People use weak password practices to secure critical information. Weak password practices include using the same password for multiple systems regardless of the value of the asset, dictionary words, short phases and keeping the same passwords for extended periods of time. For example, it’s common to find a password on a non-critical asset such as a PlayStation 3 be the same as a person’s bank account login.
The more information an attack knows about your password profile, the more likely they will crack your password. For example, a policy of “6-10 characters with one upper case letter and special character” actually helps an attacker reduce the target space meaning passwords are weaker with the policy. If an hacker captures a password for another system and notices a formula such as ‘<dictionary word>’ followed by ‘<3 numbers>’, it helps the attacker prepare a dictionary attack (utilities such as Crunch makes this easy). Any password shorter than 10 characters is an easy target to brute force attack based on today’s system process power.
Here are some tools that hackers can use to crack your passwords.
John the Ripper is an old school yet powerful password cracking utility. It has several types of engines that can crack different types of passwords including encryption and hashes. John can detect most hash types (about 90% accurate) and generate matching hash outputs to map back to auto generated passphrases Attackers like John the Ripper because it’s very customizable
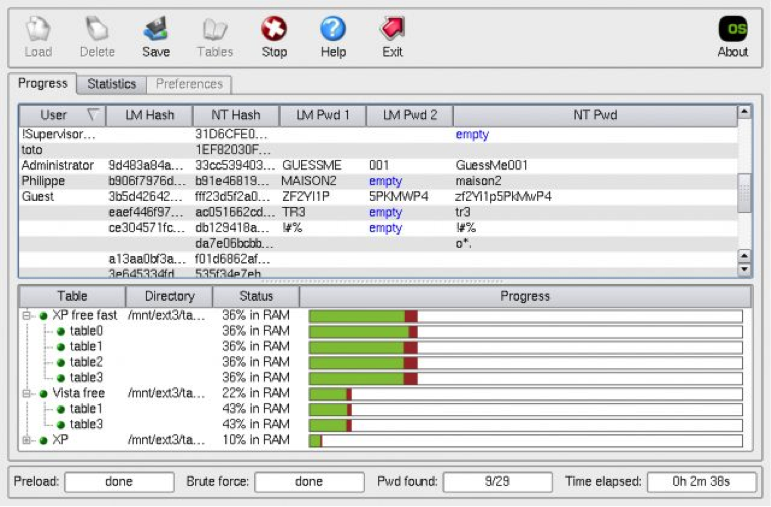
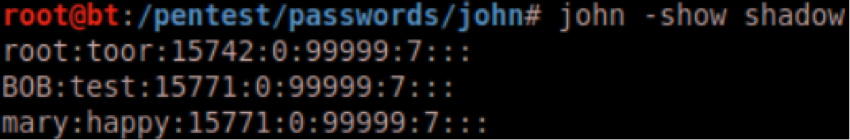 John the Ripper cracked 3 passwords from a Linux shadow file.
John the Ripper cracked 3 passwords from a Linux shadow file.
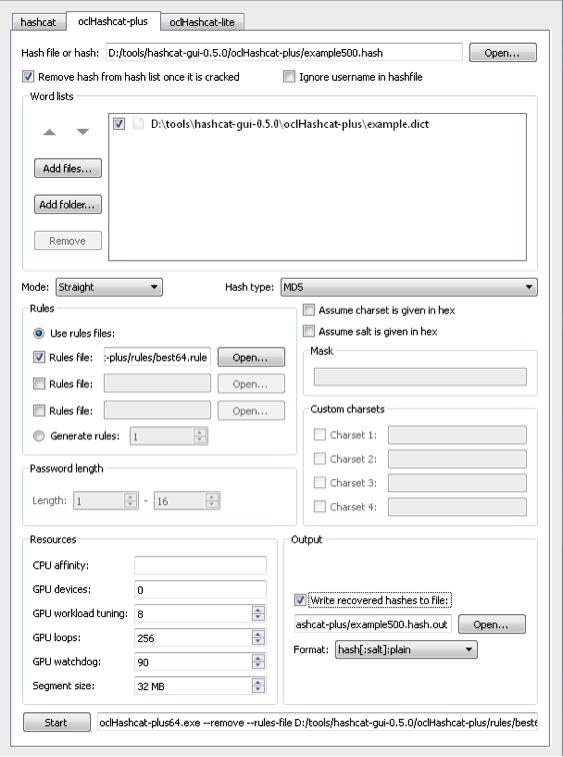
Hashcat is a password cracking utility. Hashcat is multi-thread tool meaning it can handle multiple hashes and password lists during a single attack session. Hashcat offers many attack options such as brute-force, combinator, dictionary, hybrid, mask and rule-based attacks
Hashcat GUI
Ophcrack
Ophcrack is a Windows password cracker based on rainbow tables (Rainbow tables are pre-computed hash tables). Ophcrack can import hashes from a variety of formats including dumping directly from the SAM files of Microsoft Windows.
Ophcrack Cracking Hashes
Findmyhash
Findmyhash is a python script which uses a free online service to crack hashes. Findmyhash will analyze against multiple website Rainbow tables.
