 A common saying is ” Amateurs Hack Systems, Professionals Hack People”. Social engineering is the art of manipulating people into performing actions or divulging confidential information. People fall for social engineering tricks based on their instinct to be helpful and trusting. The typical attacker never comes face-to-face with a victim using deception through email, social networks or over the phone.
A common saying is ” Amateurs Hack Systems, Professionals Hack People”. Social engineering is the art of manipulating people into performing actions or divulging confidential information. People fall for social engineering tricks based on their instinct to be helpful and trusting. The typical attacker never comes face-to-face with a victim using deception through email, social networks or over the phone.
Consultants list end-user training as a top prevention to defend against social engineering. How should you provide training for your user community? Here are some tips for educating your staff about common social engineering attacks.
Explain Why Policies Exist
It is common to see organizations send out policy reminders without explaining why they exist. The average user will delete a policy email once they realize its standard legal language.
Try explaining why users should care. For example, start off with a scenario about an email account being violated and or company data compromised. Include details about what social engineer tactic was used, investment by IT to clean up the issue and ways to avoid the threat. Close with the policy being enforced.
Provide Examples Beyond The Intranet
Organizations typically send warning emails to employees when they discover threats to internal sources. It is rare to see companies extend warnings about phishing or other external attacks. Try periodically sending out examples of different social engineering attacks highlighting what to look for and where they are common. Examples should include social networks, fake URLs, craiglist scams and threats using shareware. Your end-users can be targeted anywhere so educate on all forms of social engineering attacks.
Make Security Fun
One common problem is people leaving their computers unlocked while away from their desk. In a previous job, my team use to send out silly emails from systems found unlocked while unintended. People would laugh and start locking their systems so they don’t become the next victim. Same tactic can be done for mobile devices.
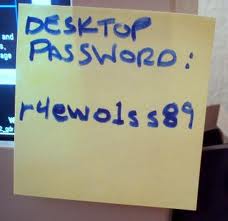
Educate Password Policy Tips
Many people use weak passwords. Try providing education around best practices for developing passwords. My favorite trick is coming up with a long sentence and using the first letter of each word. This way you can remember it and it’s random. Hopefully users will extend tricks like this with password for their personal systems as well.
Social Engineer Your Organization
Try calling and obtaining information over the phone or through social media. Test physical security by having a non-employee put on a suit and attempt to walk around the building without authorized access. Send out a periodic update of social engineering attempts (without people’s names) and what company information was provided over untrusted channels. Close with explaining why social engineering attacks are a high risk and lessons learned from the social engineering penetration test.
Make Sure You Have Executive Approval For These Exercises!


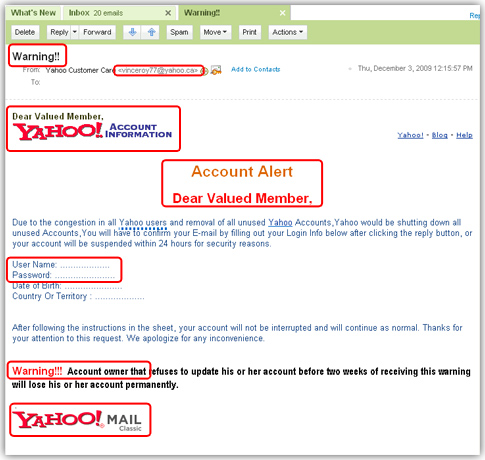





I just read Violet Blue’s November 1 article on the “Emily Williams” exploit (linked above). Fascinating…and instructional.