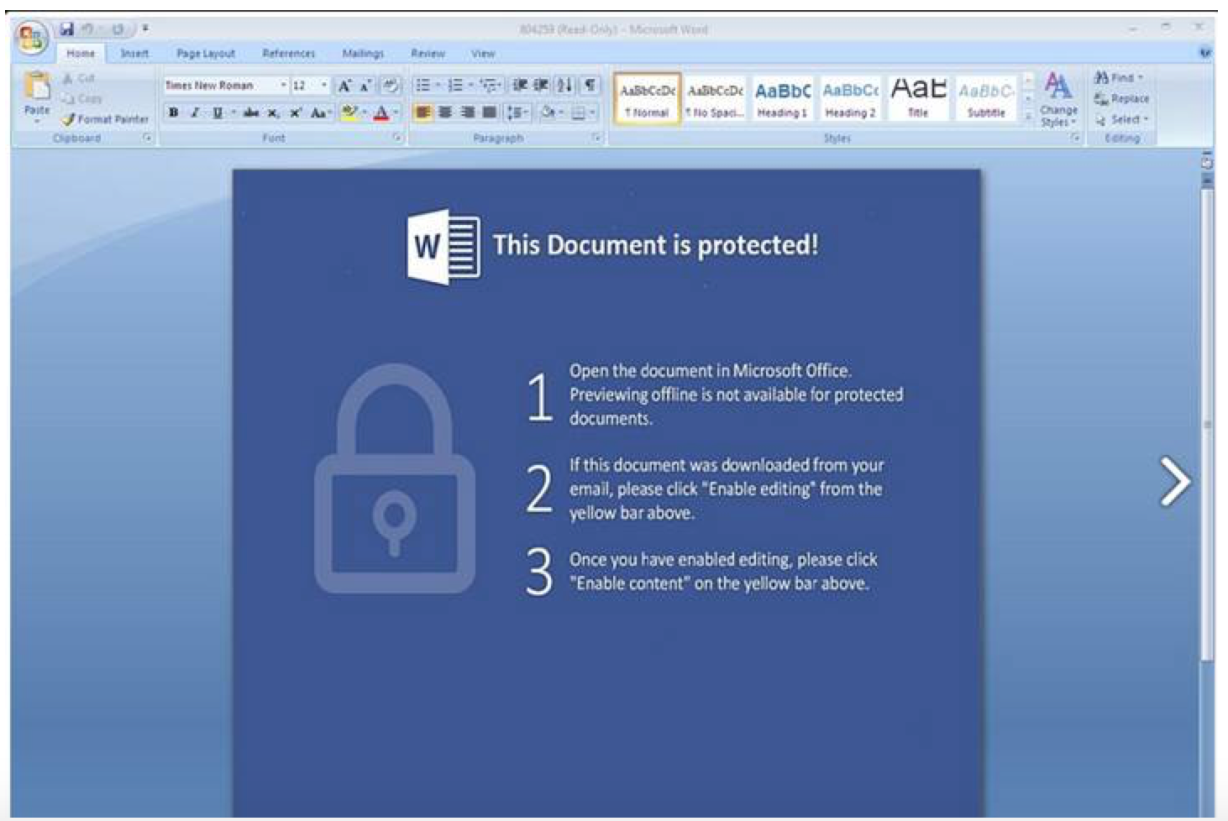 This runs a VBA macro, which downloads and runs the crypto ransomware.
This runs a VBA macro, which downloads and runs the crypto ransomware.
What to do?
There are things people can do to better protect themselves from this sort of thing:
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit. In the case of this attack, users want to be sure they are using the most updated versions of PDF and Word.
- Use Sophos Intercept X, which stops ransomware in its tracks by blocking the unauthorized encryption of files.
Sophos detected the PDF as Troj/PDFDoc-C and the payload as Troj/Locky-UP.
Other links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.