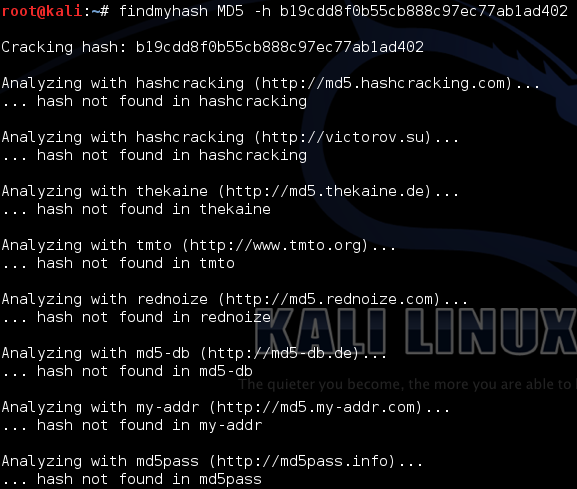 Findmyhash running a MD5 hash against multiple websites
Findmyhash running a MD5 hash against multiple websites
Crunch
Crunch is a tool used to generate password lists. This can be extremely helpful if you are able to gather intelligence on how your target creates passwords. For example, if you capture two passwords and notice the target uses a phase followed by random digits, Crunch can be used to quickly generate a list of that phrase followed by all possible random digits. Perfect tool for defeating company password policies!
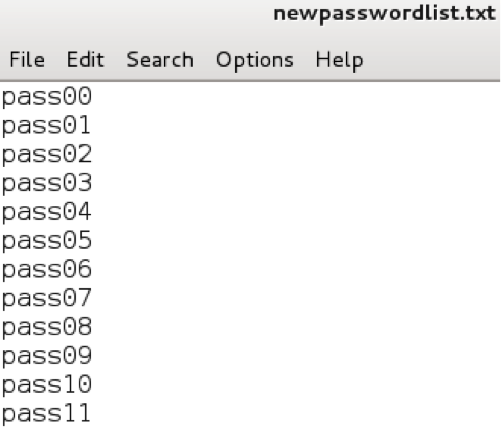
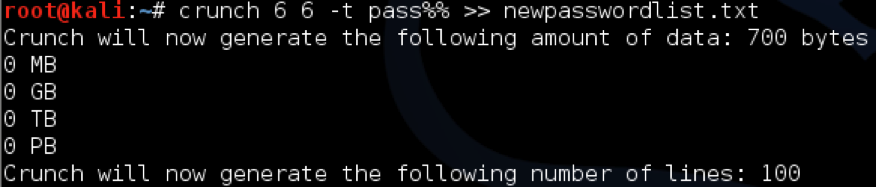 Creating a password list for the word “pass” followed by any two numbers
Creating a password list for the word “pass” followed by any two numbers
Crunch output. List of all combinations of “pass” and two numbers
Chntpw
An alternative to breaking a Windows password is completely bypassing it. Chntpw is a software utility that can reset or remove a Windows passwords. This gives a hacker with access to your Microsoft Windows SAMs file the ability to obtain Administration privileges.
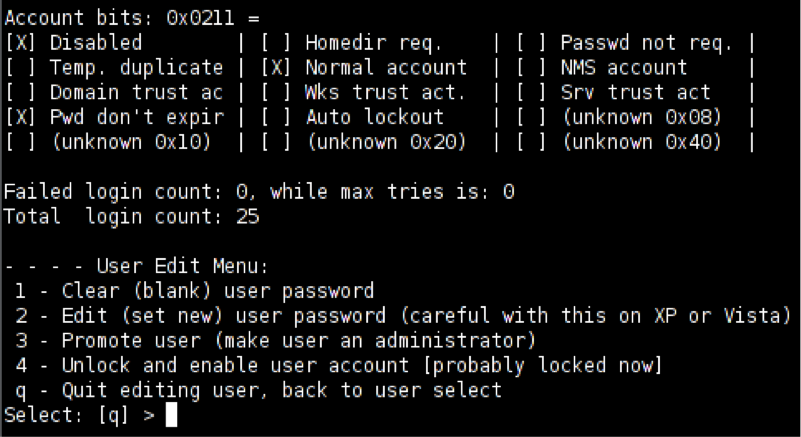 Chntpw options. Option 1 clears the password.
Chntpw options. Option 1 clears the password.
There are many tools available to break weak passwords. Best practices is using a password longer than 10 characters (having a repeated character at the end even helps!), don’t use dictionary words, change your password periodically, don’t use the same passwords for secure and non secure sources and don’t use a computer that accesses sensitive data for personal use (IE same system for Facebook and configuring routers). I suggest using the first letter of each word of a long sentence so you can remember the password yet the output is random. Hope this helps. All tools shown are free and available on BackTrack / Kali.




You can find a new sorted & uniq dictionary list for hashcat && jtr. DCHTPassv1.0 is available on http://www.dcht.org/projekti/ Check it out and Enjoy!