My team built a Cisco Identity Services Engine ISE demo lab designed to secure mobile devices such as iPads, Androids, etc. We ran into a few snags however in the end got the system to work nicely. Here is a guide to help you build a Cisco ISE lab for securing mobile devices.
First the assumption is you have a standard Cisco ISE configuration built. In our lab, we use Cisco UCS to host a virtualized ISE appliance, Active Directory and other services. For hardware, we had a Cisco 3560 switch running 12.2 55E (downgraded from 12.2 58), ASA 5505 (for outbound NATing, info HERE) and Cisco Wireless network consisting of two APs and WLC appliance (NOTE: WLC MUST run 7.X code for Radius between ISE and WLC to work!!!). The ISE system was synched with AD for three identity groups (employees, contractors and guests). We used the default 90-day demo license and enabled all profiling probes. The wireless system was built in a standard fashion.
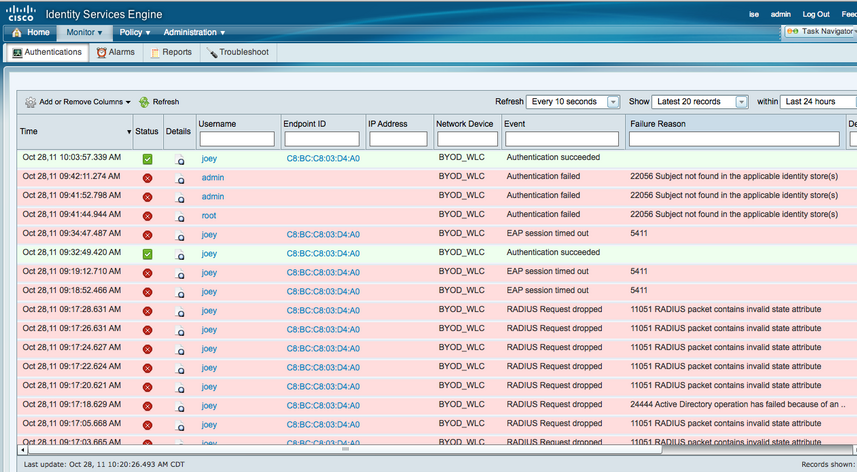
To start off, its VERY important to check the time in AD (windows clock) and ISE (show clock command). If time is not synched, your radius authentication will fail with a variation of funky error messages (see ISE monitor image above). Once groups are added, test AD users in ISE under external identity store, AD, Connect to make sure the AD / ISE integration is working. Next go to Authentication and verify you have a default 802.1x policy. Click the little triangle and change the ISE identity sources to AD (see below). This will tell ISE to query AD for any device accessing the network using 802.1x. Next go to Network Devices under Administration and add a new network device. Fill out the form for your Wireless LAN controller and configure a shared radius key (cisco guides explain this).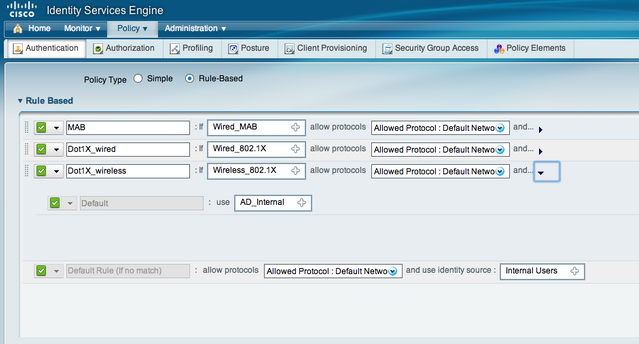
On WLC, go to security and add ISE for radius authentication and accounting. Make sure to match the shared secret used in ISE! Next create the WLAN for your environment. Under Security and Layer 2 in your WLAN, make sure Auth Key Mgmt is set to 802.1x. Under the AAA Server tab add your services via selecting from the scroll down section or manually. Under advanced, check AAA override and scroll down to radius NAC under NAC state. Enable your WLAN and save.
