Cisco released 9.2 for ASA CX and Prime Security Manager October 14th 2013. I finally got around to updating my system and so far some features are awesome while others can be improved with future releases. Here is a general overview of what is new with CX 9.2 for the mid range appliances has to offer. The formal release document can be found HERE.
NOTE I’m not covering everything from this release such as the new modules for the 5585x series or PRSM updates. I’m just touching on what I have used in my lab using my ASA 5515X.
To kick things off, the upgrade process was pretty easy. I verified I am running the correct version of ASA code (9.1.(3)) and downloaded the .pkg file from Cisco.com. I went to the upgrade manager tab in the CX GUI and uploaded the file. I selected to install and it took around 10 minutes to upgrade and reboot.
Upgrade Manager in CX
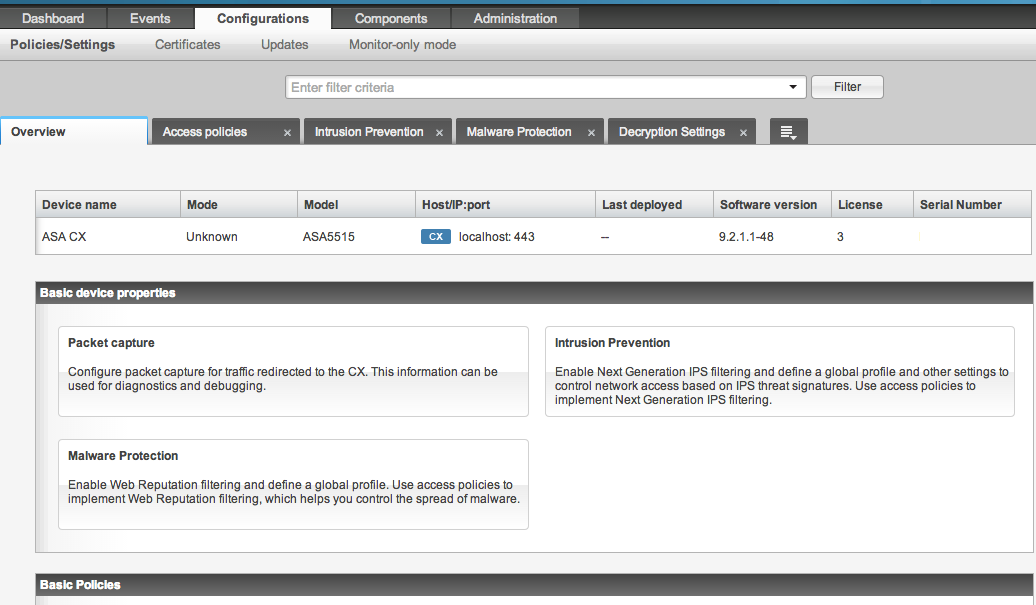
The first thing I noticed post upgrade is the layout has been updated. The Configuration tab now has a Overview tab featuring explanations of what can be configured. As you select things such as Access Policies or IPS, it opens a new dedicated tab. The screenshot below shows tabs I opened while testing. The Objects and other components called out by policies were moved to a separate tab called Components. This makes things a little easier regarding what is being enforced and what you are creating to later add to a policy.
