I have had many people ask about Intrusion Detection / Prevention (IPS / IDS) options you can add to the next generation Cisco Adaptive Security Appliance (ASA) also known as the ASA X Series. The confusion comes from the option to go with a dedicated IDS / IPS vs Application Visibility, Reputation Security and IPS all in the Next Generation Security package part of the ASA CX solution. Here is a overview of how both solutions work.
The core of both offerings is the 2nd generation ASA appliance or ASA X series (more info found HERE). The current latest ASA code release is 9.13. The ASA appliance can be configured using Command line, ASDM or Cisco Security Manager. The appliance should have a IP address so for example sake, lets say its 192.168.1.10. You can access that IP using a standard web browser and the ASA will prompt you for options to manage the ASA using ASDM.
The 2nd generation ASA series offers additional features by either leveraging a SSD hard drive or built directly into the code (as for the IDS/IPS feature). This is done by accessing a virtual space within the ASA so essentially having a virtual service enabled. This is different from previous versions of hardware meaning in the past, adding something like IDS/IPS would require a external hardware module that is inserted into the ASA appliance. The next generation ASA can virtually enable a feature like IDS/IPS inside the virtual space on the ASA and use policy maps to route traffic through that feature.
1st Generation ASA with IDS/IPS module
2nd Generation ASA with SSD
Today there are two options for adding IDS/IPS to an ASA. Option one is installing a dedicated IDS/IPS. This means going with a specific ASA code that includes the IPS/IDS build, giving the IDS/IPS a separate IP address from the core ASA and managing the IDS/IPS separately. So for example, we could give the ASA