I wrote a post comparing Cisco’s Next Generation Firewall known as ASA CX vs. Cisco’s Web Security Appliance / Proxy known as WSA HERE. Here is a update to that post as requested by some readers.
In summary, the WSA is a security appliance that can act as a proxy focusing on network bound traffic such as port 80, 443 and 21. The ASA CX is an all ports and protocol firewall with reputation and IPS security (IPS being added in October 2013). Both solutions can provide reputation based security meaning stopping the attacker (more on this concept can be found HERE), Integrate with authentication systems such as Active Directory, can view HTTPS via decryption, application visibly with policy enforcement (IE identify and block Farmsville within Facebook) and detection of threats however detection methods are slightly different (one uses a combination of AV / malware engines while the other uses IPS). 
Here is a summary of some differences
ASA CX
- All ports and Protocols
- Full featured Stateful and Application Firewall
- Remote Access and Site-to-site VPN
- New: IPS/IDS
WSA
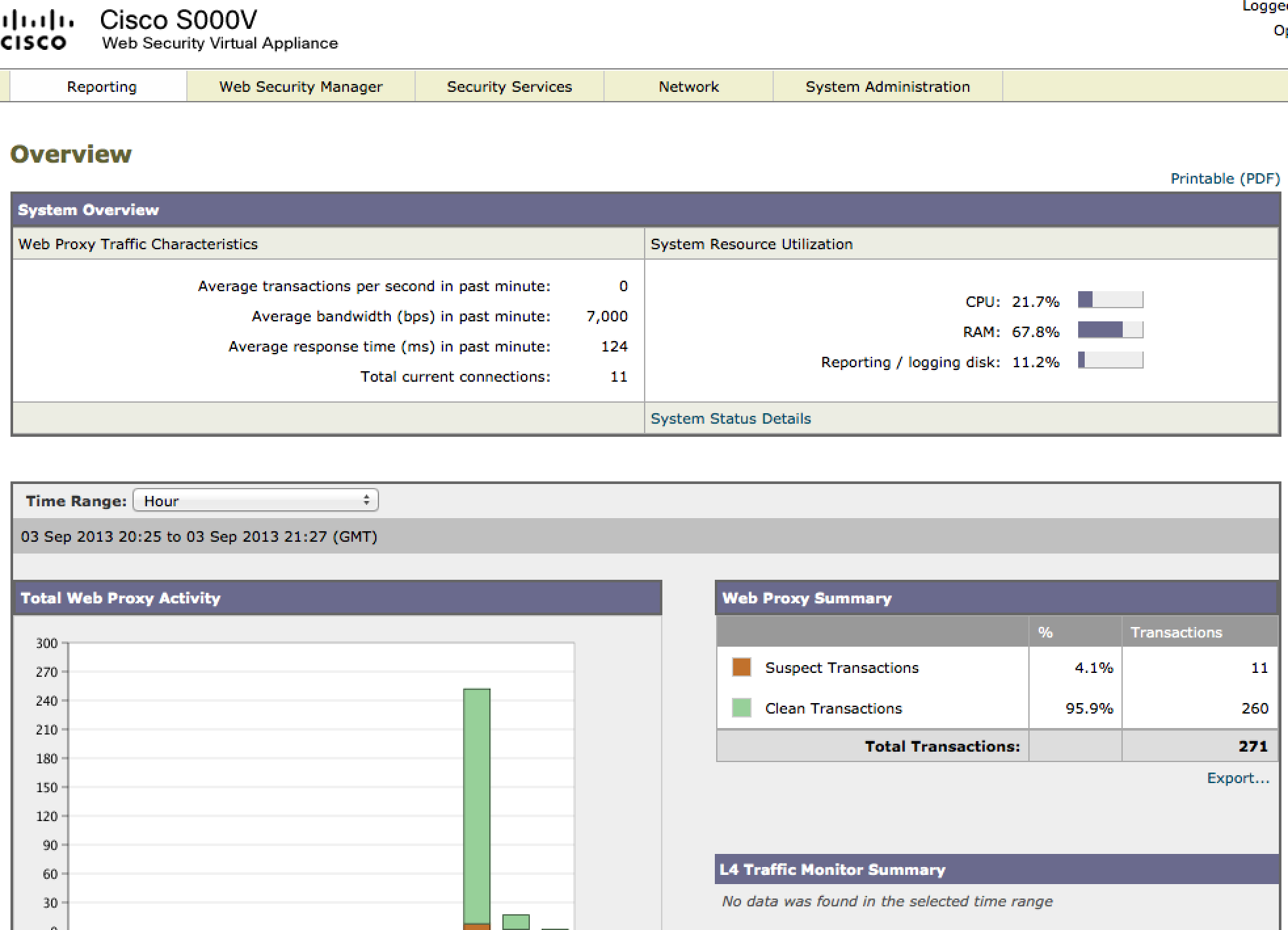
- Ports 21, 80, 443 (protocols HTTP(s), FTP)
- Malware scanning on top of reputation security
- Multiple scanners such as Anti-Virus, Malware, etc can be layered.