New Feature Highlights
- ASAs can now be in multiple context mode and support ASA CX. This is important for service providers or others looking to consolidate multiple firewalls into one box yet maintain the latest ASA next gen features
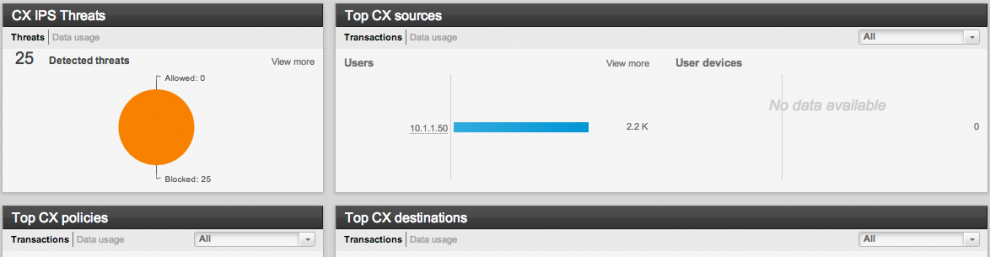
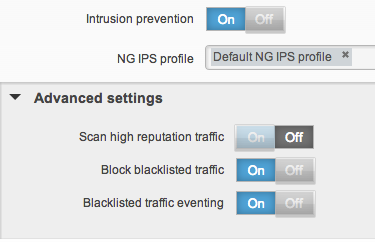
- You can now run IPS with ASA CX. This has been a long waited feature as prior to this release, you could only run IPS with ASA or CX/Next Generation Firewall with ASA. Now you can do all three. Here is a screenshot of the IPS enable tab
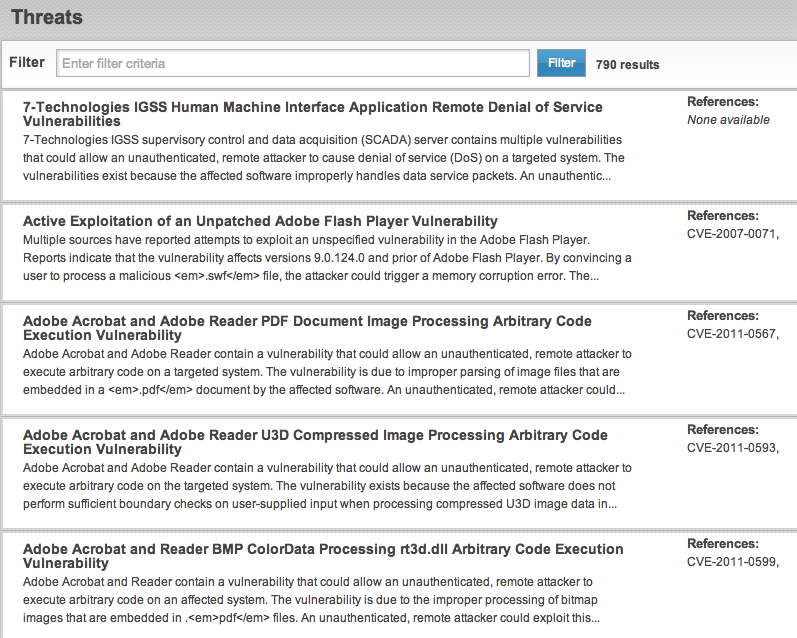
Here is a screenshot of some of the threats you can scan for (there are hundreds of signatures found as you scroll down).
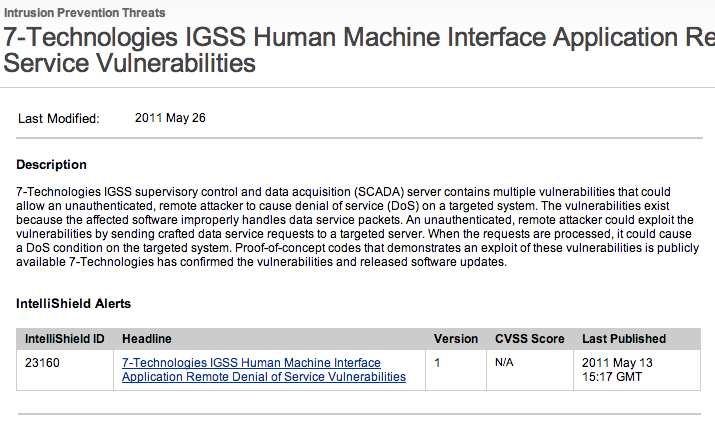
And here is a link reference that can be launched when you want to learn more about a threat
As cool as this sounds, I must say this is more like a IPS light rather than full blown IPS. This new ASA CX add on IPS can detect attacks and actually seems a bit aggressive at times however its limited in on demand tuning like Cisco’s full blown IPS. If you are looking for a feature rich IPS with lots of customizing capabilities, you probably should consider another IPS over this such as SourceFire or a dedicated Cisco IPS that can be added to the ASA without CX. If you want a general IPS, this is great for you. Thats my personal opinion.