the IP address 192.168.1.10 and IPS/IDS the IP address 192.168.1.20. Once configured, you can access the IDS/IPS management using a standard web browser that will launch Cisco IPS Manager Express (IME). You could also use Cisco Security Manager (CSM) to managed both the ASA and IPS/IDS along with other security solutions. You do NOT need the SSD drive for this option as all virtual features happen within the ASA appliance. You just need a next gen ASA, proper software code and associated licenses for IDS/IPS.
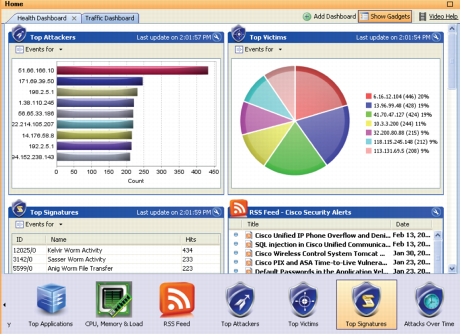
Cisco IME managing IDS/IPS Dashboard
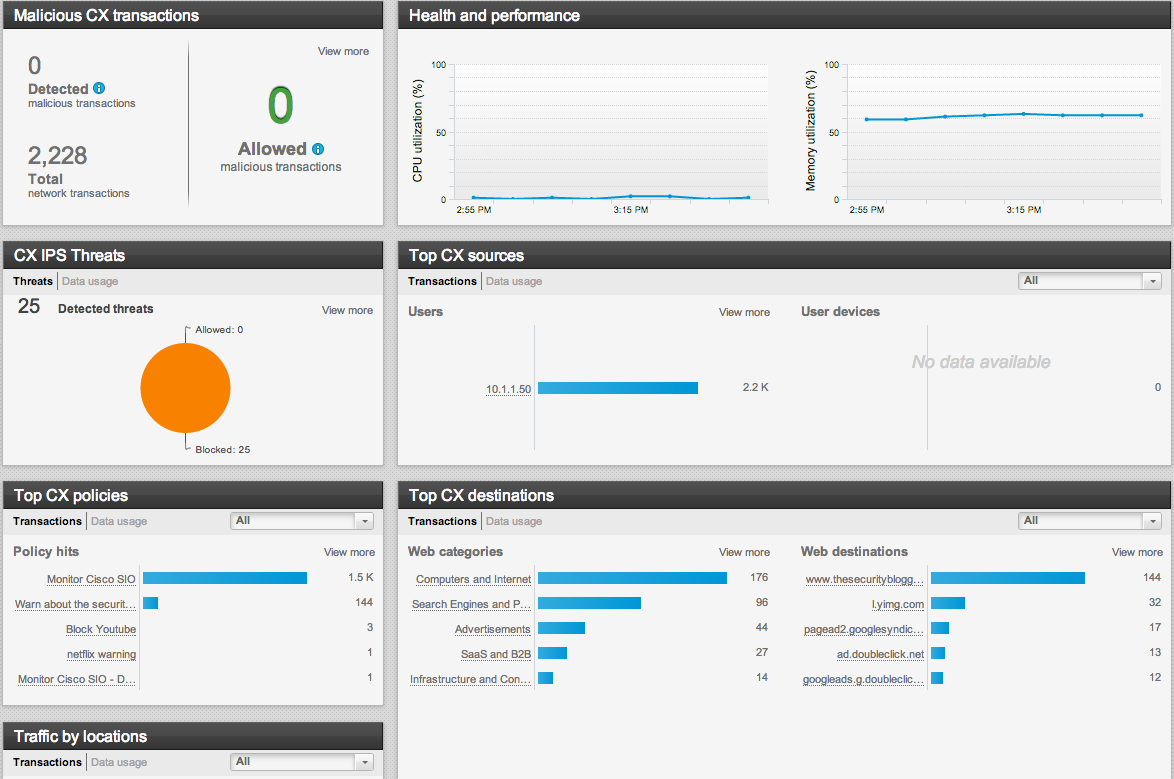
Option two for IPS/IDS is installing Cisco’s next generation security package known as ASA CX. Again, you would install the software and provide a new IP address for te CX features. So lets say you configure ASA CX part to be IP 192.168.1.20. Once you configure ASA CX, you could access the management at 192.168.1.120 using a web browser to bring up local Cisco Prime Security Manager GUI. You could also use an external version of Cisco Prime Security Manager for managing multiple ASAs and CX SSD drives. The current version for ASA CX is 9.2 meaning your ASA would run ASA code 9.13 while the SSD would run ASA CX 9.2 code. The ASA CX features leverage some space on the SSD drive meaning you would need the SSD drive along with ASA CX software and licenses to go this route. 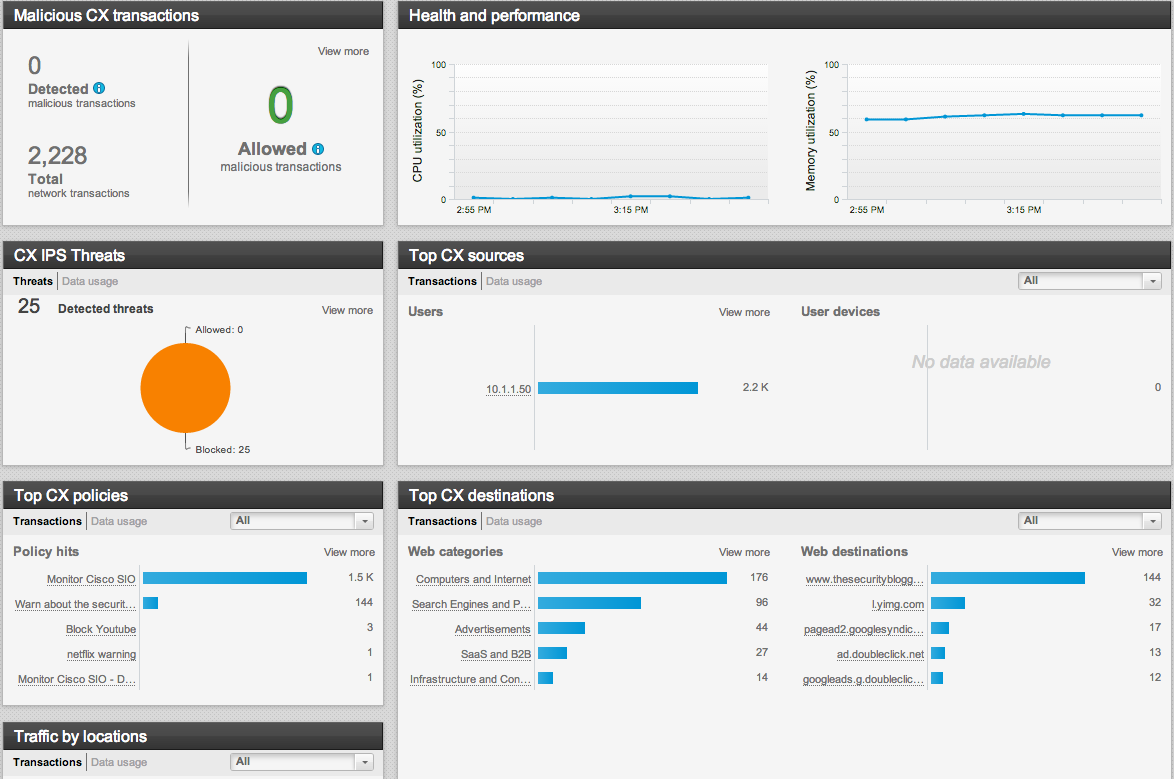
Cisco ASA CX Dashboard
The ASA with IDS/IPS and ASA with CX route both have separate systems running independently in the virtual space on the ASA appliance. For example, you can access the core ASA using command line however you would have to terminal from the ASA to the ASA CX to hit the CX CLI. So for example, here is a image of the ASA CLI and ASA CX CLI. You can find more about configuring ASA CX via CLI HERE.
