CyberX labs posted about a malware that is now modified as ransomware and targeting Industrial networks. I really liked the list explaining why attackers are targeting industrial networks. The original post can be found HERE.
CyberX’s threat intelligence research team has uncovered new evidence that the KillDisk disk-wiping malware previously used in the cyberattacks against the Ukrainian power grid has now evolved into ransomware.
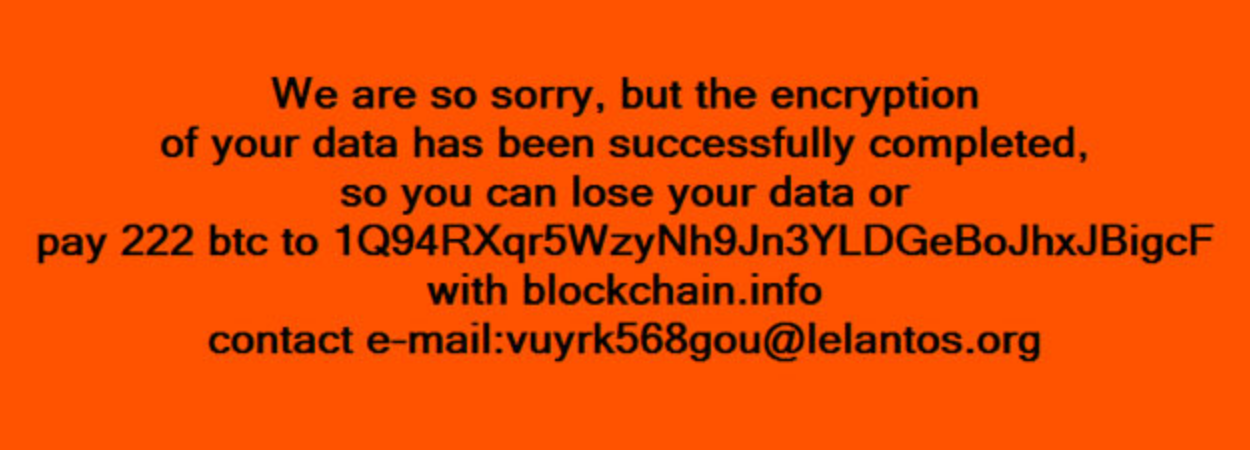
By reverse-engineering the new malware variant, CyberX’s team (led by David Atch, VP of Research) found that it displays a pop-up message (below) requesting 222 Bitcoins or approximately $206,000 in return for the decryption key.
The new malware encrypts both local hard-drives and any network-mapped folders that are shared across the organization, using a combination of RSA 1028 public key and AES shared key algorithms, where each encrypted file has its own AES key. The contact email uses a secure, anonymous email service (lelantos.org) to hide the identity of the attackers. We believe the malware is being distributed via malicious Office attachments.
 How Sandworm Previously Attacked Industrial Networks
How Sandworm Previously Attacked Industrial Networks
This new variant of KillDisk was developed by the TeleBots gang, a group of Russian cybercriminals believed to have evolved from the Sandworm gang. The Sandworm gang is responsible for a string of attacks in the United States during 2014 that compromised industrial control system (ICS) and SCADA networks using a variant of the BlackEnergy malware. According to a December 2014 alert from the DHS, this “sophisticated malware campaign” compromised human-machine interfaces (HMIs) at a number of US companies. HMIs are used to control critical industrial processes such as power generating equipment and chemicals production.
It’s also believed the Sandworm gang conducted the Ukrainian ICS/SCADA attacks during December 2015 and January 2016. The TeleBots gang recently moved into cyber-sabotage attacks against Ukrainian banks, using a version of KillDisk that displays the Mr. Robot image shown above.
We’ve already seen indications that cybercriminals are targeting chemical plants in eastern Europe for extortion. This was discussed in a security research presentation at Black Hat 2015 and DEF CON 23 entitled “Rocking the Pocketbook: Hacking Chemical Plants for Competition and Extortion.”
Why Cybercriminals Are Now Targeting Industrial Networks
According to FBI estimates, ransomware is projected to be a $1B industry in 2016. The transition from destroying disks to encrypting them for ransomware makes a lot of economic sense for industrial cybercriminals, because it enables them to monetize their attacks rather than simply performing cyber-sabotage.
Industrial organizations are excellent targets for ransomware because:
- When operational data upon which physical processes rely becomes unusable – such as HMI data — this can lead to significant consequences including catastrophic damage to production assets, production outages, and risks to physical safety.
- Industrial organizations can’t easily shut down network operations to prevent malware from spreading, because industrial processes themselves can’t easily be shut down.
- Enterprises are more likely to quietly pay the ransom because of concerns that going public with cyberattacks will invite greater scrutiny from regulators, and possibly fines (environmental, safety, etc.).
- Operational Technology (OT) environments are often less mature than IT environments and, as a result their data backup processes may not be sufficient to restore all required data.
- Employees are production workers who tend to have less security awareness training and are more likely to open malicious documents delivered via phishing emails.
- Like healthcare’s focus on HIPAA compliance, the primary focus for industrial organizations has typically been on ensuring regulatory compliance (e.g., NERC-CIP) rather than strengthening cybersecurity controls.
How Industrial Organizations Can Protect Themselves
Protecting your ICS/SCADA networks from sophisticated cybercriminals and nation-states requires a serious commitment from management to ratchet up your security controls.
This is especially true as IT and OT networks are converging to support new initiatives such as SmartGrids and Smart Manufacturing, increasing the likelihood of cyberattackers accessing critical industrial systems via the Internet or via careless employees on the IT network.
In particular, we recommend:
- Ensure OT backup processes are monitored to make sure they’re functioning properly.
- Invest in security awareness training for all employees.
- Segment OT networks as much as possible to prevent malware from spreading.
- Perform continuous risk assessments on OT networks to identify vulnerabilities such as unauthorized Internet and other remote connections, and unpatched devices and systems (for example, CyberX has reported on vulnerable HMIs, industrial firewalls, PLCs, and Industrial Internet of Things (IIoT) devices).
- Continuously monitor all OT network activity in real-time to identify behavioral anomalies indicating the presence of targeted threats and industrial malware.





I wonder what fine or how many years of imprisonment one of these hackers would get in case he got caught.