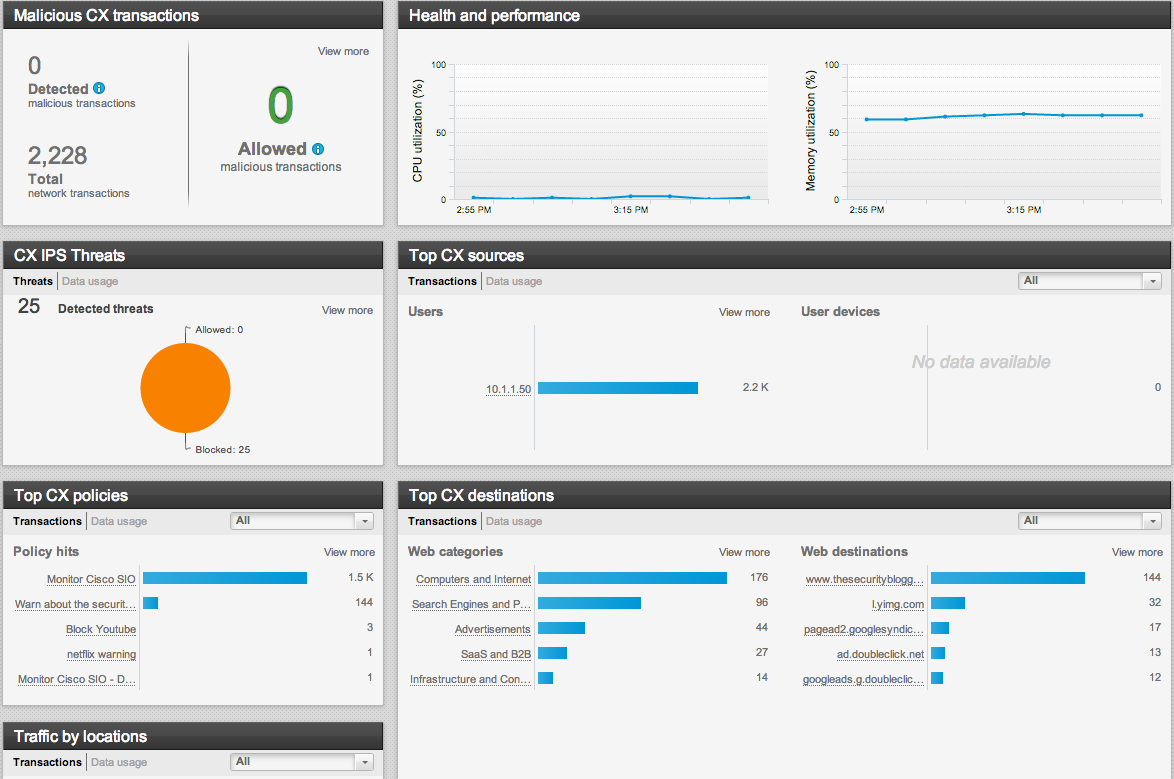
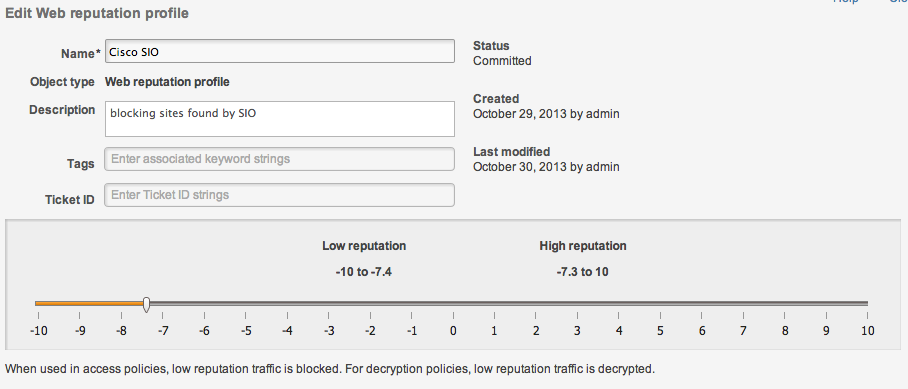
I also noticed the malware protection / global correlation piece has a dedicated tab. This is focused on the known Internet threats IE “The Attacker” rather than what typically a IPS catches via “The Attack”. This is based on credit scoring web sources as shown below.