ASA Command Line
ASA CX Command Line (on older 9.1.2 code)
Regarding migration, you can NOT run ASA CX and dedicated IPS on the same ASA appliances. The ASA CX IDS/IPS aka Next Gen IPS/IDS is part of CX and managed using PRSM while the dedicated IDS/IPS software is managed with Cisco IME. If you want to migrate from one option to another, it will require configuring the core ASA to specify which service you want to use for the virtual space aka run dedicated IPS/IDS or CX along with associated licensing and support. So for example, if you have dedicated IDS/IPS running on the ASA, you would need to issue “sw-module module ips shutdown” followed by “sw-module module ips uninstall” prior to installing the ASA CX SSD drive and going forward with the ASA CX install as explained HERE.
Regarding Cisco Prime Security Manager (PRSM), there is a local version that is free and accessed when you go to the IP address of the ASA CX (similar to accessing ASDM when going to the IP address of the ASA). There is also a PRSM external offering used for managing multiple ASAs and ASA CX installations. The local version of PRSM can configure and manage application layer features, reputation security and IDS / IPS. The external version of PRSM has ASA firewall configuration and management capabilities along with the local PRSM features. An example is pushing an ACL to multiple ASA appliances (ASA feature) along with blocking NetFlix using a CX Policy (CX feature). More feature parity between Cisco Security Manager (CSM) and external PRSM is scheduled for this year with the upcoming PRSM releases.
The million dollar question * Which ASA SSD option is right for you ? *
The answer depends on a few things however a major question is your requirement for IDS/IPS capabilities. The ASA CX with IPS/IDS option has approximately 80% of the signatures expected from a dedicated appliance. The ASA CX also doesn’t have as many customization / tuning features as a dedicated IDS/IPS. The cost however could be outweighed by having visibility and enforcement of policy for all traffic layers (IE control things like Facebook gaming, block adult websites, Identify iPads / Android tablets, know if a user is using Firefox, etc.) as well as the value using the new PRSM interface. For those desiring a very feature rich IDS/IPS, you probably would want a ASA with dedicated IPS or check out the SourceFire Firepower solution. For those looking for one appliance to provide Stateful firewall, Remote Access VPN, Site-to-site VPN, Application Visibility, Reputation Security and IDS/IPS … the ASA with CX would be ideal for you.
Hopefully this helps clear some of the confusion.





Hi Joseph,
Very good post. I was wondering if you are aware about any Cisco document which comperes the IPS (standalone) functionality with IPS embedded in CX?
Thanks,
mih
Hi Mih,
It depends on which dedicated IPS (SourceFire or Cisco’s dedicated IPS). Either way, the ASA CX’s IPS has about 80% of the signatures found in a dedicated IPS. It also isn’t as tunable meaning you can use things like custom signatures or right click an event to add actions such as “don’t alert me to these anymore”. For a simple to use IPS and part of a consolidation project, its great. For those looking for a feature rich IPS, consider a dedicated IPS such as SourceFire FirePower.
Hope this helps
Joey
Do you happen to know if the new ASA CX IPS supports SDEE (Security Device Event Exchange) like the ASA IPS standalone devices?
I’m not sure but will look into it. Sending a email to the BU now to find out. Thanks for the question
This is what I was told
“No. The IPS in CX is a feature of the CX platform and as such uses standard CX operating procedures: i.e. PRSM for all eventing.
Cisco IPS used an entirely different framework: SDEE”
Thanks, that’s a similar response I got from Cisco yesterday as well.
To make sure I understand, is this saying there are 2 different ASA based options.
