If you are starting or well into your AI journey, then you probably have asked how can a LLM have up to date knowledge from a vast number of external databases? Without this knowledge, there is no way an AI solution can know the answer to your question hence leading to made up answers commonly referred to as hallucinations. To answer this …. enters Retrieval-Augmented Generation aka RAG. For cybersecurity related AI, RAG is how LLMs pull data from security resources, so it’s important to understand.
A paper posted from Cornell University found HERE speaks not only what RAG is, but six key features that are needed for a trusted RAG. Those six features are Factuality, Robustness, Fairness, Transparency, Accountability, and Privacy. The following diagram comes from this post.
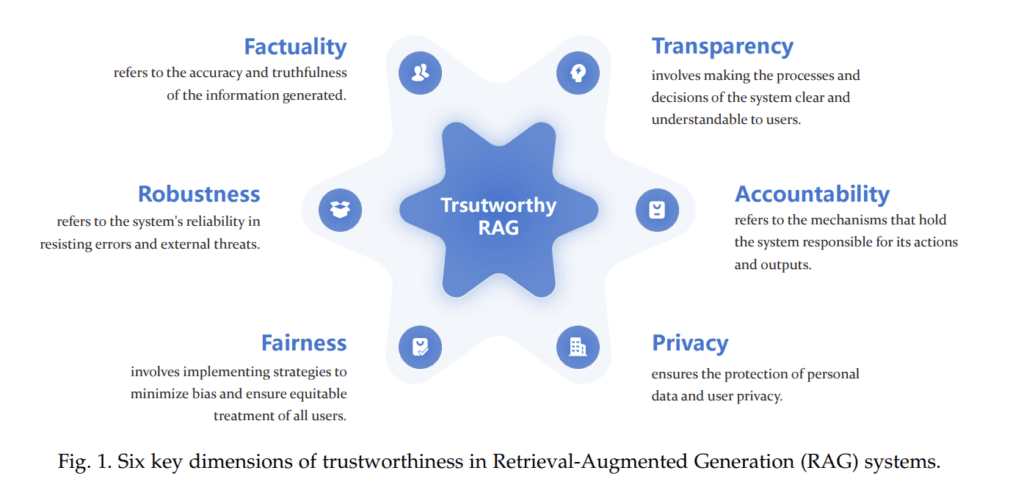
If you are looking how to validate trust in RAG, check out this paper. Also check out my previous post on responsible AI found HERE, which has a lot of overlap with the key points from a trustworthy RAG.