Many customers use Cisco networking products however don’t enable built in security features included with standard software. You can find many of these by searching google or checking out Cisco campaigns such as “Turn It On”. Some of my favorite commands typically not used by customers are Control Plane Policing, NetFlow, IP SLA, Embedded Event Manager and Port Security.
Many customers use Cisco networking products however don’t enable built in security features included with standard software. You can find many of these by searching google or checking out Cisco campaigns such as “Turn It On”. Some of my favorite commands typically not used by customers are Control Plane Policing, NetFlow, IP SLA, Embedded Event Manager and Port Security.
The route processor of Cisco devices is critical to network operation. Disrupting the route process can lead to network outages (IE denial of service attacks). Control Plane Policing (CPP) protects the control and management planes, which ensure routing stability through filtering and rate limiting control plane packets. Some administrators may use multiple ACLs to defend against these types of denial of services attacks however ACL management complexity increases as the networks scales. Best practice is to enable CPP to improve reliability of your infrastructure against this threat vector.
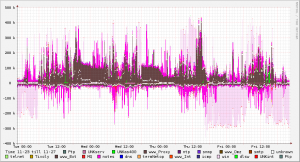 Netflow is one of the most common methods industry toolsets acquire IP operational data. Most Security Event and Information Management (SIEM) tools leverage NetFlow for network planning, security monitoring, traffic analysis and modeling. Regardless of what tool you use, best practice is to baseline your network using NetFlow and monitor for anomalies in behavior (IE. if one day there is a spike in network traffic at 2am, you may have a problem). This provides a behavior layer of defense in the event other toolsets fail to recognize a threat. There are many open source NetFlow tools such as FlowScan, FreeBSD, Netmet, etc. if you don’t have the funding for a SIEM or dedicated NetFlow analyzer such as Lancope or Fluke. Best practice is to have NetFlow as part of your security analysis.
Netflow is one of the most common methods industry toolsets acquire IP operational data. Most Security Event and Information Management (SIEM) tools leverage NetFlow for network planning, security monitoring, traffic analysis and modeling. Regardless of what tool you use, best practice is to baseline your network using NetFlow and monitor for anomalies in behavior (IE. if one day there is a spike in network traffic at 2am, you may have a problem). This provides a behavior layer of defense in the event other toolsets fail to recognize a threat. There are many open source NetFlow tools such as FlowScan, FreeBSD, Netmet, etc. if you don’t have the funding for a SIEM or dedicated NetFlow analyzer such as Lancope or Fluke. Best practice is to have NetFlow as part of your security analysis.
A great compliment to utilizing NetFlow for network monitoring is enabling IP SLA. NetFlow captures are what your devices actually observed while IP SLA is a proactive synthetic probe. IP SLA offers a broad set of measurement features such as latency, queuing delays, jitter, packet loss, burst loss and packet recording. IP SLA is bidirectional and enabled on two devices via a responder and transmitter which traffic is sent between devices and tested. IP SLA can verify network operation, monitor network health, and identify and resolve bottlenecks. Use it … especially when evaluation for VoIP capabilities.
Response time is a critical element for most network management teams. Embedded event manager (EEM) enables Cisco devices to email administrators when specific settings are triggered in near real-time. This is accomplished through scripts that can be found on the EEM community via HERE. Basically EEM can transform Cisco devices into active participates in network monitoring rather than requiring an external tool such as a SIEM or other solution for event notification.
 One final cisco IOS feature to consider is Port Security. Best practice for Access Control is to leverage automated security enforcing authentication, authorization and remediation, IE Network Admission Control, which is explained in details HERE. A free Access Control feature that prevents MAC address-flooding attacks is Port Security. Port Security limits and identifies the MAC addresses of devices allowed access to an assign switch port. Be careful on what MACs stick or you may end up running around re-enabling error disabled ports. Port Security is a good idea for static machines such as printers or desktops (not laptops) assigned to an office space. Port Security does not scale well so consider automated access control (NAC) for medium to enterprise networks.
One final cisco IOS feature to consider is Port Security. Best practice for Access Control is to leverage automated security enforcing authentication, authorization and remediation, IE Network Admission Control, which is explained in details HERE. A free Access Control feature that prevents MAC address-flooding attacks is Port Security. Port Security limits and identifies the MAC addresses of devices allowed access to an assign switch port. Be careful on what MACs stick or you may end up running around re-enabling error disabled ports. Port Security is a good idea for static machines such as printers or desktops (not laptops) assigned to an office space. Port Security does not scale well so consider automated access control (NAC) for medium to enterprise networks.
These are just a few free Cisco features you should consider to turn-on to maximize your investment.