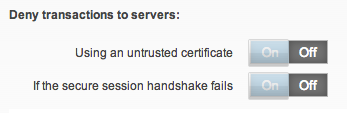
- CX now has more flexibility around decryption settings regarding untrusted certificates. Below is a screenshot showing this. My lab uses untrusted certs for many things so this is a nice option when testing new applications.
- You can configure polices for specific ASA interfaces. This is helpful for me as I’ve made aggressive policy changes that have boggled up my testing scenarios. Now I can just apply those to a specific interface.
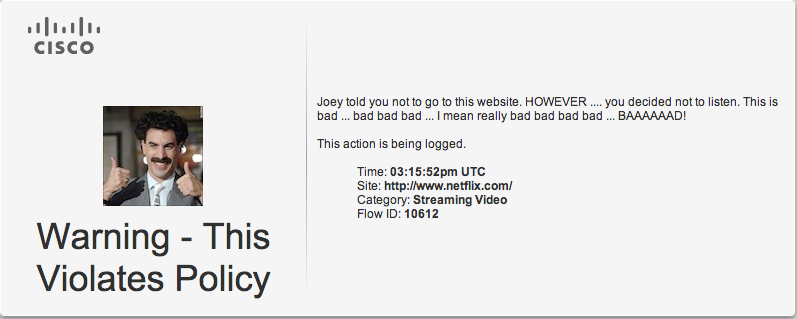
- You can set warnings to a website that a user can accept prior to proceeding. An example of this is my warning about accessing Netflix. You can click continue if you as the user believe the warning is not legit.
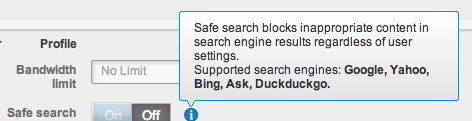
- Cisco now supports Safe Search so you can relax safe search restrictions in search engines. For those that don’t know, Safe Search stops people from pulling up bad stuff while using Internet search engines. Its popular in school and other public facing systems.
- You can configure access policies to rate limit (police) matching traffic, throttling connections that would otherwise overwhelm the network. This is key when permitting music streaming and video use.
![]() There are other things to check out however these are the first ones that stuck out to me post upgrade. Check back for more details on this and other solution overviews.
There are other things to check out however these are the first ones that stuck out to me post upgrade. Check back for more details on this and other solution overviews.



Can I ask if the threats in IPS features in ASA CX can be updated? How can I update? and how can I know that the threats are outdated?
Thank you!
Hi,
Sure you can ask. Yes, the IPS feature updates every 2-5 minutes by default. This is the only way things like the reputation security and website / app awareness can be effective. For example, if you get attacked by a malicious source, we need to know the latest information about that source (IE where is it located, how long has it been online, has it attacked anybody the last few minutes, etc?) to determine if we should permit the connect or just blacklist the source.
Next, we need to know if it meets your policy (IE is it a gambling website that is safe but not approved to viewing by your configured policy). Websites can change categories such as going from lottery (which may be ok) to gambling so knowing updated info on that is import.
Lastly, if the source does attack you (IE a hacker compromises a .gov website to bypass reputation security and attempts to exploit a host), the IPS/IDS has the latest signatures to detect the attack. Those signatures are also updated every 2-5 minutes. To verify if any signatures are updated or to see if the system is able to communicate with the update, an administrator can click the events tab and see in real time communication between cisco SIO (security intelligence operations). This is typically the first step to setup the solution once you access the administration.
Hope this helps