- Data Loss Prevention
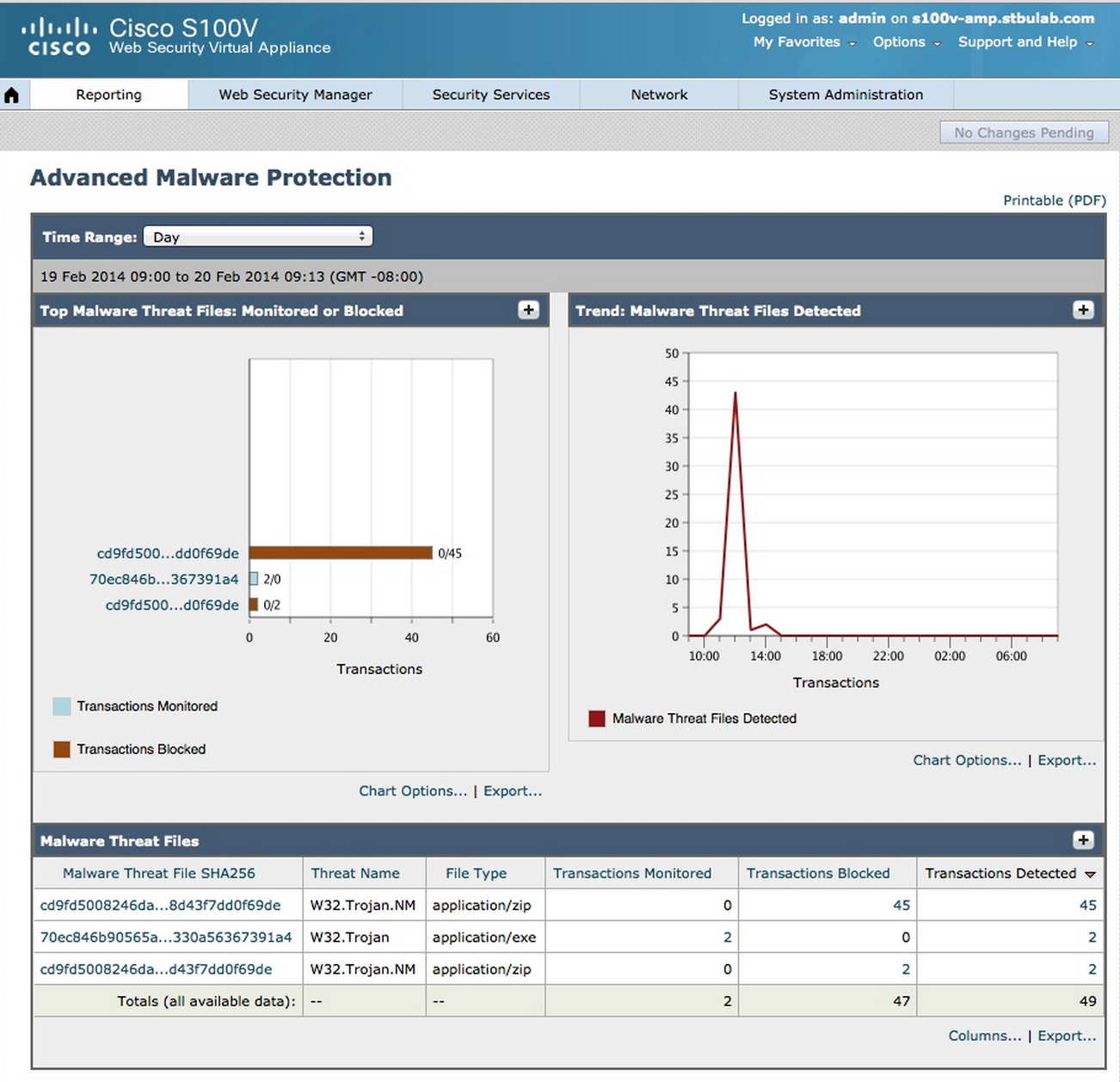
- New: FireAMP (detect infected files). See HERE for more on the announcement.
- New: Virtualized, Appliance or Cloud offering
The summary above includes some of the recent updates to both platforms. There is also a new addition to the web security portfolio leveraging SourceFire FirePower appliances with the recent SourceFire acquisition. FirePower’s core capabilities is IPS however there is a license available to enable application firewall capabilities.