– There is the ASA CX which is more all in one, including a light IPS (80% of sigs?).
– Then there is the ASA IPS Edition which is more of the full fledged IPS and self-managed using IPS Express Management.
Hi Steve,
Yes the ASA CX route is consolidating multiple functions into one solution (Firewall, Application Visibility and Controls, IPS/IDS, VPN and Reputation security). The IPS capabilities are not as tunable as a dedicated appliance and there are around 80% of the signatures found in a dedicated solution.
The dedicated IPS has more signatures, tuning capabilities and features than the consolidated version. We recommend a SourceFire’s FirePower appliance or the dedicated Cisco IPS software inside the ASA for this purpose.
Hope this helps
How about Sourcefire IPS code running on the new ASA? Now that Cisco owns Sourcefire it only makes sense. I’m sure the ASA hardware could handle it with the addition of the hard drive. I think we will hear about this very soon.
Ask this question next week at Cisco live. It is coming
I arrived here after trying to find out if we have an ASA CX, because it is allegedly vulnerable to shellshocked.
We have 5585-X’s. It’s entirely unclear from Cisco’s documentation, ASA CX FAQ, and datasheets what ASA CX actually is. I’m sure a salesman can sell us one, but if we already have a 5585-X, it’s impossible to tell what we need to upgrade it – if we have to at all.
Is the 5585-X a next generation firewall, a 2nd generation firewall, or is it a Next Generation Firewall? Is ASA CX a Next Generation Firewall installed in a next generation firewall? If so, what do we need to do to a 5585-X to change the capitalization of its description, other than spend futile hours searching cisco.com? Is it simply a code upgrade, or a hardware upgrade, or both?
The link you included to the Cisco rabbit hole, has the absurd Cisco marketing statement:
“Cisco offers two next-generation firewall solutions on the Cisco ASA 5500-X Series and ASA 5585-X Adaptive Security Appliances.”
What, a 5585-x is not part of the 5500-X series? What school of marketing algebra is this?
The same problem of marketing driven documentation exists with the X series (oh, and the 5585-X) and IPS/IDS. These require an SSP-20 module, which all X’s come with, I believe. Carefully hidden is the fact that one needs 2 SSP-20s to do IPS/IDS – that the IPS/IDS needs a dedicated SSP 20 module. This is a little better in more recent documentation, but I cannot get the hours of searching and reading back. TCO is now much less than it could have been as a result.
So is the ASA CX like the IPS/IDS – a hardware solution?
In any case, thanks very much for this comparison.
Hi Anonymous,
Whoh lets back up and hopefully I can help you. To be clear on a few things
1) ASA 55XX series is our newer firewall security appliances. So 550Xs is our 1st generation hardware (example 5580s or 5520s) while 55XX is our 2nd generation hardware (example 5585s, 5525s). The major differences between the two is around performance and ability to add other security features. You can find more on this here http://www.cisco.com/c/en/us/products/security/asa-5500-series-next-generation-firewalls/index.html.
2) Part of the newer things you can add to a 2nd generation ASA is the ability to install something in a virtual space inside rather than physically sticking in a module in the back the appliance. For example, with a 1st gen ASA, you would have to buy a IPS module to add that. For the 2nd gen hardware, you would just install the software in the virtual space on the ASA to add it.
3) There are a few “security packages” available for the virtual space in a ASA. One of those packages is SourceFire (we just announced). You can find a post talking about how I installed in on my ASA here https://www.thesecurityblogger.com/?p=4434. This gives you IPS, Application Visibility and controls, and Advanced Malware detection.
4) Another package option ASA CX. I posted on installing this on a ASA HERE. https://www.thesecurityblogger.com/?p=2756. This gives you IPS, Application Visibility and Controls.
5) The PSIRT team at Cisco can give you the latest on vulnerabilities such as BASH / Shellshock. See this for more http://tools.cisco.com/security/center/publicationListing.x
Lets look at your situation. A 5585 is a Firewall and VPN concentration depending on what you have licensed. In order to have ASA CX, you would have to have that software purchased and licensed. There is also a SSD blade required for only the 5585s to accommodate the traffic load for application layer data so you would need that as well. My assumption is you don’t have ASA CX since you didn’t mention the SSD blade or any licensing around IPS, URL or Application Visibility.
Hope this helps. You should reach out to your Cisco support rep or trusted partner to help evaluate what you have. There may be things you own or suppose to have to that you have not turned on.
Lets look at your situation.