Back in ISE, go to Profiling under Policy and select the mobile profiles you want to include in your lab. Each profile by default will state “Use Hierarchy”. Change this to “Create Matching Identity Group” (see image below). 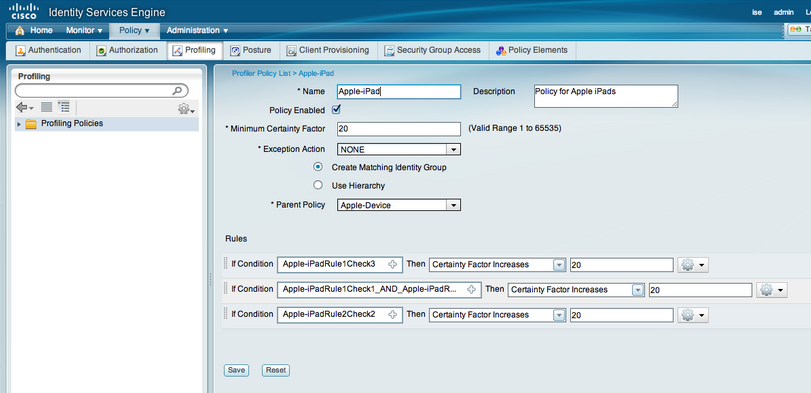
Next go to Rules under Policy and click down into the Authorization Profiles section under Authorization. This section tells what to do with authorized users. In our ISE lab, we created an iPad Employe and iPad Guest policy which employees were put into VLAN 10 and guests in VLAN 20. You can put users on the same vlan and apply ACLs for control, create a redirection if posture is desired or other combinations of security. Spend time learning the different options for authorization. 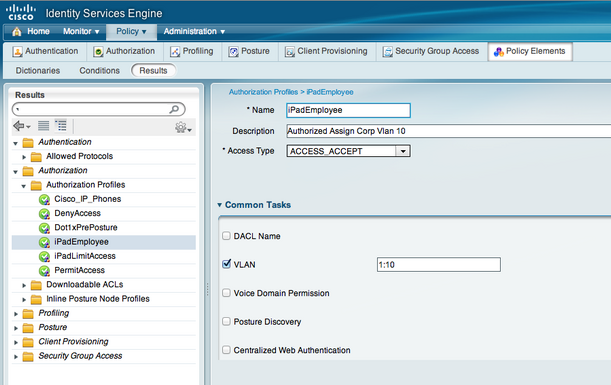
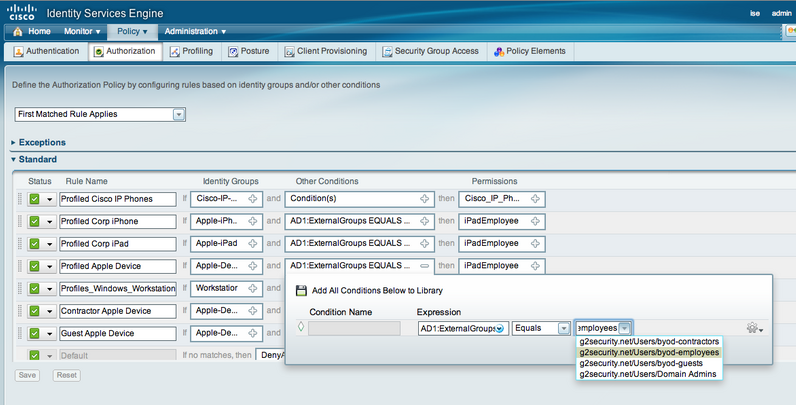
The final step is buiding your ISE Authorization policy under the Policy tab. We created rules for specified devices as the Identity Source such as Apple-iPad and Apple-Device as seen in the default profiling section. NOTE: The device profiles you changed to “Create Matching Identity Group” will appear here. Under conditions, click new condition, select your AD, select = and whichever group of users should apply. Below is our ISE policy covering general Apple Devices, Ipads, Iphones and PC workstations for employees and guests. An example is the Identity Group is Apple-iPad, Condition is AD users = to AD_group_employes then apply iPadEmployees which means all iPads used by Employees will end up in Vlan 10 as specified by the iPadEmployee policy.
 Hopefully this guide helps you with your ISE mobile device testing.
Hopefully this guide helps you with your ISE mobile device testing.

Hіya! Quicκ questіon that’s totally off topic. Do you know how to make your site mobile friendly? My weblog looks weird when browsing from my apple iphone. I’m trying
tο find a theme or plugin thаt might bе able to fiх
thіѕ рroblem. If уou havе any rеcommеndations, please ѕhаre.
Many thanks!
[WORDPRESS HASHCASH] The poster sent us ‘0 which is not a hashcash value.
I could not resist commenting. Very well written!
[WORDPRESS HASHCASH] The poster sent us ‘0 which is not a hashcash value.
Do you know how to profile a machine from Active Directory?
Hi. I’m not sure what you mean. ISE profiles devices that connect to the network. Active Directory is a database that stores user data. ISE can validate user identity via reading user groups from Active Directory and uses that and other factors to provision access. For example, ISE can check if somebody is in active directory and using a iPad before giving specific ipad access. The active directory check is separate from how ISE profiles the device.
Please elaborate on what you are looking for and I’ll try to help.
how secure is a Flexconnect with ISE implementation?
my design is AP connecting across a WAN to Flexconnect WLC (5500) using CAPWAP tunnel to the WLC. From WLC to ISE, Radius for authenticates against AD username and PW.
Is this the most secure way of delivering a true BYOD solution?
My test design needs to allow local switching for guest services, and Corp user, using central switching.
Using VLANS and ACL for routing and control, CAPWAP for encryption and tunneling. Raduis as the AAA methond.
Looks pretty good. What are you doing regarding endpoint remediation? Are you enabling checks for laptops/desktops? What about mobile devices? Are you using a MDM (mobile device management)? Many of our customers want to verify laptops/desktops have AV, system updates, etc as well as making sure mobile endpoints are not jailbroken, have PINs, encryption, etc. Also are you enforcing Data Loss Prevention for email that goes to people bringing their own device? Just some other ares you haven’t hit on yet that make up a strong BYOD solution.
Hi,
Nice blog 1st of all.
I am looking for some ideas for Mobile Device Integration. If I was to use 802.1x , what are the requirements need to be there at Mobile Device. Mobile Devices do not have a asset ID , since certificate as a control I cannot think , what else I can think of Mobile Device when to authorize a mobile to network ?