Which technology is best for you?
The first question comes down to if you should go with a Next Generation Firewall or Web Security Proxy. You should consider Cisco’s Proxy if you are looking for web caching, desire scanning through anti-virus / malware engines, integrated data loss prevention, requirements for a proxy (IE redirecting traffic with WCCP or host inline proxy requirements) or in March 2014 the ability leverage SouceFire’s FireAMP capabilities. The Proxy route also offers a few deployment options, which are physical appliance, virtualized appliance or cloud.
To elaborate a little on FireAMP, it offers the ability to identify and remediate infected files. This is done through scanning for hashes, sandboxing unknown files and various detection mechanisms based on behavior and reputation. The last big value from FireAMP is retrospective security meaning “stopping the bleeding”. Once a malicious file is identified, FireAMP can specify the history of the file and offer remediation IE removing the file off any infected system. Without retrospective visibility, you will only know of the infection and have to continuously “scan and fix” other infected hosts. FireAMP is part of the SourceFire or WSA via appliance, cloud and VM offering as of March 2014.
FireAMP in Cisco Web Security Appliances WSA
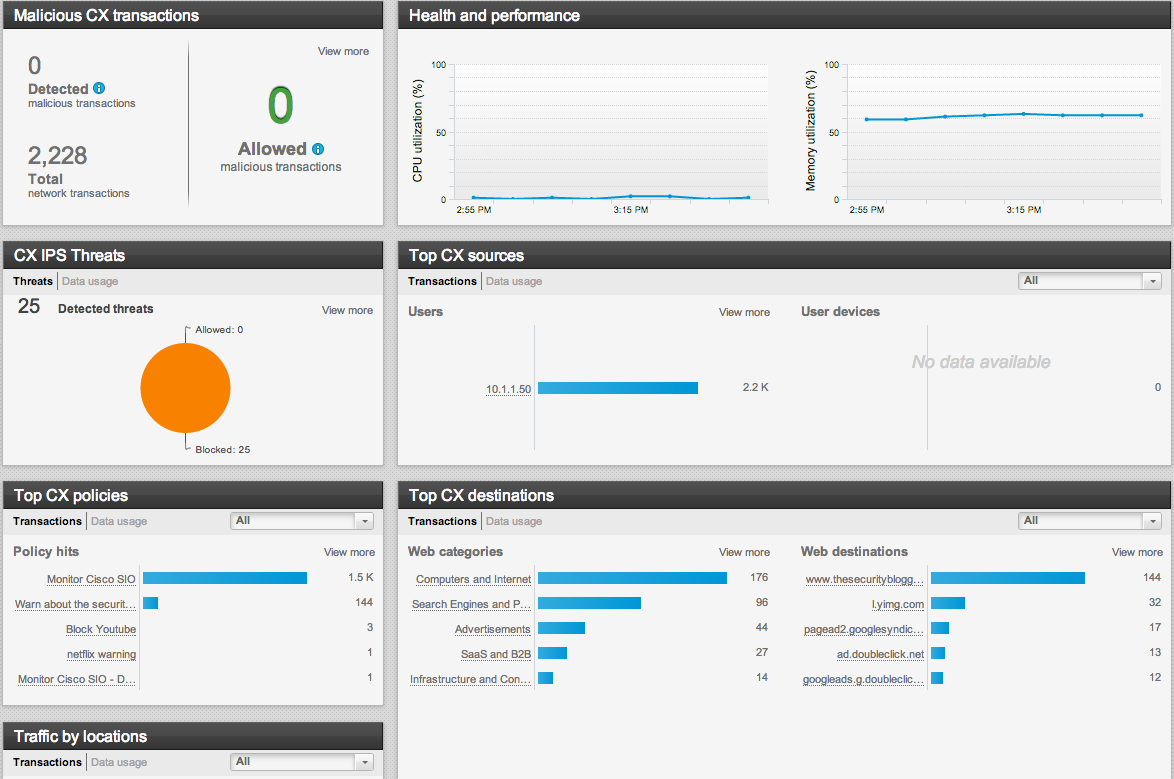
You should consider a next generation firewall if you are looking to consolidate hardware (firewall, VPN, reputation, IPS and application security as well as multi-context firewall support), need security for all ports and protocols, Internal visibility such as identifying an iPad using a Sarfi browser, and lastly blend network and web application security controls, IPS and Firewall management into one centralized dashboard.
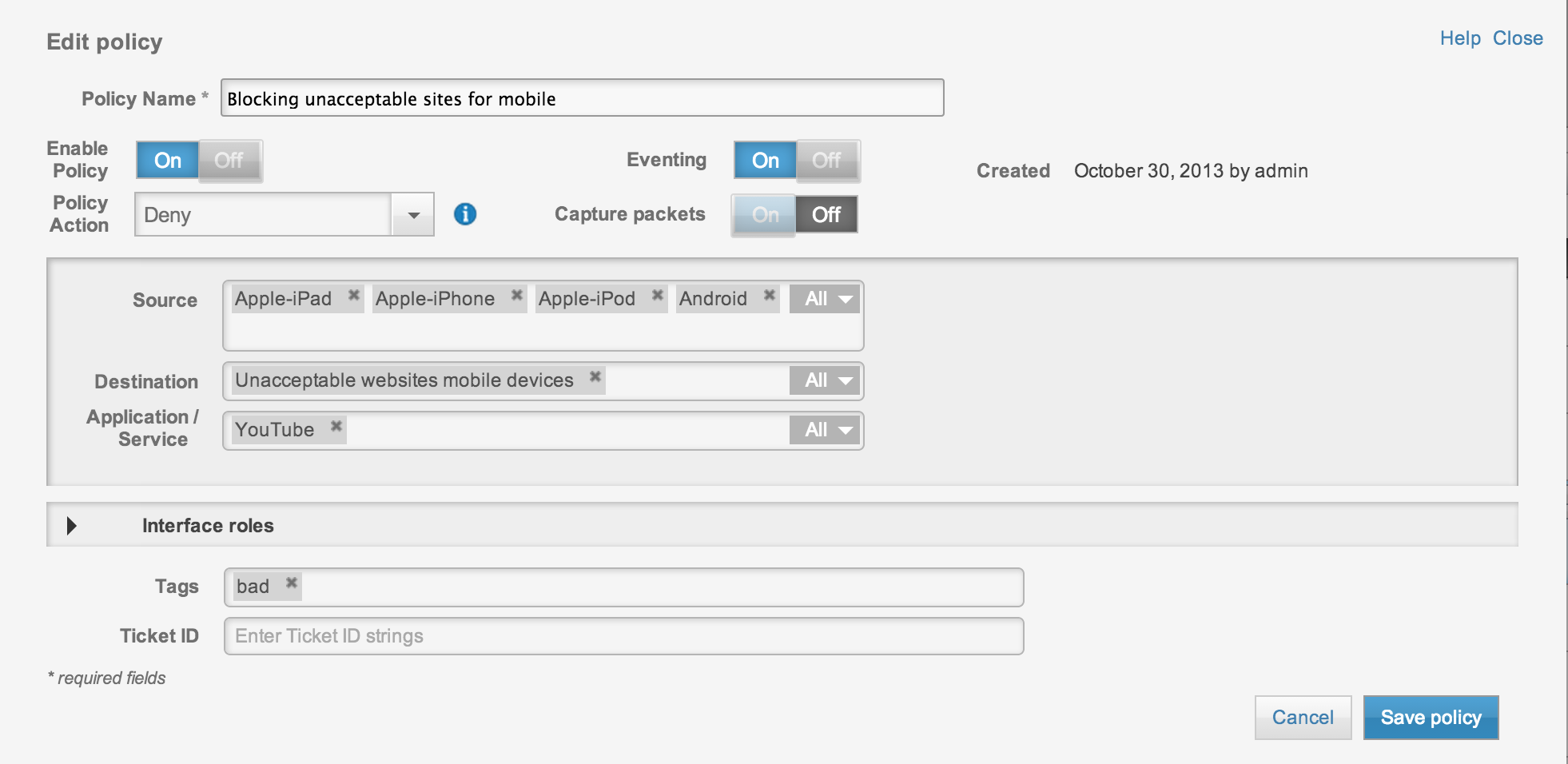
ASA CX example showing blocking Unacceptable sites (adult, gambling, etc) for only iPads, iPhones, iPods and Androids
If you are thinking next generation firewall from Cisco, the last question comes down to ASA CX vs SourceFire. The focus of each offering is different. ASA CX targets customers looking for the most consolidation capabilities and “network centric” or simplified usage. This means those looking for a simple interface that doesn’t have as many tunable options however easy to use IE the “routing, voice and security person’s tool of choice”. Small to medium organizations would target this offering.
SourceFire’s solution has very granular options and 20% more signatures than the ASA CX platform making it ideal for those with a dedicated security shop or have a security background. Large enterprises would target this offering. SourceFire also offers both virtual and physical appliances as well as can scale to higher throughputs than ASA CX.
NOTE: Cisco is releasing four new SourceFire appliances and there is a new ASA CX code coming out spring 2014. This means both platforms are not going anywhere anytime soon.
Hopefully this update helps clear up questions around each offering. There are a lot of options so its best to weigh each pro and con to meet your need.